During the last check of the server application operation, a large number of unusual directional accesses (a large amount of traffic) were found in the application log, and the network card outlet load was abnormal. Therefore, the incoming and outgoing traffic is checked through netstat, and the garbage traffic address is shielded by iptables to reduce the application running load and improve the running experience. (you can also write your own shell to automatically shield the same access with large traffic, but it may affect user access. This article introduces the manual operation method to deal with common attacks.)
Install iptables
The demo environment is Ubuntu 18.04
$ apt-get install iptables -y
View iptables version
$ iptables -V
Use netstat to check traffic
Check the ip connection of a specific port
Take the application running on port 80 as an example List the ip addresses that port 80 is being accessed by
$ netstat -tun | grep ":80"
List the ip addresses of the top 10 accessing port 80 and display the number of connections
$ netstat -antp | awk '$4 ~ /:80$/ {print $4" "$5}' | awk '{print $2}'|awk -F : {'print $1'} | uniq -c | sort -nr | head -n 10List all ip addresses accessing port 80 and display the number of connections
$ netstat -plan|grep :80|awk {'print $5'}|cut -d: -f 1|sort|uniq -c|sort -nk 1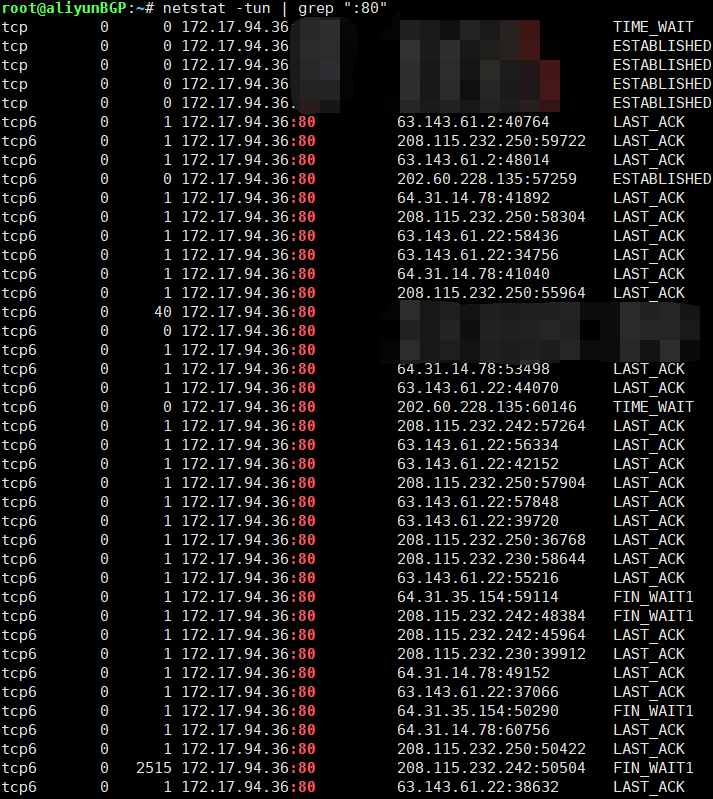
All connections
Show all network activity
$ netstat -na
Displays ip addresses with a large number of connections
$ netstat -an|awk -F: '{print $2}'|sort|uniq -c|sort -nr|headList all ip addresses that have passed
$ netstat -n -p | grep SYN_REC | sort -u
Calculate the number of connections initiated by each ip
$ netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nUse iptables to mask specific access
Displays the current firewall rules
Display rules as host names
$ iptables -L
Display rules as ip
$ iptables -L -n
Mask specific ip
$ iptables -I INPUT -s ***.***.***.*** -j DROP
for example
$ iptables -I INPUT -s 202.60.228.135 -j DROP $ iptables -I INPUT -s 47.112.148.83 -j DROP $ iptables -I INPUT -s 208.115.232.242 -j DROP $ iptables -I INPUT -s 63.143.61.22 -j DROP
Mask an ip segment
If the maliciously accessed ip comes from the same computer room, the ip segment of the computer room can be directly shielded
$ iptables -I INPUT -s ***.***.***.***/24 -j DROP
for example
$ iptables -I INPUT -s 1.2.3.0/24 -j DROP
Release masked ip
$ iptables -D INPUT -s ***.***.***.*** -j DROP
ditto
After configuration, you can use iptables -L -n to check the rules
Firewall operation
Use iptables save to save this modification Configure the last firewall rule that takes effect automatically every time you start
$ iptables-save > /etc/iptables.rules
Edit the / etc/network/interfaces file and add
pre-up iptables-restore < /etc/iptables.rules
After modifying iptables rules, execute iptables save > / etc / iptables Rules to save rules.
iptables help
$ iptables --help
iptables v1.6.1
Usage: iptables -[ACD] chain rule-specification [options]
iptables -I chain [rulenum] rule-specification [options]
iptables -R chain rulenum rule-specification [options]
iptables -D chain rulenum [options]
iptables -[LS] [chain [rulenum]] [options]
iptables -[FZ] [chain] [options]
iptables -[NX] chain
iptables -E old-chain-name new-chain-name
iptables -P chain target [options]
iptables -h (print this help information)
Commands:
Either long or short options are allowed.
--append -A chain Append to chain
--check -C chain Check for the existence of a rule
--delete -D chain Delete matching rule from chain
--delete -D chain rulenum
Delete rule rulenum (1 = first) from chain
--insert -I chain [rulenum]
Insert in chain as rulenum (default 1=first)
--replace -R chain rulenum
Replace rule rulenum (1 = first) in chain
--list -L [chain [rulenum]]
List the rules in a chain or all chains
--list-rules -S [chain [rulenum]]
Print the rules in a chain or all chains
--flush -F [chain] Delete all rules in chain or all chains
--zero -Z [chain [rulenum]]
Zero counters in chain or all chains
--new -N chain Create a new user-defined chain
--delete-chain
-X [chain] Delete a user-defined chain
--policy -P chain target
Change policy on chain to target
--rename-chain
-E old-chain new-chain
Change chain name, (moving any references)
Options:
--ipv4 -4 Nothing (line is ignored by ip6tables-restore)
--ipv6 -6 Error (line is ignored by iptables-restore)
[!] --protocol -p proto protocol: by number or name, eg. `tcp'
[!] --source -s address[/mask][...]
source specification
[!] --destination -d address[/mask][...]
destination specification
[!] --in-interface -i input name[+]
network interface name ([+] for wildcard)
--jump -j target
target for rule (may load target extension)
--goto -g chain
jump to chain with no return
--match -m match
extended match (may load extension)
--numeric -n numeric output of addresses and ports
[!] --out-interface -o output name[+]
network interface name ([+] for wildcard)
--table -t table table to manipulate (default: `filter')
--verbose -v verbose mode
--wait -w [seconds] maximum wait to acquire xtables lock before give up
--wait-interval -W [usecs] wait time to try to acquire xtables lock
default is 1 second
--line-numbers print line numbers when listing
--exact -x expand numbers (display exact values)
[!] --fragment -f match second or further fragments only
--modprobe=<command> try to insert modules using this command
--set-counters PKTS BYTES set the counter during insert/append
[!] --version -V print package version.reference resources: https://help.ubuntu.com/community/IptablesHowTo