This article is shared from Huawei cloud community< Web vulnerability shooting range construction (OWASP Benchmark) >, author: xuuu.
Remember to talk about penetration testing on paper. In the process of learning penetration testing knowledge, we usually need a test environment containing vulnerabilities for training. In the case of unauthorized, the penetration test attack on the website involves laws and regulations, so we often need to build a vulnerability shooting range to avoid directly testing the unauthorized targets of the public network.
The vulnerability shooting range can not only help us exercise our penetration testing ability, help us analyze the formation mechanism of vulnerabilities, but also learn how to repair and improve our code ability. At the same time, it can also help us detect the effects of various vulnerability scanners.
OWASP Benchmark | OWASP Foundation shooting range is selected for this shooting range. Owasp benchmark aims to evaluate the ability of security testing tools (accuracy, coverage, scanning speed, etc.) and quantify the scanning ability of security testing tools, so as to better compare the advantages and disadvantages of various security tools.
test case
Current v1 Version 2 contains nearly 3000 vulnerabilities, covering common SQL injection, command injection, path traversal, XSS, and many security coding problems
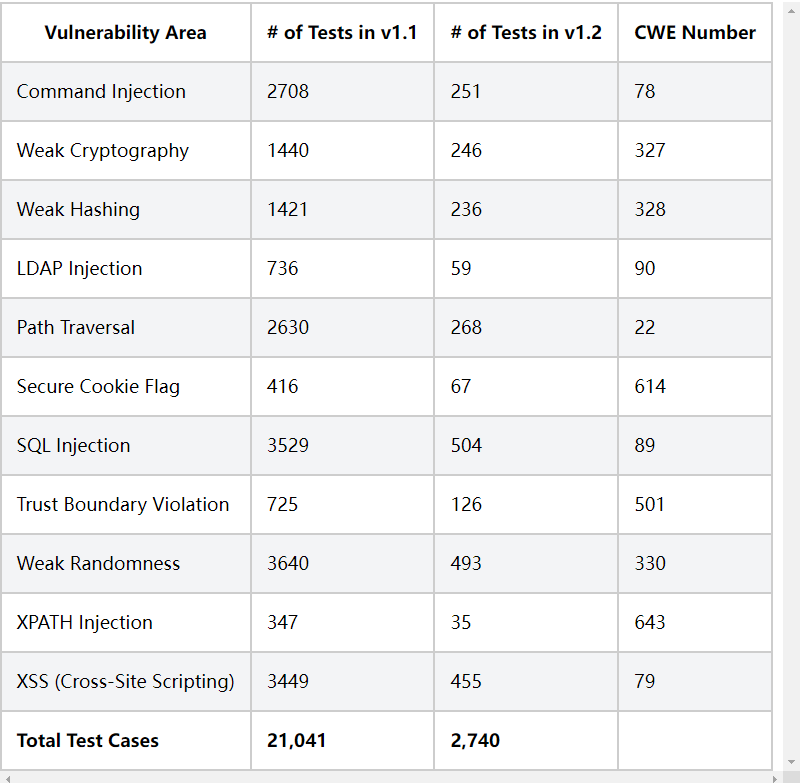
Each vulnerability contains a variety of vulnerability scenarios. For command injection, the test tool can be verified in:
- Multiple injection locations: param / data / form data / JSON / mut / header / cookie/
- Multiple call scenarios: ProcessBuilder/RuntimeExec
- Different splicing methods: controllable variables are spliced as independent commands and only as parameters of ls/echo
- Complex business process: if/else/switch makes it impossible to enter the vulnerability location (false vulnerability scenario)
And so on.
Scoring criteria
Benchmark can score the test tool according to the scan report of the test tool. All vulnerability information of benchmark range is stored in BenchmarkJava/expectedresults-1.2.csv at master · OWASP-Benchmark/BenchmarkJava , this file is used to identify the vulnerability information under each scenario. Benchmark parses the scan report of the test tool and compares it with the expected results to score each tool.
For the testing tool, we expect it to be able to
- Find all the really problematic vulnerabilities, i.e. True Positive, TP index, and the detection rate shall be as high as possible
- It can ignore all non problem vulnerabilities, namely False Positive, FP index, and the False Positive rate should be as low as possible
Benchmark will draw a graph with TP and FP as coordinate axes. When the point is closer to the upper left, it is considered that the test function capability is better.
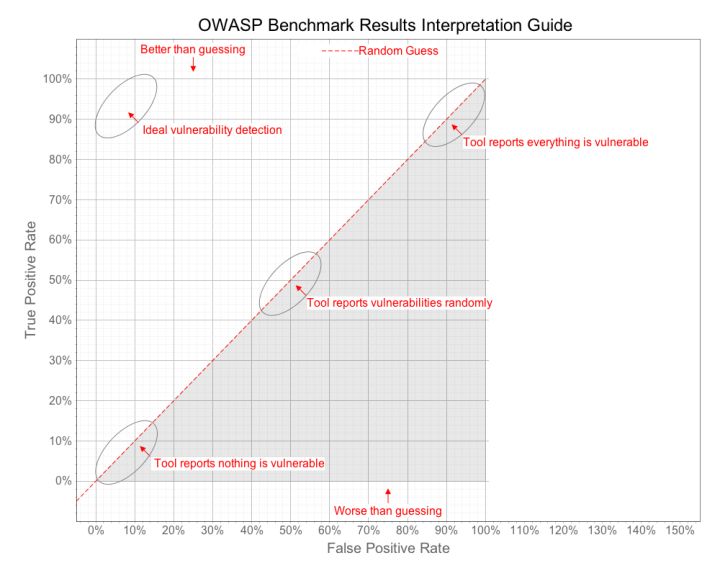
The final score of Benchmark is given with reference to the Jordan index, and the score is calculated with the following formula. The closer the score is to 11, the stronger the ability of the test tool is.
Sensitivity+Specificity-1=TP+(1-FP)-1=TP-FPSensitivity+Specificity−1=TP+(1−FP)−1=TP−FP
Scan report analysis
Benchmark currently supports most mainstream testing tools. For details, see OWASP Benchmark | OWASP Foundation page.
When evaluating test tools, you can expand them yourself OWASP-Benchmark/BenchmarkUtils: OWASP Benchmark Project Utilities - Provides scorecard generation and crawling tools for Benchmark style test suites. Org. In owasp. benchmarkutils. score. parsers. Reader class
- Override parse method: used to parse the report content
- Rewrite canRead method: used to determine which report file to parse
Analyze the url/cwe and other key information in the report to realize automatic scoring.
Demo
package org.owasp.benchmark.score.parsers;
import org.dom4j.Document;
import org.dom4j.Element;
import org.dom4j.io.SAXReader;
import java.io.File;
import java.util.List;
import java.util.regex.Matcher;
import java.util.regex.Pattern;
public class SecScanReader extends Reader {
private static final String NUMBER_PATTERN = "BenchmarkTest(\\d+)";
private static Pattern pattern;
public SecScanReader() {
pattern = Pattern.compile(NUMBER_PATTERN);
}
public boolean canRead(ResultFile resultFile) {
return resultFile.filename().endsWith(".xml") && resultFile.xmlRootNodeName().equals("XXXXXX");
}
public TestResults parse(File file) throws Exception {
TestResults tr = new TestResults("XXXXXX", true, TestResults.ToolType.DAST);
for (Object obj : issues) {
// .....
TestCaseResult tcr = new TestCaseResult();
tcr.setCategory("XSS");
tcr.setCWE(cweLookup(13));
tcr.setNumber(0001);
tr.put(tcr);
}
return tr;
}
public static int cweLookup(String pluginId) {
switch (pluginId) {
default: return 0;
}
}
}Generate scoring Report
$ mvn validate -Pbenchmarkscore -Dexec.args="expectedresults-1.2.csv results"
Deployment run
$ git clone https://github.com/OWASP-Benchmark/BenchmarkJava $ cd benchmark $ mvn compile (This compiles it) $ runRemoteAccessibleBenchmark.sh/.bat - This compiles and runs it.
The runRemoteAccessibleBenchmark script is used to open a remotely accessible Benchmark Web application.
Refernece
- OWASP Benchmark | OWASP Foundation
Welfare at the end of the article: Huawei cloud vulnerability scanning service VSS Basic limited time free experience > > >
Click follow to learn about Huawei's new cloud technology for the first time~