Name mobile phone numbers are often stored in databases, such as ID number, bank card number, name and phone number. Such information is usually required to store encrypted storage to meet compliance requirements according to compliance requirements.
Pain point 1:
The usual solution is to manually encrypt and insert the corresponding encrypted fields when writing SQL, and manually decrypt them before using them during query. This method is feasible, but it is very inconvenient and cumbersome to use, which makes the daily business development closely coupled with the details of storage compliance
Pain point 2:
For some systems that did not realize compliance desensitization at the beginning in order to go online quickly, how to quickly make the existing business meet the compliance requirements and minimize the transformation of the original system. (usually, this process includes at least: 1. Storage of new desensitized columns; 2. Simultaneous data migration; 3. Business code compatibility logic, etc.).
There is a data desensitization module under Apache ShardingSphere, which integrates common data desensitization functions. Its basic principle is to parse and intercept the SQL input by the user, and rewrite the SQL by relying on the user's desensitization configuration, so as to realize the encryption of the original field and the decryption of the encrypted field. Finally, encryption, decryption, storage and query without feeling to users are realized.
Desensitization Quick Start - Spring display configuration:
The following describes how to quickly make the system support desensitization configuration based on Spring.
1. Introduce dependency
<!-- for spring namespace -->
<dependency>
<groupId>org.apache.shardingsphere</groupId>
<artifactId>sharding-jdbc-spring-namespace</artifactId>
<version>${sharding-sphere.version}</version>
</dependency>
2. Create desensitization configuration rule object
Before creating a data source, you need to prepare an EncryptRuleConfiguration for desensitization configuration. The following is an example of two table cards in the same data source_ info,pay_ AES encryption is performed in different fields of order
private EncryptRuleConfiguration getEncryptRuleConfiguration() {
Properties props = new Properties();
//The built-in aes algorithm needs
props.setProperty("aes.key.value", aeskey);
EncryptorRuleConfiguration encryptorConfig = new EncryptorRuleConfiguration("AES", props);
//Custom algorithm
//props.setProperty("qb.finance.aes.key.value", aeskey);
//EncryptorRuleConfiguration encryptorConfig = new EncryptorRuleConfiguration("QB-FINANCE-AES", props);
EncryptRuleConfiguration encryptRuleConfig = new EncryptRuleConfiguration();
encryptRuleConfig.getEncryptors().put("aes", encryptorConfig);
//START: card_ Desensitization configuration of info} table
{
EncryptColumnRuleConfiguration columnConfig1 = new EncryptColumnRuleConfiguration("", "name", "", "aes");
EncryptColumnRuleConfiguration columnConfig2 = new EncryptColumnRuleConfiguration("", "id_no", "", "aes");
EncryptColumnRuleConfiguration columnConfig3 = new EncryptColumnRuleConfiguration("", "finshell_card_no", "", "aes");
Map<String, EncryptColumnRuleConfiguration> columnConfigMaps = new HashMap<>();
columnConfigMaps.put("name", columnConfig1);
columnConfigMaps.put("id_no", columnConfig2);
columnConfigMaps.put("finshell_card_no", columnConfig3);
EncryptTableRuleConfiguration tableConfig = new EncryptTableRuleConfiguration(columnConfigMaps);
encryptRuleConfig.getTables().put("card_info", tableConfig);
}
//END: card_ Desensitization configuration of info} table
//START: pay_ Desensitization configuration of order} table
{
EncryptColumnRuleConfiguration columnConfig1 = new EncryptColumnRuleConfiguration("", "card_no", "", "aes");
Map<String, EncryptColumnRuleConfiguration> columnConfigMaps = new HashMap<>();
columnConfigMaps.put("card_no", columnConfig1);
EncryptTableRuleConfiguration tableConfig = new EncryptTableRuleConfiguration(columnConfigMaps);
encryptRuleConfig.getTables().put("pay_order", tableConfig);
}
log.info("Desensitization configuration construction completed:{} ", encryptRuleConfig);
return encryptRuleConfig;
}
explain:
-
When creating EncryptColumnRuleConfiguration, there are four parameters. The first two parameters are divided into tables called plainColumn and cipherColumn, which means the real two columns (name column and desensitized column) in the database storage. For the new system, you only need to set the desensitized column. The above example is that plainColumn is "".
-
When creating EncryptTableRuleConfiguration, you need to pass in a map. The value stored in this map is #1 the EncryptColumnRuleConfiguration described in, and its key is a logical column. For the new system, this logical column is the real desensitization column. When Sharding Shpere intercepts SQL rewriting, it will map the logical column to the name document column or desensitization column (default) according to the user's configuration, as shown in the following example
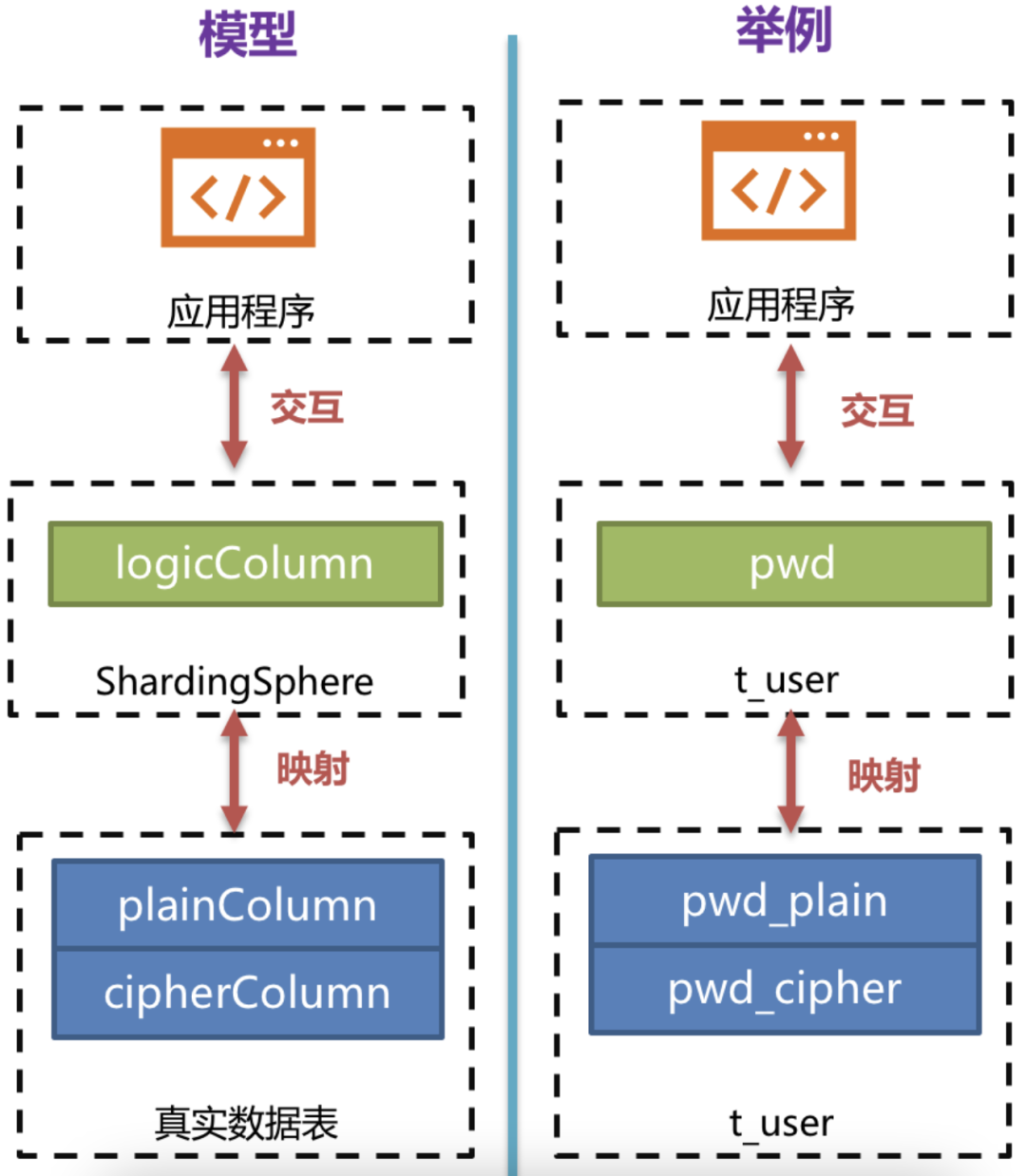
3. Use the Sharding Sphere data source for management
Wrap the original data source
@Bean("tradePlatformDataSource")
public DataSource dataSource(@Qualifier("druidDataSource") DataSource ds) throws SQLException {
return EncryptDataSourceFactory.createDataSource(ds, getEncryptRuleConfiguration(), new Properties());
}
Desensitization configuration Quick Start - Spring Boot version:
The following steps are managed using Spring Boot, which can be solved only with configuration files:
1. Introduce dependency
<!-- for spring boot -->
<dependency>
<groupId>org.apache.shardingsphere</groupId>
<artifactId>sharding-jdbc-spring-boot-starter</artifactId>
<version>${sharding-sphere.version}</version>
</dependency>
<!-- for spring namespace -->
<dependency>
<groupId>org.apache.shardingsphere</groupId>
<artifactId>sharding-jdbc-spring-namespace</artifactId>
<version>${sharding-sphere.version}</version>
</dependency>
2.Spring configuration file
spring.shardingsphere.datasource.name=ds spring.shardingsphere.datasource.ds.type=com.alibaba.druid.pool.DruidDataSource spring.shardingsphere.datasource.ds.driver-class-name=com.mysql.jdbc.Driver spring.shardingsphere.datasource.ds.url=xxxxxxxxxxxxx spring.shardingsphere.datasource.ds.username=xxxxxxx spring.shardingsphere.datasource.ds.password=xxxxxxxxxxxx #Default AES encryptor spring.shardingsphere.encrypt.encryptors.encryptor_aes.type=aes spring.shardingsphere.encrypt.encryptors.encryptor_aes.props.aes.key.value=hkiqAXU6Ur5fixGHaO4Lb2V2ggausYwW # card_info # AES encryption spring.shardingsphere.encrypt.tables.card_info.columns.name.cipherColumn=name spring.shardingsphere.encrypt.tables.card_info.columns.name.encryptor=encryptor_aes # card_info # ID card # AES encryption spring.shardingsphere.encrypt.tables.card_info.columns.id_no.cipherColumn=id_no spring.shardingsphere.encrypt.tables.card_info.columns.id_no.encryptor=encryptor_aes # card_info , bank card number , AES encryption spring.shardingsphere.encrypt.tables.card_info.columns.finshell_card_no.cipherColumn=finshell_card_no spring.shardingsphere.encrypt.tables.card_info.columns.finshell_card_no.encryptor=encryptor_aes # pay_order , bank card number , AES encryption spring.shardingsphere.encrypt.tables.pay_order.columns.card_no.cipherColumn=card_no spring.shardingsphere.encrypt.tables.pay_order.columns.card_no.encryptor=encryptor_aes