Characteristic
Fully using Shiro's annotated configuration to maintain high flexibility.
Give up cookies, Session, and use JWT for authentication to fully implement stateless authentication.
JWT keys support expiration times.
Provides support across domains.
Dead work
Before starting this tutorial, make sure you are familiar with the following points.
Spring Boot basic syntax, at least understand the basic comments Controller, RestController, Autowired, and so on. It's almost like looking at the official Getting-Start tutorial.
The basic concepts of JWT (Json Web Token) and the JAVA SDK for JWT are simple to operate on.
See the official 10 Minute Tutorial for Shiro's basic operations.
Simulate the HTTP request tool, and I'm using PostMan.
Briefly explain why we use JWT, because we want to achieve complete front-end and back-end separation, so it is not possible to use session, cookie for authentication, so JWT is useful, you can use an encryption key for front-end and back-end authentication.
Procedural logic
We logged in with POST username and password to/login, and if we successfully returned an encrypted token, we directly returned a 401 error if we failed.
The user then has to add an Authorizationfield to the header for each web address request that requires permission, such as Authorization: token, where token is the key.
The token check is performed in the background and returns 401 directly if there is a mistake.
Token Encryption Description
Carries username information in token.
Set expiration time.
Encrypt token with user login password.
Token Check Process
Get the username information carried in token.
Enter the database to search for the user and get his password.
Use the user's password to verify that token is correct.
Preparing Maven Files
Create a new Maven project and add related dependencies.
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>org.inlighting</groupId>
<artifactId>shiro-study</artifactId>
<version>1.0-SNAPSHOT</version>
<dependencies>
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.3.2</version>
</dependency>
<dependency>
<groupId>com.auth0</groupId>
<artifactId>java-jwt</artifactId>
<version>3.2.0</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
<version>1.5.8.RELEASE</version>
</dependency>
</dependencies>
<build>
<plugins>
<!-- Srping Boot Packaging Tool -->
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
<version>1.5.7.RELEASE</version>
<executions>
<execution>
<goals>
<goal>repackage</goal>
</goals>
</execution>
</executions>
</plugin>
<!-- Appoint JDK Compiled Version -->
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-compiler-plugin</artifactId>
<configuration>
<source>1.8</source>
<target>1.8</target>
<encoding>UTF-8</encoding>
</configuration>
</plugin>
</plugins>
</build>
</project>
To reduce the code for the tutorial, I used HashMap to simulate a database locally, structured as follows:
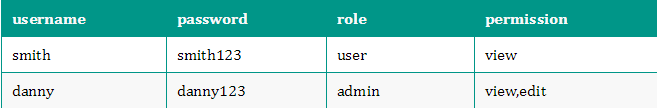
This is the simplest user rights table, if you want to know more, Baidu RBAC yourself.
Then build a UserService to simulate the database query and place the results in the UserBean.
UserService.java
@Component
public class UserService {
public UserBean getUser(String username) {
// No such user returned null directly
if (! DataSource.getData().containsKey(username))
return null;
UserBean user = new UserBean();
Map<String, String> detail = DataSource.getData().get(username);
user.setUsername(username);
user.setPassword(detail.get("password"));
user.setRole(detail.get("role"));
user.setPermission(detail.get("permission"));
return user;
}
}
UserBean.java
public class UserBean {
private String username;
private String password;
private String role;
private String permission;
public String getUsername() {
return username;
}
public void setUsername(String username) {
this.username = username;
}
public String getPassword() {
return password;
}
public void setPassword(String password) {
this.password = password;
}
public String getRole() {
return role;
}
public void setRole(String role) {
this.role = role;
}
public String getPermission() {
return permission;
}
public void setPermission(String permission) {
this.permission = permission;
}
}
Configure JWT
We wrote a simple JWT encryption, verification tool, and used the user's own password as the encryption key, which ensured that token could not be cracked even if intercepted. And we have username information attached to the token and the key will expire in five minutes.
public class JWTUtil {
// Expiration time 5 minutes
private static final long EXPIRE_TIME = 5*60*1000;
/**
* Verify that token is correct
* @param token secret key
* @param secret User's password
* @return Is it correct
*/
public static boolean verify(String token, String username, String secret) {
try {
Algorithm algorithm = Algorithm.HMAC256(secret);
JWTVerifier verifier = JWT.require(algorithm)
.withClaim("username", username)
.build();
DecodedJWT jwt = verifier.verify(token);
return true;
} catch (Exception exception) {
return false;
}
}
/**
* Getting information from a token does not require secret decryption
* @return token User name included in
*/
public static String getUsername(String token) {
try {
DecodedJWT jwt = JWT.decode(token);
return jwt.getClaim("username").asString();
} catch (JWTDecodeException e) {
return null;
}
}
/**
* Generate signature, expire in 5 minutes
* @param username User name
* @param secret User's password
* @return Encrypted token
*/
public static String sign(String username, String secret) {
try {
Date date = new Date(System.currentTimeMillis()+EXPIRE_TIME);
Algorithm algorithm = Algorithm.HMAC256(secret);
// Attached username information
return JWT.create()
.withClaim("username", username)
.withExpiresAt(date)
.sign(algorithm);
} catch (UnsupportedEncodingException e) {
return null;
}
}
}
Build URL s
*ResponseBean.java*
Since we want to restful, we want to make sure that the format returned is the same for each time, so I've created a ResponseBean to unify the format returned.
public class ResponseBean {
// http status code
private int code;
// Return information
private String msg;
// Data returned
private Object data;
public ResponseBean(int code, String msg, Object data) {
this.code = code;
this.msg = msg;
this.data = data;
}
public int getCode() {
return code;
}
public void setCode(int code) {
this.code = code;
}
public String getMsg() {
return msg;
}
public void setMsg(String msg) {
this.msg = msg;
}
public Object getData() {
return data;
}
public void setData(Object data) {
this.data = data;
}
}
Custom Exception
To enable myself to manually throw exceptions, I wrote an UnauthorizedException myself. Java
public class UnauthorizedException extends RuntimeException {
public UnauthorizedException(String msg) {
super(msg);
}
public UnauthorizedException() {
super();
}
}
URL structure;
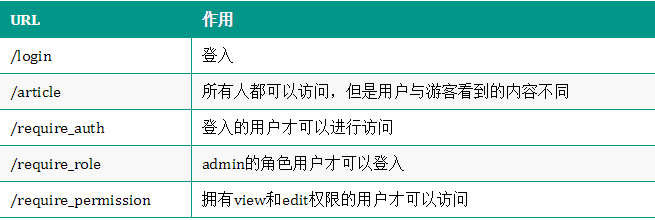
Controller
@RestController
public class WebController {
private static final Logger LOGGER = LogManager.getLogger(WebController.class);
private UserService userService;
@Autowired
public void setService(UserService userService) {
this.userService = userService;
}
@PostMapping("/login")
public ResponseBean login(@RequestParam("username") String username,
@RequestParam("password") String password) {
UserBean userBean = userService.getUser(username);
if (userBean.getPassword().equals(password)) {
return new ResponseBean(200, "Login success", JWTUtil.sign(username, password));
} else {
throw new UnauthorizedException();
}
}
@GetMapping("/article")
public ResponseBean article() {
Subject subject = SecurityUtils.getSubject();
if (subject.isAuthenticated()) {
return new ResponseBean(200, "You are already logged in", null);
} else {
return new ResponseBean(200, "You are guest", null);
}
}
@GetMapping("/require_auth")
@RequiresAuthentication
public ResponseBean requireAuth() {
return new ResponseBean(200, "You are authenticated", null);
}
@GetMapping("/require_role")
@RequiresRoles("admin")
public ResponseBean requireRole() {
return new ResponseBean(200, "You are visiting require_role", null);
}
@GetMapping("/require_permission")
@RequiresPermissions(logical = Logical.AND, value = {"view", "edit"})
public ResponseBean requirePermission() {
return new ResponseBean(200, "You are visiting permission require edit,view", null);
}
@RequestMapping(path = "/401")
@ResponseStatus(HttpStatus.UNAUTHORIZED)
public ResponseBean unauthorized() {
return new ResponseBean(401, "Unauthorized", null);
}
}
Handle Framework Exceptions
Previously, restful was said to return in a uniform format, so we also want to handle Spring Boot throws globally. It works well with @RestControllerAdvice.
@RestControllerAdvice
public class ExceptionController {
// Catch shiro's exceptions
@ResponseStatus(HttpStatus.UNAUTHORIZED)
@ExceptionHandler(ShiroException.class)
public ResponseBean handle401(ShiroException e) {
return new ResponseBean(401, e.getMessage(), null);
}
// Capture UnauthorizedException
@ResponseStatus(HttpStatus.UNAUTHORIZED)
@ExceptionHandler(UnauthorizedException.class)
public ResponseBean handle401() {
return new ResponseBean(401, "Unauthorized", null);
}
// Catch all other exceptions
@ExceptionHandler(Exception.class)
@ResponseStatus(HttpStatus.BAD_REQUEST)
public ResponseBean globalException(HttpServletRequest request, Throwable ex) {
return new ResponseBean(getStatus(request).value(), ex.getMessage(), null);
}
private HttpStatus getStatus(HttpServletRequest request) {
Integer statusCode = (Integer) request.getAttribute("javax.servlet.error.status_code");
if (statusCode == null) {
return HttpStatus.INTERNAL_SERVER_ERROR;
}
return HttpStatus.valueOf(statusCode);
}
}
Configure Shiro
You can start with the official Spring-Shiro integrated tutorial to get a preliminary understanding. But now that we're using Spring-Boot, we're definitely fighting for zero profiles.
Implement JWTToken
JWTToken is almost the carrier of Shiro username passwords. Because we are front-end and back-end separate, the server does not need to save user state, so we do not need such functions as RememberMe. We can simply implement the AuthenticationToken interface. Because token already contains information such as user names, I've got a field here. If you like to drill down, you can see how the official Username PasswordToken is implemented.
public class JWTToken implements AuthenticationToken {
// secret key
private String token;
public JWTToken(String token) {
this.token = token;
}
@Override
public Object getPrincipal() {
return token;
}
@Override
public Object getCredentials() {
return token;
}
}
Implement Realm
The realm's use to handle the legitimacy of users requires our own implementation.
@Service
public class MyRealm extends AuthorizingRealm {
private static final Logger LOGGER = LogManager.getLogger(MyRealm.class);
private UserService userService;
@Autowired
public void setUserService(UserService userService) {
this.userService = userService;
}
/**
* Big pit!, This method must be overridden or Shiro will fail
*/
@Override
public boolean supports(AuthenticationToken token) {
return token instanceof JWTToken;
}
/**
* This method is invoked only when it is necessary to detect user permissions, such as checkRole,checkPermission
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {
String username = JWTUtil.getUsername(principals.toString());
UserBean user = userService.getUser(username);
SimpleAuthorizationInfo simpleAuthorizationInfo = new SimpleAuthorizationInfo();
simpleAuthorizationInfo.addRole(user.getRole());
Set<String> permission = new HashSet<>(Arrays.asList(user.getPermission().split(",")));
simpleAuthorizationInfo.addStringPermissions(permission);
return simpleAuthorizationInfo;
}
/**
* By default, this method is used to verify whether the user name is correct or not, and the error throws an exception.
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken auth) throws AuthenticationException {
String token = (String) auth.getCredentials();
// Decrypt to get username for comparison with database
String username = JWTUtil.getUsername(token);
if (username == null) {
throw new AuthenticationException("token invalid");
}
UserBean userBean = userService.getUser(username);
if (userBean == null) {
throw new AuthenticationException("User didn't existed!");
}
if (! JWTUtil.verify(token, username, userBean.getPassword())) {
throw new AuthenticationException("Username or password error");
}
return new SimpleAuthenticationInfo(token, token, "my_realm");
}
}
In doGetAuthenticationInfo(), users can customize to throw many exceptions, as detailed in the documentation.
Override Filter
All requests pass through the Filter first, so we inherit the official BasicHttpAuthentication Filter and override the authentication method.
Code execution process preHandle -> isAccessAllowed -> isLoginAttempt -> executeLogin.
public class JWTFilter extends BasicHttpAuthenticationFilter {
private Logger LOGGER = LoggerFactory.getLogger(this.getClass());
/**
* Determine if the user wants to log in.
* Just check if the header contains an Authorization field
*/
@Override
protected boolean isLoginAttempt(ServletRequest request, ServletResponse response) {
HttpServletRequest req = (HttpServletRequest) request;
String authorization = req.getHeader("Authorization");
return authorization != null;
}
/**
*
*/
@Override
protected boolean executeLogin(ServletRequest request, ServletResponse response) throws Exception {
HttpServletRequest httpServletRequest = (HttpServletRequest) request;
String authorization = httpServletRequest.getHeader("Authorization");
JWTToken token = new JWTToken(authorization);
// Submit to realm for login, if wrong he will throw an exception and be caught
getSubject(request, response).login(token);
// Logon success if no exception is thrown, returning true
return true;
}
/**
* Here we detail why all of the eventual returns are true, that is, access is allowed
* For example, we provide an address GET/article
* Logged-in users and tourists see different things
* If false is returned here, the request is directly intercepted and the user cannot see anything
* So we're going to return true here, in Controller we can use subject.isAuthenticated() to determine whether a user is logged in
* If some resources are accessible only to the logged-in user, we just need to add the @RequiresAuthentication comment to the method
* However, one drawback of this approach is that it is not possible to filter authentication separately for requests such as GET,POST, etc. (because we override the official method), but it actually has little impact on the application.
*/
@Override
protected boolean isAccessAllowed(ServletRequest request, ServletResponse response, Object mappedValue) {
if (isLoginAttempt(request, response)) {
try {
executeLogin(request, response);
} catch (Exception e) {
response401(request, response);
}
}
return true;
}
/**
* Provide support across domains
*/
@Override
protected boolean preHandle(ServletRequest request, ServletResponse response) throws Exception {
HttpServletRequest httpServletRequest = (HttpServletRequest) request;
HttpServletResponse httpServletResponse = (HttpServletResponse) response;
httpServletResponse.setHeader("Access-control-Allow-Origin", httpServletRequest.getHeader("Origin"));
httpServletResponse.setHeader("Access-Control-Allow-Methods", "GET,POST,OPTIONS,PUT,DELETE");
httpServletResponse.setHeader("Access-Control-Allow-Headers", httpServletRequest.getHeader("Access-Control-Request-Headers"));
// Cross-domain will first send an option request, where we directly return the option request to its normal state
if (httpServletRequest.getMethod().equals(RequestMethod.OPTIONS.name())) {
httpServletResponse.setStatus(HttpStatus.OK.value());
return false;
}
return super.preHandle(request, response);
}
/**
* Jump illegal request to/401
*/
private void response401(ServletRequest req, ServletResponse resp) {
try {
HttpServletResponse httpServletResponse = (HttpServletResponse) resp;
httpServletResponse.sendRedirect("/401");
} catch (IOException e) {
LOGGER.error(e.getMessage());
}
}
}
getSubject(request, response).login(token); This step is committed to realm for processing.
Configure Shiro
@Configuration
public class ShiroConfig {
@Bean("securityManager")
public DefaultWebSecurityManager getManager(MyRealm realm) {
DefaultWebSecurityManager manager = new DefaultWebSecurityManager();
// Use your own realm
manager.setRealm(realm);
/*
* Close the session that comes with shiro. See the documentation for details
* http://shiro.apache.org/session-management.html#SessionManagement-StatelessApplications%28Sessionless%29
*/
DefaultSubjectDAO subjectDAO = new DefaultSubjectDAO();
DefaultSessionStorageEvaluator defaultSessionStorageEvaluator = new DefaultSessionStorageEvaluator();
defaultSessionStorageEvaluator.setSessionStorageEnabled(false);
subjectDAO.setSessionStorageEvaluator(defaultSessionStorageEvaluator);
manager.setSubjectDAO(subjectDAO);
return manager;
}
@Bean("shiroFilter")
public ShiroFilterFactoryBean factory(DefaultWebSecurityManager securityManager) {
ShiroFilterFactoryBean factoryBean = new ShiroFilterFactoryBean();
// Add your own filter and name it jwt
Map<String, Filter> filterMap = new HashMap<>();
filterMap.put("jwt", new JWTFilter());
factoryBean.setFilters(filterMap);
factoryBean.setSecurityManager(securityManager);
factoryBean.setUnauthorizedUrl("/401");
/*
* Custom url rules
* http://shiro.apache.org/web.html#urls-
*/
Map<String, String> filterRuleMap = new HashMap<>();
// All requests through our own JWT Filter
filterRuleMap.put("/**", "jwt");
// Access 401 and 404 pages without our Filter
filterRuleMap.put("/401", "anon");
factoryBean.setFilterChainDefinitionMap(filterRuleMap);
return factoryBean;
}
/**
* The following code adds annotation support
*/
@Bean
@DependsOn("lifecycleBeanPostProcessor")
public DefaultAdvisorAutoProxyCreator defaultAdvisorAutoProxyCreator() {
DefaultAdvisorAutoProxyCreator defaultAdvisorAutoProxyCreator = new DefaultAdvisorAutoProxyCreator();
// Force cglib to prevent duplicate proxies and problems that may cause proxy errors
// https://zhuanlan.zhihu.com/p/29161098
defaultAdvisorAutoProxyCreator.setProxyTargetClass(true);
return defaultAdvisorAutoProxyCreator;
}
@Bean
public LifecycleBeanPostProcessor lifecycleBeanPostProcessor() {
return new LifecycleBeanPostProcessor();
}
@Bean
public AuthorizationAttributeSourceAdvisor authorizationAttributeSourceAdvisor(DefaultWebSecurityManager securityManager) {
AuthorizationAttributeSourceAdvisor advisor = new AuthorizationAttributeSourceAdvisor();
advisor.setSecurityManager(securityManager);
return advisor;
}
}
Inside the URL rule you can refer to the document yourself http://shiro.apache.org/web.html .
summary
Let me just say what else I can do with the code
Shiro's Cache function is not implemented.
Instead of returning 401 information directly when authentication fails in Shiro, it is achieved by jumping to/401 address.