My latest and complete articles are on pumpkin slow www.pkslow.com Welcome to tea. Com!
1 Preface
Coupon www.fenfaw.com cnTwo articles have been written on the integration of Spring Cloud Data Flow into UAA. The previous scheme was to save user information in the database; However, in many enterprises, AD is used to manage account information. This article will explain how to integrate Data Flow and LDAP.
Spring Cloud Data Flow related articles:
Initial experience of Spring Cloud Data Flow, running in Local mode
Deploy Spring Cloud Data Flow on Kubernetes and try another task
Spring Cloud Data Flow is operated by Shell to facilitate the establishment of CICD
After being cheated by Spring, I checked the source code and finally solved the problem of deploying K8s application by DataFlow
Spring Cloud Data Flow integrates Cloudfoundry UAA services for permission control
Spring Cloud Data Flow integrates UAA and uses external databases and API interfaces
2 start the LDAP server
2.1 start the server
We use Apache's open source framework as Ldap server, and introduce dependencies as follows:
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter</artifactId>
<version>2.1.0.RELEASE</version>
</dependency>
<dependency>
<groupId>org.apache.directory.server</groupId>
<artifactId>apacheds-protocol-ldap</artifactId>
<version>1.5.5</version>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-ldap</artifactId>
</dependency>
</dependencies>
The startup classes of Springboot are as follows:
@SpringBootApplication
public class LdapServer {
public static void main(String[] args) throws Throwable {
SpringApplication.run(LdapServer.class, args);
}
@Bean
public ApacheDSContainer apacheDSContainer() throws Exception {
final File temporaryFolder = Files.createTempDirectory("ldap_server").toFile();
final String ldapFileName = "testUsers.ldif";
ApacheDSContainer apacheDSContainer = new ApacheDSContainer("dc=springframework,dc=org",
"classpath:" + ldapFileName);
apacheDSContainer.setPort(40000);
final File workingDir = new File(temporaryFolder, UUID.randomUUID().toString());
apacheDSContainer.setWorkingDirectory(workingDir);
return apacheDSContainer;
}
}
The startup port is 40000, and the user configuration information ldif file is testusers ldif, we configure the ad account and group information used in the test in this file. DC = spring framework, DC = org is the root directory of AD and the starting point of all configuration information trees.
testUsers. LDIF is relatively large, please refer to: https://github.com/LarryDpk/pkslow-samples/blob/master/spring-cloud/ldap-server/src/main/resources/testUsers.ldif .
2.2 connecting to the server
After starting the Ldap server, we can view and manage it through the Apache Directory Studio client tool. As shown in the figure below:
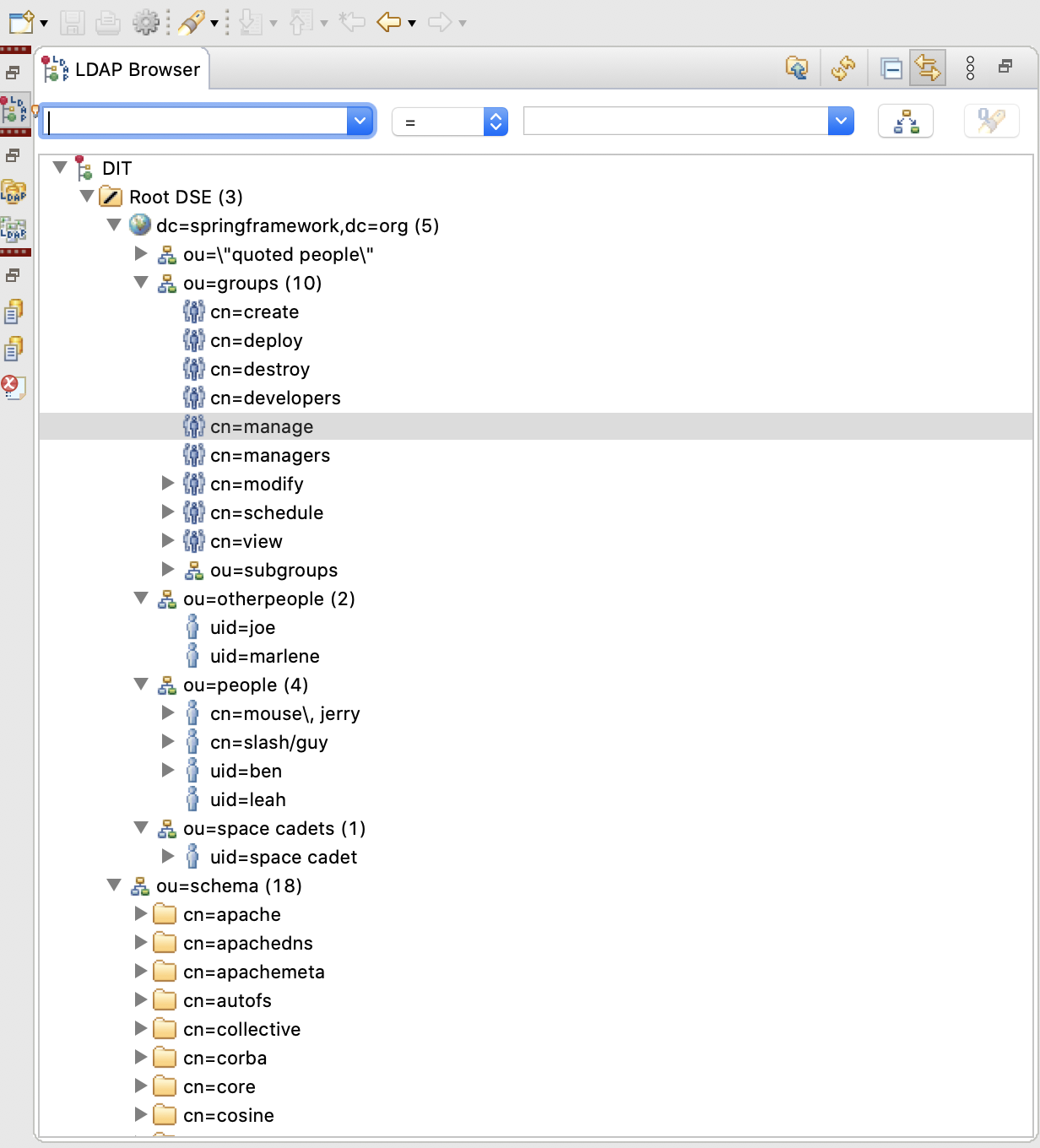
3 UAA configuration
The UAA server needs to configure relevant information to connect to the Ldap service, which is configured in UAA The specific configurations added in the YML file are as follows:
spring_profiles: default,postgresql,ldap
ldap:
profile:
file: ldap/ldap-search-and-bind.xml
base:
url: 'ldap://localhost:40000/'
userDn: 'uid=leah,ou=people,dc=springframework,dc=org'
password: 'leahberlin'
searchBase: 'ou=otherpeople,dc=springframework,dc=org'
searchFilter: 'uid={0}'
referral: follow
groups:
file: 'ldap/ldap-groups-map-to-scopes.xml'
searchBase: 'ou=groups,dc=springframework,dc=org'
searchSubtree: true
groupSearchFilter: member={0}
maxSearchDepth: 10
autoAdd: true
profiles needs to add ldap to enable this function.
After adding the configuration, restart the UAA server to take effect. However, we can now obtain the user's AD group through the user's login information, but this group is different from the UAA group, and a mapping relationship needs to be established for them. Namely:
AD group --> UAA group --> Data Flow Role.
The second half of the mapping relationship was explained earlier. The first half can be configured through uaac or Rest API, as follows:
uaac group map "cn=view,ou=groups,dc=springframework,dc=org" --name="dataflow.view" --origin=ldap uaac group map "cn=create,ou=groups,dc=springframework,dc=org" --name="dataflow.create" --origin=ldap uaac group map "cn=manage,ou=groups,dc=springframework,dc=org" --name="dataflow.manage" --origin=ldap
4 login test
We directly use the user marlene/supersecret configured in the ldif file to log in as follows:
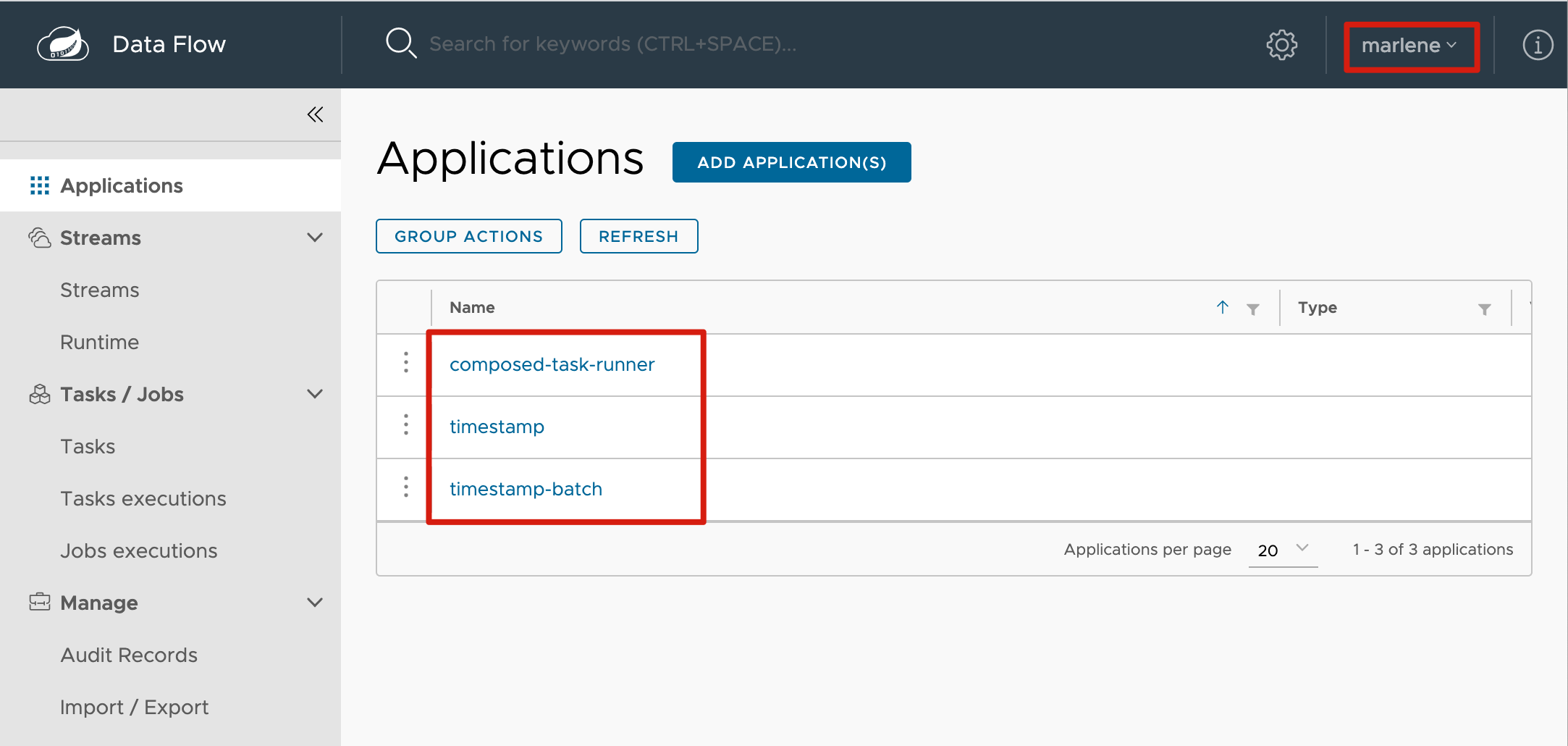
In fact, we can still log in using the account saved in the database (such as larry/larry). They can coexist and provide great convenience.
5 Summary
This article explains the integration of Data Flow and LDAP. So far, the authentication of Spring Cloud Data Flow has been relatively complete.
Please check the code: https://github.com/LarryDpk/pkslow-samples
Reference documents:
security-ldap-uaa-example
Introduction to OpenLDAP concept and working principle
Welcome to WeChat official account, "pumpkin slow talk", which will continue to update for you.
Read more and share more; Write more and organize more.