2. First install the keepalived and ipvsadm packages
3.1 Master Configuration (Master Load Balancer)
3.2 Backup Configuration (from Load Balancer)
4. Configure a real server node
5. Test Keepalived+LVS/DR Load Balancing Cluster
5.2 High Availability Functional Test
In this mode, virtual IP can only belong to one node at a time, and another node exists as a standby node.When the primary node is unavailable, the standby node takes over the virtual IP to provide normal service.
1. Instance environment
|
VIP (Virtual IP) |
192.168.73.111 |
|
Master (Master Load Balancer) |
192.168.73.159 |
|
Backup (from Load Balancer) |
192.168.73.133 |
|
Server1 (Server 1) |
192.168.73.156 |
|
Server2 (Server 2) |
192.168.73.154 |
Note: All devices are turned off the firewall and SELinux, otherwise the experiment may not succeed.
[root@master ~]# systemctl stop firewalld [root@master ~]# setenforce 0
2. First install the keepalived and ipvsadm packages
Installed on both primary and secondary load balancers
[root@master ~]# yum -y install ipvsadm keepalived [root@backup ~]# yum -y install ipvsadm keepalived
3.Keepalived configuration
3.1 Master Configuration (Master Load Balancer)
[root@CentOS7 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs { #Global Definition Section
notification_email { #Set an alarm email address, which can have multiple
root@loaclhost.localdomain
}
notification_email_from root@localhost.localdomain
smtp_server 192.168.200.1 #Set SMTP Server Address
smtp_connect_timeout 30 #Set timeout for connection to SMTP server
router_id master #An identity that identifies the keepalived server running
# vrrp_skip_check_adv_addr
# vrrp_strict
# vrrp_garp_interval 0
# vrrp_gna_interval 0
}
vrrp_instance VI_1 { #VRRP instance definition section
state MASTER #Specify that the node is the primary node (uppercase) and the standby node is BACKUP
interface ens33 #Network interface bound to virtual IP
virtual_router_id 51 #VRRP group name, two nodes need to be set the same to indicate that each node belongs to the same VRRP group
priority 100 #Priority of the primary node (1-254), default 100, note that the secondary node priority needs to be lower than the primary node
advert_int 1 #Set the time interval between synchronization checks between two nodes, the two nodes need to be consistent
authentication { #Set validation information, two nodes need to be consistent
auth_type PASS #Set up authentication types, mainly PASS and AH
auth_pass 1111 #Set the authentication password, two nodes must use the same secret under a vrrp_instance
//Code to communicate properly
}
virtual_ipaddress { #Specify virtual IP, two nodes need to be set the same, can have more than one, one per line
192.168.73.111
}
}
virtual_server 192.168.73.111 80 { #Virtual IP Service
delay_loop 6 #Set interval to check actual server
lb_algo rr #Specify LVS Scheduling Algorithm
lb_kind DR #Specify LVS mode, mainly NAT, TUN, DR
# persistence_timeout 50 #Session Hold Time
protocol TCP #Forwarding protocol is TCP
real_server 192.168.73.154 80 { #Backend Real Server Configuration
weight 1 #Set the weight value of the server node
TCP_CHECK { #Real Server State Detection Settings section, in seconds
connect_timeout 3 #Connection timeout
nb_get_retry 3 #retry count
delay_before_retry 3 #retry interval
connect_port 80 #Connection Port
}
}
real_server 192.168.73.156 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
connect_port 80
}
}
}
Start the keepalived service
[root@master ~]# systemctl start keepalived
3.2 Backup Configuration (from Load Balancer)
[root@backup ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
root@loaclhost.localdomain
}
notification_email_from root@localhost.localdomain
smtp_server 192.168.200.1
smtp_connect_timeout 30
router_id backup
# vrrp_skip_check_adv_addr
# vrrp_strict
# vrrp_garp_interval 0
# vrrp_gna_interval 0
}
vrrp_instance VI_1 {
state BACKUP
interface ens33
virtual_router_id 51
priority 90
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.73.111
}
}
virtual_server 192.168.73.111 80 {
delay_loop 6
lb_algo rr
lb_kind DR
# persistence_timeout 50
protocol TCP
real_server 192.168.73.154 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
connect_port 80
}
}
real_server 192.168.73.156 80 {
weight 1
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
connect_port 80
}
}
}
Start the keepalived service
[root@backup ~]# systemctl start keepalived
4. Configure a real server node
[root@Server1 ~]# vim /etcinit.d/lvsrsdr
#!/bin/bash
#description:Start Real Server
VIP=192.168.73.111
source /etc/init.d/functions
case "$1" in
start)
echo "start LVS of Realserver DR"
/sbin/ifconfig lo:1 $VIP broadcast $VIP netmask 255.255.255.255 up
#!/bin/bash
#description:start Realserver
VIP=192.168.73.111
source /etc/init.d/functions
case $1 in
start)
echo "start LVS of Realserver DR"
/sbin/ifconfig lo:1 $VIP broadcast $VIP netmask 255.255.255.255 up
/sbin/route add -host $VIP dev lo:1
echo '1' > /proc/sys/net/ipv4/conf/lo/arp_ignore
echo '2' > /proc/sys/net/ipv4/conf/lo/arp_announce
echo '1' > /proc/sys/net/ipv4/conf/all/arp_ignore
echo '2' > /proc/sys/net/ipv4/conf/all/arp_announce
;;
stop)
/sbin/ifconfig lo:1 down
echo "Close LVS of Realserver DR"
echo '0' > /proc/sys/net/ipv4/conf/lo/arp_ignore
echo '0' > /proc/sys/net/ipv4/conf/lo/arp_announce
echo '0' > /proc/sys/net/ipv4/conf/all/arp_ignore
echo '0' > /proc/sys/net/ipv4/conf/all/arp_announce
;;
*)
echo "Usage: $0 {start|stop}"
exit 1
esac
stay Server1 and server2 Do the following on the node [root@Server1 init.d]# chmod +x lvsrzdr [root@Server1 init.d]# ./lvsrzdr start start LVS of Realserver DR [root@Server1 ~]# echo 192.168.73.156 > /var/www/html/index.html [root@Server1 ~]# systemctl start httpd [root@Server2 init.d]# chmod +x lvsrzdr [root@Server2 init.d]# ./lvsrzdr start start LVS of Realserver DR [root@Server2 ~]# echo 192.168.73.154 > /var/www/html/index.html [root@Server2 ~]# systemctl start httpd
5. Test Keepalived+LVS/DR Load Balancing Cluster
5.1 Load Balancing Test
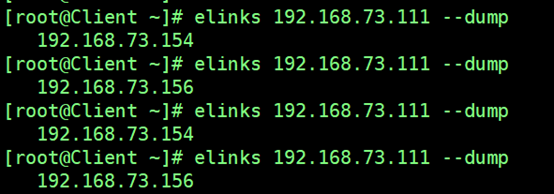
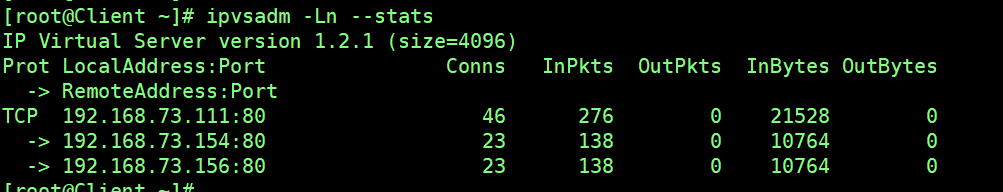
5.2 High Availability Functional Test
High availability is achieved through two load balancers in the LVS.To simulate a failure, stop the Keepalived service on the primary load balancer, and then observe the Keepalived log on the standby load balancer with the following information.As you can see from the log, the standby machine detects the failure of the host immediately, then the standby becomes the MASTER role, takes over the virtual IP resources of the host, and finally binds the virtual IP to the ens33 device.

5.3 Failure Switching Test
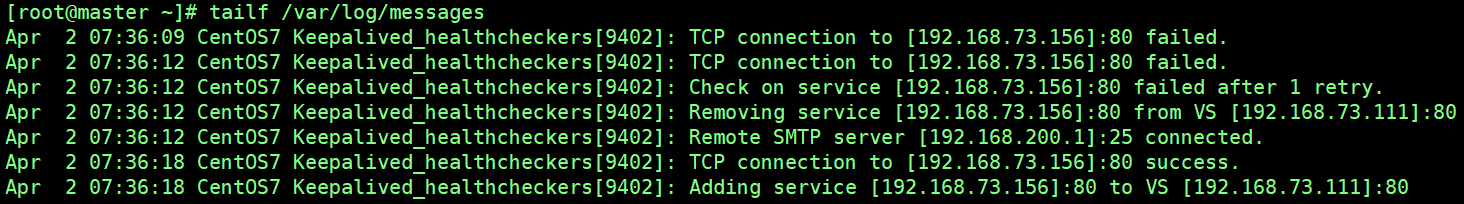
Failover is to test whether Keepalived monitoring module can detect a failure in time after a node fails, then shield the failed node and transfer the service to a normal node for execution.The service of the Real Server 1 node is stopped here. Assuming the node fails, check the primary and standby log information, which is shown below.
From the log, it can be seen that the Keepalived monitoring module removed this node from the cluster system after it detected 192.168.73.156 host failure.
When you visit the address http://192.168.73.111, you should only see "192.168.73.156", because Server1 failed and Keepalived monitoring module excluded Server1 from the cluster system.
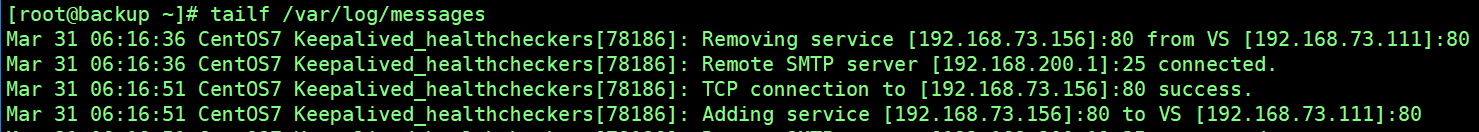
Restart the service of the real server 1 node below, and you can see the following log information for Keepalived.
From the log, Keepalived monitoring module detected 192.168.73.156, which returned to normal, and then joined this node to the cluster system.