
advanced setting
Authelia
Enter Nginx Proxy Manager and find Authelia domain name auth laosu. Ml corresponding Proxy Hosts, enter the editing state, and switch to the Advanced interface
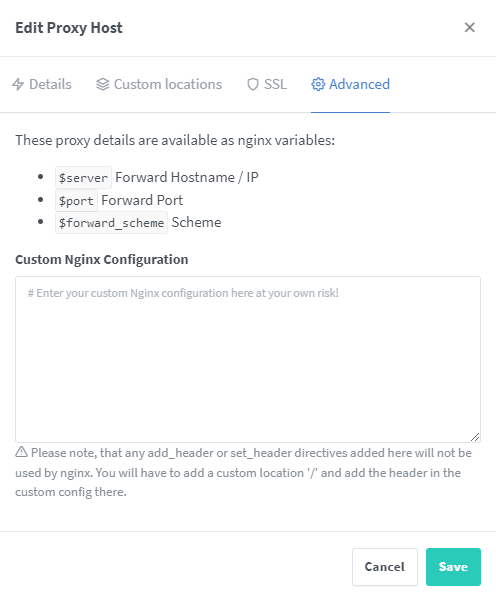
Paste the following code in Custom Nginx Configuration
location / {
set $upstream_authelia http://192.168.0.199:9091; # ip and port of Australia
proxy_pass $upstream_authelia;
client_body_buffer_size 128k;
#Timeout if the real server is dead
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
# Advanced Proxy Config
send_timeout 5m;
proxy_read_timeout 360;
proxy_send_timeout 360;
proxy_connect_timeout 360;
# Basic Proxy Config
proxy_set_header Host $http_host; # Originally $host, changed to $HTTP as suggested by the author_ host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $host;
proxy_set_header X-Forwarded-Uri $request_uri;
proxy_set_header X-Forwarded-Ssl on;
proxy_redirect http:// $scheme://;
proxy_http_version 1.1;
proxy_set_header Connection "";
proxy_cache_bypass $cookie_session;
proxy_no_cache $cookie_session;
proxy_buffers 64 256k;
set_real_ip_from 192.168.0.0/24; #Modify according to your network segment
real_ip_header X-Forwarded-For;
real_ip_recursive on;
}
There are two changes before pasting 👇
- The first place should be changed to the IP of your Qunhui host and the port of Authelia
set $upstream_authelia http://192.168.0.199:9091;
- The second part is modified according to your network segment
set_real_ip_from 192.168.0.0/24; #Modify according to your network segment
Protected domain
| domain name | purpose | rule |
|---|---|---|
| https://ad.laosu.ml | Access address of administrator | one_factor |
| https://sp1.laosu.ml | Access address of speed test | one_factor |
| https://nas.laosu.ml | Access address of Qunhui management interface | two_factor |
| https://n8n.laosu.ml | Access address of n8n | two_factor |
Every protected domain, whether one_factor or two_ For all factors, enter the Nginx Proxy Manager, find the corresponding Proxy Hosts, enter the editing state, switch to the Advanced interface, and paste the following code in the Custom Nginx Configuration
location /authelia {
internal;
set $upstream_authelia http://192.168.0.199:9091/api/verify; # ip and port of Australia
proxy_pass_request_body off;
proxy_pass $upstream_authelia;
proxy_set_header Content-Length "";
# Timeout if the real server is dead
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
client_body_buffer_size 128k;
proxy_set_header Host $http_host;
proxy_set_header X-Original-URL $scheme://$http_host$request_uri;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Uri $request_uri;
proxy_set_header X-Forwarded-Ssl on;
proxy_redirect http:// $scheme://;
proxy_http_version 1.1;
proxy_set_header Connection "";
proxy_cache_bypass $cookie_session;
proxy_no_cache $cookie_session;
proxy_buffers 4 32k;
send_timeout 5m;
proxy_read_timeout 240;
proxy_send_timeout 240;
proxy_connect_timeout 240;
}
location / {
set $upstream_speedtest http://192.168.0.199:8180; # Change the name, IP and port of the app
proxy_pass $upstream_speedtest; # To change the name of an application, you can generally use upstream_ How to apply names
auth_request /authelia;
auth_request_set $target_url $scheme://$http_host$request_uri;
auth_request_set $user $upstream_http_remote_user;
auth_request_set $groups $upstream_http_remote_groups;
proxy_set_header Remote-User $user;
proxy_set_header Remote-Groups $groups;
error_page 401 =302 https://auth.laosu.ml:444/?rd=$target_url; # Change to your authelia domain name and bring it with you if you have a port
client_body_buffer_size 128k;
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
send_timeout 5m;
proxy_read_timeout 360;
proxy_send_timeout 360;
proxy_connect_timeout 360;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Uri $request_uri;
proxy_set_header X-Forwarded-Ssl on;
proxy_redirect http:// $scheme://;
proxy_http_version 1.1;
proxy_set_header Connection "";
proxy_cache_bypass $cookie_session;
proxy_no_cache $cookie_session;
proxy_buffers 64 256k;
set_real_ip_from 192.168.0.0/16; #Modify according to your network segment
real_ip_header X-Forwarded-For;
real_ip_recursive on;
}
There are several changes before pasting 👇
- The first place should be changed to the IP of your Qunhui host and the port of Authelia
set $upstream_authelia http://192.168.0.199:9091/api/verify; # ip and port of Australia
- The second is to modify $upstream_speedtest is generally changed according to the name of the application and the name of the container, mainly for easy identification, for example: $upstream_adminer, $upstream_n8n et al
- Back address http://192.168.0.199:8180 You need to set it according to your application. This is the speedtest application installed by Lao su
set $upstream_speedtest http://192.168.0.199:8180; # Change the name, IP and port of the app
proxy_pass $upstream_speedtest; # To change the name of an application, you can generally use upstream_ How to apply names
- The third place needs to be changed to your authelia domain name. If it is not filed like Lao Su, you must bring the port here
error_page 401 =302 https://auth.laosu.ml:444/?rd=$target_url; # Change to your authelia domain name and bring it with you if you have a port
- Fourth, modify according to your network segment
set_real_ip_from 192.168.0.0/16; #Modify according to your network segment
function
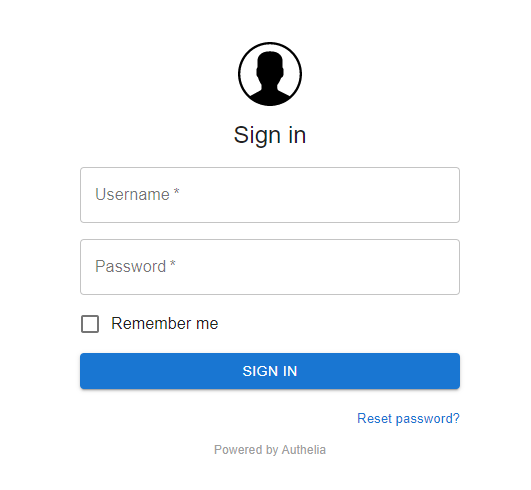
Open first https://auth.laosu.ml:444 , the login interface of authelia appears
Follow our previous steps in users_ database. The settings in YML, the account number is authelia and the password is 123456; Lao Su here is just an example. If you set it like this, it makes no difference whether it is set or not
After successful login
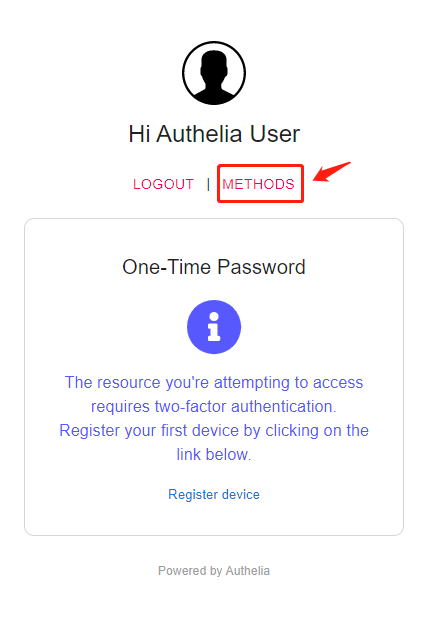
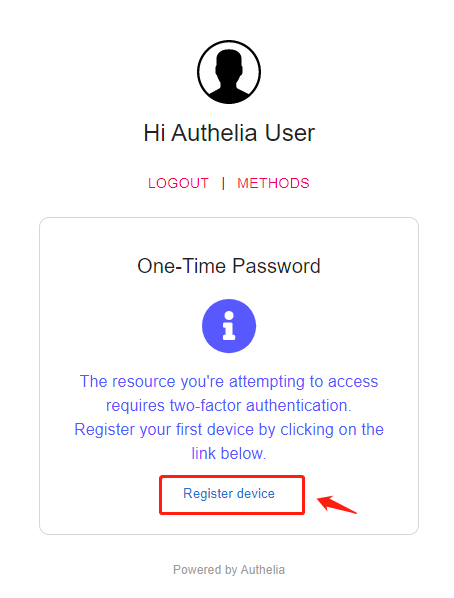
If two is set_ Factor, the device to be registered will be displayed
Next try https://sp1.laosu.ml:444 , the login interface of Australia appears. Enter the account and password, and the test interface is opened directly after successful login
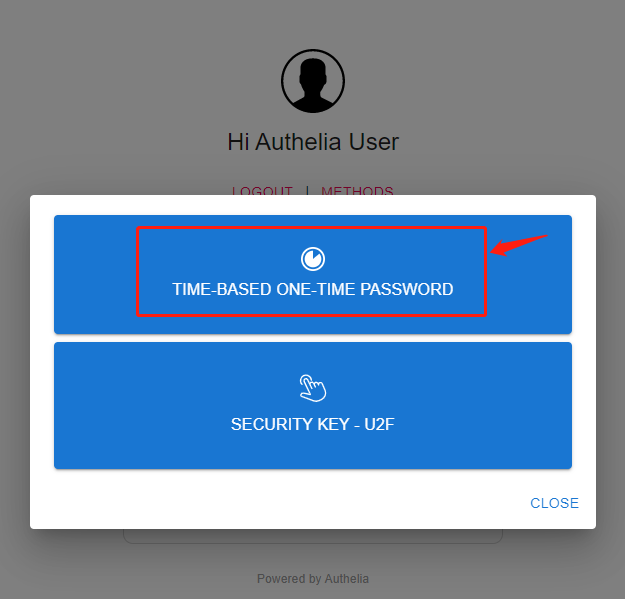
Open https://n8n.laosu.ml:444 , the rule is two_factor, click METHODS and select TOTP
Click Register device to register the device
One time password (OTP), also known as "one time password", refers to a password that can only be used once. One time password is a combination of unpredictable random numbers generated every 60 seconds according to a special algorithm. iKEY One-Time Password has been widely used in the fields of finance, telecommunications, online games and so on, which effectively protects the security of users. [Baidu Encyclopedia]
There are many old Microsoft OTP and authenticator software
Send mail is displayed in the upper right corner
Enter the mailbox and click the blue Register button in the middle
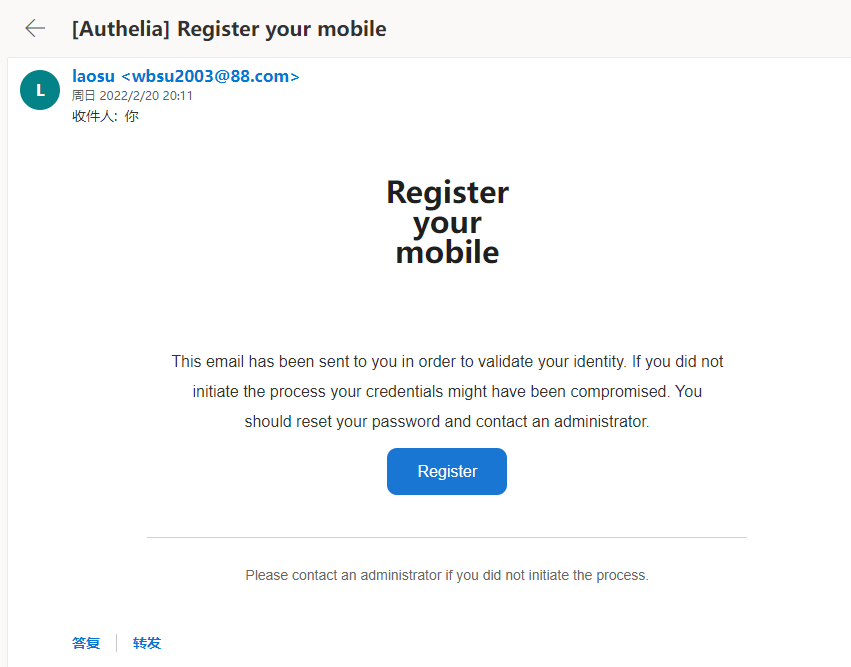
If the page is wrong, check whether the port is missing in the url. The 444 port used by Lao Su is a non-standard port (the default SSL port is 443, so Lao Su thinks 444 is non-standard). You need to add it yourself. If you add it, just enter in the address bar and refresh the page
According to the author, you may need to go to v4 34 will fix the problem of non-standard port operation

Lao Su uses Microsoft Authenticator. After opening it, he scans QR code by adding account -- > personal account -- >
Back to the login interface of the web page, six boxes will be displayed after refreshing
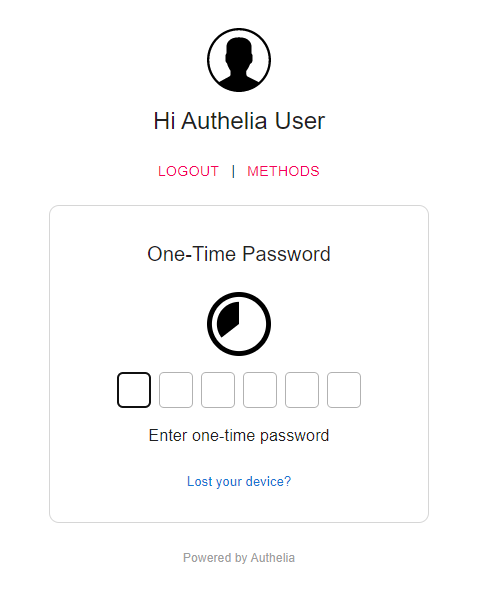
Fill in the 6-digit number in Microsoft Authenticator. After verification, you can see n8n the interface
epilogue
With Authelia and Fail2ban to prevent violent cracking, the security of public network access will be greatly guaranteed.
Although the official emphasizes that OpenID Connect is still in the preview stage, Authelia actually supports OIDC authentication. However, due to space limitation, I'd like to save it for the next time.
Next period notice 👉 "The Outline uses Authelia to realize local authentication". This article will discuss how to realize the Outline to complete local authentication through Authelia's OIDC, instead of relying on the third-party authentication based on the public network.
Reference documents
authelia/authelia: The Single Sign-On Multi-Factor portal for web apps
Address: https://github.com/authelia/authelia
Home - Authelia
Address: https://www.authelia.com/docs/
Running authelia on a non standard HTTPs port. Base href is not valid. · Issue #2765 · authelia/authelia
Address: https://github.com/authelia/authelia/issues/2765
Authelia - SSO and 2FA portal
Address: https://www.blackvoid.club/authelia-sso-and-2fa-portal/
Self-Hosted SSO with Authelia and NGINX
Address: https://matwick.ca/authelia-nginx-sso/
Setup Authelia to work... | The Homelab Wiki
Address: https://thehomelab.wiki/books/dns-reverse-proxy/page/setup-authelia-to-work-with-nginx-proxy-manager
Authelia: Install Guide on Unraid + NGINX (Brief) - YouTube
Address: https://www.youtube.com/watch?app=desktop&v=fr-t7sGrYtI
SkyPi/README.md at main · Just5KY/SkyPi
Address: https://github.com/Just5KY/SkyPi/blob/main/Authelia/README.md