Springboot integrates RabbitMQ on serialization and deserialization during object transmission
In the process of using RabbitMQ as message middleware in Springboot project, sometimes we use java objects as transmitted messages. By default, java objects are allowed to be used as transmitted messages, but there are strict conditions:
1. The java objects in the producer and consumer must be the same;
2. The package names in java objects must also be consistent.
If the developer and consumer belong to the same project in the project, there is no problem. If the developer and consumer belong to different projects, the second condition is more troublesome. Of course, there are solutions.
- For example, entity classes are introduced into producer and consumer projects as basic packages, and so on.
- By converting the java object to a json string in the producer, the json string is converted back to the java object in the consumer. This method has many disadvantages. Firstly, it needs to increase the amount of code (mutual conversion), and it needs to increase the converted code for different objects, such as Jackson translator.
- producer
/**
* Test transmission object message
* @return
*/
@GetMapping("/sendDirectMessage2")
public String sendDirectMessage2() {
Person person = new Person();
person.setId(String.valueOf(UUID.randomUUID()));
person.setName("zhangsan");
//Serialize the object as a json string
rabbitTemplate.setMessageConverter(new Jackson2JsonMessageConverter());
//Send the message with the binding key value: TestDirectRouting to the switch TestDirectExchange
rabbitTemplate.convertAndSend("testDirectExchange", "testDirectRouting2", person);
return "ok";
}
- Consumer end
package com.yemuxia.config;
import org.springframework.amqp.rabbit.annotation.RabbitListenerConfigurer;
import org.springframework.amqp.rabbit.listener.RabbitListenerEndpointRegistrar;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.messaging.converter.MappingJackson2MessageConverter;
import org.springframework.messaging.handler.annotation.support.DefaultMessageHandlerMethodFactory;
import org.springframework.messaging.handler.annotation.support.MessageHandlerMethodFactory;
/**
* @author Shi Kaiqiang
* @date 2021/12/23 21:11
* @desc
**/
@Configuration
public class RabbitConfig implements RabbitListenerConfigurer {
// You can deserialize json strings into objects
@Override
public void configureRabbitListeners(RabbitListenerEndpointRegistrar rabbitListenerEndpointRegistrar) {
rabbitListenerEndpointRegistrar.setMessageHandlerMethodFactory(messageHandlerMethodFactory());
}
@Bean
MessageHandlerMethodFactory messageHandlerMethodFactory(){
DefaultMessageHandlerMethodFactory messageHandlerMethodFactory = new DefaultMessageHandlerMethodFactory();
messageHandlerMethodFactory.setMessageConverter(mappingJackson2MessageConverter());
return messageHandlerMethodFactory;
}
@Bean
public MappingJackson2MessageConverter mappingJackson2MessageConverter(){
return new MappingJackson2MessageConverter();
}
}
Underlying principle of HashMap
data structure
Array + linked list + (red black tree JDK > = 8)
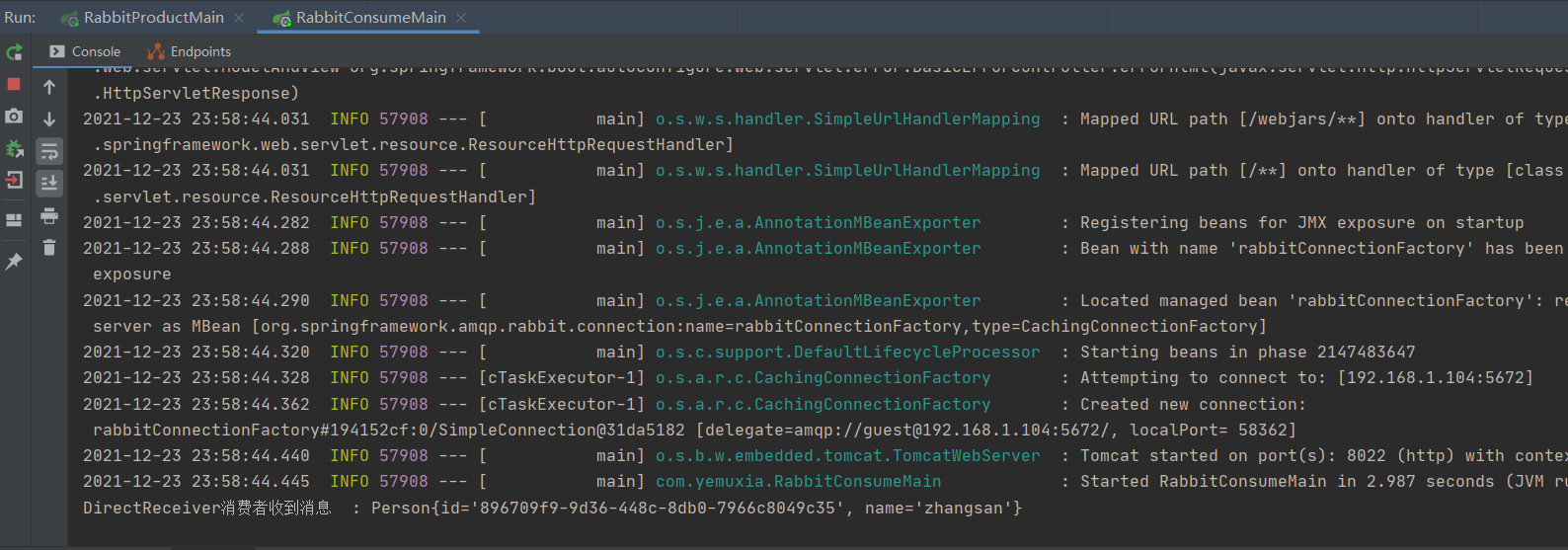
The bottom layer of Map is implemented through hash table. Let's see what hash table is first.
JDK1. Before 8, the bottom layer of the hash table was implemented by array + linked list, that is, the linked list was used to deal with conflicts, and the elements of the same hash value were stored in a linked list. However, when there are many elements in a bucket, that is, there are many elements with equal hash values, the efficiency of searching by key value in turn is low.
JDK1. In 8, the hash table storage is realized by array + linked list + red black tree. When the length of the linked list exceeds the threshold (8), the linked list is converted into a red black tree, which greatly reduces the search time.
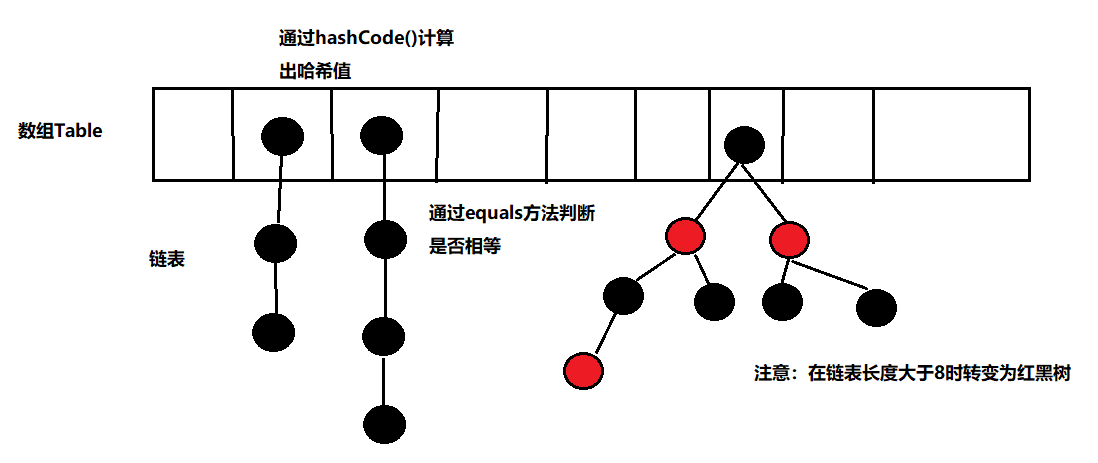
explain:
1. When storing key value pairs, first calculate the hash value of key (K) through hashCode(), and then query in the array. If not, save it.
2. However, if the same hash value is found, then call the equals method to determine whether their values are the same. Only when the above two conditions are met can it be recognized as the same data. Therefore, the hashCode() and equals() methods are rewritten in the wrapper class in Java.
JDK1.8. The red black tree is introduced to greatly optimize the performance of HashMap, which is determined according to the hashCode and equals methods of the object. If we store custom objects in the collection, to ensure their uniqueness, we must duplicate the hashCode and equals methods to establish a comparison method belonging to the current object.
https://www.cnblogs.com/szrs/p/12164982.html
https://baijiahao.baidu.com/s?id=1665667572592680093&wfr=spider&for=pc
https://blog.csdn.net/yemuxiaweiliang/article/details/121050857
RPC remote call
RPC refers to Remote Procedure Call (English: Remote Procedure Call, abbreviated as RPC). It is a computer communication protocol. It is located in the fifth layer of OSI architecture: session layer, and also the fourth layer (application layer) of TCP / IP protocol stack. Below it is TCP / IP protocol.
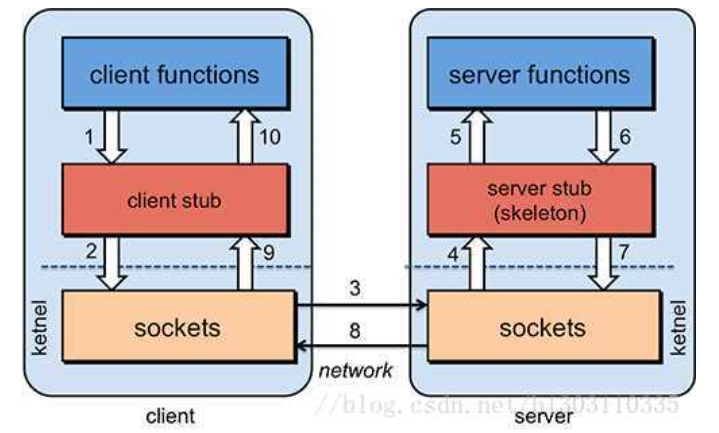
In other words, two servers A and B, one application deployed on server A, want to call the functions / methods provided by the application on server B. because they are not in the same memory space, they cannot be called directly. They need to express the calling semantics and convey the calling data through the network
General steps for realizing remote communication
-
To solve the problem of communication, we mainly establish a TCP connection between the client and the server. All the exchanged data of remote procedure calls are transmitted in this connection. The connection can be an on-demand connection, which is broken after the call, or a long connection. Multiple remote procedure calls share the same connection.
-
To solve the problem of addressing, that is, how does the application on server A tell the underlying RPC framework, How to connect to the B server (such as host or IP address) and specific port, and what is the name of the method to complete the call. For example, for RPC based on Web service protocol stack, you need to provide an endpoint URI or find it from UDDI service. If it is RMI call, you also need an RMI Registry to register the address of the service.
-
When an application on server A initiates A remote procedure call, the parameters of the method need to be transmitted to server B through the underlying network protocol such as TCP. Because the network protocol is based on binary, the values of the parameters in memory should be serialized into binary form, That is, Serialize or marshal, which sends the serialized binary to the B server through addressing and transmission.
-
After receiving the request, the B server needs to deserialize the parameters (the reverse operation of serialization), restore them to the expression in memory, and then find the corresponding method (part of the addressing) to call locally, and then get the return value.
-
The return value should also be sent back to the application on server A, and it should also be sent through serialization. After receiving it, server A will deserialize it, restore it to the expression in memory, and give it to the application on server A
Simple implementation of rpc:
https://www.jianshu.com/p/5b90a4e70783
mysql master-slave replication for database synchronization
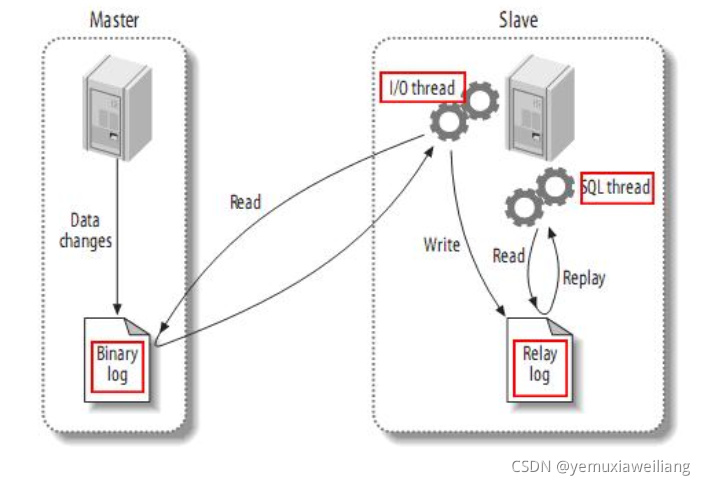
The master-slave architecture of MySQL services is generally implemented through binlog log files. That is, open binlog on the main service to record each step of database operation, and then there will be an IO thread on the slave service, which is responsible for establishing a TCP connection with the main service and requesting the main service to transmit binlog. At this time, there will be an IO dump thread on the master library, which is responsible for transmitting the binlog log to the IO thread of the slave library through this TCP connection. Then, the IO thread from the service will write the read binlog data to its own relay log file. Then another SQL thread from the service will read the contents of the relay log and repeat the operation to restore the data. The read-write separation configuration we usually do for MySQL must be built based on the master-slave architecture.
MySQL binlog can be used not only for master-slave synchronization, but also for cache data synchronization and other scenarios.
For example, Canal can simulate a slave node, initiate binlog synchronization to MySQL, and then land the data to Redis, Kafka and other components to realize real-time data flow.
When building a master-slave cluster, there are two necessary requirements:
Both MySQL versions must be the same. At least the version of the master service is required to be lower than that of the slave service
The time between the two nodes needs to be synchronized.
The article can be referred to
https://blog.csdn.net/yemuxiaweiliang/article/details/121632878
Life cycle of java classes and objects
https://blog.csdn.net/yanliguoyifang/article/details/80964237
https://www.jianshu.com/p/af1edcaa3e89
The difference between socket connection and http connection
-
HTTP protocol: application layer protocol. HTTP protocol is based on TCP connection. It mainly solves how to package data
-
Socket encapsulates the TCP/IP protocol. Socket itself is not a protocol, but an API. Only through socket can we use the TCP/IP protocol.
TCP protocol: corresponds to the transport layer, IP protocol: corresponds to the network layer. TCP and IP protocols mainly solve how data is transmitted in the network;
-
http connection: http connection is the so-called short connection, that is, the client sends a request to the server, and the connection will be broken after the server responds;
-
Socket connection: socket connection is the so-called long connection. Theoretically, once the connection between the client and the server is established, it will not be broken actively; However, due to various environmental factors, the connection may be disconnected, such as server or client host down, network failure, or no data transmission between the two for a long time, the network firewall may disconnect the connection to release network resources. Therefore, when there is no data transmission in a socket connection, you need to send a heartbeat message in order to maintain the connection ~ ~ the specific heartbeat message format is defined by the developer.