As the mainstream SDN controller at present, ODL has been used by major manufacturers. The SSL secure connection between ODL and OVS is rarely fully shared on domestic and foreign networks. Based on the practice of SSL secure connection (active connection and passive connection) between ODL and OVS, this paper comprehensively expounds the setting of SSL secure connection between ODL and OVS.
The secure connection between ODL and ovs takes ovs equipment as the connection object, and the controller connects ovs mainly in two ways: 1. Active connection; 2. Passive connection. In addition, there are two ways to configure SSL connection: 1. Manually generate pem format Certificate (used by ovs client), and then convert it to jks format certificate supported by ODL (JDK platform); 2. Manually generate jks Certificate (used by ODL), and then convert it to pem format Certificate (used by ovs). The following verification is performed according to the configured SSL connection mode 2. No matter how the ovs is connected based on the above controller, the controller side needs to be modified according to different configurations.
The configuration steps are mainly divided into certificate generation (including OVS end use certificate and controller end use certificate), OVS device end configuration certificate and ODL controller end configuration certificate.
1.1 generate self signed certificate at ODL end
Use Keytool tool to generate a self signed certificate library ODL JKS (including private key and public key certificate information), - alias and - storepass need to be consistent with the configuration on the controller side.
_# keytool -genkey -keyalg RSA -alias controller -keystore odl.jks -storepass 111111 -validity 365 -keysize 2048_
Add ODL JKS is converted to ODL in two steps PEM file: ODL jks→odl.p12→odl.pem (for convenience, it is recommended to set the password to be consistent with the odl.jks password 111111)
_# keytool -importkeystore -srckeystore odl.jks -destkeystore odl.p12 -srcstoretype jks -deststoretype pkcs12_ _# openssl pkcs12 -in odl.p12 -out odl.pem_
odl. The content of PEM is as follows:
_# cat odl.pem_ Bag Attributes friendlyName: controller localKeyID: 54 69 6D 65 20 31 36 34 32 31 32 35 34 31 31 38 33 33 Key Attributes: <No Attributes> -----BEGIN ENCRYPTED PRIVATE KEY----- MIIFHDBOBgkqhkiG9w0BBQ0wQTApBgkqhkiG9w0BBQwwHAQICvDsQcvStsACAggA MAwGCCqGSIb3DQIJBQAwFAYIKoZIhvcNAwcECOcPvR2phfFzBIIEyM5QRmjjmD0I YcuPocLrPGDJe/x3RV77fessvCEtEWsYqFmW6Xi9SdoG6y0zDgEEpY+jCM+SOruC IGk7UIu//DBVj+JcaSEu0n8B/rGGuqmU1Ea52sqDW8xxOk0llapYi1P6VX0LgY/H QJCM/CvArrg/EO5seV6i9iXpOpX6I7yJTfXfMYMP+zncHJ/7AesRSkEA9fBow7tq d00onsea6HL1nVX8uzyxzHuBsittsOQ5RIyqC+Gpny2mIxkqkXga1XSs2miVspy/ QcxYYts4F8IgA9N5fgenPsCR7K0wgqkO30W6pKMdL2YDCauhJ+E4ylwVaAqwUHZV btLQKORAps1DKrNV7xpXkJ/Q9BUTbAaqSHPn5mfdsD6cxSM8OEenVdZFmkSWtZNa ET39e5JfhesPINq/Lx6jl58EiP7y1MgYXN9zsuimoJAVooJ5TfcgeqKZetPzPEop i0q30dfHQNpJsNkfqnWIlifXMVcGztbpdWSNKs70B8Dr+3wFco3th5EGtSgfVgnb WFSDdOsvaOP8ljfRlCr6Zs6p6BYoPlIQTIO9lfTz1JPyAE7orIogXXbSsZ1saDPf nkhzhRP4FSfYbYPeWBSzFcaPOmXSilarEfa7/CROJRn1HTJrDrZZYrQr7Gj/W5Gw yQbNHEzP0G2LKFtUCBBCrAsr7V6owh5YvrOMriO+SZcsHnbHwl9jSI0AXe97XfkT qgULx/3zc9G6D0tUwCst5lUo3DYnx8WtbXzcMwrCmTKkpE9pISu1UJytBiz493XD nOM+MoKZWIyOqcDe2Ac7km6Ybo2wLuA6kIxwYgun6NJl9mAgqJ/+T0itvuOB3PD/ FeqnnRq5eZlSmo3PL5ycKKja0z6z9ylaIWDRZYsPFNBt4jqCa9hizC+VioiuGECJ Sqf2JH1X5TBhU41Naoe3vur6rpBydkPDj33qELSG2q+90i2M9PT/8akAm0TWTs/u UwJjMVfVGp5jgbYAAjuyrtkMioFuMlJJg9f53elCttx2Zmaotu3d3I1gh1tTP9ON bF9Ls5QnqW3Ujkr3qmLUeE2EE3M+uPuoA4GtEPeMili+NeY1WKXORATy2q/d/Aus 31i51k79cZvgL39r/G/DOHkw/xRQSonWRCadNpA12FJ+GxJ2OBHkdtrQ2RPycJ5c 9EvqiY0IGfY1cmY3tgXl925Rxc+EtvMLJqoi8M9WeuwEVo2tuU9DVdwRgLFoQnnP xCxwRjln75mxAyxUP/dZ79Ex3+CmsZj+OSrM78tKNnsjAGrV5XSPZwnY5+I9o5lw 9dIJL49ROktjQgKZW5SIsNK2zavJuVVP0RgY6nxEMZtR1xwxytCMKNtSe7i1LQST qbYSaBEeHnjGWYa8JUemyRsegaNkrhWOium5HsmYi8UGQ+aytGIM0PYPe8SVNwol YKxbg81bzFmw4I/Kqgwzdq+fGp/+NOEqHmsWJi/S5UdA0UwKG68qTglVWL3+mDrT rVwHD7F96GMkfbp2+w+RaASVcNs6itl/rEI9RkdZA+9uX7wtp0GQc879yJA+MBkS i/fsmxvwJ24RMRA9fjuMCHt8ma5lmC0OPXLhthh7T5NSZYffHTSbLQHSQCg/raN6 cytEzo9X78+7H5ky4JDH/A== -----END ENCRYPTED PRIVATE KEY----- Bag Attributes friendlyName: controller localKeyID: 54 69 6D 65 20 31 36 34 32 31 32 35 34 31 31 38 33 33 subject=C = CN, ST = Hubei, L = Wuhan, O = test, OU = sdn, CN = Jun Wu issuer=C = CN, ST = Hubei, L = Wuhan, O = test, OU = sdn, CN = Jun Wu -----BEGIN CERTIFICATE----- MIIDXzCCAkegAwIBAgIETFbI0TANBgkqhkiG9w0BAQsFADBgMQswCQYDVQQGEwJD TjEOMAwGA1UECBMFSHViZWkxDjAMBgNVBAcTBVd1aGFuMRIwEAYDVQQKEwlmaWJl cmhvbWUxDDAKBgNVBAsTA3NkbjEPMA0GA1UEAxMGSnVuIFd1MB4XDTIyMDExNDAx NTQ1OFoXDTIzMDExNDAxNTQ1OFowYDELMAkGA1UEBhMCQ04xDjAMBgNVBAgTBUh1 YmVpMQ4wDAYDVQQHEwVXdWhhbjESMBAGA1UEChMJZmliZXJob21lMQwwCgYDVQQL EwNzZG4xDzANBgNVBAMTBkp1biBXdTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC AQoCggEBAI+M3NJzXklDYtHMy0bs4iIVIkHwQHHCch0bOcNpFmZXEEn+F9aTAEvL TNh10xSJoaFtGeAMZaOU1rU+woeXz+3sZV+WdoExnJXiuB6w5kzJTfNlAFNg41T0 SizgSvxmbdwl5C2TKpj7vyQPmNoriznwOdF7bQjGKTEPuJTALqP+zmNcwGqi47ll Ni/z5I4jwyjhfBUdGqUl3it6D4NZ3Y+tTknM7RJD2U5Ush5V0oWWM/CHEjVJNVbp LnfzsRFG5TggnUDTAiP17FWqRllqpIqtxDDtRdnx4Cv8r8g4jOc5/rVx6EcuMtNU BA7OZxploDONOROwqfm7iQ7wBgiyOuMCAwEAAaMhMB8wHQYDVR0OBBYEFCDdbV1G KtmPJqGrDVb4fKz9NnRUMA0GCSqGSIb3DQEBCwUAA4IBAQAVCVTDcbpAghr+mgtK wb7u+MelO+EymsbGKgNEYFMsqRnyRkbbWaUCMdDDuC9r/Nq0rS4adNMRXUpb3WYY +KF1Ub7AaiiTAMzNj3lt22ztpYoP05kkQPSj65DCmWBduQHrPJXf/gdW3pPLEexB u8qJxHRHiivhQFeusKhGd+bi3EMlAlYrO66kXiprt2VCbBBB2Zbdm93pK1yyckmz fkEQkGTnirni9axs4eZiyjPNRJlGwzwzpZ69qlwknZDPCKfxDtGp7GOFRKKUQVhf 3KTYyH2adJY7Fv0D1aGiKb1rYwpzfFKsjw+PrH1tSMcA60RH7SyM+9aVOE5wG41K ibLf -----END CERTIFICATE-----
Next, we need to create a cacert PEM file is used for OVS, and its content is ODL The certificate part of PEM, from "Bag Attributes" in the middle to the last part:
_# cat cacert.pem_ Bag Attributes friendlyName: controller localKeyID: 54 69 6D 65 20 31 36 34 32 31 32 35 34 31 31 38 33 33 subject=C = CN, ST = Hubei, L = Wuhan, O = test, OU = sdn, CN = Jun Wu issuer=C = CN, ST = Hubei, L = Wuhan, O = test, OU = sdn, CN = Jun Wu -----BEGIN CERTIFICATE----- MIIDXzCCAkegAwIBAgIETFbI0TANBgkqhkiG9w0BAQsFADBgMQswCQYDVQQGEwJD TjEOMAwGA1UECBMFSHViZWkxDjAMBgNVBAcTBVd1aGFuMRIwEAYDVQQKEwlmaWJl cmhvbWUxDDAKBgNVBAsTA3NkbjEPMA0GA1UEAxMGSnVuIFd1MB4XDTIyMDExNDAx NTQ1OFoXDTIzMDExNDAxNTQ1OFowYDELMAkGA1UEBhMCQ04xDjAMBgNVBAgTBUh1 YmVpMQ4wDAYDVQQHEwVXdWhhbjESMBAGA1UEChMJZmliZXJob21lMQwwCgYDVQQL EwNzZG4xDzANBgNVBAMTBkp1biBXdTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC AQoCggEBAI+M3NJzXklDYtHMy0bs4iIVIkHwQHHCch0bOcNpFmZXEEn+F9aTAEvL TNh10xSJoaFtGeAMZaOU1rU+woeXz+3sZV+WdoExnJXiuB6w5kzJTfNlAFNg41T0 SizgSvxmbdwl5C2TKpj7vyQPmNoriznwOdF7bQjGKTEPuJTALqP+zmNcwGqi47ll Ni/z5I4jwyjhfBUdGqUl3it6D4NZ3Y+tTknM7RJD2U5Ush5V0oWWM/CHEjVJNVbp LnfzsRFG5TggnUDTAiP17FWqRllqpIqtxDDtRdnx4Cv8r8g4jOc5/rVx6EcuMtNU BA7OZxploDONOROwqfm7iQ7wBgiyOuMCAwEAAaMhMB8wHQYDVR0OBBYEFCDdbV1G KtmPJqGrDVb4fKz9NnRUMA0GCSqGSIb3DQEBCwUAA4IBAQAVCVTDcbpAghr+mgtK wb7u+MelO+EymsbGKgNEYFMsqRnyRkbbWaUCMdDDuC9r/Nq0rS4adNMRXUpb3WYY +KF1Ub7AaiiTAMzNj3lt22ztpYoP05kkQPSj65DCmWBduQHrPJXf/gdW3pPLEexB u8qJxHRHiivhQFeusKhGd+bi3EMlAlYrO66kXiprt2VCbBBB2Zbdm93pK1yyckmz fkEQkGTnirni9axs4eZiyjPNRJlGwzwzpZ69qlwknZDPCKfxDtGp7GOFRKKUQVhf 3KTYyH2adJY7Fv0D1aGiKb1rYwpzfFKsjw+PrH1tSMcA60RH7SyM+9aVOE5wG41K ibLf -----END CERTIFICATE-----
Please note: two intermediate files ODL P12 and ODL PEM is useless and should be deleted for security reasons.
1.2 copy odl certificate to OVS
Put cacert The certificate in the directory named / vspec.ovm can be copied to the directory named / vspec.ovm in which the certificate of the authority is stored (the certificate in the directory named / vspec.ovm can be used to back up).
root@root12-virtual-machine:/var/lib/openvswitch/pki/controllerca# cat cacert.pem Bag Attributes friendlyName: controller localKeyID: 54 69 6D 65 20 31 36 34 32 31 32 35 34 31 31 38 33 33 subject=C = CN, ST = Hubei, L = Wuhan, O = test, OU = sdn, CN = Jun Wu issuer=C = CN, ST = Hubei, L = Wuhan, O = test, OU = sdn, CN = Jun Wu -----BEGIN CERTIFICATE----- MIIDXzCCAkegAwIBAgIETFbI0TANBgkqhkiG9w0BAQsFADBgMQswCQYDVQQGEwJD TjEOMAwGA1UECBMFSHViZWkxDjAMBgNVBAcTBVd1aGFuMRIwEAYDVQQKEwlmaWJl cmhvbWUxDDAKBgNVBAsTA3NkbjEPMA0GA1UEAxMGSnVuIFd1MB4XDTIyMDExNDAx NTQ1OFoXDTIzMDExNDAxNTQ1OFowYDELMAkGA1UEBhMCQ04xDjAMBgNVBAgTBUh1 YmVpMQ4wDAYDVQQHEwVXdWhhbjESMBAGA1UEChMJZmliZXJob21lMQwwCgYDVQQL EwNzZG4xDzANBgNVBAMTBkp1biBXdTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC AQoCggEBAI+M3NJzXklDYtHMy0bs4iIVIkHwQHHCch0bOcNpFmZXEEn+F9aTAEvL TNh10xSJoaFtGeAMZaOU1rU+woeXz+3sZV+WdoExnJXiuB6w5kzJTfNlAFNg41T0 SizgSvxmbdwl5C2TKpj7vyQPmNoriznwOdF7bQjGKTEPuJTALqP+zmNcwGqi47ll Ni/z5I4jwyjhfBUdGqUl3it6D4NZ3Y+tTknM7RJD2U5Ush5V0oWWM/CHEjVJNVbp LnfzsRFG5TggnUDTAiP17FWqRllqpIqtxDDtRdnx4Cv8r8g4jOc5/rVx6EcuMtNU BA7OZxploDONOROwqfm7iQ7wBgiyOuMCAwEAAaMhMB8wHQYDVR0OBBYEFCDdbV1G KtmPJqGrDVb4fKz9NnRUMA0GCSqGSIb3DQEBCwUAA4IBAQAVCVTDcbpAghr+mgtK wb7u+MelO+EymsbGKgNEYFMsqRnyRkbbWaUCMdDDuC9r/Nq0rS4adNMRXUpb3WYY +KF1Ub7AaiiTAMzNj3lt22ztpYoP05kkQPSj65DCmWBduQHrPJXf/gdW3pPLEexB u8qJxHRHiivhQFeusKhGd+bi3EMlAlYrO66kXiprt2VCbBBB2Zbdm93pK1yyckmz fkEQkGTnirni9axs4eZiyjPNRJlGwzwzpZ69qlwknZDPCKfxDtGp7GOFRKKUQVhf 3KTYyH2adJY7Fv0D1aGiKb1rYwpzfFKsjw+PrH1tSMcA60RH7SyM+9aVOE5wG41K ibLf -----END CERTIFICATE-----
1.3 generate the self signed certificate on the OVS side and configure the SSL on the OVS side
Enter the / etc/openvswitch directory on the OVS side, use your own pki to request and sign a digital certificate, and generate the OVS private key file SC privkey PEM and public key certificate sc-cert.pem:
root@root12-virtual-machine:/etc/openvswitch# ovs-pki --dir=/var/lib/openvswitch/pki req+sign sc switch root@root12-virtual-machine://etc/openvswitch# ll total 48 drwxr-xr-x 2 root root 4096 1 month 14 10:25 ./ drwxr-xr-x 126 root root 12288 1 month 16 06:31 ../ -rw-r--r-- 1 root root 4082 1 month 14 10:25 sc-cert.pem -rw------- 1 root root 1679 1 month 14 10:25 sc-privkey.pem -rw-r--r-- 1 root root 3617 1 month 14 10:25 sc-req.pem root@root12-virtual-machine://etc/openvswitch#
Start the OVS service and use OVS vsctl set SSL to set the SSL on the OVS side (configure the location of OVS private key file, OVS certificate file and ODL certificate file):
Controller active safety connection(pssl:6640),The operation of the controller side corresponding to the active safety connection is different from that of the passive connection. This part will be introduced in the sequel: _# ovs-vsctl set-manager pssl:6640_ _# OVS vsctl Set Manager SSL: 10.190.23.66:6640 (controller passive, OVS device active connection)_ default setting Bootstrap: false _# ovs-vsctl set-ssl /etc/openvswitch/sc-privkey.pem /etc/openvswitch/sc-cert.pem /var/lib/openvswitch/pki/controllerca/cacert.pem_ default setting Bootstrap: true _# ovs-vsctl -- --bootstrap set-ssl /etc/openvswitch/sc-privkey.pem /etc/openvswitch/sc-cert.pem /var/lib/openvswitch/pki/controllerca/cacert.pem_
Use OVS vsctl get SSL to view configuration information:
_# ovs-vsctl get-ssl_ Private key: /etc/openvswitch/sc-privkey.pem Certificate: /etc/openvswitch/sc-cert.pem CA Certificate: /var/lib/openvswitch/pki/controllerca/cacert.pem Bootstrap: true
1.4 copy the OVS certificate to the ODL side
Copy the sc-cert.pem on the OVS side to the SSL folder on the odl side, and then use keytool -importcert on the odl side to import the sc-cert.pem into the odl certificate library In JKS:
_# keytool -importcert -file sc-cert.pem -keystore odl.jks_ Enter keystore password: Owner: CN=sc id:b7e00bac-95d2-43f7-a9f3-e2017cdc1d57, OU=Open vSwitch certifier, O=Open vSwitch, ST=CA, C=US Issuer: CN=OVS switchca CA Certificate (2022 1� 04 17:11:15), OU=switchca, O=Open vSwitch, ST=CA, C=US Serial number: 4 Valid from: Fri Jan 14 10:25:58 CST 2022 until: Mon Jan 12 10:25:58 CST 2032 Certificate fingerprints: SHA1: B6:E6:5A:94:E3:37:0A:B0:EC:FE:41:CB:2F:FD:67:84:BB:8A:F1:60 SHA256: 5B:EF:35:AD:A9:AB:29:B8:7C:89:5A:CF:07:72:5B:1F:E7:85:59:1A:44:8E:39:F0:FC:11:E6:46:80:79:8A:F8 Signature algorithm name: SHA512withRSA Subject Public Key Algorithm: 2048-bit RSA key Version: 1 Trust this certificate? [no]: yes Certificate was added to keystore Warning: The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore odl.jks -destkeystore odl.jks -deststoretype pkcs12".
root@root12-virtual-machine:/home/root12/dcnv1r2/opendaylight/configuration/ssl# ll total 16 drwxr-xr-x 2 root root 4096 1 month 14 14:53 ./ drwxr-xr-x 5 root root 4096 1 month 14 14:49 ../ -rw-r--r-- 1 root root 2224 1 month 14 09:55 odl.jks -rw-r--r-- 1 root root 4082 1 month 14 10:25 sc-cert.pem
Use the following command to view the contents of the certificate library. You can find that the certificate library already contains PrivateKeyEntry and trustedCertEntry:
_# keytool -list -keystore odl.jks_ Enter keystore password: Keystore type: JKS Keystore provider: SUN Your keystore contains 2 entries controller, Jan 14, 2022, PrivateKeyEntry, Certificate fingerprint (SHA-256): CE:55:30:19:B6:B8:7C:D4:C8:5B:63:0D:73:26:E6:74:AD:AF:C8:F5:10:FA:6B:96:ED:B2:5F:83:B9:C7:12:C9 mykey, Jan 17, 2022, trustedCertEntry, Certificate fingerprint (SHA-256): 5B:EF:35:AD:A9:AB:29:B8:7C:89:5A:CF:07:72:5B:1F:E7:85:59:1A:44:8E:39:F0:FC:11:E6:46:80:79:8A:F8 Warning: The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore odl.jks -destkeystore odl.jks -deststoretype pkcs12". root@root12-virtual-machine:/home/root12/dcnv1r2/opendaylight/configuration/ssl#
Here, the certificates required for OVS and ODL have been generated, and the OVS side SSL configuration has been made. Next, the controller side SSL configuration needs to be carried out.
1.5 the controller actively connects to the ODL end of OVS equipment and configures SSL
As described above, the controller is actively connected and configured on the OVS side using the following command line
_# ovs-vsctl set-manager pssl:6640_
After the OVS side is set, the controller side needs to be configured as follows. The ODL produced above Copy and transfer the JKS certificate to the opendaylight/configuration/ssl directory and rename it CTL JKS and truststore JKS (the purpose is consistent with the name of the controller to facilitate reading files)
root@ubuntu:~/dcnv1r2/opendaylight/configuration/ssl# ll Total consumption 16 drwxr-xr-x 2 root root 4096 1 month 26 17:00 ./ drwxr-xr-x 5 root root 4096 1 month 26 10:15 ../ -rw-r--r-- 1 root root 3575 1 month 20 16:09 ctl.jks -rw-r--r-- 1 root root 3575 1 month 20 16:09 truststore.jks
Then enter the opendaylight/etc/opendaylight/datastore/initial/config directory to modify the OVSDB SSL connection configuration file
root@ubuntu:~/dcnv1r2/opendaylight/etc/opendaylight/datastore/initial/config# ll Total consumption 52 drwxr-xr-x 2 root root 4096 1 month 26 16:46 ./ drwxr-xr-x 3 root root 4096 1 month 26 10:04 ../ -rw-r--r-- 1 root root 14607 1 month 26 10:04 aaa-app-config.xml -rw-r--r-- 1 root root 856 1 month 27 14:12 aaa-cert-config.xml -rw-r--r-- 1 root root 182 1 month 26 10:04 aaa-datastore-config.xml -rw-r--r-- 1 root root 518 1 month 26 10:04 aaa-encrypt-service-config.xml -rw-r--r-- 1 root root 215 1 month 26 10:04 aaa-password-service-config.xml -rw-r--r-- 1 root root 953 1 month 26 16:46 default-openflow-connection-config.xml -rw-r--r-- 1 root root 941 1 month 26 10:04 legacy-openflow-connection-config.xml -rw-r--r-- 1 root root 130 1 month 26 10:04 serviceutils-upgrade-config.xml ------------------------------------------------------------------------------------ root@ubuntu:~/dcnv1r2/opendaylight/etc/opendaylight/datastore/initial/config# cat aaa-cert-config.xml <?xml version="1.0" encoding="UTF-8" standalone="no"?><aaa-cert-service-config xmlns="urn:opendaylight:yang:aaa:cert"> <use-config>true</use-config> <use-mdsal>false</use-mdsal> <bundle-name>opendaylight</bundle-name> <ctlKeystore> <name>ctl.jks</name> <alias>controller</alias> <store-password>111111</store-password> <dname>C = CN, ST = Hubei, L = Wuhan, O = sdn, OU = test, CN = JunWu</dname> <validity>365</validity> <key-alg>RSA</key-alg> <sign-alg>SHA1WithRSAEncryption</sign-alg> <keysize>1024</keysize> <tls-protocols>TLSv1.2</tls-protocols> <cipher-suites> <suite-name>TLS\_RSA\_WITH\_AES\_128\_CBC\_SHA</suite-name> </cipher-suites> </ctlKeystore> <trustKeystore> <name>truststore.jks</name> <store-password>111111</store-password> </trustKeystore>
Then go to opendaylight/etc and find org opendaylight. ovsdb. library. CFG configuration file and modify the use SSL configuration setting use SSL = true.
root@ubuntu:~/dcnv1r2/opendaylight/etc# vi org.opendaylight.ovsdb.library.cfg [1]+ Stopped vi org.opendaylight.ovsdb.library.cfg root@ubuntu:~/dcnv1r2/opendaylight/etc# cat org.opendaylight.ovsdb.library.cfg _#\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*_ _# Boot Time Configuration \*_ _# Config knob changes will require controller restart \*_ _#\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*_ _#Ovsdb plugin's (OVS, HwVtep) support both active and passive connections. OVSDB library by_ _#default listens on all IPs for switch initiated connections. Use following config_ _#knob for changing this default IP._ ovsdb-listener-ip = 0.0.0.0 _#Ovsdb plugin's (OVS, HwVtep) support both active and passive connections. OVSDB library by_ _#default listens on port 6640 for switch initiated connection. Please use following config_ _#knob for changing this default port._ ovsdb-listener-port = 6640 _#This flag will be enforced across all the connection's (passive and active) if set to true_ use-ssl = true _#Set Json Rpc decoder max frame length value. If the OVSDB node contains large configurations_ _#that can cause connection related issue while reading the configuration from the OVSDB node_ _#database. Increasing the max frame lenge helps resolve the issue. Please see following bug_ _#report for more details ( https://bugs.opendaylight.org/show\_bug.cgi?id=2732 &_ _#https://bugs.opendaylight.org/show\_bug.cgi?id=2487). Default value set to 100000._ json-rpc-decoder-max-frame-length = 100000 _#\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*_ _# Run Time Configuration \*_ _# Config knob changes doesn't require controller resart \*_ _#\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*_ _#Timeout value (in millisecond) after which OVSDB rpc task will be cancelled.Default value is_ _#set to 1000ms, please uncomment and override the value if requires.Changing the value don't_ _#require controller restart._ ovsdb-rpc-task-timeout = 1000
Finally, use postman, call (put) http: / / controller IP: 8181 / rest / data / network topology: network topology / topology = OVSDB% 3A1, and import the OVS device information remote IP and remote port to the controller, so as to realize the controller OVSDB protocol to actively connect OVS devices.
{
"topology": [
{
"topology-id": "ovsdb:1",
"node": [
{
"node-id": "ovsdb://HOST2",
"ovsdb:connection-info": {
"ovsdb:remote-ip": "10.190.51.111",
"ovsdb:remote-port": 6640
}
}
]
}
]
}View information on ovs:
root@root12-virtual-machine:~_# ovs-vsctl show_ 1db8fd94-c6ab-41f8-9993-bdc83a14c430 Manager "pssl:6640" is\_connected: true
View information of controller interface:
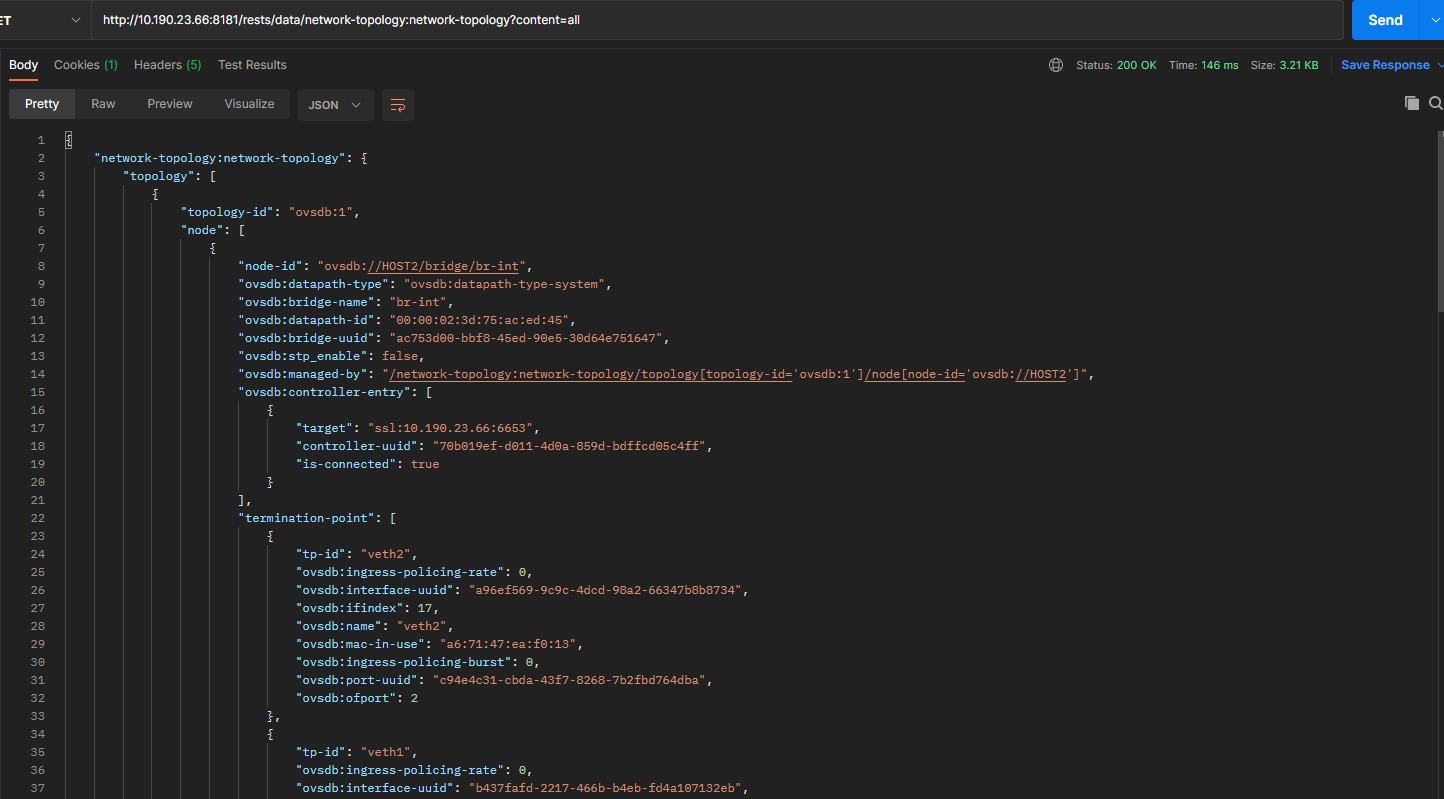
For this ovsdb, PSSL connection verification was successful.
For this ovsdb, PSSL connection verification was successful.
1.6 OPENFLOW SSL secure connection
openflow ssl link, which is configured on the OVS side using the following command line
_# ovs-vsctl set-controller br-int ssl:10.190.23.66:6653_
As in 1.5, enter the opendaylight/etc/opendaylight/datastore/initial/config directory, modify the openflow SSL connection configuration file, and specify the port, protocol, certificate path and other information.
root@ubuntu:~/dcnv1r2/opendaylight/etc/opendaylight/datastore/initial/config# ll Total consumption 52 drwxr-xr-x 2 root root 4096 1 month 26 16:46 ./ drwxr-xr-x 3 root root 4096 1 month 26 10:04 ../ -rw-r--r-- 1 root root 14607 1 month 26 10:04 aaa-app-config.xml -rw-r--r-- 1 root root 856 1 month 27 14:12 aaa-cert-config.xml -rw-r--r-- 1 root root 182 1 month 26 10:04 aaa-datastore-config.xml -rw-r--r-- 1 root root 518 1 month 26 10:04 aaa-encrypt-service-config.xml -rw-r--r-- 1 root root 215 1 month 26 10:04 aaa-password-service-config.xml -rw-r--r-- 1 root root 953 1 month 26 16:46 default-openflow-connection-config.xml -rw-r--r-- 1 root root 941 1 month 26 10:04 legacy-openflow-connection-config.xml -rw-r--r-- 1 root root 130 1 month 26 10:04 serviceutils-upgrade-config.xml ------------------------------------------------------------------------------------ root@ubuntu:~/dcnv1r2/opendaylight/etc/opendaylight/datastore/initial/config# cat default-openflow-connection-config.xml <switch-connection-config xmlns="urn:opendaylight:params:xml:ns:yang:openflow:switch:connection:config"> <instance-name>openflow-switch-connection-provider-default-impl</instance-name> <port>6653</port> <transport-protocol>TLS</transport-protocol> <group-add-mod-enabled>false</group-add-mod-enabled> <channel-outbound-queue-size>1024</channel-outbound-queue-size> <tls> <keystore>configuration/ssl/ctl.jks</keystore> <keystore-type>JKS</keystore-type> <keystore-path-type>PATH</keystore-path-type> <keystore-password>111111</keystore-password> <truststore>configuration/ssl/truststore.jks</truststore> <truststore-type>JKS</truststore-type> <truststore-path-type>PATH</truststore-path-type> <truststore-password>111111</truststore-password> <certificate-password>111111</certificate-password> <cipher-suites>TLS\_RSA\_WITH\_AES\_128\_CBC\_SHA</cipher-suites> </tls> </switch-connection-config>
To view openflow connection information:
To view connection information on ovs:
root@root12-virtual-machine:~_# ovs-vsctl show_ 1db8fd94-c6ab-41f8-9993-bdc83a14c430 Manager "pssl:6640" is\_connected: true Bridge br-int Controller "ssl:10.190.23.66:6653" is\_connected: true Port br-int Interface br-int type: internal Port "veth2" Interface "veth2" Port "veth1" Interface "veth1" ovs\_version: "2.9.8"
Control interface view information:
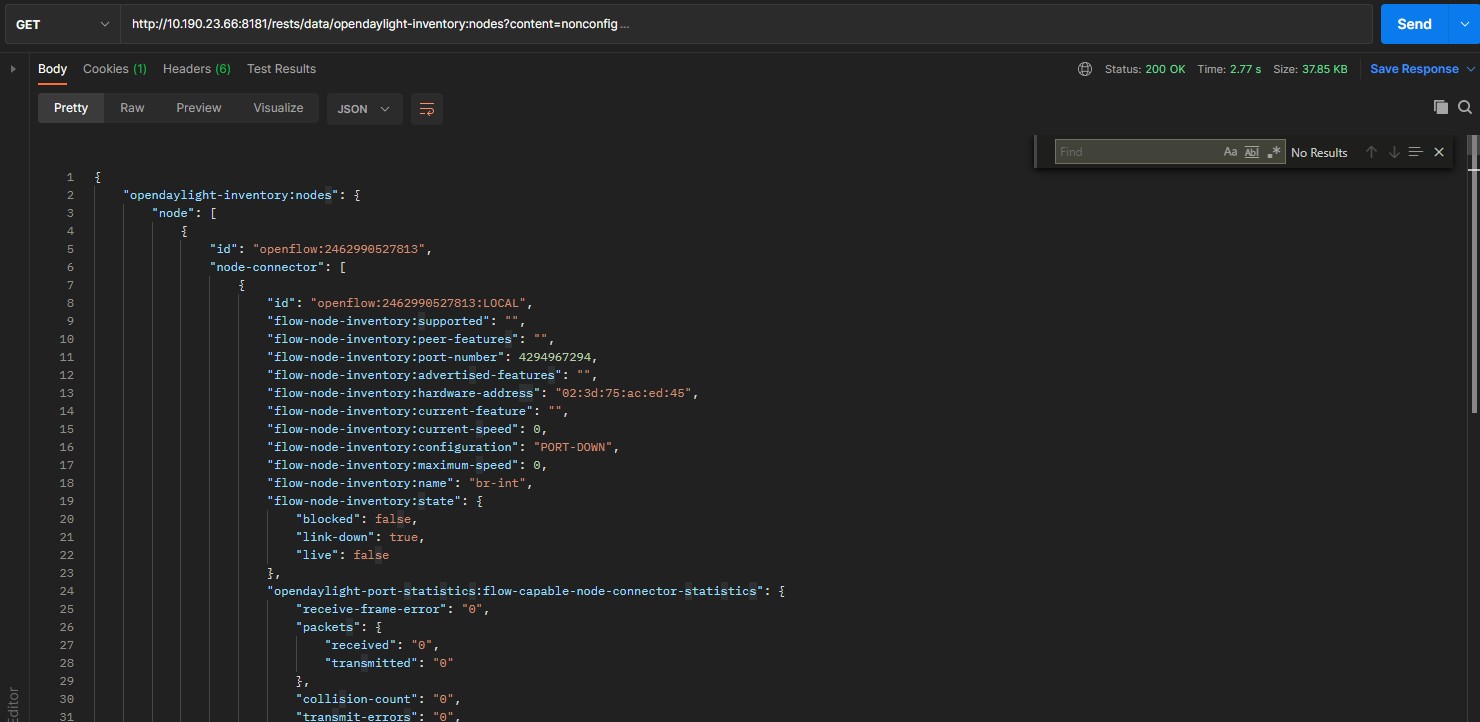
So far, openflow SSL secure connection verification is successful.