1, Basic measures for account security
1. System account cleaning
(1) Set the Shell of the non logged in user to / sbin/nologin
usermod -S /sbin/nologin
(2) Lock accounts that have not been used for a long time
usermod-L user name
passwd - | user name
passwd -S username
(3) Delete useless account
userdel [-r] delete home directory together
(4) Lock account files passwd and shadow
Chatr + I / etc / passwd / etc / shadow (lock file and view status)
Isattr /etc/passwd /etc/shadow (unlock file and view status)
Chatr - I / etc / passwd / etc / shadow (unlock file and view status)
[root@localhost ~]# chattr +i /etc/passwd /etc/shadow [root@localhost ~]# lsattr /etc/passwd /etc/shadow ----i----------- /etc/passwd ----i----------- /etc/shadow Prevent adding or modifying passwords at this time [root@localhost ~]# chattr -i /etc/passwd /etc/shadow [root@localhost ~]# lsattr /etc/passwd /etc/shadow ---------------- /etc/passwd ---------------- /etc/shadow At this moment, you can add or modify the password
2. Password security control
(1) Set password validity
(2) Require the user to change the password at the next login
For new users [root@localhost ~]# vim /etc/login.defs # # Please note that the parameters in this configuration file control the # behavior of the tools from the shadow-utils component. None of these # tools uses the PAM mechanism, and the utilities that use PAM (such as the # passwd command) should therefore be configured elsewhere. Refer to # /etc/pam.d/system-auth for more information. # # *REQUIRED* # Directory where mailboxes reside, _or_ name of file, relative to the # home directory. If you _do_ define both, MAIL_DIR takes precedence. # QMAIL_DIR is for Qmail # #QMAIL_DIR Maildir MAIL_DIR /var/spool/mail #MAIL_FILE .mail # Password aging controls: # # PASS_MAX_DAYS Maximum number of days a password may be used. # PASS_MIN_DAYS Minimum number of days allowed between password changes. # PASS_MIN_LEN Minimum acceptable password length. # PASS_WARN_AGE Number of days warning given before a password expires. # PASS_MAX_DAYS 30 PASS_MIN_DAYS 0 :wq
Suitable for old users
[root@localhost ~]# chage -M 30 123
Days user name
[root@localhost ~]# cat /etc/shadow |grep 123
123:$6$1VOb.Rd.emlYopvT$tclzmGjvX3.y/pLPumnx.L1Ew4s8bCP2Ovc7tjYGO0R3/LljHB/gqlhuyleqjjsv1lJTwDoyTobYAJmLiULkH0::0:30:7:::
We can view the password validity through this
[root@localhost ~]# Chage - d 0 123change the password every time you log in[root@localhost ~]# echo "123123" |passwd --stdin 123
Change the password of user 123 to 1231233. Command history restrictions
Reduce the number of recorded commands
Automatically clear command history on logout
(1) Look at history
[root@localhost ~]# history
1 vim /etc/sysconfig/network-scripts/ifcfg-ens33
2 vim /etc/sysconfig/network-scripts/ifcfg-ens33
3 systemctl restart network
. . . (There are many more below (omitted here)(2) Temporarily hide history
[root@localhost ~]# history -c temporarily hides the history. It will appear again after shutdown and restart
[root@localhost ~]# history
1 history
(3) Reduce the number of recorded commands
[root@localhost ~]# vim /etc/profile input/HIS<enter> HOSTNAME=`/usr/bin/hostname 2>/dev/null` HISTSIZE=10(This is modified here) :wq (Save (exit) [root@localhost ~]# source /etc/profile let's refresh [root@localhost ~]# history 391 chage -M 30 123 392 cat /etc/shadow |grep 123 393 su 123 394 hitory 395 history 396 vim /etc/profile 397 history 398 source .bashrc 399 source /etc/profile 400 history (Now we'll show only the last ten Histories)
(4) Clear command history
[root@localhost ~]# vim .bashrc
# .bashrc
Press o Insert, enter in the space
echo "" > ~/.bash_history
:wq Save exit
[root@localhost ~]# Source. Bashrc refresh
[root@localhost ~]# cat ./bash_history
((the contents are empty)
[root@localhost ~]# reboot restart
[root@localhost ~]# history is gone
1 history3. Terminal automatic logoff
Automatically log off after being idle for 60 seconds
[root@localhost ~]# vim .bash_profile PATH=$PATH:$HOME/bin export PATH G To the end of the line, enter export TMOUT=60 <esc>input :wq Save exit [root@localhost ~]# source .bash_profile to refresh Idle for 60 seconds will automatically log off
2, Switch user su command
1. Purpose and usage
Purpose: Substitute User to switch users
Format: su - user name
2. Password verification
root → any user, no need to verify password
Ordinary users → other users, you need to verify the password of the target user
[root@localhost ~]# su 123 [123@localhost root]$ pwd /root [123@localhost root]$ echo $PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin No-,Retain all current environments [root@localhost ~]# su - 123 [123@localhost ~]$ pwd /home/123 [123@localhost ~]$ echo $PATH /usr/local/bin:/bin:/usr/bin:/usr/local/sbin:/usr/sbin:/home/123/.local/bin:/home/123/bin plus-,Use target user's shell Environment, switch the directory to the home directory of the target user
View current user name
[123@localhost ~]$ whoami 123 View current user name
3. Idle users using su command
Add users who are allowed to use the su command to the wheel group
Enable pam_wheel
[root@localhost pam.d]# vim su Open the sixth line and delete it# #%PAM-1.0 auth sufficient pam_rootok.so # Uncomment the following line to implicitly trust users in the "wheel" group. #auth sufficient pam_wheel.so trust use_uid # Uncomment the following line to require a user to be in the "wheel" group. auth required pam_wheel.so use_uid(After opening, only wheel Only users in the group can use it su) auth substack system-auth auth include postlogin account sufficient pam_succeed_if.so uid = 0 use_uid quiet account include system-auth password include system-auth session include system-auth session include postlogin session optional pam_xauth.so :wq [123@localhost pam.d]$ su root password: 12^Hsu: Permission denied (permission denied here) Open the second line and comment(#)The sixth line and comment, the second line and the sixth line are su commands that can be used by all users
4. View su operation records
Security log file: / var/log/secure
3, PAM security authentication in Linux
1. Potential safety hazards of Su command
(1) By default, any user is allowed to use the su command, and has the opportunity to repeatedly try the login password of other users (such as root), which brings security risks
(2) In order to strengthen the use control of su command, with the help of PAM authentication module, only a few users are allowed to use su command for switching
2.PAM(Pluggable Authentication Modules) pluggable authentication module
(1) It is an efficient, flexible and convenient user level authentication method
(2) It is a widely used authentication method for Linux servers
3.PAM certification principle
(1) Generally follow the order
Service → PAM → pam_ * so
(2) first determine which service, then load the corresponding PAM configuration file (located under /etc/pam.d), and finally call the authentication file (located under /lib64/security') for security authentication.
(3) When a user accesses the server, a service program of the server sends the user's request to the PAM module for authentication
(4) Different applications have different PAM modules
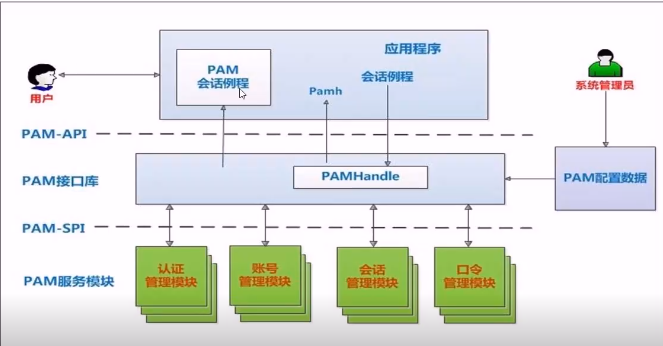
4. Composition of PAM certification
(1) To check whether a program supports PAM authentication, you can use the Is command
Example: check su whether PAM module authentication is supported
[123@localhost pam.d]$ ls /etc/pam.d | grep su ksu su sudo sudo-i su-l
(2) View Su's PAM configuration file: cat /etc/pam.d/su
Each line is an independent authentication process
Each line can be divided into three fields: authentication type; Control type; PAM module and its parameters
[123@localhost pam.d]$ cat /etc/pam.d/su #%PAM-1.0 #auth sufficient pam_rootok.so # Uncomment the following line to implicitly trust users in the "wheel" group. #auth sufficient pam_wheel.so trust use_uid # Uncomment the following line to require a user to be in the "wheel" group. #auth required pam_wheel.so use_uid auth substack system-auth auth include postlogin account sufficient pam_succeed_if.so uid = 0 use_uid quiet account include system-auth password include system-auth session include system-auth session include postlogin session optional pam_xauth.so

The first column represents the PAM authentication module type
auth: identify the user's identity. If prompted to enter a password, judge whether it is root.
Account: check the attributes of the account, such as whether it is allowed to log in to the system, whether the account has expired, whether it has reached the maximum number of users, etc.
Password: use user information to update data, such as changing user password.
Session: defines the session operation management to be performed before and after login, such as login connection information,
Open and close user data, Mount file system. How many terminals can be connected
The second column represents the PAM control flag
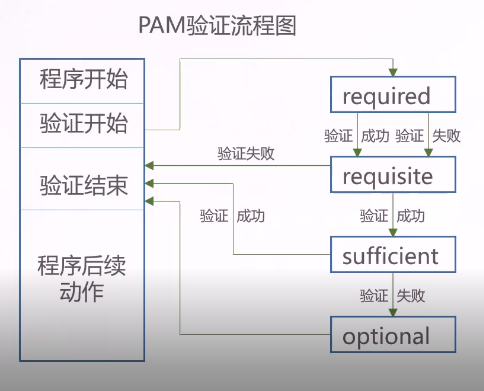
required: indicates that a success value needs to be returned. If the return fails, the failure result will not be returned immediately, but the next verification of the same type will continue. After the execution of all modules of this type is completed, the failure will be returned.
Required: similar to reguired, but if this module returns a failure, it immediately returns a failure and indicates that this type of failure.
sufficient: if this module returns success, it will directly return success to the program, indicating such success. If it fails, it will not affect this type of return value.
optional: it does not return success or failure. It is generally not used for verification, but only displays information (usually used for session type),
include: indicates that other PAM configuration files are called during validation.
For example, many applications call / etc/pam.d/syatem- auth (mainly responsible for user login authentication)
To achieve authentication without having to write configuration items one by one.
5.PAM verification process
4, Using sudo mechanism to elevate permissions
1. Purpose and usage of sudo (super userdo super user) command
Purpose: execute authorization commands as other users (such as root)
Usage: sudo authorization command
2. Configure sudo authorization
(1) visudo or vi /etc/sudoers
(2) Record format
user Host name list = command program list
[123@localhost root]$ sudo ifconfig ens33:2 192.168.91.202/24
We trust that you have learned the daily precautions from the system administrator.
To sum up, there are no more than these three points:
#1) Respect other people's privacy.
#2) Consider (consequences and risks) before entering.
#3) The greater the power, the greater the responsibility.
[sudo] 123 Password for:
Sorry, user 123 does not have permission to root Where is your identity localhost.localdomain Upper execution /sbin/ifconfig ens33:2 192.168.91.202/24.
[root@localhost ~]# visudo
## The COMMANDS section may have other options added to it.
##
## Allow root to run any commands anywhere
root ALL=(ALL) ALL
## Allows members of the 'sys' group to run networking, software,
## service management apps and more.
# %sys ALL = NETWORKING, SOFTWARE, SERVICES, STORAGE, DELEGATING, PROCESSES, LOCATE, DRIVERS
## Allows people in group wheel to run all commands
%wheel ALL=(ALL) ALL
## Same thing without a password
# %wheel ALL=(ALL) NOPASSWD: ALL
## Allows members of the users group to mount and unmount the
## cdrom as root
# %users ALL=/sbin/mount /mnt/cdrom, /sbin/umount /mnt/cdrom
## Allows members of the users group to shutdown this system
# %users localhost=/sbin/shutdown -h now
## Read drop-in files from /etc/sudoers.d (the # here does not mean a comment)
#includedir /etc/sudoers.d
123 localhost=(root) /sbin/iconfig
:wq