SSH
Common remote connection software
-
Putty: putty is an open source software with only more than 500 k, small and lightweight, but single function
-
SecureCRT: SecureCRT is a terminal emulator that supports SSH(SSH1 and SSH2). In short, it is the software that logs in to the UNIX or Linux server host under Windows. The disadvantage is that the color scheme is not in line with public habits
-
Xshell: xshell is a powerful security terminal simulation software. It supports SSH1, SSH2 and TELNET protocol of Microsoft Windows platform. Xshell helps users enjoy their work in a complex network environment through the secure connection from the Internet to remote hosts and its innovative design and features. Disadvantages: charges
-
MobaXterm: powerful and free
SSH
summary
-
SSH is a network protocol used for encrypted login between computers. Users can log in to another computer remotely from the local computer using SSH protocol.
-
sshd service, which is based on SSH protocol and used for remote connection, is automatically installed with the system
-
sshd service
- 22 port
- TCP protocol
-
Based on C/S architecture, client ssh, server openssh
encryption algorithm
Symmetric encryption algorithm (DES)
-
The sender uses the key to encrypt the plaintext data into ciphertext and send it out
-
After receiving the ciphertext, the receiver uses the same key to decrypt the ciphertext into plaintext
Asymmetric encryption algorithm (RSA)
- The public key corresponds to the private key one by one. The public key can be made public and the private key is private
- The receiver sends the public key to the sender
- The sender uses the public key sent by the receiver to encrypt the plaintext data into ciphertext and send it out
- After receiving the ciphertext, the receiver decrypts the ciphertext into plaintext using its own locally retained private key
Des & RSA comparison
| Comparison item | Symmetric encryption | Asymmetric encryption |
|---|---|---|
| secret key | identical | Different, but there is a corresponding relationship |
| Encryption speed | Faster | slower |
| Data transmission speed | Faster | slower |
| Security | Lower | higher |
SSH authentication
User name password based authentication
principle
-
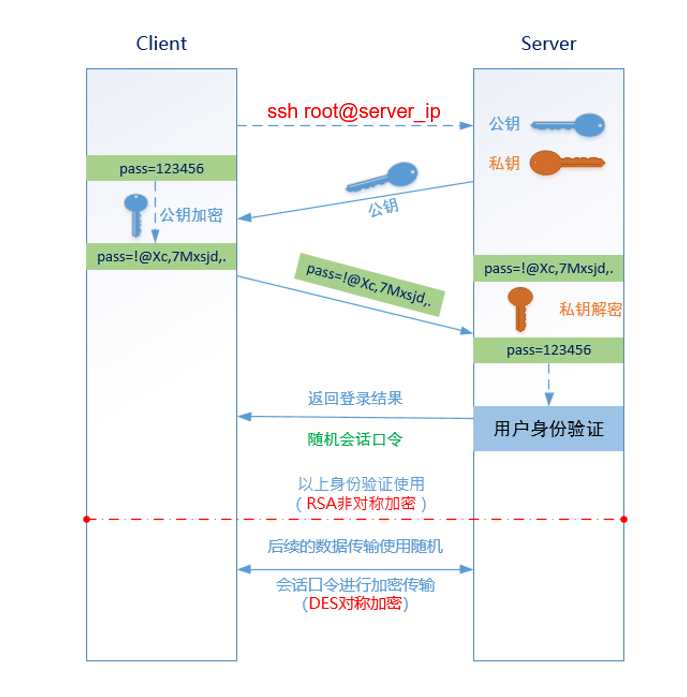
The client sends a login request to the server
-
The server sends its public key to the client
-
The client uses the public key sent by the server to encrypt its password and send it to the SSH server
-
After receiving the encrypted password sent by the client, the server decrypts it with the locally retained private key
-
The server compares the decrypted password with the user password in the / etc/shadow file for authentication
-
If the server authentication is successful, the login success result is returned, and a random session password is sent to the client, which is used for a temporary encrypted session password for data transmission between the next two hosts
Remote connection
Get the of the server ip
[root@server ~]# ip a
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:76:f9:7d brd ff:ff:ff:ff:ff:ff
inet 192.168.226.10/24 brd 192.168.226.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet6 fe80::1b78:bfb3:4567:b45c/64 scope link noprefixroute
valid_lft forever preferred_lft forever
ip The address is 192.168.226.10
Enter the set password to log in
[root@client ~]# ssh root@192.168.226.10
root@192.168.226.20's password:
Last failed login: Sat Aug 21 15:46:55 CST 2021 from node1 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Sat Aug 21 15:35:38 2021 from 192.168.226.1
Key pair based authentication
principle
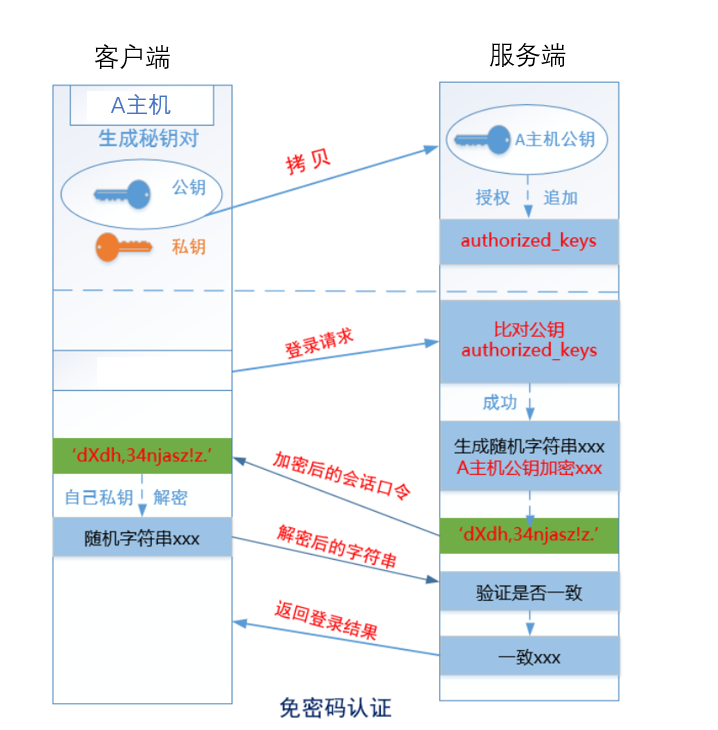
- Generate a key pair (public key and private key) at the client
- The client sends the public key to the server, which saves it in ~ / ssh/authorized_keys
- The client initiates a login request to the server, and the server compares the public key (whether the public key sent again is consistent with the public key saved in ~ /. ssh/authorized_keys)
- After the comparison is consistent, the server will generate a random string and encrypt it through the public key sent by the client
- The server sends the encrypted string to the client
- After receiving it, the client decrypts it through the local private key, and then sends the decrypted string back to the non server
- The server compares the string to verify whether it is consistent with the generated string
- If you are consistent, you can log in successfully
Password free login
Generate "key pair" in client host [root@client ~]# ssh-keygen #Just press enter Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Created directory '/root/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: SHA256:olnJ6qKrHOywFyCOr3elrSjJewf+Tbwn4CG1zNJS1+8 root@client The key's randomart image is: +---[RSA 2048]----+ | | | | | . | |o + o . | |+. * B S . | |o..= %o. . | |o=..X+oo . | |*o*=oo+... E | |B@+o=o oo | +----[SHA256]-----+ [root@client ~]# ls /root/.ssh/ id_rsa id_rsa.pub id_rsa Private key file id_rsa.pub Public key file( public) Transfer the public key file to the remote host (required if the default port is changed)-p (specify port number) [root@client ~]# ssh-copy-id root@192.168.226.20 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub" The authenticity of host '192.168.226.20 (192.168.226.20)' can't be established. ECDSA key fingerprint is SHA256:+RvxL8ZDWnyO030Z5rOfjBuJaOG1yFvD9ieOY9uzWBA. ECDSA key fingerprint is MD5:d2:a2:8c:c6:60:15:46:9b:09:75:ce:3f:e1:ea:6e:aa. Are you sure you want to continue connecting (yes/no)? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@192.168.226.20's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'root@192.168.226.20'" and check to make sure that only the key(s) you wanted were added. [root@server ~]# ls /root/.ssh/ authorized_keys <--Public key file from client You can also create it on the remote host first~/.ssh/authorized_keys File, and then copy the contents of the client public key file to the file
~/.ssh : 700
~/.ssh/authorized_keys : 600
Do not modify the permissions of these two files at will, otherwise it may lead to secret free failure
SSH service setup
For safety reasons, there are the following requirements:
- Disable root remote login
- The sshd service does not allow the use of the default 22 port to prevent automatic script attacks
- The account and password of the client user are randomly generated by professional tools
Prepare environment [root@server ~]# systemctl stop firewalld.service [root@server ~]# systemctl disable firewalld.service [root@server ~]# setenforce 0 setenforce: SELinux is disabled [root@server ~]# sed -i 's/enforced/disabled/' /etc/selinux/config install openssh,Installed by default (this step can be ignored) [root@server ~]# yum install -y openssh [root@server ~]# RPM - QL openssh server view which server files are generated /etc/pam.d/sshd /etc/ssh/sshd_config Master profile /etc/sysconfig/sshd /usr/lib/systemd/system/sshd-keygen.service /usr/lib/systemd/system/sshd.service /usr/lib/systemd/system/sshd.socket /usr/lib/systemd/system/sshd@.service /usr/lib64/fipscheck/sshd.hmac /usr/libexec/openssh/sftp-server /usr/sbin/sshd /usr/sbin/sshd-keygen Used to generate public and private keys /usr/share/man/man5/moduli.5.gz /usr/share/man/man5/sshd_config.5.gz Help for configuration files /usr/share/man/man8/sftp-server.8.gz /usr/share/man/man8/sshd.8.gz /var/empty/sshd [root@server ~]# RPM - QL openssh clients view which client files are generated /etc/ssh/ssh_config /usr/bin/scp /usr/bin/sftp /usr/bin/slogin /usr/bin/ssh /usr/bin/ssh-add /usr/bin/ssh-agent /usr/bin/ssh-copy-id /usr/bin/ssh-keyscan /usr/lib64/fipscheck/ssh.hmac /usr/libexec/openssh/ssh-pkcs11-helper /usr/share/man/man1/scp.1.gz /usr/share/man/man1/sftp.1.gz /usr/share/man/man1/slogin.1.gz /usr/share/man/man1/ssh-add.1.gz /usr/share/man/man1/ssh-agent.1.gz /usr/share/man/man1/ssh-copy-id.1.gz /usr/share/man/man1/ssh-keyscan.1.gz /usr/share/man/man1/ssh.1.gz /usr/share/man/man5/ssh_config.5.gz /usr/share/man/man8/ssh-pkcs11-helper.8.gz Modify profile [root@server ~]# man 5 sshd_config view help information for the configuration file [root@server ~]# vim /etc/ssh/sshd_config 17 Port 2882 modify sshd Default port 38 PermitRootLogin no prohibit root Remote login [root@server ~]# systemctl restart sshd Create an ordinary employee [root@server ~]# groupadd staff [root@server ~]# useradd -g staff staff1 [root@server ~]# useradd -g staff staff2 Set password for user( pwgen) [root@server ~]# yum install -y epel-release.noarch [root@server ~]# yum install -y pwgen [root@server ~]# pwgen --help Usage: pwgen [ OPTIONS ] [ pw_length ] [ num_pw ] Options supported by pwgen: -c or --capitalize Include at least one capital letter in the password Contains at least one capital letter -n or --numerals Include at least one number in the password Contains at least one number -s or --secure Generate completely random passwords Generate a completely random password -B or --ambiguous Don't include ambiguous characters in the password Does not contain ambiguous characters (1)&l,0&o) -1 Don't print the generated passwords in columns Do not print passwords in columns (one per row) [root@server ~]# pwgen -cnBs1 10 2 YPurX4FCTd Password assigned to staff1 H9F9aYXrzJ Password assigned to staff2 [root@server ~]# passwd staff1 Change user staff1 Your password. New password: Re enter the new password: passwd: All authentication tokens have been successfully updated. [root@server ~]# passwd staff2 Change user staff2 Your password. New password: Re enter the new password: passwd: All authentication tokens have been successfully updated. Create a data directory for employees and specify permissions [root@server ~]# mkdir -p /jobs/staff [root@server ~]# chgrp -R staff /jobs/staff/ [root@server ~]# chmod 1770 /jobs/staff/ [root@server ~]# ll -d /jobs/staff/ drwxrwx--T 2 root staff 6 8 May 21:39 /jobs/staff/ test [root@client ~]# ssh root@192.168.226.10 The authenticity of host '192.168.226.10 (192.168.226.10)' can't be established. ECDSA key fingerprint is SHA256:+RvxL8ZDWnyO030Z5rOfjBuJaOG1yFvD9ieOY9uzWBA. ECDSA key fingerprint is MD5:d2:a2:8c:c6:60:15:46:9b:09:75:ce:3f:e1:ea:6e:aa. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.226.10' (ECDSA) to the list of known hosts. root@192.168.226.10's password: Permission denied, please try again. root@192.168.226.10's password: Permission denied, please try again. --------------------------------------------------root User not allowed to log in [root@client ~]# ssh staff1@192.168.226.10 -p 2882 staff1@192.168.226.10's password: [staff1@server ~]$ cd /jobs/staff/ [staff1@server staff]$ touch test.txt [staff1@server staff]$ exit Logout Connection to 192.168.226.10 closed. -------------------------------------------------- [root@client ~]# ssh staff2@192.168.226.10 -p 2882 staff2@192.168.226.10's password: [staff2@server ~]$ cd /jobs/staff/ [staff2@server staff]$ mkdir dir1 [staff2@server staff]$ ll Total consumption 0 drwxr-xr-x 2 staff2 staff 6 8 September 21-22:28 dir1 -rw-r--r-- 1 staff1 staff 0 8 September 21-22:26 test.txt [staff2@server staff]$ rm -rf test.txt rm: Cannot delete"test.txt": Operation not allowed ----------------------------------------staff2 Cannot delete staff1 Files created
file transfer
scp remote copy file
-
Based on ssh protocol
-
To copy files between hosts, you must have the copy execution account and operation permission of two hosts at the same time.
-
Both hosts must be Linux systems and cannot cross operating systems
Download to local( server1) [root@server2 ~]# ls anaconda-ks.cfg dir1 video.mp4 [root@server1 ~]# scp root@192.168.226.20:/root/video.mp4 ./ root@192.168.226.20's password: video.mp4 [root@server1 ~]# scp -r root@192.168.226.20:/root/dir1 ./ root@192.168.226.20's password: [root@server1 ~]# ls anaconda-ks.cfg a.txt dir1 video.mp4 Upload to remote( aliyun-server) [root@server1 ~]# scp ./video.mp4 root@120.24.76.94:/tmp/ The authenticity of host '120.24.76.94 (120.24.76.94)' can't be established. ECDSA key fingerprint is SHA256:9pEHWkFQ19qj+ZYAyORdvYejZfSXWhjfgwHyfbXMPss. ECDSA key fingerprint is MD5:a9:2a:14:cb:1b:bb:2a:09:65:7c:91:04:d6:f3:a2:b0. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '120.24.76.94' (ECDSA) to the list of known hosts. root@120.24.76.94's password: video.mp4 100% 40MB 6.9MB/s 00:05 [root@server1 ~]# scp -r ./dir2 root@120.24.76.94:/tmp/ root@120.24.76.94's password: [root@aliyun-server ~]# ls /tmp dir2 video.mp4 Option Description: -r: Recursion, for folders -P: appoint sshd Service port. If this option is not added, the default port is 22
lrzsz (file transfer between Windows and Linux)
yum install lrzsz -y rz Select file and save to Linux sz test1 Select the storage location to save to Windows in