SSL Connection in Mysql
The following is from the network reference and self-test collation, did not find the relevant information. If there are any mistakes, please correct them.
Current Mysql client versions are basically not able to support caching_sha2_password authentication. With Mysql 8.0, it is recommended to add parameters:
default-authentication-plugin=mysql_native_password
Otherwise, the client connection may fail. The following cases are based on this. The client's lack of support will result in the failure to reflect the real results.
Users in the current database
root@(none):53: >select host,user,ssl_type,ssl_cipher,x509_issuer,x509_subject,plugin from mysql.user; +--------------+------------------+----------+------------+-------------+--------------+-----------------------+ | host | user | ssl_type | ssl_cipher | x509_issuer | x509_subject | plugin | +--------------+------------------+----------+------------+-------------+--------------+-----------------------+ | % | rep | | | | | mysql_native_password | | % | root | | | | | mysql_native_password | | % | test | | | | | mysql_native_password | | % | test1 | | | | | caching_sha2_password | | 192.168.20.% | cat | X509 | | | | mysql_native_password | | localhost | mysql.infoschema | | | | | caching_sha2_password | | localhost | mysql.session | | | | | caching_sha2_password | | localhost | mysql.sys | | | | | caching_sha2_password | | localhost | root | | | | | caching_sha2_password | +--------------+------------------+----------+------------+-------------+--------------+-----------------------+ 10 rows in set (0.00 sec)
Requ_secure_transport = OFF mode
This is the default setting, in which users can connect to the database without ssl encryption
-- No passage SSL Connection mode mysql -h mysql1 -utest -ptest --ssl-mode=DISABLED SSL: Not in use -- adopt SSL Connection mode mysql -h mysql1 -utest -ptest mysql -h mysql1 -utest -ptest --ssl-mode=PREFERRED mysql -h mysql1 -utest1 -ptest1 --ssl-mode=PREFERRED mysql -h mysql1 -utest1 -ptest1 --ssl-mode=REQUIRED SSL: Cipher in use is DHE-RSA-AES128-GCM-SHA256
navicate can be connected by configuring only regular tabs
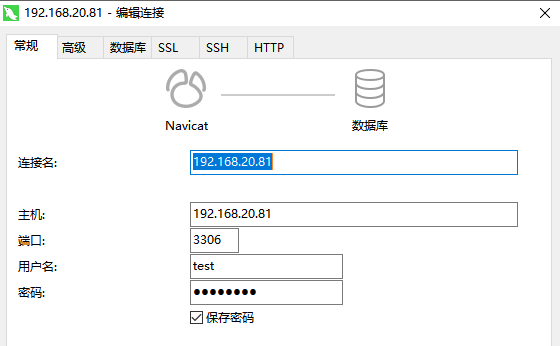
Connection followed by non-encrypted mode
show status like 'ssl_cipher';
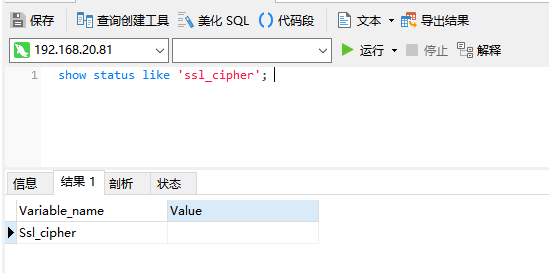
But we can also use encrypted connections
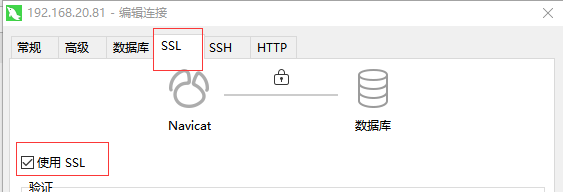
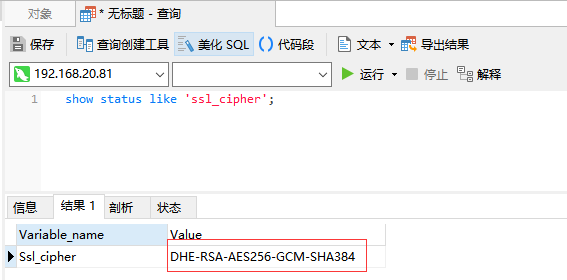
Requ_secure_transport = ON mode
Mandatory configuration of ssl
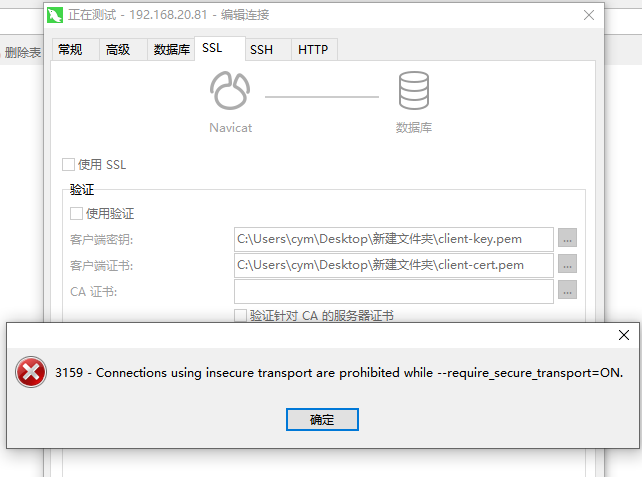
If you don't use an SSL connection, the MySQL command line will report an error
-- No use SSL [root@mysql2 ~]# mysql -h mysql1 -utest -ptest --ssl-mode=disabled mysql: [Warning] Using a password on the command line interface can be insecure. ERROR 3159 (HY000): Connections using insecure transport are prohibited while --require_secure_transport=ON. -- Use SSL [root@mysql2 ~]# mysql -h mysql1 -utest -ptest mysql: [Warning] Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 17 Server version: 8.0.16 MySQL Community Server - GPL Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql> show status like 'ssl_cipher'; +---------------+---------------------------+ | Variable_name | Value | +---------------+---------------------------+ | Ssl_cipher | DHE-RSA-AES128-GCM-SHA256 | +---------------+---------------------------+ 1 row in set (0.01 sec)
SSL-MODE has the following five options
'DISABLED D'-- No use of SSL encryption
'PREFERRED','REQUIRED'-- Encryption algorithms are the same using SSL
'VERIFY_CA','VERIFY_IDENTITY'-- Options such as ssl-ca need to be added
Use of PEM
The official document will recommend that we initialize Mysql and execute the following commands
mysql_ssl_rsa_setup --datadir=datadir path, which generates the following files in the data directory.
So how do you use these files?
[root@mysql1 mydata1]# ll /u01/mydata1/*.pem -rw-------. 1 mysql mysql 1680 Jun 4 03:12 /u01/mydata1/ca-key.pem -rw-r--r--. 1 mysql mysql 1112 Jun 4 03:12 /u01/mydata1/ca.pem -rw-r--r--. 1 mysql mysql 1112 Jun 4 03:12 /u01/mydata1/client-cert.pem -rw-------. 1 mysql mysql 1680 Jun 4 03:12 /u01/mydata1/client-key.pem -rw-------. 1 mysql mysql 1676 Jun 4 03:12 /u01/mydata1/private_key.pem -rw-r--r--. 1 mysql mysql 452 Jun 4 03:12 /u01/mydata1/public_key.pem -rw-r--r--. 1 mysql mysql 1112 Jun 4 03:12 /u01/mydata1/server-cert.pem -rw-------. 1 mysql mysql 1680 Jun 4 03:12 /u01/mydata1/server-key.pem
Creating Users
root@(none):39: >create user cat@'192.168.20.%' identified with mysql_native_password by 'cat' require ssl; -- This requires that the user must use SSL,Even parameters require_secure_transport = OFF
root@(none):39: >grant all on *.* to cat@'192.168.20.%';
root@(none):39: >alter user cat@'192.168.20.%' require x509; -- Here is the requirement for use pem Documents
root@(none):39: >select host,user,ssl_type,ssl_cipher,x509_issuer,x509_subject,plugin from mysql.user where user='cat' \G
*************************** 1. row ***************************
host: 192.168.20.%
user: cat
ssl_type: X509
ssl_cipher:
x509_issuer:
x509_subject:
plugin: mysql_native_password
1 row in set (0.00 sec)
Testing regular SSL connections will fail
[root@mysql2 ~]# mysql -h mysql1 -ucat -pcat mysql: [Warning] Using a password on the command line interface can be insecure. ERROR 1045 (28000): Access denied for user 'cat'@'192.168.20.82' (using password: YES) [root@mysql2 ~]# mysql -h mysql1 -ucat -pcat --ssl-mode=PREFERRED mysql: [Warning] Using a password on the command line interface can be insecure. ERROR 1045 (28000): Access denied for user 'cat'@'192.168.20.82' (using password: YES)
Copy pem files
If you want to connect successfully, you need to use the PEM file. copy the PEM file on the server side to the client side.
#mysql1 [root@mysql1 mydata1]# scp client-cert.pem mysql2:/home/mysql client-cert.pem 100% 1112 873.8KB/s 00:00 [root@mysql1 mydata1]# scp client-key.pem mysql2:/home/mysql client-key.pem 100% 1680 169.9KB/s 00:00 #mysql2 [root@mysql2 ~]# ll /home/mysql total 8 -rw-r--r-- 1 root root 1112 Jul 14 09:43 client-cert.pem -rw------- 1 root root 1680 Jul 14 09:43 client-key.pem
Successful connection with pem
[root@mysql2 ~]# mysql -h mysql1 -ucat -pcat --ssl-cert=/home/mysql/client-cert.pem --ssl-key=/home/mysql/client-key.pem mysql: [Warning] Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 50 Server version: 8.0.16 MySQL Community Server - GPL Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
The ssl-ca parameter can also be used, and the ca.pem of the server segment needs to be copied to the client. as
[root@mysql2 ~]# mysql -h mysql1 -ucat -pcat --ssl-ca=/home/mysql/ca.pem --ssl-cert=/home/mysql/client-cert.pem --ssl-key=/home/mysql/client-key.pem
Tool Connection
You need to download the pem file on the server side to your computer and specify the location of the pem file for the connection tool before you can connect to the database.
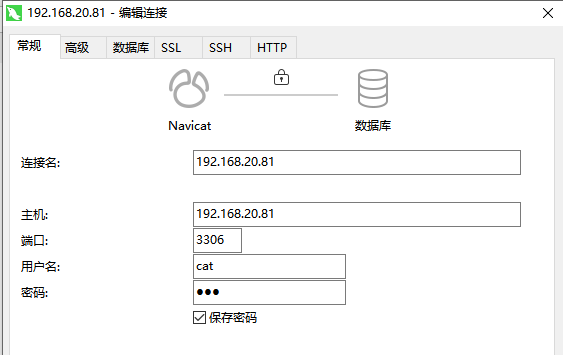
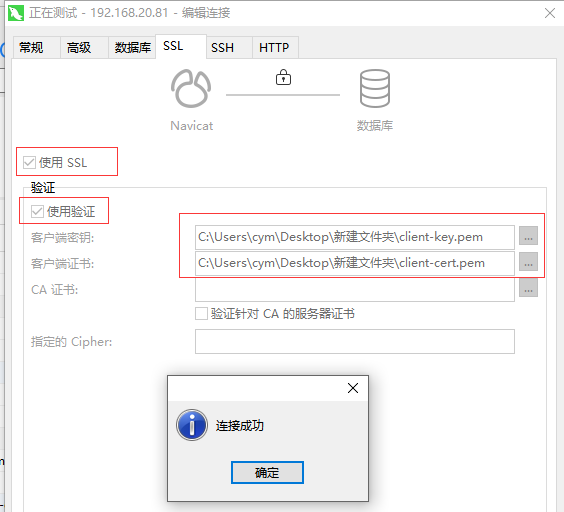
Do you need to re-copy pem files to add users?
-- Adding users root@(none):09: >create user dog@'192.168.20.%' identified with mysql_native_password by 'dog' require x509; -- Use x509 Can not be specified require ssl,But it will still be mandatory. SSL Query OK, 0 rows affected (0.00 sec) root@(none):09: >grant all on *.* to dog@'192.168.20.%'; Query OK, 0 rows affected (0.01 sec)
Add new users without having to copy again
-- Successful connection [root@mysql2 ~]# mysql -h mysql1 -udog -pdog --ssl-cert=/home/mysql/client-cert.pem --ssl-key=/home/mysql/client-key.pem mysql: [Warning] Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 13 Server version: 8.0.16 MySQL Community Server - GPL Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
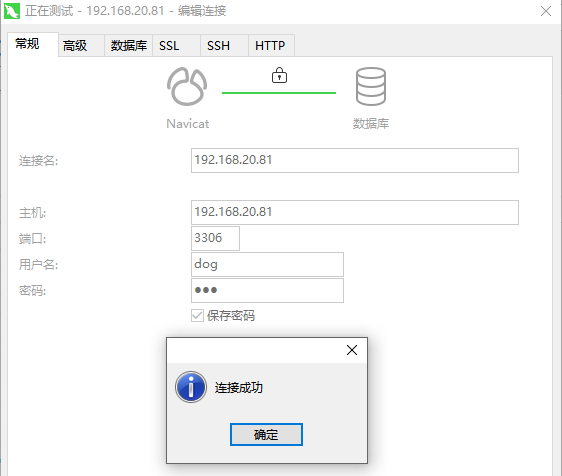

The pem file is fixed after the database is installed. copy can be used permanently after it reaches the client without being affected by database changes.
Are pem files and ssl connections related on the server side?
#Move all pem files away [root@mysql1 mydata1]# mkdir pemdefault [root@mysql1 mydata1]# mv *.pem pemdefault/ [root@mysql1 mydata1]# ll *.pem ls: cannot access *.pem: No such file or directory # Test client connection [root@mysql2 ~]# mysql -h mysql1 -udog -pdog --ssl-cert=/home/mysql/client-cert.pem --ssl-key=/home/mysql/client-key.pem mysql: [Warning] Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 35 Server version: 8.0.16 MySQL Community Server - GPL Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
Explain that deletion of the *. pem file on the server side does not affect the SSL connection on the client side.
However, if the database is restarted, the server will regenerate the new pem file.
[root@mysql1 mydata1]# ll *.pem -rw------- 1 mysql mysql 1680 Jul 14 10:24 ca-key.pem -rw-r--r-- 1 mysql mysql 1112 Jul 14 10:24 ca.pem -rw-r--r-- 1 mysql mysql 1112 Jul 14 10:24 client-cert.pem -rw------- 1 mysql mysql 1680 Jul 14 10:24 client-key.pem -rw------- 1 mysql mysql 1676 Jul 14 10:24 private_key.pem -rw-r--r-- 1 mysql mysql 452 Jul 14 10:24 public_key.pem -rw-r--r-- 1 mysql mysql 1112 Jul 14 10:24 server-cert.pem -rw------- 1 mysql mysql 1680 Jul 14 10:24 server-key.pem
At this point, the remote connection will report a mistake.
[root@mysql2 ~]# mysql -h mysql1 -udog -pdog --ssl-cert=/home/mysql/client-cert.pem --ssl-key=/home/mysql/client-key.pem mysql: [Warning] Using a password on the command line interface can be insecure. ERROR 2026 (HY000): SSL connection error: error:1409441B:SSL routines:ssl3_read_bytes:tlsv1 alert decrypt error
Recopy the PEM file to the client and reconnect the test
#copy pem file [root@mysql1 mydata1]# scp client-cert.pem mysql2:/home/mysql client-cert.pem 100% 1112 1.4MB/s 00:00 [root@mysql1 mydata1]# scp client-key.pem mysql2:/home/mysql client-key.pem #Connection recovery [root@mysql2 ~]# mysql -h mysql1 -udog -pdog --ssl-cert=/home/mysql/client-cert.pem --ssl-key=/home/mysql/client-key.pem mysql: [Warning] Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 19 Server version: 8.0.16 MySQL Community Server - GPL Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
So in conclusion, although pem ssl remote connection does not need to be verified by pem file matching on the server side, it is still unable to delete pem files on the server side, because restarting the database after deletion will regenerate new pem files, which will lead to the failure of remote connection and need to copy again.