1 configure SSL
1.1 introduction to SSL
SSL configuration is a scenario we often see in practical applications
SSL(Secure Sockets Layer) is a security protocol that provides security and data integrity for forgotten communication. SSL encrypts the network connection in the network transmission layer. SSL protocol is located between TCP/IP protocol and various application layer protocols to provide security support for data communication.
SSL protocol can be divided into two layers:
- SSL record protocol, which is based on reliable transmission protocol (such as TCP), provides data encapsulation, compression, encryption and other basic functions for high-level protocols
- SSL handshake protocol, which is based on SSL recording protocol, is used for identity authentication, negotiation of encryption algorithm, interactive encryption key, etc. between communication parties before the actual data transmission
In Web applications based on B/S, SSL is realized through HTTPS. HTTPS is an HTTP channel with security as its goal. In short, it is the secure version of HTTP, that is, adding SSL layer under http. The security basis of HTTPS is SSL
Because spring boot uses embedded tomcat, we need to do the following operations when configuring SSL
1.2 keytool generated certificate
Using SSL first requires a certificate, which can be either self signed or obtained from the SSL certificate authorization center.
Every JDK or JRE has a tool called keytool, which is a certificate management tool that can be used to generate self signed certificates
Keytool is a Java data certificate management tool. Keytool stores keys and certificates in a file called keystore, which contains two kinds of data:
- Key entity - secret key, or private key and paired public key (asymmetric encryption)
- trusted certificate entries - only public keys
keystore command:
keytool -genkey -alias tomcat -keyalg RSA -keystore d:/mykeystore -dname "CN=localhost, OU=localhost, O=localhost, L=SH, ST=SH, C=CN" -keypass password -storepass password -validity 36500
Parameter Description:
- -genkey means to create a new key
- -dname means Distinguished Names of the key, CN=commonName
OU=organizationUnit ,O=organizationName
L=localityName ,S=stateName ,C=country
Distinguished Names indicates the identity of the issuer of the key - -keyalg uses an encryption algorithm. Here is RSA
- -Alias is the alias of the key. Each keystore is associated with a unique alias. This alias is usually case insensitive
- -keypass is the password of the private key, which is set as password here
- -The keystore key is saved in the mykeystore file in the D: disk directory. If the generation location is not specified, the keystore will exist in the system default directory with the user's file name keystore
- -storepass access password, which is set as password here. This password provides the system to take out the information from the mykeystore file
- -Validity the validity period of this key is 36500, which means 100 years (90 days by default)
1.3 cacerts certificate
The cacerts certificates file
The modified certificate file exists in Java Home / lib / security directory is the CA certificate warehouse of Java system
Verify that a certificate with the same name has been created
keytool -list -v -alias tomcat -keystore "%JAVA_HOME%/jre/lib/security/cacerts" -storepass password
1.4 configuration in springboot
server.ssl.key-store=classpath:tomcat_rsa.keystore server.ssl.key-alias=tomcat_rsa server.ssl.key-store-type=JKS server.ssl.key-store-password=123456
Note: the classpath here is Tomcat_ rsa. Keystore is found from the relative path in the project, or from the absolute path
1.5 error reporting ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Configure ssl certificate for SpringBoot and access prompt ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Generate * Specifying - keyalg RSA during keystore can avoid such problems
Or add field properties in the configuration
server.ssl.ciphers=TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_ECDHE_RSA_WITH_RC4_128_SHA,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA,SSL_RSA_WITH_RC4_128_SHA,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
2 HTTP to HTTPS
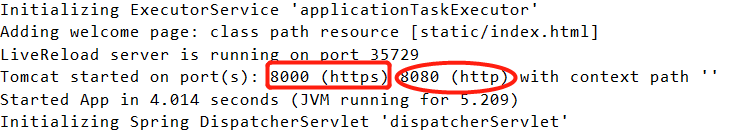
Directly enter the port number corresponding to http in the browser address bar, and then automatically jump to the port number corresponding to https
import org.apache.catalina.Context;
import org.apache.catalina.connector.Connector;
import org.apache.tomcat.util.descriptor.web.SecurityCollection;
import org.apache.tomcat.util.descriptor.web.SecurityConstraint;
import org.springframework.boot.web.embedded.tomcat.TomcatServletWebServerFactory;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
@Configuration
public class HttpConfig {
@Bean
public Connector httpContector(){
Connector connector=new Connector("org.apache.coyote.http11.Http11NioProtocol");
connector.setScheme("http");
connector.setPort(8080);
connector.setSecure(false);
connector.setRedirectPort(8000);
return connector;
}
@Bean
public TomcatServletWebServerFactory tomcatServletWebServerFactory(Connector connector){
TomcatServletWebServerFactory tomcat=new TomcatServletWebServerFactory(){
@Override
protected void postProcessContext(Context context) {
SecurityConstraint securityConstraint=new SecurityConstraint();
securityConstraint.setUserConstraint("CONFIDENTIAL");
SecurityCollection collection=new SecurityCollection();
collection.addPattern("/*");
securityConstraint.addCollection(collection);
context.addConstraint(securityConstraint);
}
};
tomcat.addAdditionalTomcatConnectors(connector);
return tomcat;
}
}
After successful startup, you can see