Catalog
2. Differences between firewalld and iptables
3. The concept of firewalld region
Fourth, firewalld firewall predefined nine zones
5. Firewall Data Processing Process
6. Configuration method of Firewall
7. Configuration method of firewalld
8. Common firewall-cmd command options
1. Overview of firewalld
firewalldfirewall Is the default firewall management tool for Centos7 system, replacing the previous iptables firewall, also works in the network layer, belongs to the packet filtering firewall
firewalld and iptables They are tools used to manage firewalls (in the user state) to define the various rule functions of the firewall, and their internal structure points to the netfilter network filtering subsystem (in the kernel state) to implement the packet filtering firewall function.
firewalld provides dynamic firewall management tools that support network connections defined by network zones and security levels of interfaces. It supports IPV4, IPv6 firewall settings, and Ethernet bridges (which may be used in some advanced services, such as cloud computing), and has two configuration modes: runtime configuration and permanent configuration.
2. Differences between firewalld and iptables
1,
iptables are mainly based on interfaces to set rules to judge the security of the network.
Firealld is region-based and sets different rules according to different regions to ensure the security of the network. Similar to hardware firewall settings.
2,
Iptables store configuration in/etc/sysconfig/iptables
Firewalld stores the configuration in various XML files in / etc/firewalld/ (preferential loading) and / usr/lib/firewalld/ (default configuration file).
3,
Using iptables for each individual change means clearing all old rules and reading all new rules from/etc/sysconfig/iptables.
With firewalld, no new rules are created, just the differences in the rules are run. Firealld can therefore change settings during runtime without losing existing connections.
4,
iptables firewall type is static firewall
firewalld firewall type is dynamic firewall
3. The concept of firewalld region
The firewalld firewall divides all network traffic into zones to simplify management. Then, according to the source IP address of the packet or the incoming network interface, the traffic is transferred to the corresponding area. Each zone defines its own list of ports and services to open or close.
Fourth, firewalld firewall predefined nine zones
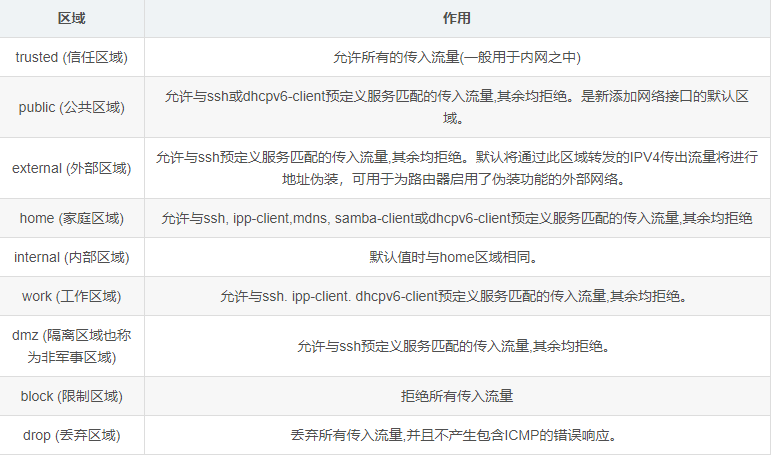
The security level of the final zone depends on the rules set by the administrator in that zone.
Regions are like security gates that enter the host. Each region has rules with varying degrees of restriction that allow only traffic that meets the rules to enter. One or more zones can be used depending on the size of the network, but any active zone requires at least one associated source address or interface.
By default, the public zone is the default zone and contains all interfaces (network cards).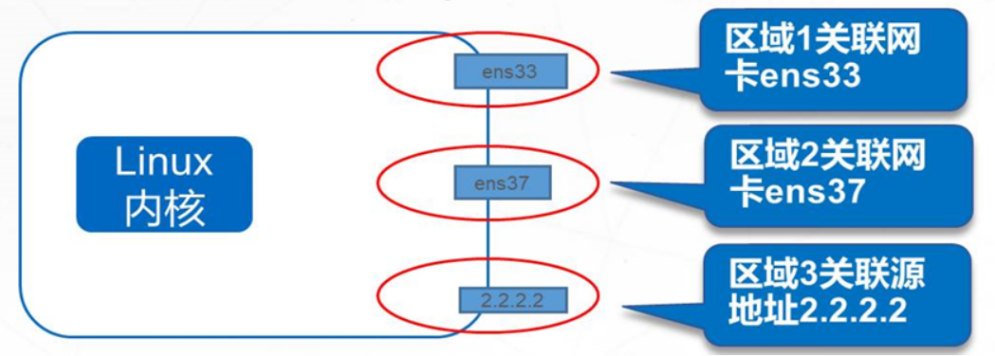
5. Firewall Data Processing Process
Check the source address of the data source
- If the source address is associated with a particular region, the rules specified in that region are enforced
- If the source address is not associated to a particular zone, use the zone passed in to the network interface and enforce the rules specified in that zone
- If the network interface is not associated to a particular zone, the default zone is used and the rules specified in that zone are enforced (generally, the rules for the default zone are deny all)
6. Configuration method of Firewall
1. Runtime Configuration
- Effective in real time until Firewall restarts or reloads the configuration
- Do not interrupt existing connections
- Cannot modify service configuration
2. Permanent Configuration
- Not immediately effective unless Firewall restarts or reloads the configuration
- Disconnect existing connections
- Service configuration can be modified
7. Configuration method of firewalld
1. Use firewall-cmd command line tools. (Common)
2. Use firewall-config graphics tools.
3. Write a configuration file in/etc/firewalld/systemctl start firewalld.service
8. Common firewall-cmd command options
(1) Common commands
--get-default-zone :Show current default zone --set-default-zone=<zone> :Set Default Zone --get-active-zones :Show the area currently in use and its corresponding network card interface --get-zones :Show all available areas --get-zone-of-interface=<interface> :Displays the region for the specified interface binding --zone=<zone> --add-interface=<interface> :Bind region for specified interface --zone=<zone> --change-interface=<interface> :Change the bound network interface for the specified zone --zone=<zone> --remove-interface=<interface> :Remove bound network interfaces for the specified zone --get-zone-of-source=<source> [/<mask>] :Show the area of the specified source address binding --zone=<zone> -add-source=<source> [/<mask>] :Bind region for specified source address --zone=<zone> -change-source=<source> [/<mask>] :Change the source address of the binding for the specified zone --zone=<zone> -remove-source=<source> [/<mask>] :Remove the source address of the binding for the specified zone --list-all-zones :Show all areas and their rules [--zone=<zone>] --list-al1 :Show all rules for all specified zones,ellipsis--zone=<zone>Only for the default zone [--zone=<zone>] --list-services :Displays all services allowed in a specified area [--zone=<zone>] --add-service=<service> :Allow access to a service for a specified locale [--zone=<zone>] --remove-service=<service> :Delete a service that has been set to allow access in the specified region [--zone=<zone>] --list-ports :Displays all port numbers allowed in the specified zone [--zone=<zone>] --add-port=<portid> [-<portid>]/<protocol> :Allow access to a specified locale/A section of port number(Include protocol name) [--zone=<zone>] --remove-port=<portid> [-<portid>]/<protocol> :Delete the allowed access port number already set in the specified region(Include protocol name) [--zone=<zone>] --list-icmp-blocks :Displays all access denied within a specified area ICMP type [--zone=<zone>] --add-icmp-block=<icmptype> :Deny access to an item for a specified locale ICMP type [--zone=<zone>] --remove-icmp-block=<icmptype> :Delete an item that has been set up in the specified region to deny access ICMP type firewall-cmd --get-icmptypes :Show all ICMP type
(2) Regional Management
(1)Show default areas in the current system firewall-cmd --get-default-zone (2)Show all rules for the default zone firewall-cmd --list-all (3)Show the area currently in use and its corresponding network card interface firewall-cmd --get-active-zones (4)Set Default Zone firewall-cmd --set-default-zone=home firewall-cmd --get-default-zone
(3) Service management
(1)View all services allowed in the default zone firewall-cmd --list-service (2)Add to httpd Service to public region firewall-cmd --add-service=http --zone=public (3)See public Zone Configured Rules firewall-cmd --list-all --zone=public (4)delete public Regional httpd service firewall-cmd --remove-service=http --zone=public (5)Add at the same time httpd,https Service to Default Zone,Set to Permanent Effectiveness firewall-cmd --add-service=http --add-service=https --permanent firewall-cmd --reload firewall-cmd --list-al1 #Add the use of the --permanent option to indicate that the settings are permanently valid and that you need to restart the firewalld service or execute the firewall-cmd --reload command Firewall rules will not take effect until they are reloaded. Without this option,Represents the rule used to set the runtime,But these rules are in the system or firewalld Configuration will fail when service is restarted or stopped. --runtime-to-permanent :Write the current runtime configuration to the rules configuration file,Make it a permanent configuration.
(4) Port management
(1)allow TCP Port 443 to internal region firewall-cmd --zone=internal --add-port=443/tcp firewall-cmd --list-all --zone=internal (2)from internal Region will TCP 443 port removal for firewall-cmd --zone=internal --remove-port=443/tcp (3)allow UDP 2048-2050 Port to Default Zone firewall-cmd --add-port=2048-2050/udp firewall-cmd --list-all