brief introduction
- Weave is a solution developed by weaveworks to solve Docker cross host network. It can create a virtual network to connect Docker containers deployed on multiple hosts. In this way, the container is like being connected to the same network switch. Those applications using the network do not have to configure port mapping, links and other information
- External devices can access the services provided by the application container on the weave network, and existing internal systems can also be exposed to the application container. Weave can penetrate the firewall and run on partially connected networks. In addition, weave communication supports encryption, so users can connect to the host from an untrusted network.
- For containers, weave is like a huge Ethernet switch. All containers are connected to this switch. Containers can communicate directly without NAT and port mapping. In addition, weave's DNS module enables containers to be accessed through hostname
- Weave does not rely on distributed databases (e.g. etcd and consumer) exchange network information. A cross host container network can be established only by running the weave component on each host. However, it is also its disadvantage: the host cannot dynamically join the node network, and can only manually join the weave network through weave launch or connect. It does not support dynamic IP allocation, and all IPS need to be manually managed and allocated, which is difficult to ensure that the allocated IP does not change Conflict.
- Project address: https://github.com/weaveworks/weave
weave network communication model
-
weave starts the virtual router on each host of the docker cluster, takes the host as the router, and forms an interconnected network topology. On this basis, it realizes the cross host communication of the container. See the following figure for the host network topology
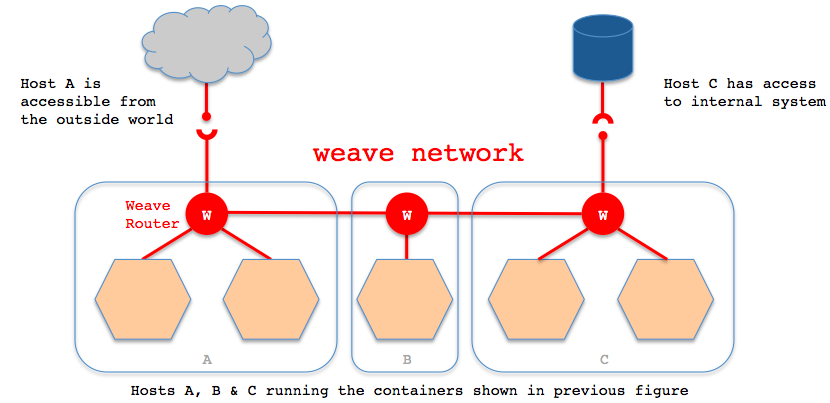
-
A W (i.e. weave router, which can also be deployed as a container) is deployed on each host deploying Docker. The weave network is composed of peer-to-peer endpoints composed of these weave routers, and the network topology can be customized through the weave command line.
-
TCP and UDP connections will be established between each host deployed with weave router to ensure the passage of control surface traffic and data surface traffic between weave routers. The control plane is composed of TCP connections established between weave routers, through which handshake and topological relationship information exchange and communication are carried out. The communication of the control surface can be configured as encrypted communication. The data plane is composed of UDP connections established between weave routers, and most of these connections will be encrypted. These connections are full duplex and can cross the firewall
-
When the container communicates across hosts through weave, its network communication model can refer to the following figure. For each container in the weave network, weave will create a bridge, and create a veth pair between the bridge and each container. One end is added to the container's network namespace as a container network card, and the container network card is configured with ip and corresponding mask. One end is connected to the bridge, and finally the traffic is forwarded to the opposite host through the weave router on the host.
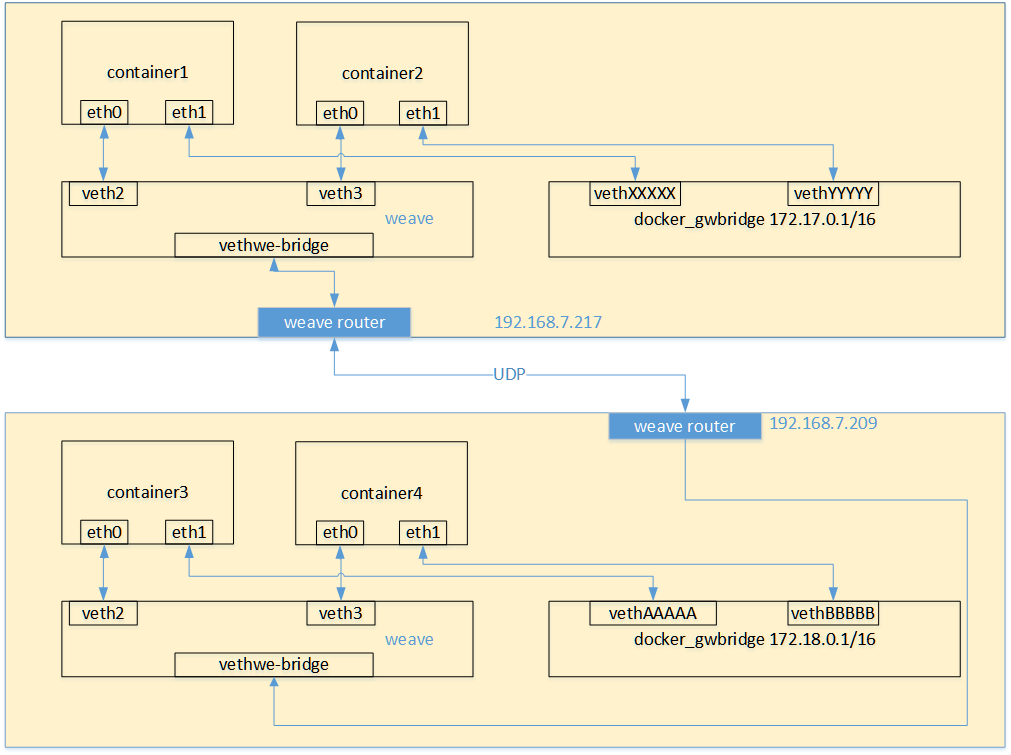
-
Basic process
- The container traffic reaches the weave router bridge on the host through the veth pair.
- In the hybrid mode, the weave router uses pcap to intercept network packets on the bridge and exclude the data traffic directly forwarded by the kernel through the bridge, such as the data within the subnet, between local containers, and between the host and local containers. The captured packets are forwarded to the weave router end of other hosts through UDP.
- At the receiving end, the weave router injects packets into the interface on the bridge through pcap, and distributes traffic to the network card of the container through the veth pair on the bridge. By default, weave hosts packets between containers based on UDP, and can completely customize the network topology of the whole cluster. However, from the perspective of performance and use, it still has major defects:
- The packet unpacking method of weave custom container packets is not universal enough, the transmission efficiency is relatively low, and the performance loss is relatively large.
- The cluster configuration compares the load, and the network topology needs to be built manually through the weave command line. In the case of large-scale clusters, it increases the burden of administrators.
-
Network card device
- Container eth0: eth0 is the default network of the container host. It mainly provides services provided by the container to access the external network. It follows the default docker network architecture, but it creates docker_gwbridge this bridge.
- docker_gwbridge: docker_ Gwbridge is a bridge created by the container, which replaces the service of docker0.
- Container ethwe: it is a veth pair virtual device pair, a network virtual network card that communicates with other containers.
- We bridge: a weave bridge created by ethwe device pairs. Specific IP and gateway assigned within the bridge.
- Weave: weave bridge, which finds the target through the route routing table and forwards the data packet to the opposite port node through the port.
- eth0: the real machine network card is connected with the external network card. It is used to forward the data packets of VXLAN and NAT network card types to the specified opposite node.
install
-
Weave does not need centralized key value storage, and can be installed directly
-
Installation environment:
- Linux kernel 3.8 and above
- docker 1.10.0 and above
- If there is a firewall between nodes, TCP 6783 and UDP 6783/6784 ports must be released to each other, which are Weave control and data ports.
- Host names cannot be the same
-
install
$ sudo curl -L https://git.io/weave -o /usr/local/bin/weave $ sudo chmod a+x /usr/local/bin/weave Test for successful installation $ weave version weave script 2.8.1 weave 2.8.1
-
Initialize Weave network
1. Install prerequisite dependencies $ yum install -y bridge-utils net-tools 2. This command is to run a command in the container weave router,This service needs to be enabled on each host. The service requires three docker Container to assist operation,The first run will automatically download the relevant image $ weave launch Or use weave setup Preload mirror Set the environment variable so that docker The container started from the command line is automatically connected to the weave In the network. $ eval $(weave env) 3. View downloaded and running containers $ docker ps weaveworks/weaveexec 2.8.1 e02bec83a27c 7 months ago 71.2MB weaveworks/weave 2.8.1 8de39aae7c4e 7 months ago 61.2MB weaveworks/weavedb latest 19661b1dbf28 8 months ago 698B 4. It also generates a name called weave Network bridge,docker0 Is the default. View Bridge $ brctl show bridge name bridge id STP enabled interfaces docker0 8000.02429362485b no weave 8000.4231bec3cf76 no vethwe-bridge $ ifconfig weave weave: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1376 inet6 fe80::4031:beff:fec3:cf76 prefixlen 64 scopeid 0x20<link> ether 42:31:be:c3:cf:76 txqueuelen 1000 (Ethernet) RX packets 14 bytes 936 (936.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 7 bytes 634 (634.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 docker A user interface is also generated in weave Custom network for the bridge. $ docker network ls docker network ls NETWORK ID NAME DRIVER SCOPE 3dbd79b0c831 bridge bridge local b31f13c07393 host host local bc7e4b7556c4 none null local 468375b4740b weave weavemesh local 5. weave The data is stored on each machine assigned a name of weavedb On the container, It's a data volume Container, which is only responsible for data persistence.
Connecting different hosts
-
Machine: turn off the firewall of both machines. If you turn on the firewall, you need to open port 6783
host name IP address software environment docker1 192.168.100.140 Weave,Docker Docker2 192.168.100.141 Weave,Docker -
Connect from docker1 to docker2. Just follow the weave launch with the ip or hostname of the docker2 host. The two machines will automatically establish a cluster and synchronize all the required information.
1. stay docker1(192.168.100.140)Upper execution This command is equivalent to starting locally weave route,Pass again weave connect 192.168.100.141 come and $ weave launch 192.168.100.141 29d7b8b5740b71e065beb4fef1e86b904aa4e776a6c855b28aee6c270a5de3b9 2. stay docker2(192.168.100.141)Upper execution $ weave launch 192.168.100.140 3. View status information $ weave status Version: 2.8.1 (up to date; next check at 2021/09/21 17:04:19) Service: router Protocol: weave 1..2 Name: fe:f7:46:79:0c:d7(docker1) Encryption: disabled PeerDiscovery: enabled Targets: 1 Connections: 1 (1 established) # Establish connection Peers: 2 (with 2 established connections) # 2 means there are two nodes TrustedSubnets: none Service: ipam Status: ready Range: 10.32.0.0/12 DefaultSubnet: 10.32.0.0/12 Service: dns Domain: weave.local. Upstream: 192.168.100.2 TTL: 1 Entries: 6 Service: proxy Address: unix:///var/run/weave/weave.sock Service: plugin (legacy) DriverName: weave 4. View status details $ weave status connections -
If you want to connect to a new host
$ weave connect $NEW_HOST
-
Disconnect
$ weave forget $HOST
-
stop it
$ weave stop
Integrated Docker
-
Weave and Docker are integrated so that the running container runs in the weave network.
- Modify dokcer using the weave env command_ The value of the host environment variable enables docker client to interact with weave, and weave interacts with docker daemon to automatically configure the network for the container, which is transparent to users.
- Using the weave plugin, use the -- net=weave parameter when running the container.
-
Method 1: use weave env
1. to configure Weave Net Environment in order to pass Docker Command line initiated containers are automatically attached to Weave network $ eval $(weave env) $ docker run -it --rm --name docker1-busybox busybox $ docker run -it --rm --name docker1-busybox busybox
-
Method 2: directly run the container using the weave plugin
1. stay docker1 Upper boot container $ docker run -it --rm --net=weave --name docker1-busybox busybox 2. stay docker2 Upper boot container $ docker run -it --rm --net=weave --name docker2-busybox busybox 3. You can see in the container that there will be one more network card ethwe0 docker1 lower $ ifconfig ...ellipsis... ethwe0 Link encap:Ethernet HWaddr 7E:CA:30:FC:3E:8B inet addr:10.40.0.0 Bcast:10.47.255.255 Mask:255.240.0.0 UP BROADCAST RUNNING MULTICAST MTU:1376 Metric:1 RX packets:16 errors:0 dropped:0 overruns:0 frame:0 TX packets:11 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:1244 (1.2 KiB) TX bytes:798 (798.0 B) ...ellipsis... docker2 lower $ ifconfig ...ellipsis... ethwe0 Link encap:Ethernet HWaddr C2:97:2B:BF:7E:A2 inet addr:10.32.0.1 Bcast:10.47.255.255 Mask:255.240.0.0 UP BROADCAST RUNNING MULTICAST MTU:1376 Metric:1 RX packets:17 errors:0 dropped:0 overruns:0 frame:0 TX packets:11 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:1342 (1.3 KiB) TX bytes:798 (798.0 B) ...ellipsis... -
By default, weave's DNS will not be used, so it cannot be accessed with the container name. If you want to use the container host name, do the following:
If specified when creating the container--name Parameters, registered in DNS When or with hostname Priority. $ docker run -it --rm --net=weave --name docker1-busybox -h c1.weave.local $(weave dns-args) busybox $ docker run -it --rm --net=weave --name docker2-busybox -h c2.weave.local $(weave dns-args) busybox stay docker The following methods can be used ping c1 ping c2 ping docker1-busybox ping docker2-busybox View on host $ weave dns-lookup c1.weave.local 10.40.0.0 $ weave dns-lookup c2.weave.local 10.32.0.1
-
View local domain
$ weave status ...ellipsis... Service: dns Domain: weave.local. Upstream: 192.168.100.2 TTL: 1 Entries: 4 ...ellipsis... -
Modify local domain
$ weave launch --dns-domain="cluster.local."
-
Load balancing can be provided through DNS
1. Start multiple containers(c2.weave.local) $ docker run --net=weave --rm --name docker21-busybox -h c2.weave.local $(weave dns-args) -ti busybox $ weave dns-lookup c2.weave.local 10.32.0.1 10.32.0.2
skill
-
Manual IP allocation: weave will ensure that the container IP is unique, and is automatically responsible for the allocation and recycling of container IP. You don't need to configure anything to get this benefit. If you have specific requirements for allocation, you can also customize the allocation of IP network segments. The default network segment used by weave is 10.32 0.0/12, i.e. from 10.32 0.0 to 10.47 255.255. If this network segment is already occupied, weave will report an error. At this time, you can use the -- ipalloc range parameter to manually specify the network segment to be used by weave
$ weave launch --ipalloc-range 10.60.0.0/12
-
Network isolation: by default, all containers are in the same subnet, but the assigned subnet can be specified through -- ipalloc default subnet (the subnet must be in the assignable network segment). If you want to realize the isolation of container network, instead of all containers in the cluster can access each other. Weave can use a subnet to achieve this function. Containers in the same subnet are connected to each other, while containers in different subnets are isolated. A container can be interconnected with containers in multiple networks in multiple subnets. Docker allows containers on the same machine to communicate with each other. For complete isolation, you need to add -- icc=false to the startup parameter of docker daemon.
$ weave launch --ipalloc-default-subnet 10.40.0.0/24 192.168.2.210
-
Specify a specific IP address:
-
By setting environment variables
$ eval $(weave env) $ docker run -e WEAVE_CIDR=10.35.1.1/24 --name c3 -it busybox sh /# ifconfig
-
Through the weave run command
$ weave run 10.36.1.1/24 --name c4 -it busybox sh $ docker exec -it c4 sh
-
Dynamically allocate the network: if the network cannot be determined when running the container, - e weave can be used_ CIDR = none parameter does not allocate network information first.
$ eval $(weave env) $ docker run -e WEAVE_CIDR=none --name c5 -it busybox sh / # ifconfig use weave attach ${container_id}Assign a network to a running container $ weave attach b1f7a647aee3 10.32.0.1 If you want to remove a container from a network, you can use weave detach command $ weave detach net:10.32.0.0/24 b1f7a647aee3 10.32.0.1
-
Internet connected weave
-
Weave is a private VxLAN network, which is isolated from the external network by default. How can external networks access containers in weave?
- First, join the host to the weave network.
- Then the host is used as the gateway to access the weave network. To join the host to weave, execute weave expose
-
How does the host host access the Docker image in the virtual machine
1. macos $ sudo route add -net 10.32.0.0/12 -netmask 255.240.0.0 192.168.100.141 2. linux $ ip route add 10.32.0.0/12 via 192.168.100.141
Command collation
-
command
1. see weave state $ weave status 2. View status details $ weave status connections 3. see weave Relationship between nodes $ weave status peers 4. View currently assigned containers $ weave ps 5. see weave current version $ weave version 6. Start and establish connection with other hosts weave And download the image $ weave launch 7. Connect IP Connect to peer server $ weave launch <ip address> 8. use weave agent $ weave env 9. Execute output|come from weave env Output of $ export DOCKER_HOST=unix:///var/run/weave/weave.sock 10. close weave $ weave stop 11. close weave env agent $ export DOCKER=OPTS=
common problem
-
If you test with a virtual machine and multiple virtual machines are cloned with the same virtual machine, the machine ID of all machines will be the same. The connection between different hosts will fail because the IP segments allocated by the virtual network card on the Weave bridge of each host are the same. The solution is to regenerate a different machine ID for each machine:
$ rm /etc/machine-id /var/lib/dbus/machine-id $ dbus-uuidgen --ensure $ systemd-machine-id-setup $ reboot