What is the relationship between HTTPS and HTTP? What is the HTTPS encryption process? How to integrate SSL in Websocket project? How Alibaba cloud develops HTTPS.
An overview of HTTP and HTTPS
1.1 HTTP protocol
-
summary
The first version of HTTP can only transfer hypertext markup language (HTML) files, so it is called hypertext transfer protocol. -
features
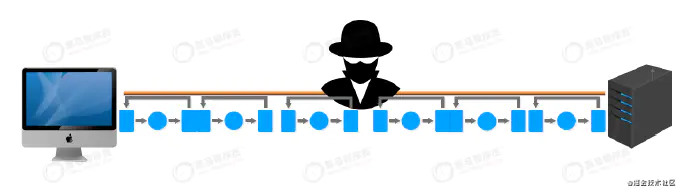
A is a request response stateless application layer protocol.
b based on TCP/IP protocol family to transmit (plaintext) data, all WWS must comply with this standard.

Explanation above
Domain name: represents different pages in the website. Communication protocol: the language of communication between browser and server.
-
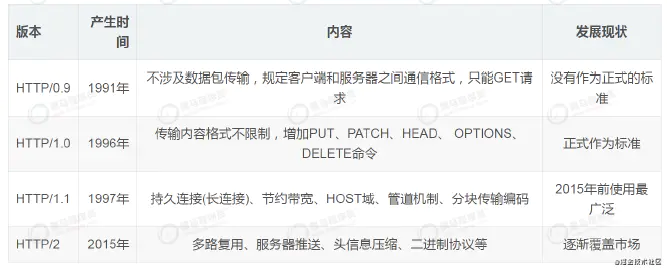
HTTP history
1.2 HTTPS
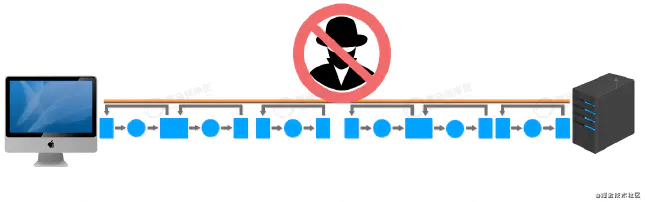
HTTPS (Chinese name is hypertext security protocol) adds SSL layer based on HTTP. SSL is the detailed content of encryption (data encryption and identity authentication).
That is, it can be understood as encrypting data before data transmission for HTTP upgrade.
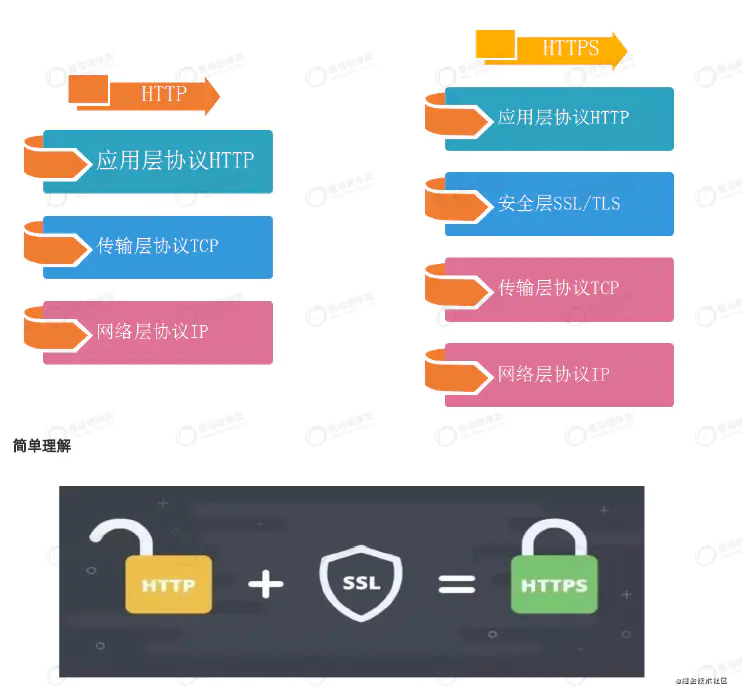
- Difference between HTTPS and HTTP
1,https The agreement requires application CA,certificate,http No certificate required 2,http It is hypertext transfer protocol, and information is plaintext transmission, https Is safe ssl/tls Encrypted transport protocol. 3,http and https The connection mode is completely different, and the port used is also different. The former is 80 and the latter is 443. 4,http The connection of is simple and stateless; HTTPS The agreement is made by SSL/TLS+HTTP Encrypted transmission protocol 5,http Directly interact with the four layers, https First interact with the security layer, and then interact with the four layers
Analysis of encryption principle and algorithm
2.1 SSL and TLS
-
summary
SSL (secure socket protocol) and its successor TLS (Transport Layer Security) provide security and data integrity for network communication
A security protocol. SSL and TLS encrypt network connections between the transport layer and the application layer. -
TLS (Transport Layer Security) history
a Formerly SSL,First several versions(SSL1.0,SSL2.0,SSL3.0). b 1999 Year from 3.1 Begin to be IETF It has been standardized and renamed for several years TLS1.0,TLS1.1,TLS1.2 Three versions. c TLS1.3 Changes will be better than xia It is relatively large and has not been popularized on a large scale. At present, the most widely used is TLS 1.2.
2.2 encryption details
2.2.1 general
visit www.taobao.com
-
Access process
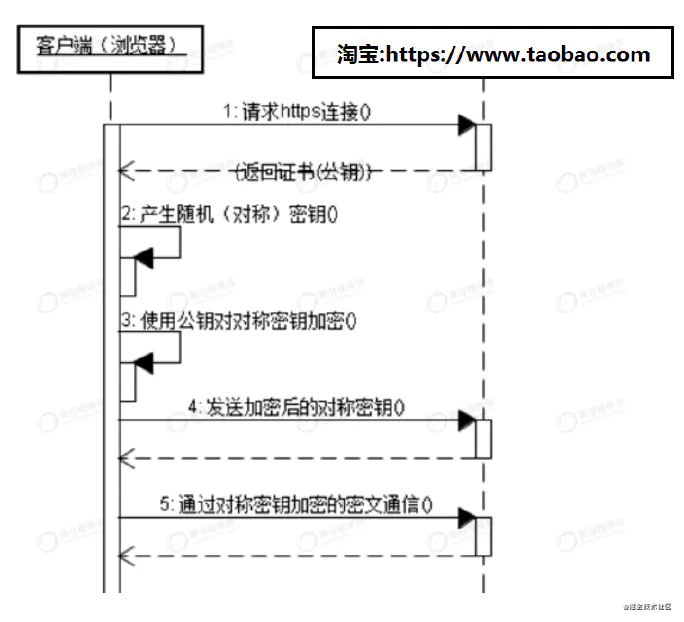
Description above
a obtains the public key from the server first.
b generate a symmetric encrypted key.
c public key encrypts the symmetric key and passes it to the server.
d the server decrypts with the private key to obtain the symmetric encryption key.
e the client encrypts the data with a symmetric key and then transmits it to the server. The server decrypts and obtains the original data with a symmetric key.
Conclusion: symmetric encryption is used in the process of data transmission because of its high efficiency. The symmetric key generated by the client is passed to the server.
In order to ensure the security of symmetric key,Therefore, the symmetric key is asymmetrically encrypted and transmitted to the server. Then the server will
Get symmetric key.
-
Analysis of encryption algorithm
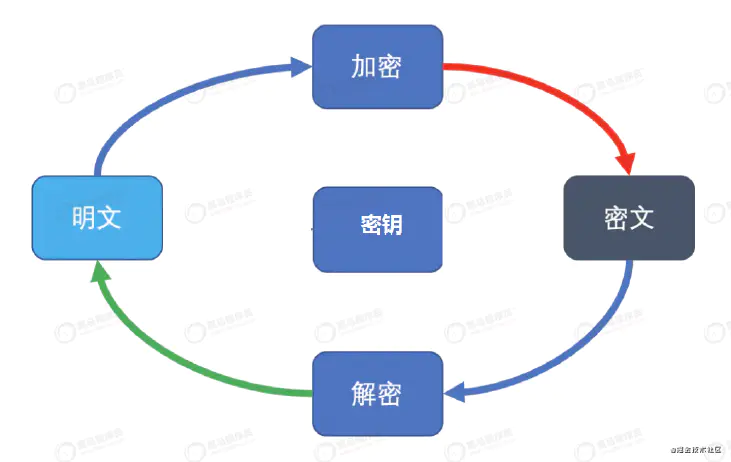
To establish a cryptosystem, five spaces are required (described above)
Plaintext M: Information before encryption or after decryption; ciphertext C: Information encrypted in plaintext; secret key K: It is composed of encryption key and decryption key; encryption E: Transformation from plaintext to ciphertext; decrypt D: Transformation from ciphertext to plaintext
2.2.2 encryption algorithm
2.2.2.1 symmetric encryption
-
describe
Also known as single key encryption, it means that encryption and decryption use the same key. -
advantage
Encryption and decryption are fast and efficient. Representative algorithms: AES algorithm, DES algorithm, RC4, 3DES, Triple DES, RC2, etc; -
characteristic
The sender and receiver share the same key to communicate, which ensures the security to a certain extent.
For enumeration attacks, the longer the password length, the harder it is to crack -
case
0010101010101010 plaintext
0001010001011 secret key
0011111011100001 ciphertext (after XOR)
0010101010101010 plaintext (after decryption)
2.2.2.2 asymmetric encryption
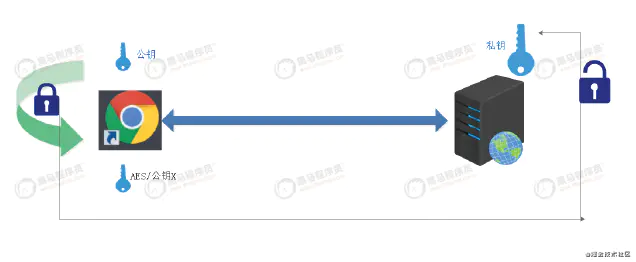
-
describe
The encryption and decryption keys are different, which are called public key and private key respectively. The public key and algorithm are public, and the private key is confidential. -
excellent vacancy
Low computing performance, limited length of encrypted data and strong security. For example: RSA, DSA, ECDSA, DH, ECDHE; -
characteristic
Only a specific host has a private key to ensure data security.
Solve the problem of inconvenient key management of symmetric encryption. -
Difference between symmetric and asymmetric
Symmetric encryption has high efficiency, but its security cannot be guaranteed in key management and key exchange. Therefore, the network environment is a mixture of the two.
2.2.2.3 hash encryption
-
describe
The algorithm is irreversible. Users can generate a unique hash value of a specific length for the target information through the hash algorithm.
However, the target information cannot be retrieved through this hash value. -
Common algorithms
MD5, SHA-1, SHA-2, SHA-256, etc
2.3 CA certificate
-
definition
CA certificate, as its name implies, is a digital certificate issued by Ca (Certification Authority, also known as "certificate authorization center"). -
What does the certificate contain
Issuer, user, version, signature algorithm, user, public key, fingerprint, fingerprint algorithm, etc. -
Coding format
10. In 509 specification, PEM format is generally recommended to store certificate related files. The file name suffix of the certificate file is usually. crt or. cer
The file name suffix of the corresponding private key file is generally. Key. The file name suffix of the certificate request file is. csr. Sometimes pem is used as
File name suffix. -
Certificate (browse to understand)
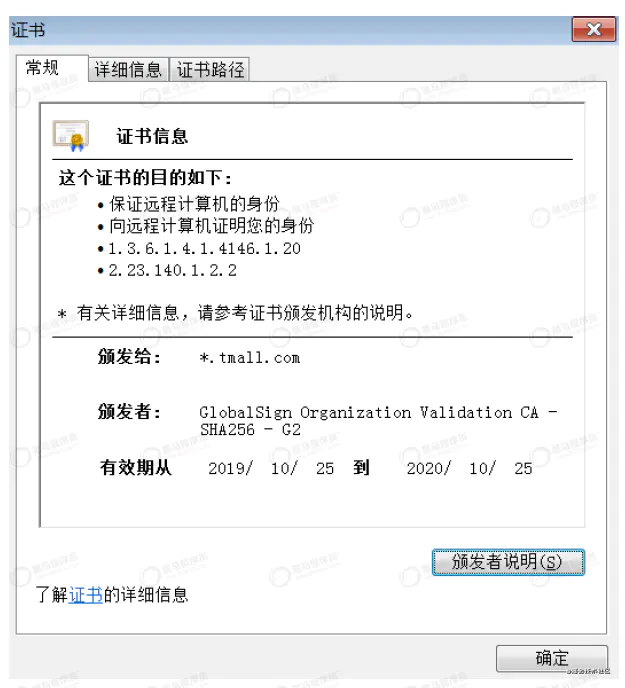
Version number(Version Number): CA The certificate is a specification version number, which is currently version 3 and the value is 0 x2; Serial number( Serial Number): from CA It is maintained. Each certificate issued by it is assigned a serial number to track and revoke the certificate As long as you have the issuer information and serial number, you can uniquely identify a certificate, with a maximum of 20 bytes; Signature algorithm( Signature Algorithm): Algorithms used for digital signature, such as: sha256-with-RSA-Encryption ccdsa-with-SHA2S6; Issuer( Issuer): Identification information of the certificate issuing unit, such as " C=CN,ST=Beijing, L=Beijing, O=org.example.com,CN=ca.org. example.com "; term of validity(Validity): The validity period of the certificate is very long, including the start and end time.
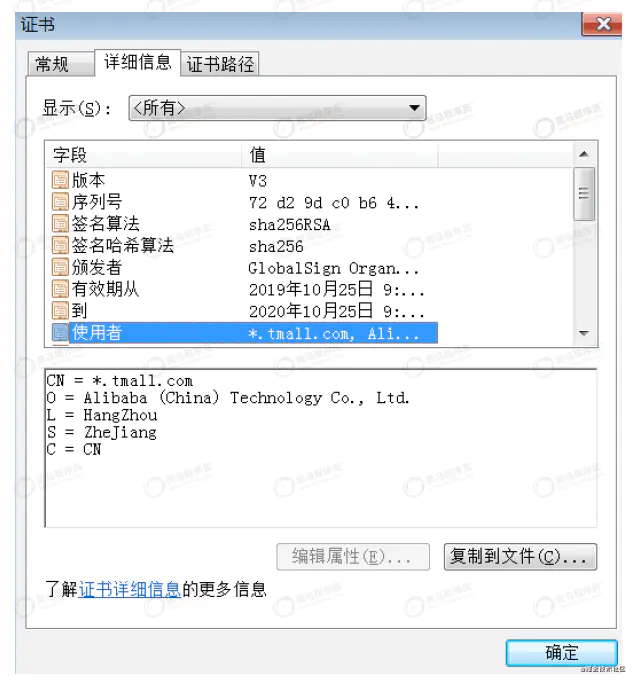
The server provides the public key of the server to the ca organization to generate a certificate. The certificate generally includes the following contents:
◆Issuer (Certificate issuing authority) ◆Valid from , Valid to (Validity of certificate) ◆Public key (Public key) ◆Subject (Subject, user) ◆Signature algorithm (Algorithm used for signature) ◆Thumbprint, Thumbprint algorithm (Fingerprint and fingerprint algorithm)
- Certificate generation process
hold Issuer (Certificate issuing authority),Public key (Public key),Subject (theme),Valid from,Valid to(Validity of certificate)Such information is written into the certificate in clear text as the content, and then a fingerprint algorithm is used (Taobao is sha1)calculation A fingerprint (that is, signature) of the contents of these digital certificates is generated, and the fingerprint and fingerprint algorithm are encrypted with their own private key, and then generated certificate