Summary of Linux polkit rights raising
As soon as I was about to take my annual leave, I received a regulatory vulnerability alert - "pkexec program in Linux Polkit has a privilege escalation vulnerability (vulnerability number: CVE-2021-4034). Pkexec application is a pre installed tool for Linux system, and the vulnerability affects mainstream Linux distributions such as Ubuntu, Debian, Fedora and CentOS...", ah, it is the time of the Winter Olympic network protection, and all parties are sensitive. Please study it quickly. See details for details Green alliance's CERT emergency notice
1. Vulnerability overview
1 On June 26, Green Alliance Technology CERT Monitored Qualys The research team publicly disclosed Polkit of pkexec A privilege escalation vulnerability was found in( CVE-2021-4034) ,Also known as PwnKit. The vulnerability is due to pkexec The call parameters cannot be handled correctly, so that the environment variable is executed as a command. An attacker with arbitrary user rights can exploit this vulnerability by modifying the environment variable under the default configuration, so as to obtain the information of the affected host root jurisdiction. Details and of the current vulnerability PoC It has been made public. Please take measures to protect it as soon as possible. Polkit(PolicyKit)Is class Unix An application level tool set in the system realizes the communication between processes with different priorities by defining and reviewing permission rules. pkexec yes Polkit Part of the open source application framework, which enables authorized non privileged users to execute commands as privileged users according to defined policies.
2. Scope of influence
Affected version 2009 All published since May Polkit edition Note: Polkit Pre installed in CentOS,Ubuntu,Debian,Redhat,Fedora,Gentoo,Mageia Wait for multiple Linux On the distribution, all exist Polkit of Linux All systems are affected. Unaffected version CentOS: CentOS 6: polkit-0.96-11.el6_10.2 CentOS 7: polkit-0.112-26.el7_9.1 CentOS 8.0: polkit-0.115-13.el8_5.1 CentOS 8.2: polkit-0.115-11.el8_2.2 CentOS 8.4: polkit-0.115-11.el8_4.2 Ubuntu: Ubuntu 14.04 ESM: policykit-1-0.105-4ubuntu3.14.04.6+esm1 Ubuntu 16.04 ESM: policykit-1-0.105-14.1ubuntu0.5+esm1 Ubuntu 18.04 LTS: policykit-1-0.105-20ubuntu0.18.04.6 Ubuntu 20.04 LTS: policykit-1-0.105-26ubuntu1.2 Ubuntu 21.10: policykit-1-0.105-31ubuntu0.1 Debain: Debain stretch: policykit-1 0.105-18+deb9u2 Debain buster: policykit-1 0.105-25+deb10u1 Debain bullseye: policykit-1 0.105-31+deb11u1 Debain bookworm,bullseye: policykit-1 0.105-31.1
3. Vulnerability detection
Linux System users can view Polkit Version to determine whether the current system is within the affected range, mainstream Linux The release commands are as follows: CentOS: rpm -qa polkit Ubuntu: dpkg -l policykit-1
4. Vulnerability verification
Seeing the evaluation of the vulnerability, the CVSS score is 7.8. The vulnerability CVE-2021-4034 exposed this time is a local right lifting vulnerability, which has a large impact and wide spread. The mainstream Linux operating systems are affected. It immediately reminds me of the sudo local right lifting vulnerability exposed in January 2021. When it was exposed, it also caused a great shock. ***
1) . verify CVE-2021-4034 (Linux Polkit authorization)
Verify with a Centos 7 VM virtual machine on hand. The version information is as follows,
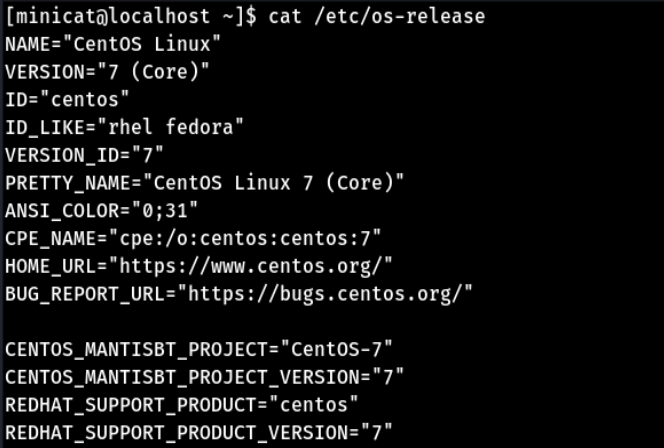
View the version information of polkit, rpm -qa polkit
See Github for more information on POC released online, polkit rights poc , after compilation, execute the poc code, as shown in the figure
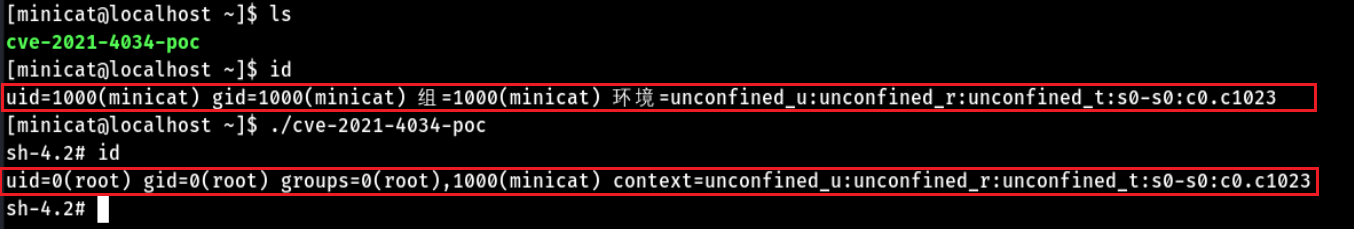
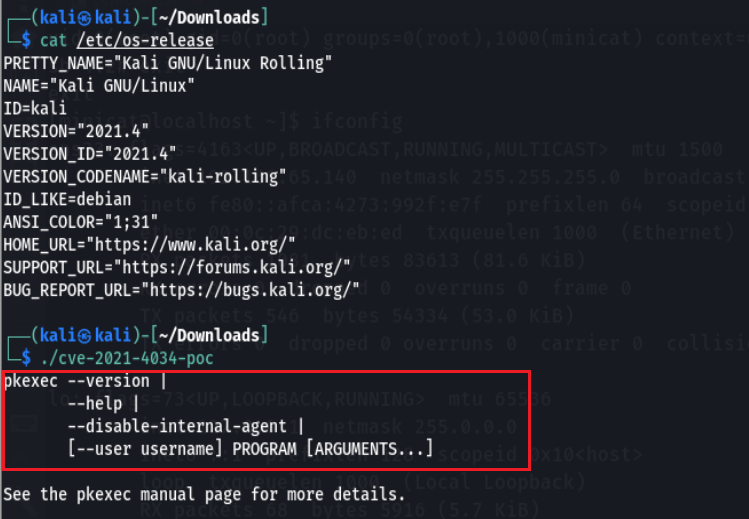
Got root permission. When the same poc code is tried in Kali on 2021-04, it is found that it has been repaired and the right cannot be raised, as shown in the figure:
5. Vulnerability repair
Temporary mitigation measures, removal pkexec of suid Bit, chmod 0755 /usr/bin/pkexec
Retry the above poc code, and the authorization lifting fails, indicating that the permission is missing, as shown in the figure
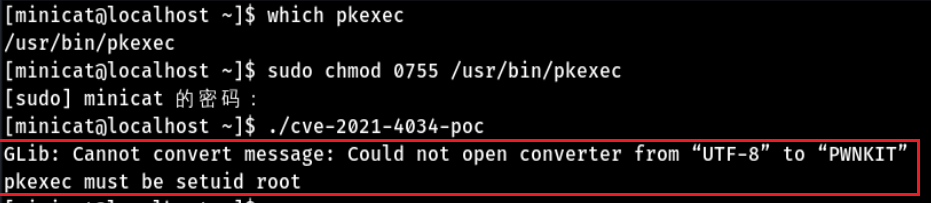
So far, the mainstream Linux distributions have provided the upgrade package of polkit tool. Directly upgrading to the latest version can effectively fix this vulnerability.
summary
The vulnerability is relatively simple to exploit and has a wide range of impact. Most Linux versions are affected. Therefore, I thought of sudo right raising vulnerability [CVE-2021-3156] that broke out in April 2021, which is a buffer overflow vulnerability.
Enter a negative number after sudo -u#-1 whoami # number, resulting in overflow. See sudo rights At that time, it also affected a large number of Linux distributions, which is similar to the current polkit components.
However, sudo's right raising vulnerability requires high requirements. It can only be successfully implemented if the following three conditions are met at the same time:
1. Sudo Version less than 1.8.28 2. Know the user's password (current user, not root (password for) 3. User in sudo In the permission list 4. existence ALL Compound restriction logic of keywords