For study purposes only.Do not use for illegal purposes and I will not be legally liable.
Preface
apk version, Tmall 8.11.0, this time mainly talks about how to run x-sign using unidbg. The blogger is also a beginner. If you have any questions, you can discuss with the blogger. It is very welcome.
charles packet analysis
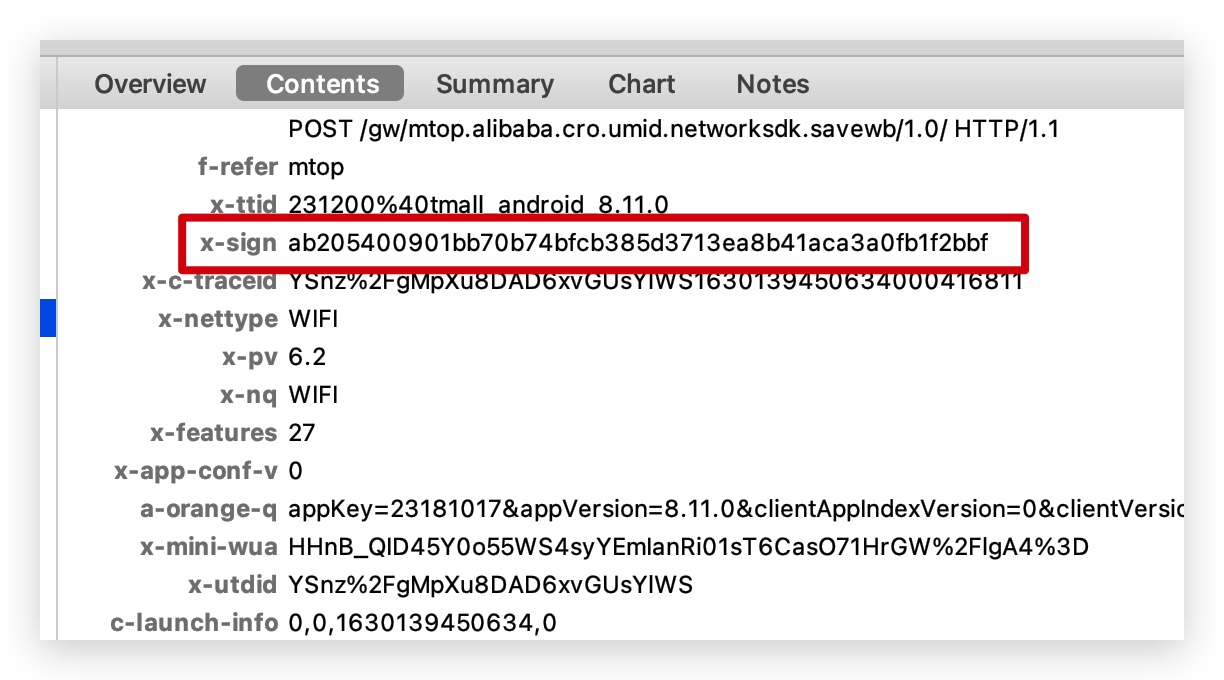
Analyze this x-sign to get started with unidbg once you know the target
unidbg
Specific function positioning aside, you all know that JNICLibrary.doCommandNative is the so entry
package com.xiayu;
import com.github.unidbg.AndroidEmulator;
import com.github.unidbg.Emulator;
import com.github.unidbg.LibraryResolver;
import com.github.unidbg.file.FileResult;
import com.github.unidbg.file.IOResolver;
import com.github.unidbg.file.linux.AndroidFileIO;
import com.github.unidbg.linux.android.AndroidEmulatorBuilder;
import com.github.unidbg.linux.android.AndroidResolver;
import com.github.unidbg.linux.android.dvm.AbstractJni;
import com.github.unidbg.linux.android.dvm.DvmClass;
import com.github.unidbg.linux.android.dvm.DvmObject;
import com.github.unidbg.linux.android.dvm.VM;
import com.github.unidbg.memory.Memory;
import com.github.unidbg.spi.SyscallHandler;
import com.github.unidbg.virtualmodule.android.AndroidModule;
import org.json.JSONException;
import org.json.JSONObject;
import java.io.File;
import java.io.IOException;
import java.util.LinkedHashMap;
import java.util.Map;
public class TianMaoXSign1 extends AbstractJni implements IOResolver<AndroidFileIO> {
private final AndroidEmulator emulator;
private final VM vm;
private long slot;
public String sgMain = "unidbg-android/src/test/resources/test_so/tianmao8110/libsgmainso-6.4.156.so";
public String sgSecurityBody = "unidbg-android/src/test/resources/test_so/tianmao8110/libsgsecuritybodyso-6.4.90.so";
public String sgAvMp = "unidbg-android/src/test/resources/test_so/tianmao8110/libsgavmpso-6.4.34.so";
public String sgMisc = "unidbg-android/src/test/resources/test_so/tianmao8110/libsgmiscso-6.4.44.so";
public File sgMainFile = new File(sgMain);
public File sgSecurityBodyFile = new File(sgSecurityBody);
public File sgAvMpFile = new File(sgAvMp);
public File sgMiscFile = new File(sgMisc);
public String dataAppPath = "/data/app/com.tmall.wireless-NsaOVgz2fomXJNoPTrbOwg==";
public String packageName = "com.tmall.wireless";
public String methodSign = "doCommandNative(I[Ljava/lang/Object;)Ljava/lang/Object;";
public DvmClass JNICLibrary;
public DvmObject<?> context;
public DvmObject<?> ret;
public String APK_INSTALL_PATH = dataAppPath + "/base.apk";
public File APK_FILE = new File("/Users/admin/Desktop/android/file/tianmao-8.11.0.apk");
private static LibraryResolver createLibraryResolver() {
return new AndroidResolver(23);
}
private static AndroidEmulator createARMEmulator() {
return AndroidEmulatorBuilder
.for32Bit()
.setRootDir(new File("appFile/tianmao-xsign1"))
.setProcessName("com.tmall.wireless")
.build();
}
public TianMaoXSign1() {
emulator = createARMEmulator();
Map<String, Integer> iNode = new LinkedHashMap<>();
iNode.put("/data/system", 671745);
iNode.put("/data/app", 327681);
iNode.put("/sdcard/android", 294915);
iNode.put("/data/user/0/com.tmall.wireless", 655781);
iNode.put("/data/user/0/com.tmall.wireless/files", 655864);
emulator.set("inode", iNode);
emulator.set("uid", 10074);
Memory memory = emulator.getMemory();
memory.setLibraryResolver(createLibraryResolver());
SyscallHandler<AndroidFileIO> handler = emulator.getSyscallHandler();
handler.setVerbose(false);
handler.addIOResolver(this);
vm = emulator.createDalvikVM(APK_FILE);
vm.setJni(this);
vm.setVerbose(true);
new AndroidModule(emulator, vm).register(memory);
JNICLibrary = vm.resolveClass("com/taobao/wireless/security/adapter/JNICLibrary");
context = vm.resolveClass("android/content/Context").newObject(null);
}
public static void main(String[] args) throws IOException {
TianMaoXSign1 tm2 = new TianMaoXSign1();
tm2.destroy();
}
public void destroy() throws IOException {
emulator.close();
}
@Override
public FileResult<AndroidFileIO> resolve(Emulator<AndroidFileIO> emulator, String pathname, int oflags) {
System.out.println("resolve.pathname: " + pathname);
return null;
}
}
Let's put the framework together first. IOResolver <AndroidFileIO>is an interface class that can use unidbg's virtual file system directly to supplement files.Run, if there are no errors, everything is OK, proceed to the next step
Here we start to initialize each so. For the specific initialization process, frida hook can be used to view the overall process. jnitrace is incomplete, which makes it easier to get problems
libsgmainso
public void initMain() {
DalvikModule dm = vm.loadLibrary(sgMainFile, true);
dm.callJNI_OnLoad(emulator);
ret = JNICLibrary.callStaticJniMethodObject(
emulator, methodSign, 10101,
new ArrayObject(
context,
DvmInteger.valueOf(vm, 3),
new StringObject(vm, ""),
new StringObject(vm, "/data/user/0/" + packageName + "/app_SGLib"),
new StringObject(vm, "")
));
System.out.println("xiayu, initMain.ret-10101: " + ret.getValue().toString());
ret = JNICLibrary.callStaticJniMethodObject(
emulator, methodSign, 10102,
new ArrayObject(
new StringObject(vm, "main"),
new StringObject(vm, "6.5.156"),
new StringObject(vm, "/data/user/0/com.tmall.wireless/app_SGLib/app_1627957761/main/libsgmainso-6.5.156.so")
));
System.out.println("xiayu, initMain.ret-10102: " + ret.getValue().toString());
}
Here's the result of initializing the sgmain process as a frida hook, calling it in the main function and starting to run
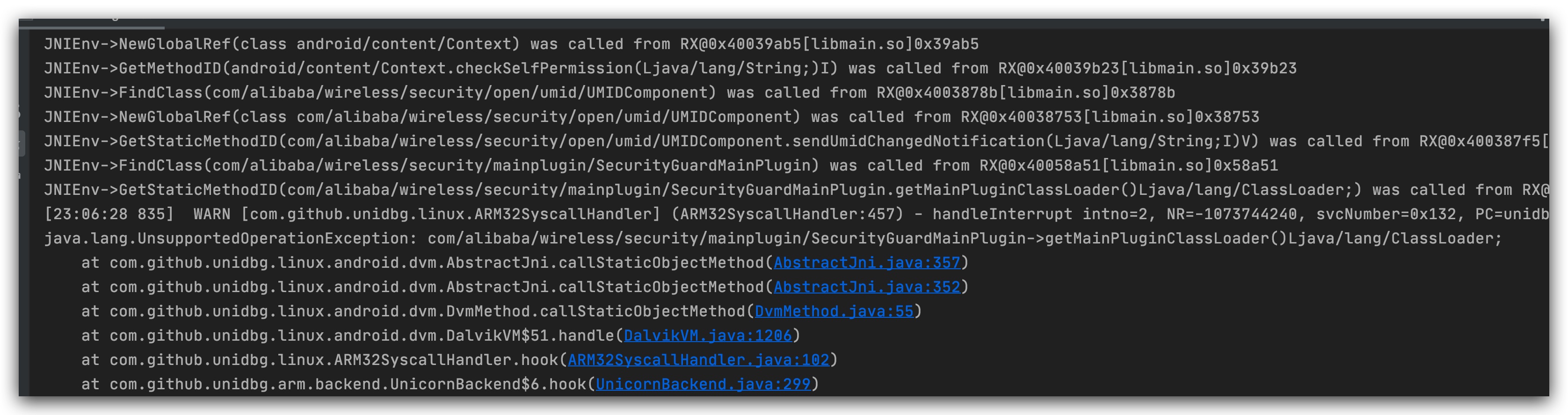
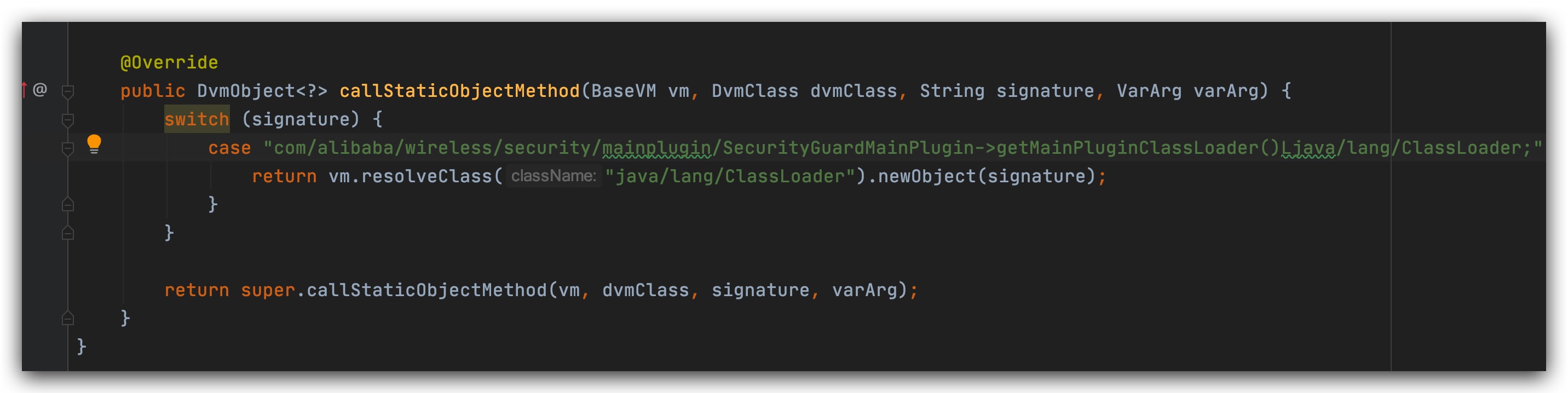
This is where we start reporting common environmental errors. Let's add
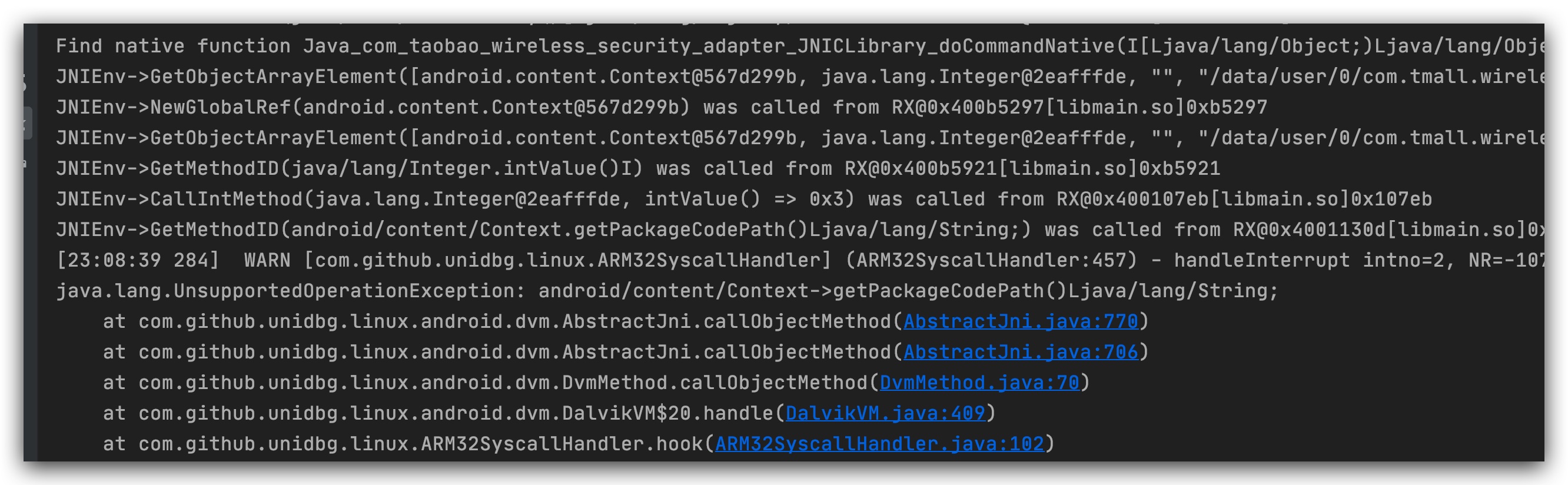
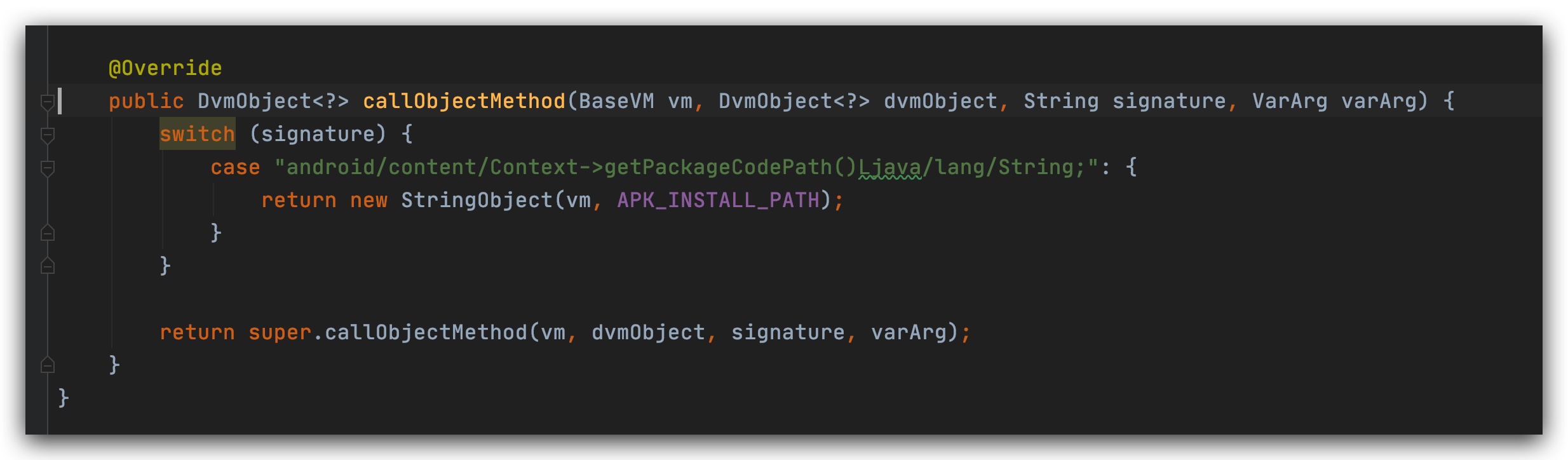
Continue here and return to the base.apk path of the APK
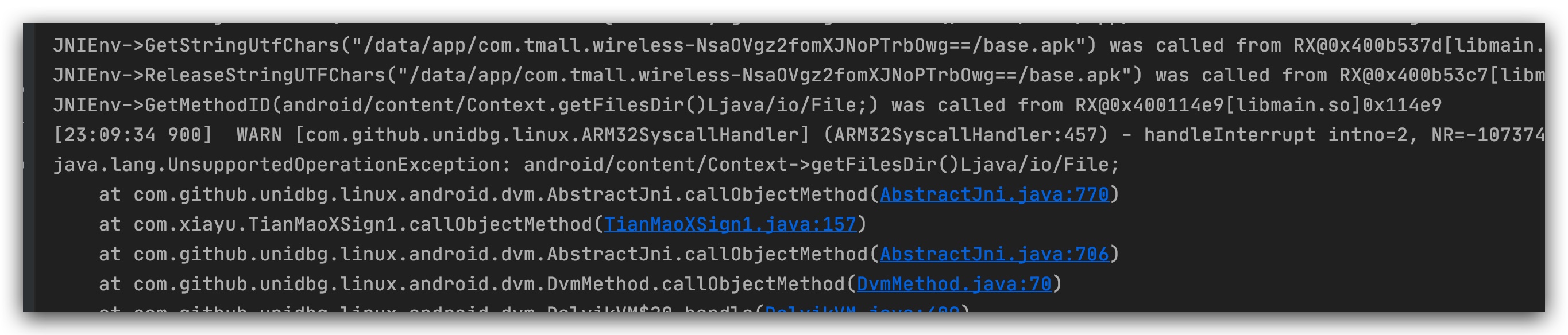
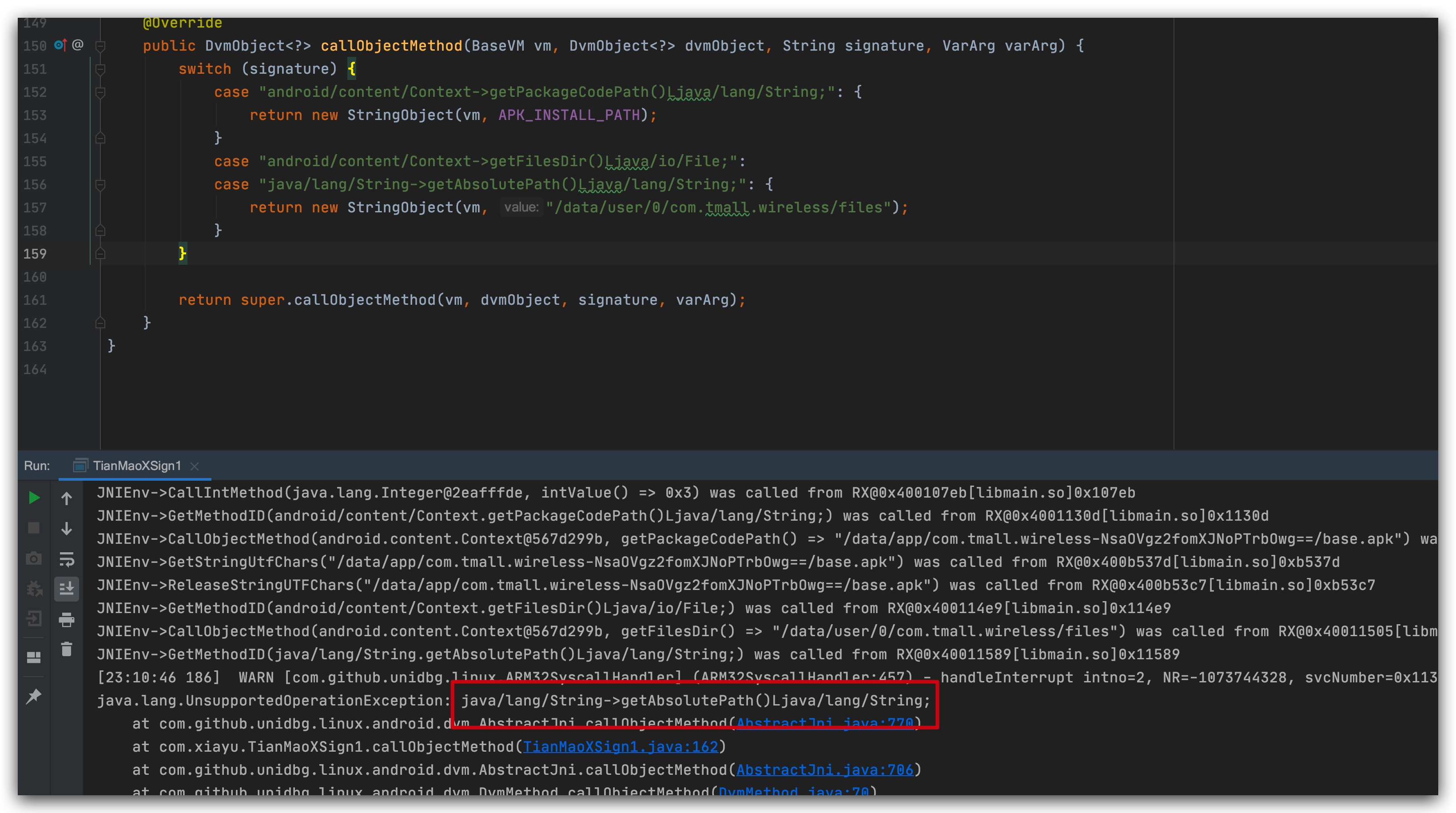
Two consecutive errors reported here can be handled uniformly, returning the file folder path
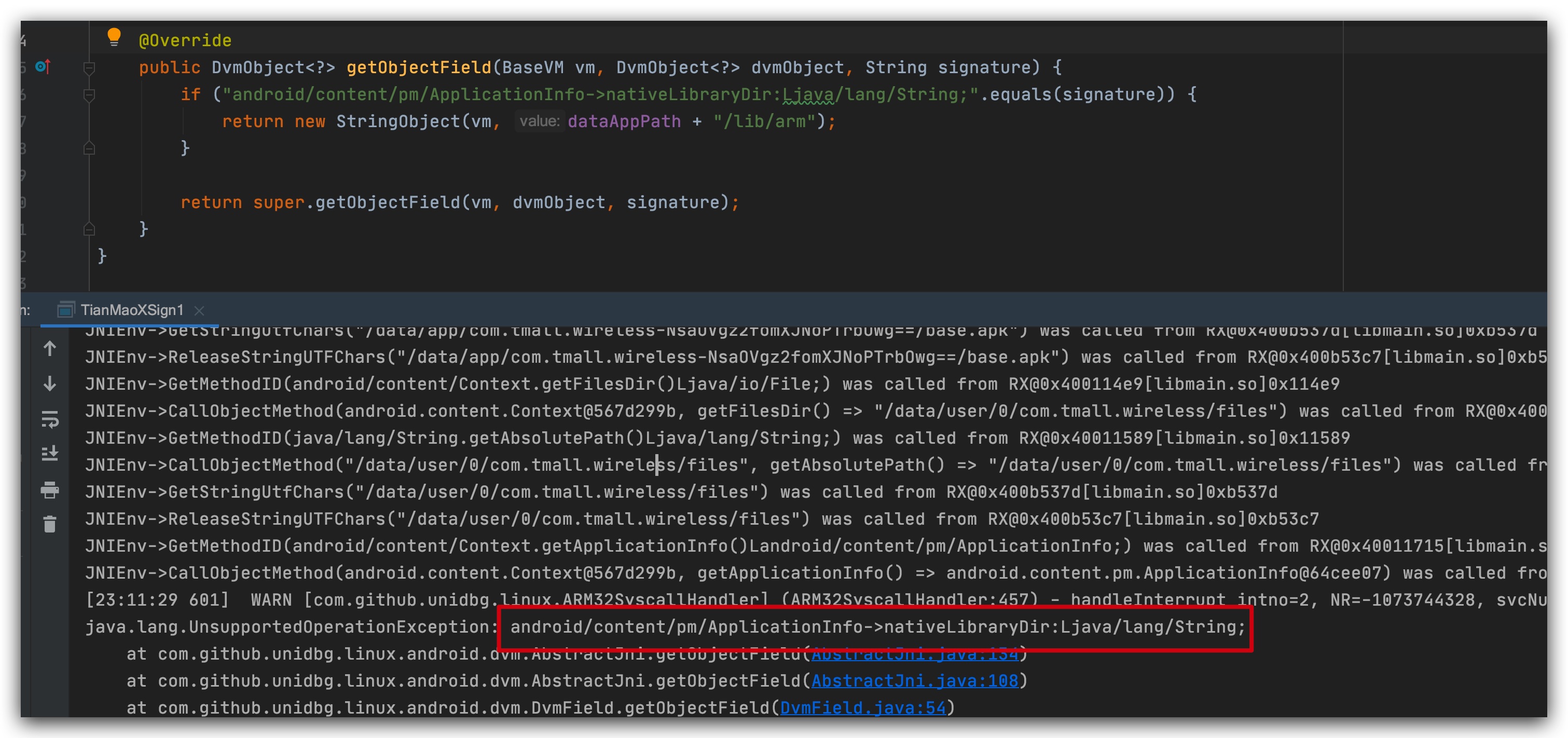
The native lib/arm path of the apk needs to be returned here
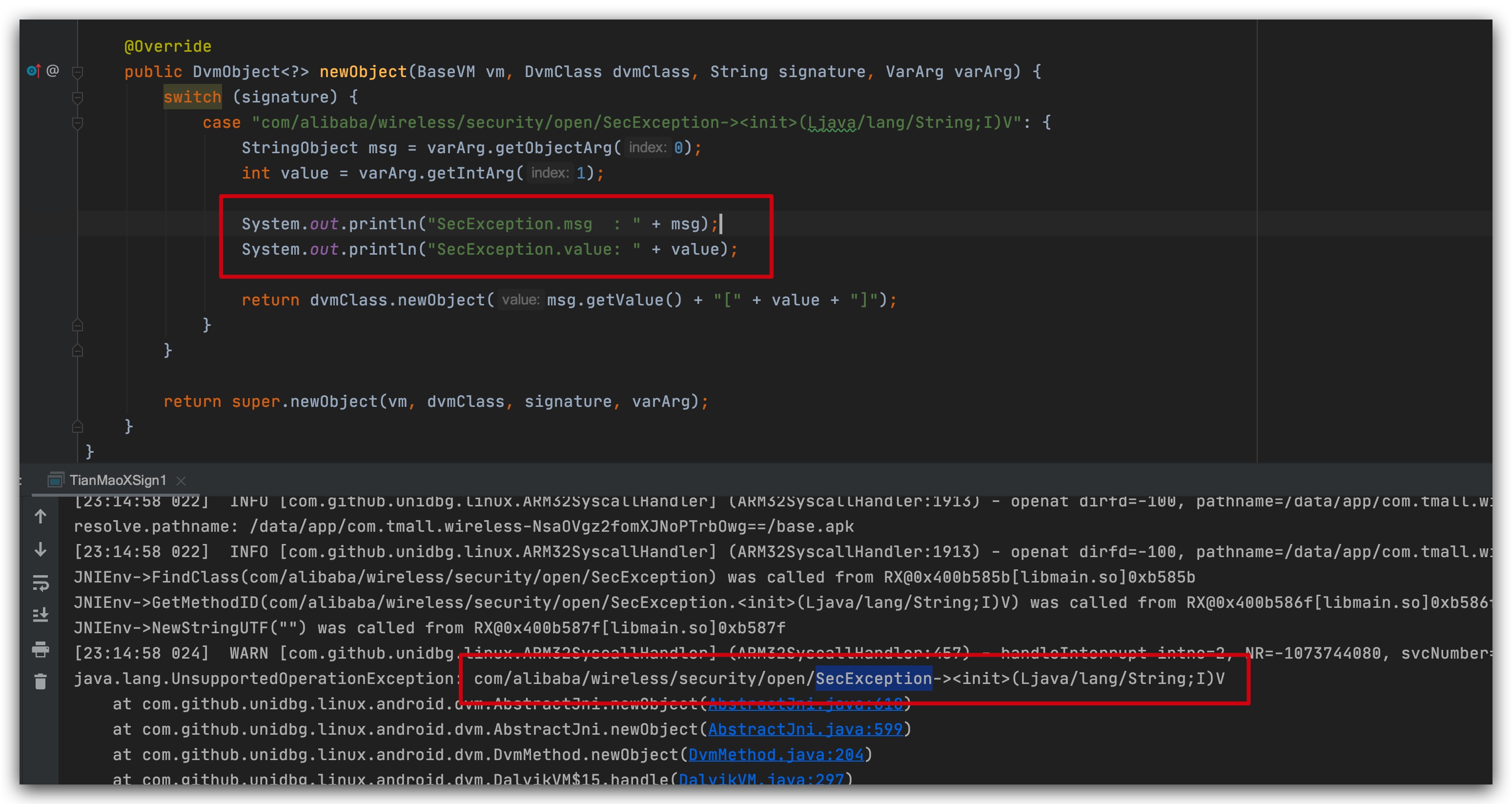
This is a class that sgmain throws an exception. We need to print the msg code to see what went wrong
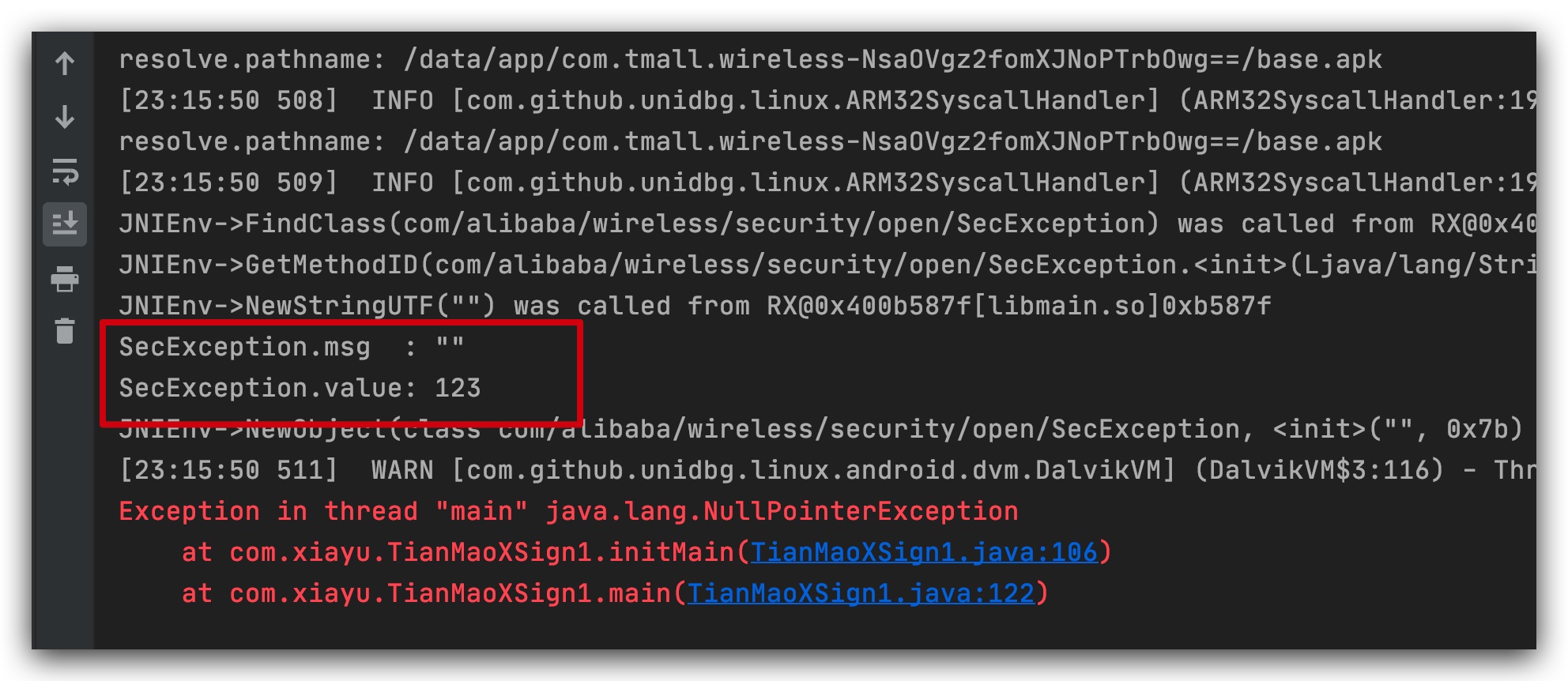
Continue execution, and error code = 123 is reported.There are two reasons to find errors here. The first is what is wrong with Baidu's search for Ali Ju Security 123. The second is to check the log log log and guess what is wrong.The process is still rather pitted. I have stepped on a lot of pits here, so I can directly say the answer is that there is no file.What file is missing? Search resolve.pathname: This word, don't know what can be filled.
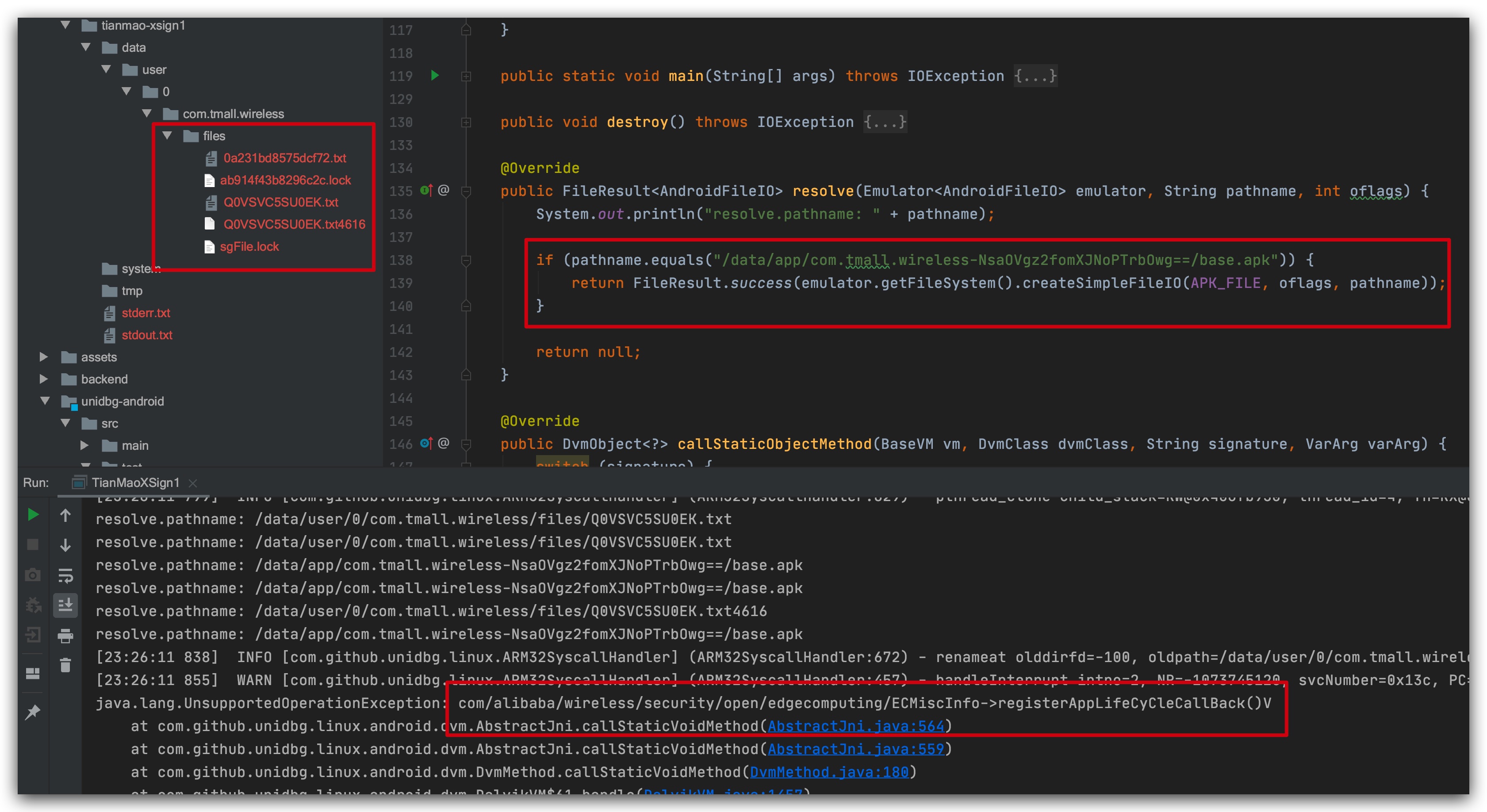
Here I've filled in a few files on the left side. With base.apk, the files are in the directory corresponding to the mobile phone. pull them down and then run. I find that 123 errors are no longer reported.
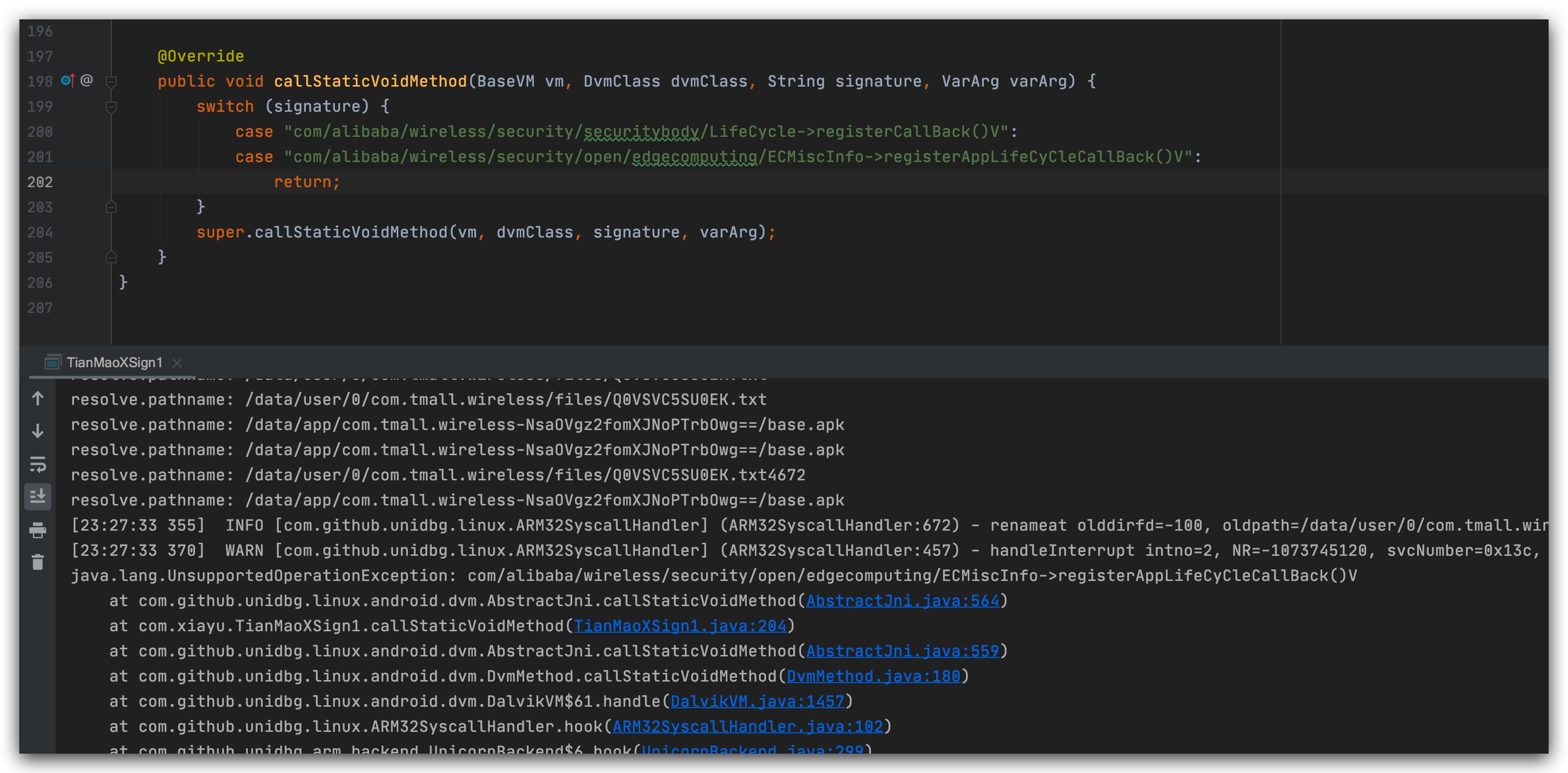
Two errors have been reported here and can be fixed together
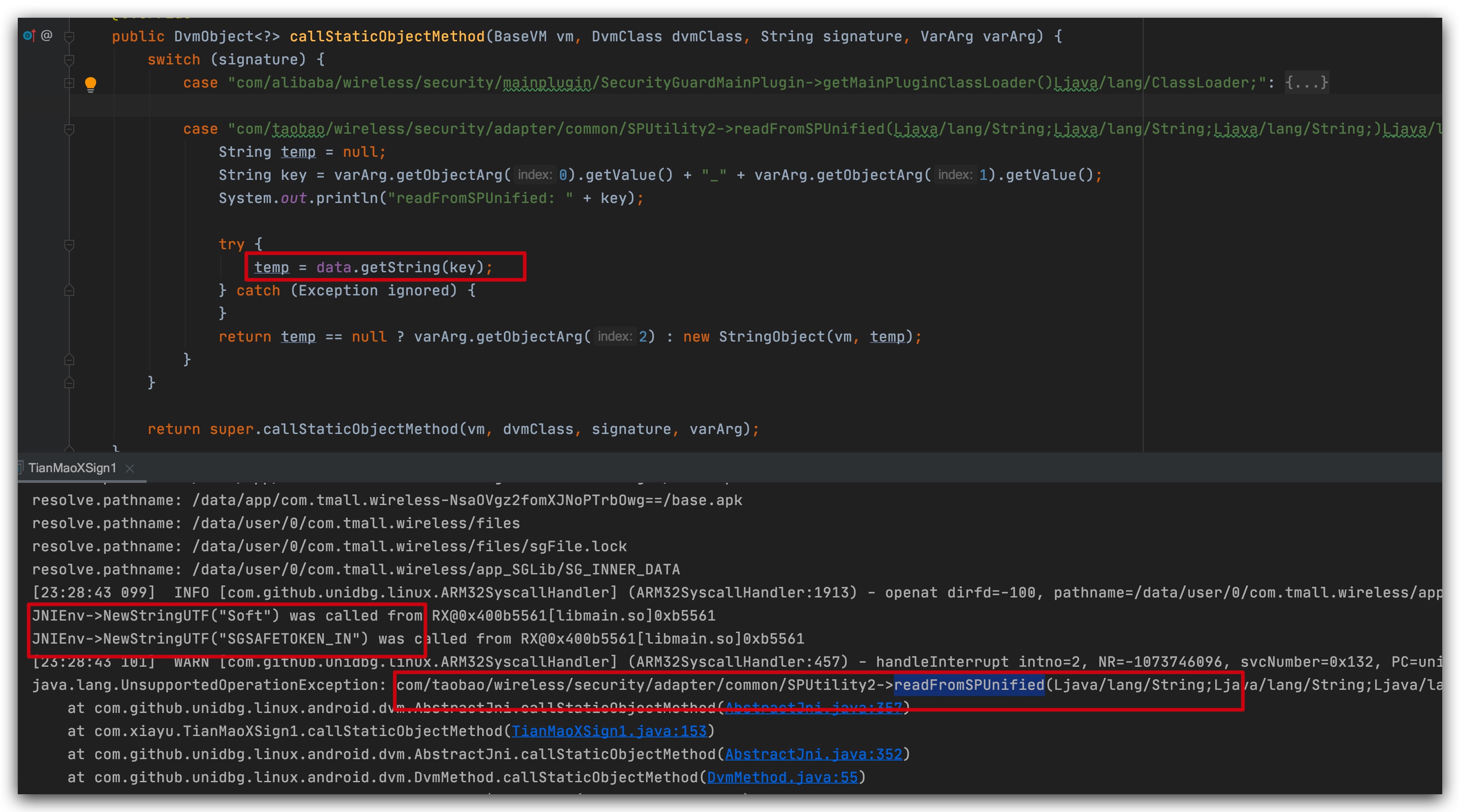
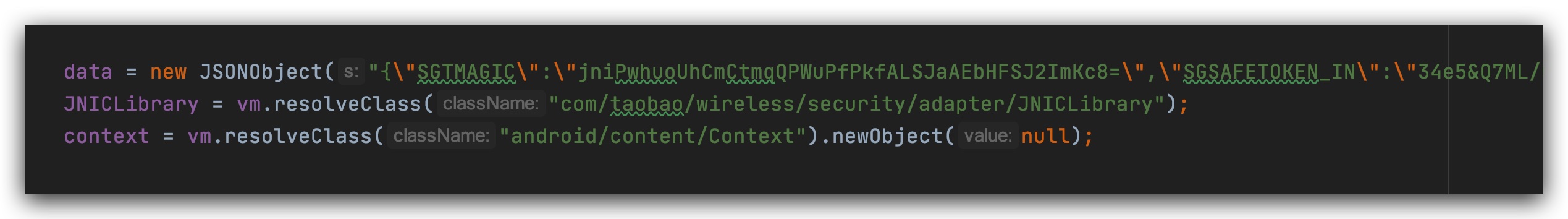
After a few more errors have been filled in the middle, here is the json content in the file to read, because it is fixed and I take it out directly, after which I make up a common OK
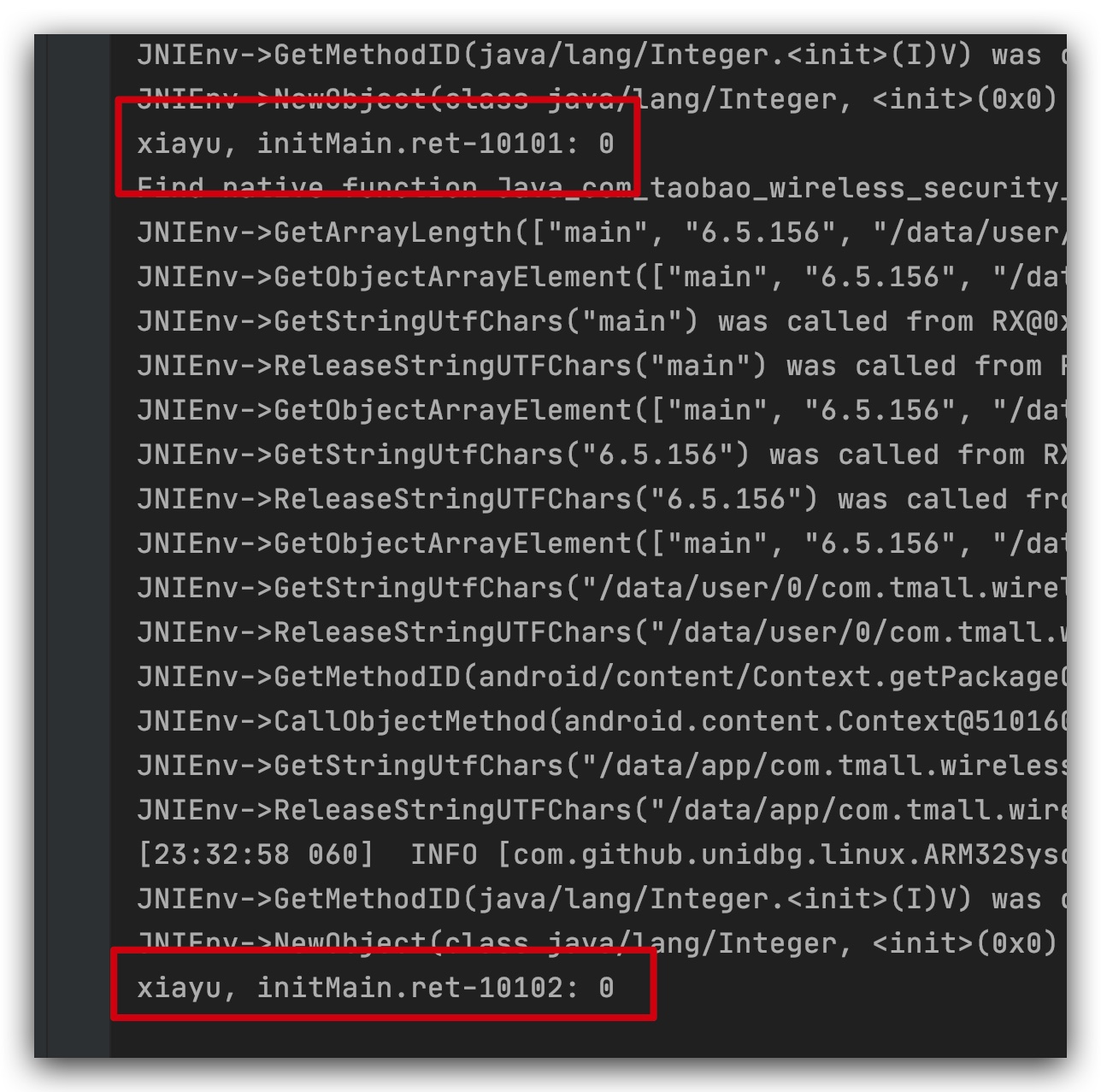
Here's sgmain. It returned 0 normally. I got frida call as the result
libsgsecuritybodyso
public void initSecurityBody() {
DalvikModule securityBody = vm.loadLibrary(sgSecurityBodyFile, true);
securityBody.callJNI_OnLoad(emulator);
ret = JNICLibrary.callStaticJniMethodObject(
emulator, methodSign, 10102,
new ArrayObject(
new StringObject(vm, "securitybody"),
new StringObject(vm, "6.4.90"),
new StringObject(vm, "/data/user/0/com.tmall.wireless/app_SGLib/app_1627957761/main/libsgsecuritybodyso-6.4.90.so")
));
System.out.println("xiayu, initSecurityBody.ret-10102: " + ret.getValue().toString());
}
New function called in main function
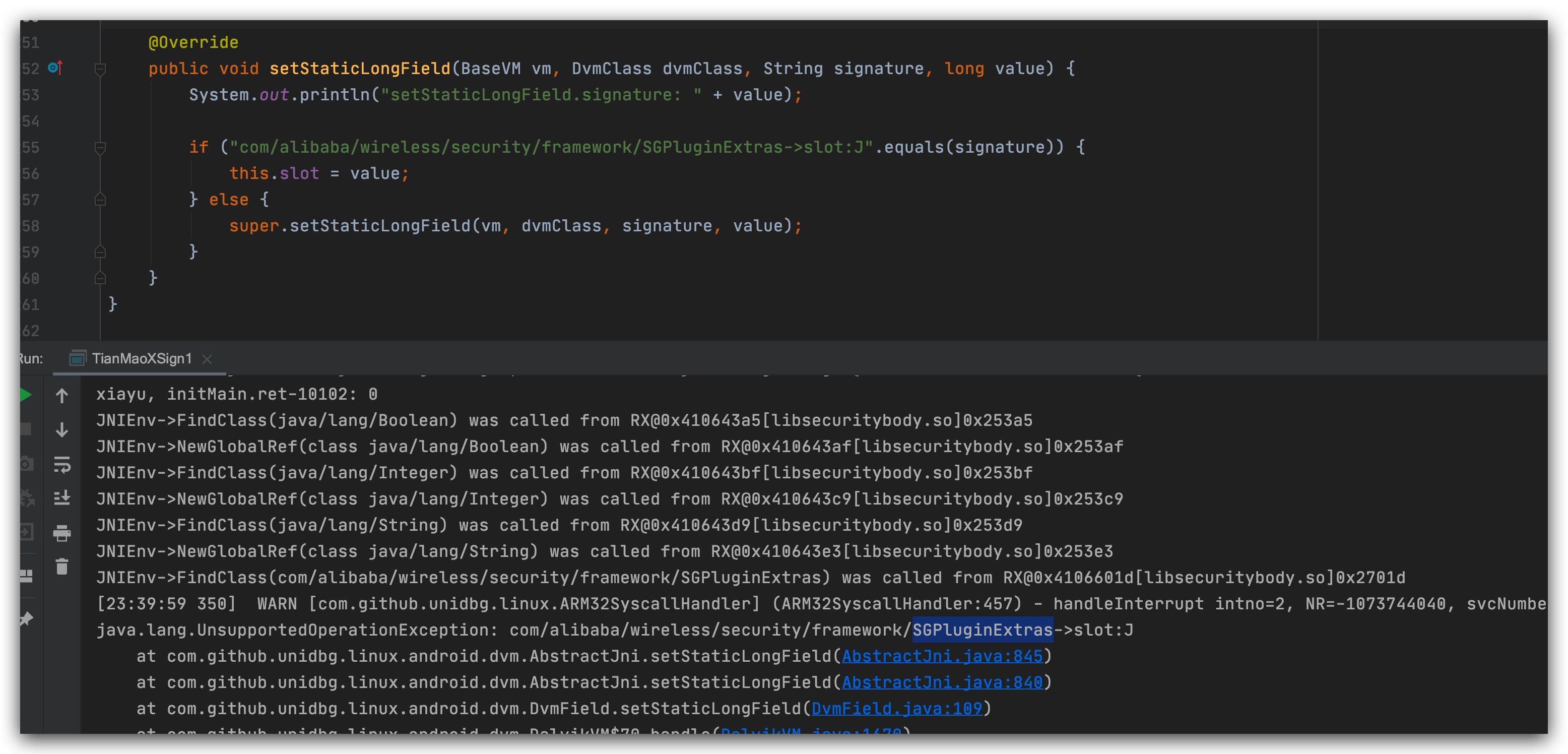
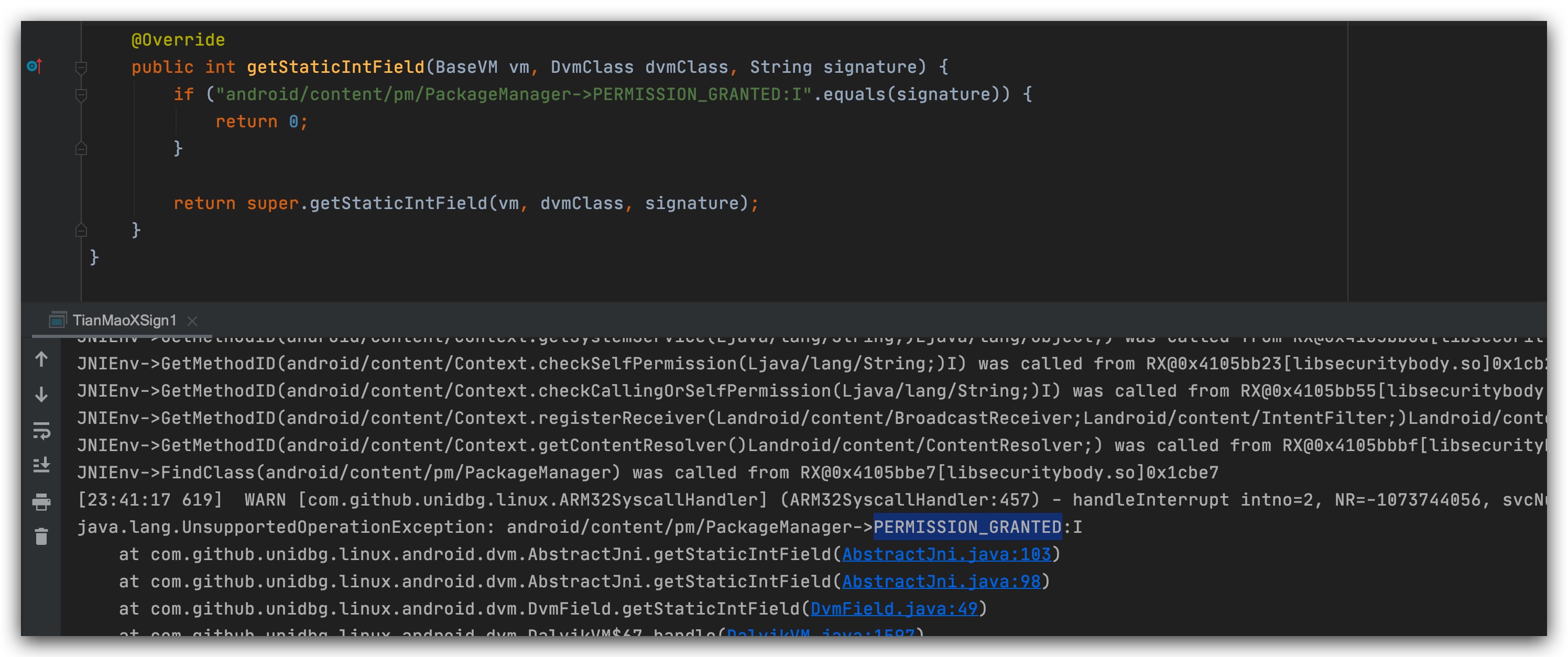
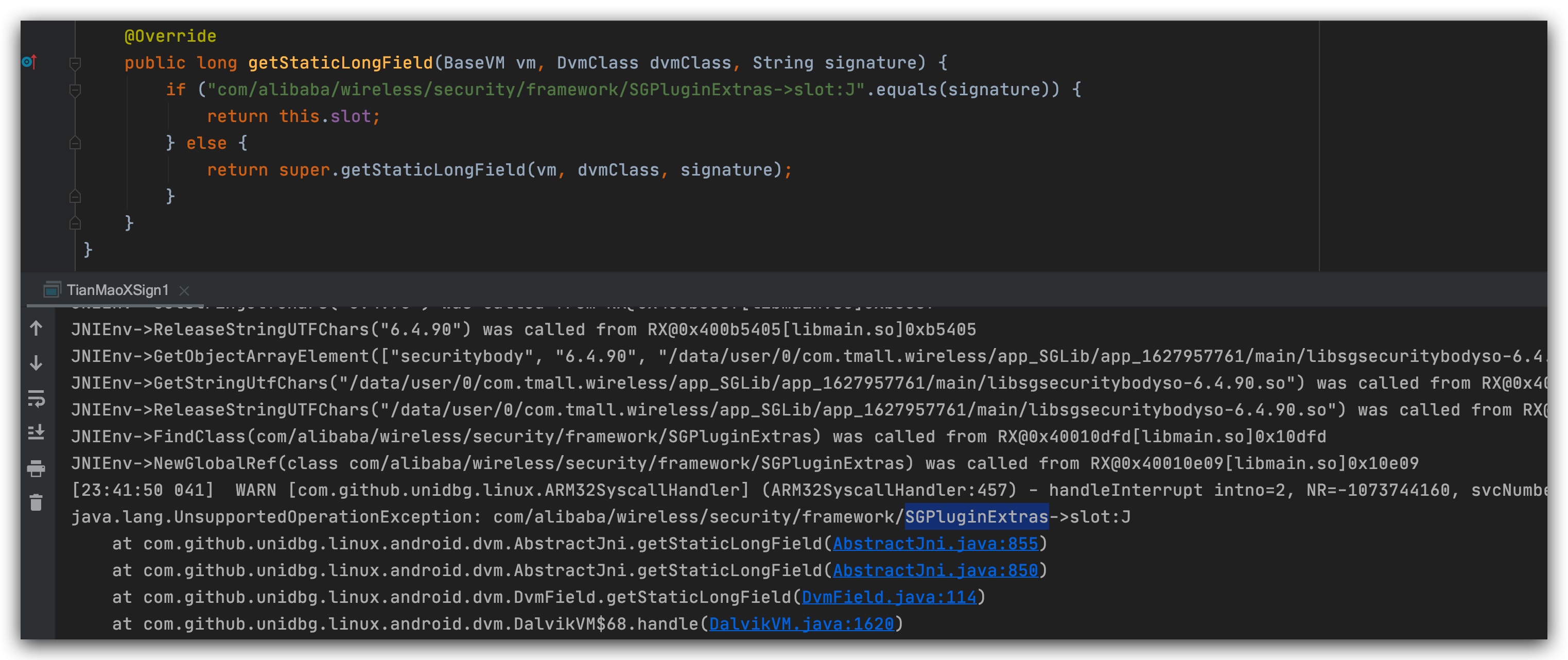
The above figure is the result of execution, but nothing else, just go
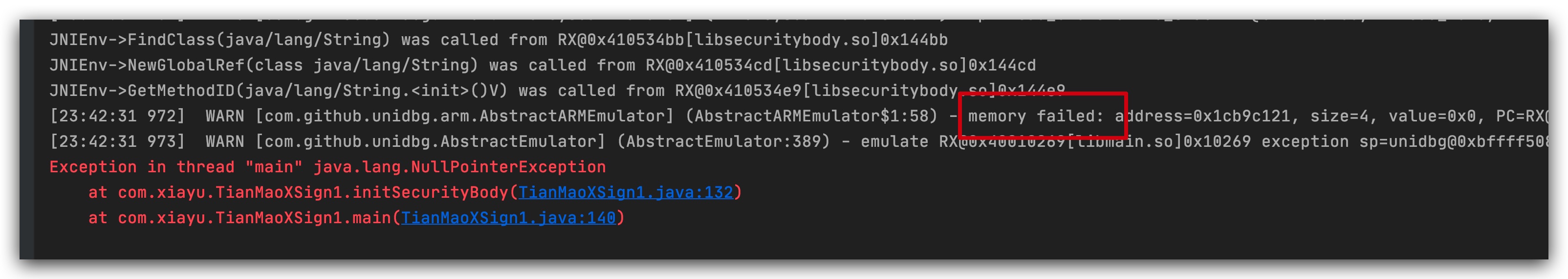
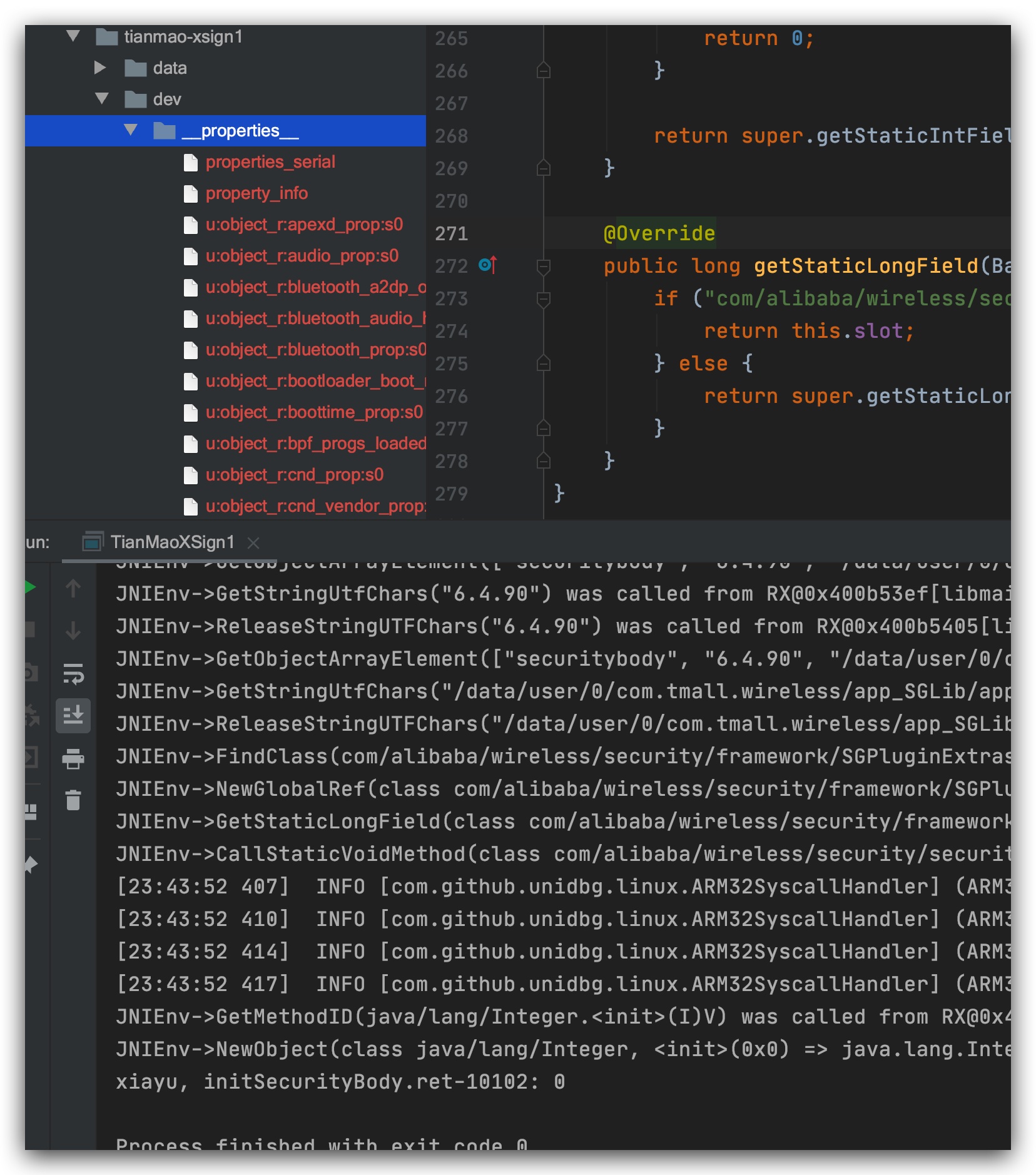
A pointer error was reported at the end of the filling, because you don't know anything, or use the same method to fill the file, after testing to fill dev/uProperties_uOkay, keep running, OK
libsgavmpso
public void initAvMp() {
DalvikModule avMp = vm.loadLibrary(sgAvMpFile, true);
avMp.callJNI_OnLoad(emulator);
ret = JNICLibrary.callStaticJniMethodObject(
emulator, methodSign, 10102,
new ArrayObject(
new StringObject(vm, "avmp"),
new StringObject(vm, "6.4.34"),
new StringObject(vm, "/data/user/0/com.tmall.wireless/app_SGLib/app_1627957761/main/libsgavmpso-6.4.34.so")
));
System.out.println("xiayu, initAvMp.ret-10102: " + ret.getValue().toString());
}
It's simple, just like the logic of appeal, let alone do anything.
get x-sign
public void getXSign() {
Map<String, String> map = new HashMap<>();
map.put("INPUT", "&&&231817&1c9d79ea8dd4bc56fb7a7727a30366&1629886&mtop.tmall.inshopsearch.searchitems&1.0&&231200@tmall_android_8.11.0&AnlJxyMxqqSURHlmKQRVnNJ8Y7la4LNiuKMrpD&&&27&&&&&&&");
DvmObject<?> ret = JNICLibrary.callStaticJniMethodObject(
emulator, methodSign, 10401,
new ArrayObject(
vm.resolveClass("java/util/HashMap").newObject(map),
new StringObject(vm, "23181017"),
DvmInteger.valueOf(vm, 7),
null,
DvmBoolean.valueOf(vm, true)
));
System.out.println("xiayu, getXSign.ret-10401: " + ret.getValue().toString());
}
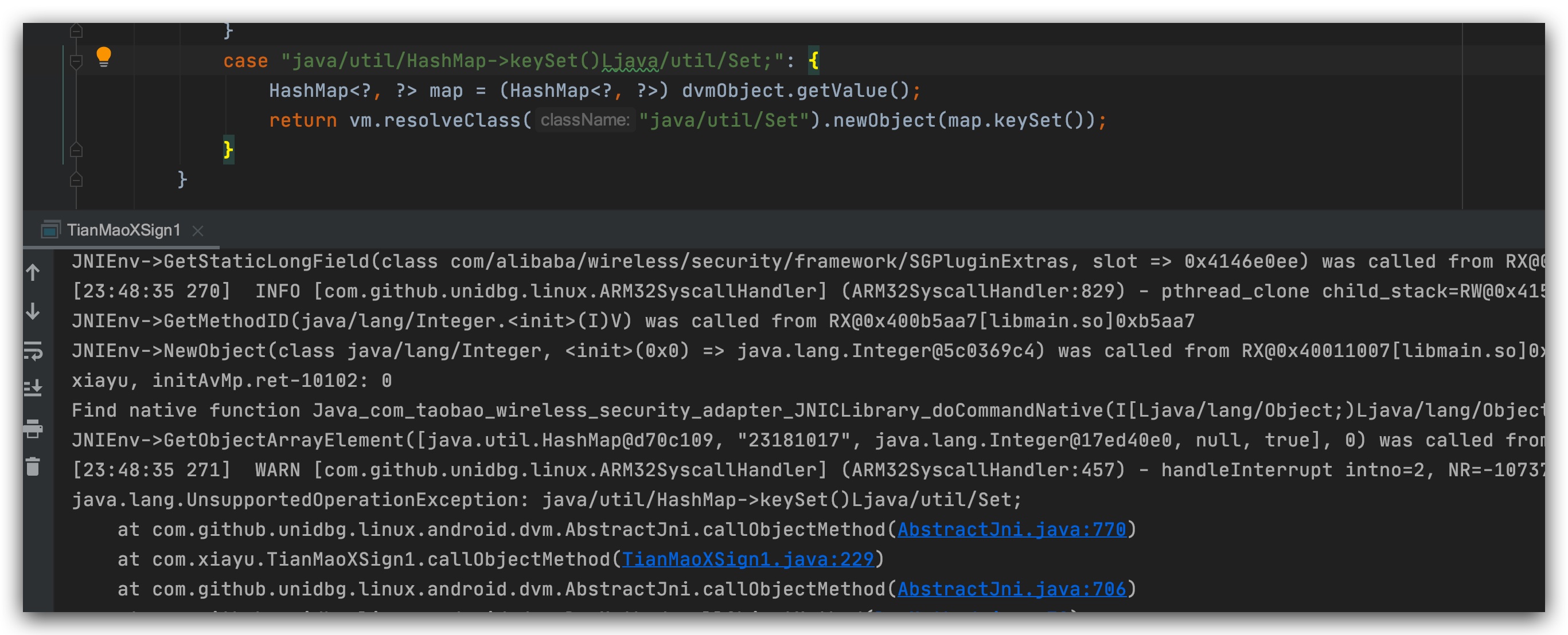
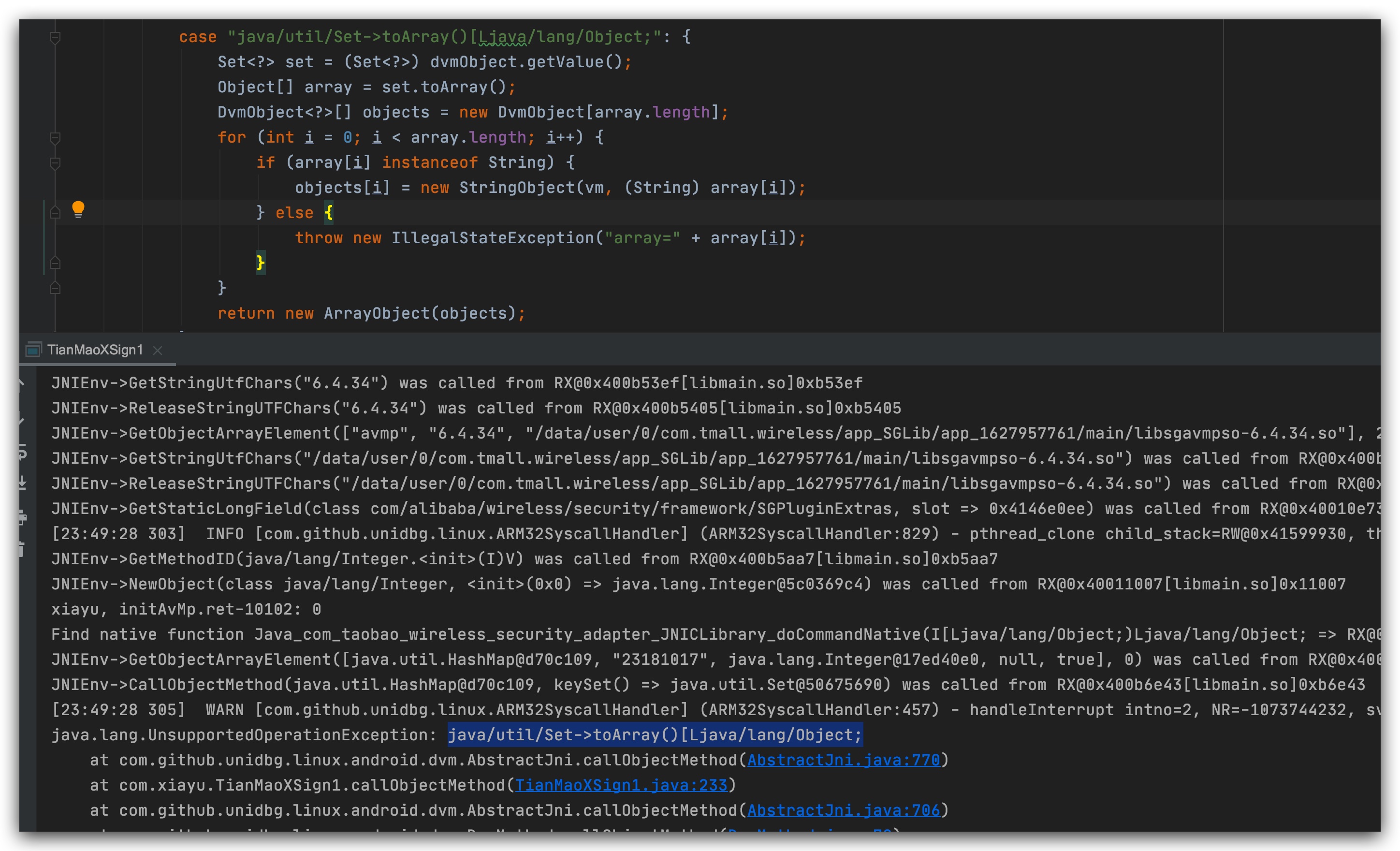
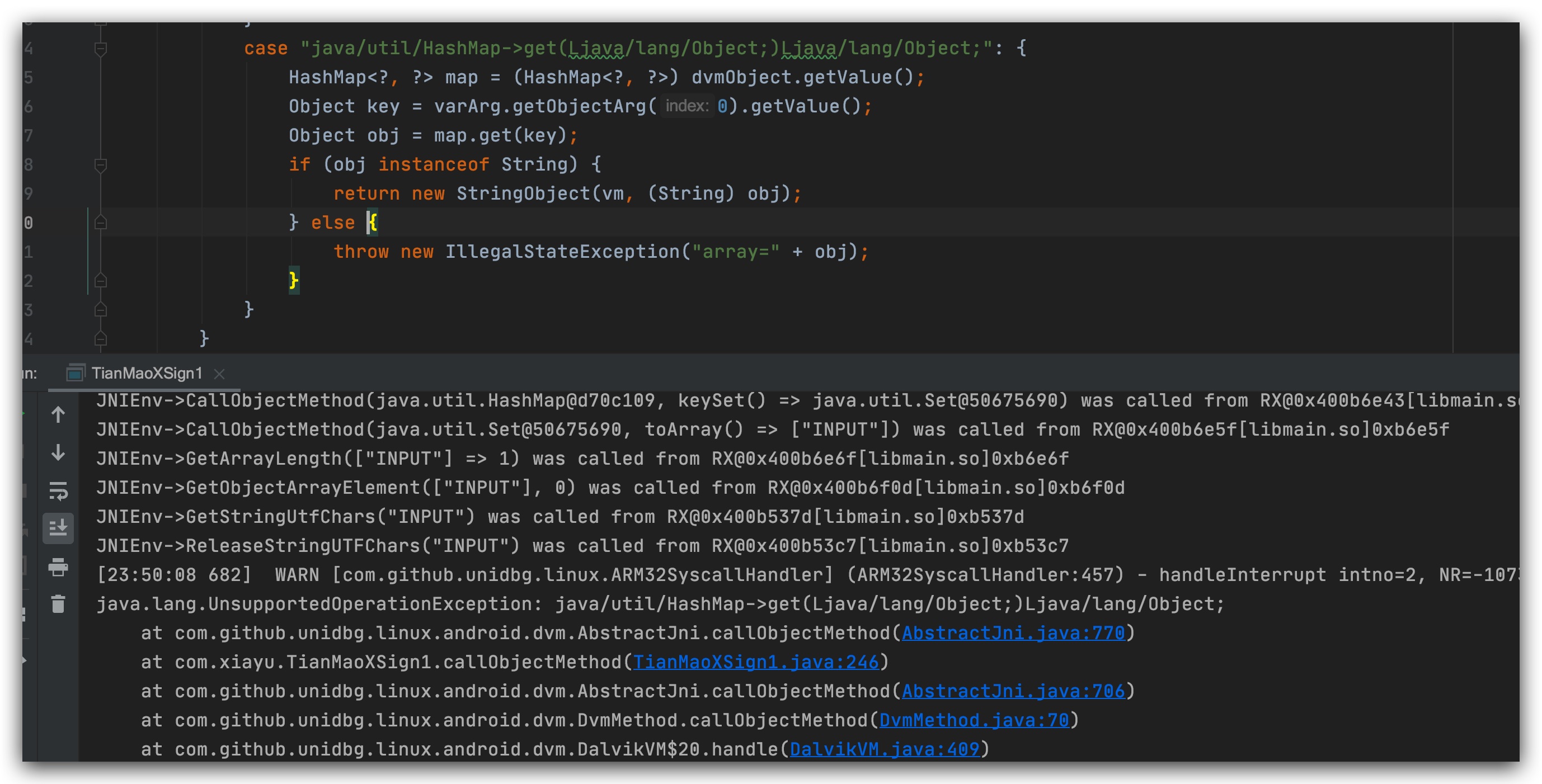
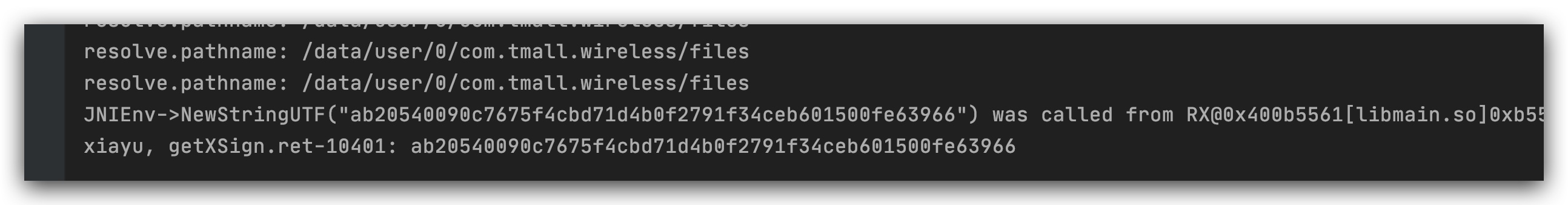
After all the above environment errors have been corrected, the result can be obtained and tested to be usable.