The project is the tenth chapter of "white hat security development practice", which contains zero trust security. The development language is go language. This project consists of three parts: reverse proxy and routing module (not an implicit proxy, which does not realize the function of hiding the proxy), authentication module and authentication module. I'm still learning the detailed development process. Because I haven't been in contact with go language, I don't know much about many places, so I have to learn from scratch.
The github address of this project is:
http://github.com/netxfly
I have encountered many problems in running this project on the local machine. First, the go language relies on packages. Many packages on the Internet and github cannot be downloaded due to network problems. I solved this problem by modifying the go mod and go init commands, plus modifying the go language network agent and opening the agent. In this way, the project does not report errors in the local vscode. Secondly, there is a very strange network problem. The demo of the first part of the project can run through the local machine, but the last integrated test demo always fails to run on the local machine. The server cannot receive and record the client's access request and some basic ip information. The final solution is to configure relevant files on the linux virtual machine from scratch. Fortunately, it finally runs through on the linux virtual machine.
Project presentation results:
There is a video of station B, which is the operation effect of the project https://www.bilibili.com/video/BV1uK4y1S7Ny?from=search&seid=12273164360537456600
The results are as follows:
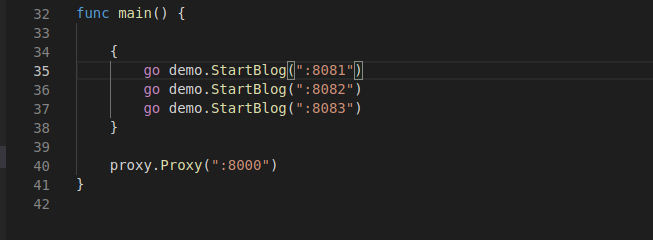
First, run main. Under zero trust demo Go file. The implementation effect is to start four ports, of which 808180828083 is the upper server and 8000 is the proxy server. When we access port 8000, we will automatically jump to one of the upper servers of 808180828083
Demonstration effect:
Direct access to port 8000 will directly tell you i am proxy
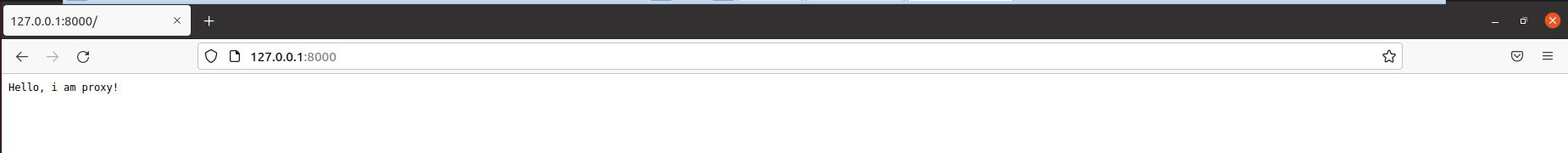
Direct access to upstream server port 808180828083
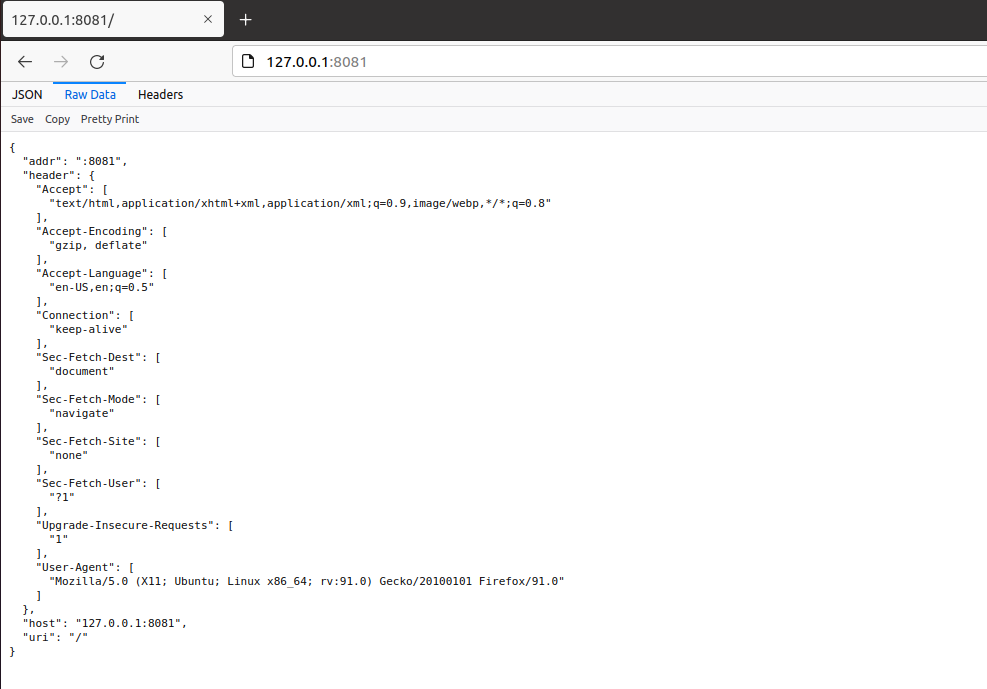

The function of this upstream server is to output the listening address of the back-end every time the user visits. The host of the back-end server, the url and header requested by the user are implemented by middleware.
When accessing the / blog directory under port 8000, port 8000 is allowed and will automatically jump to the upstream server, as shown in the figure below. After each refresh, it will randomly jump to one of the servers of 808180828083.
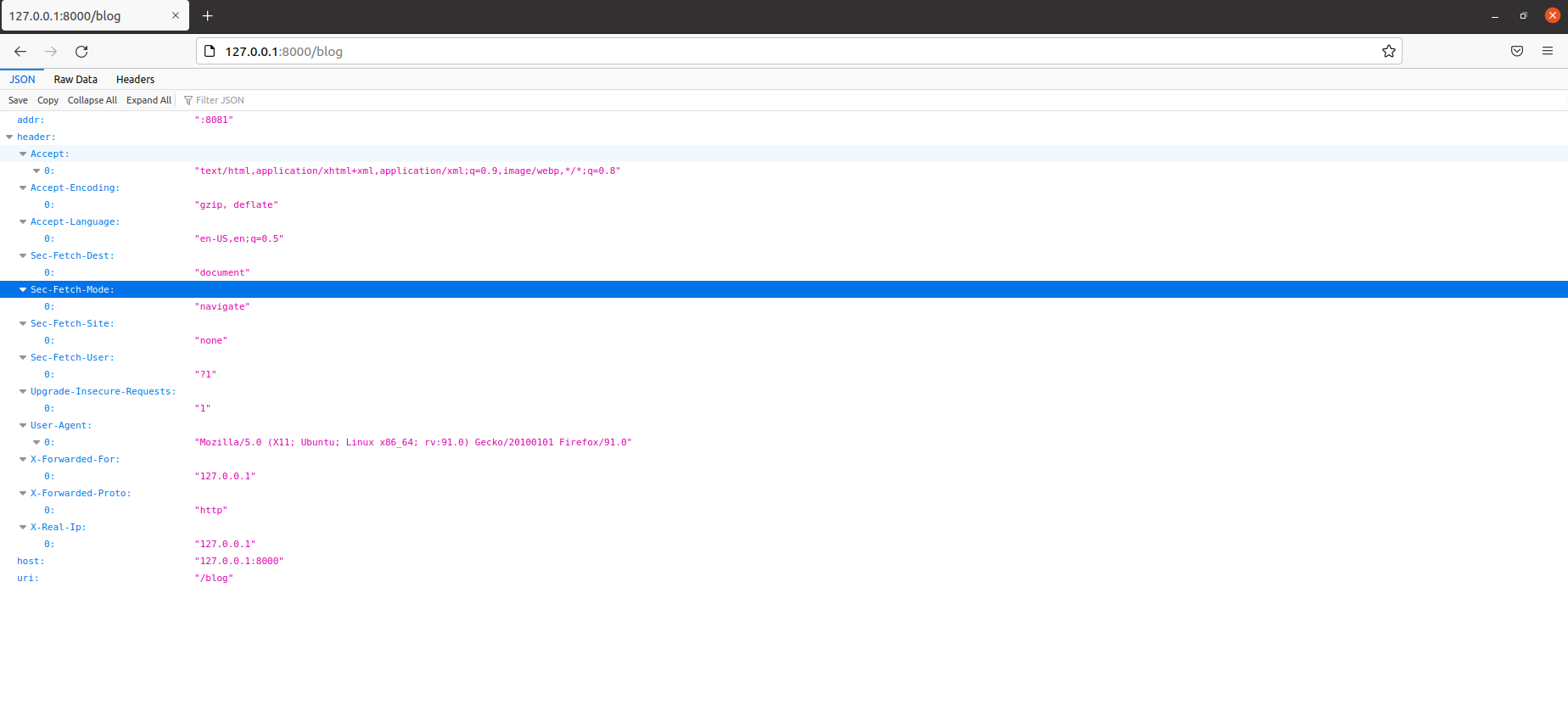
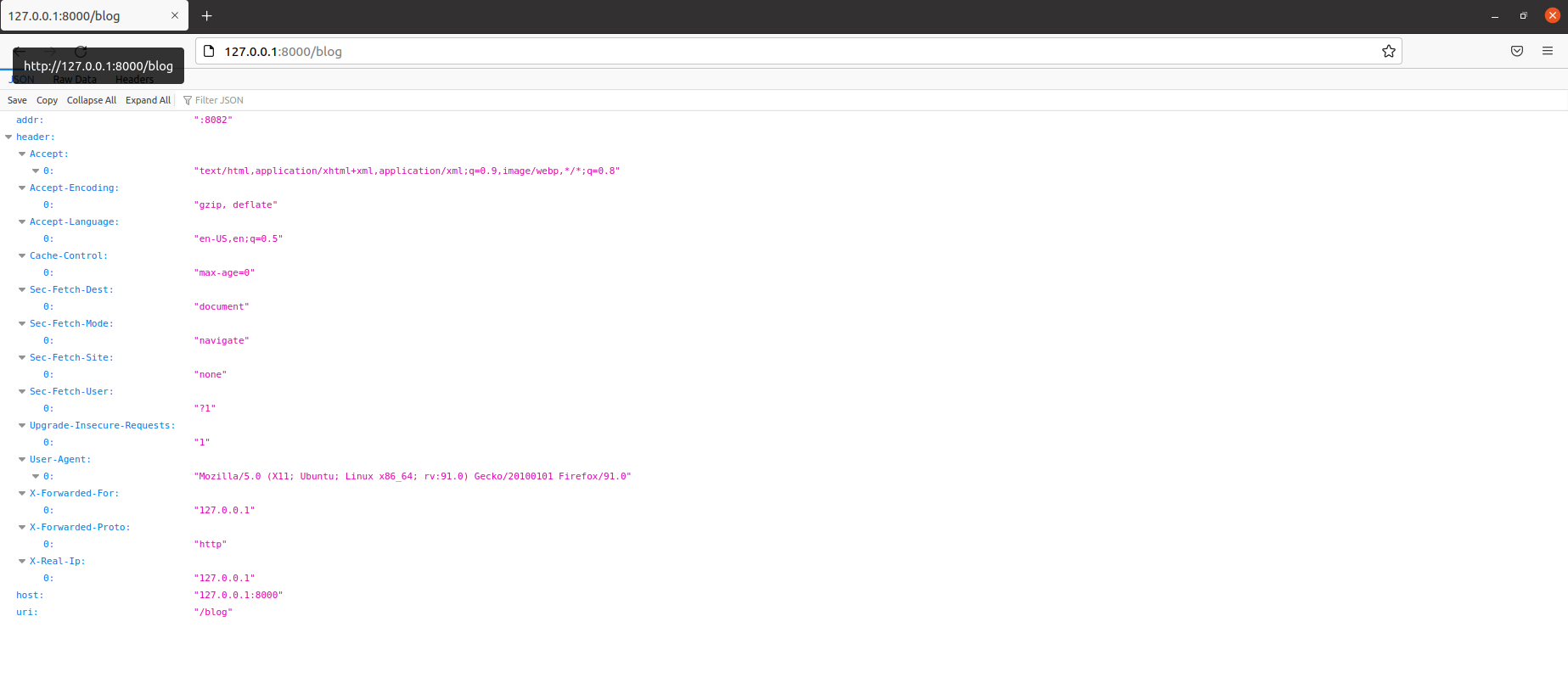
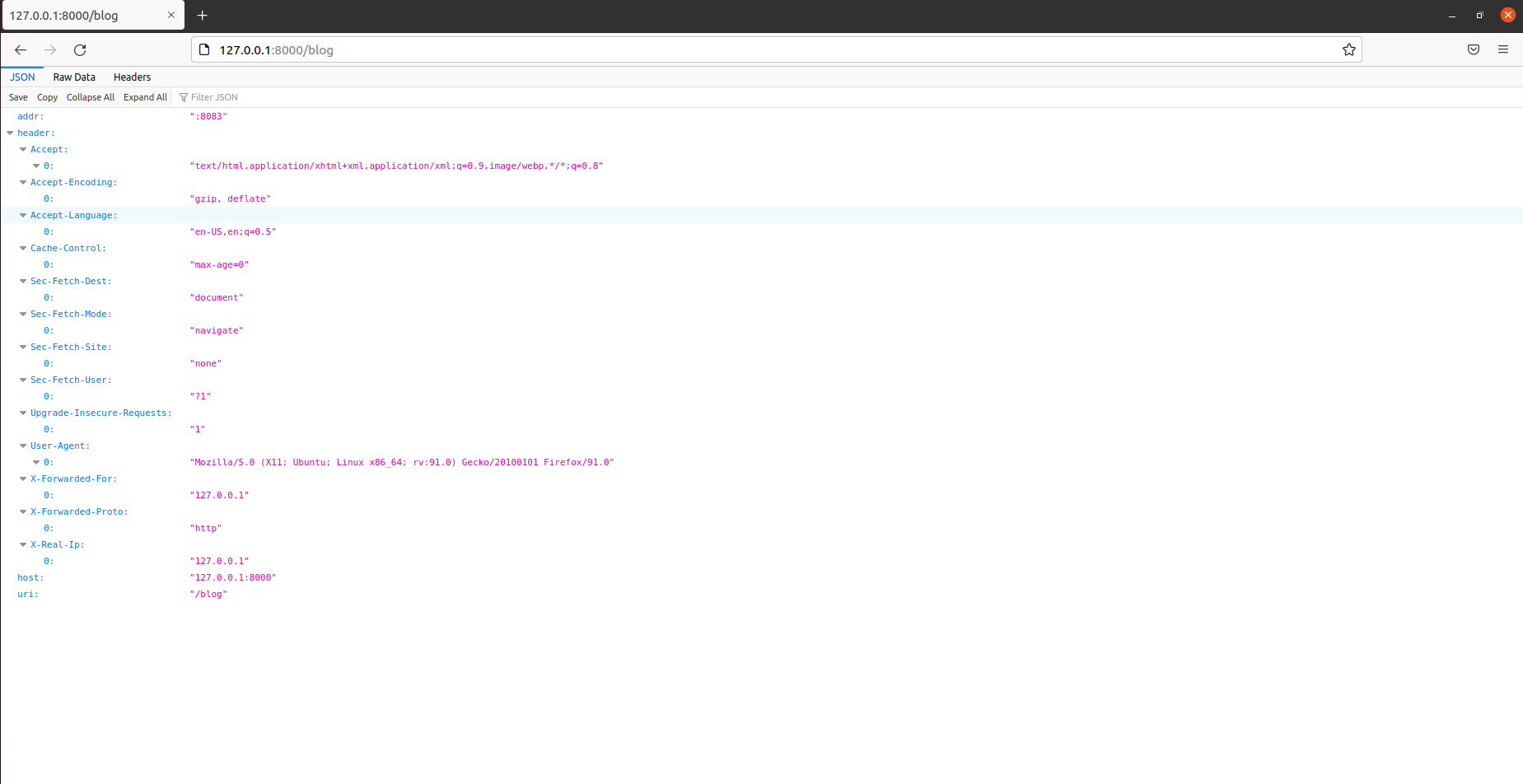
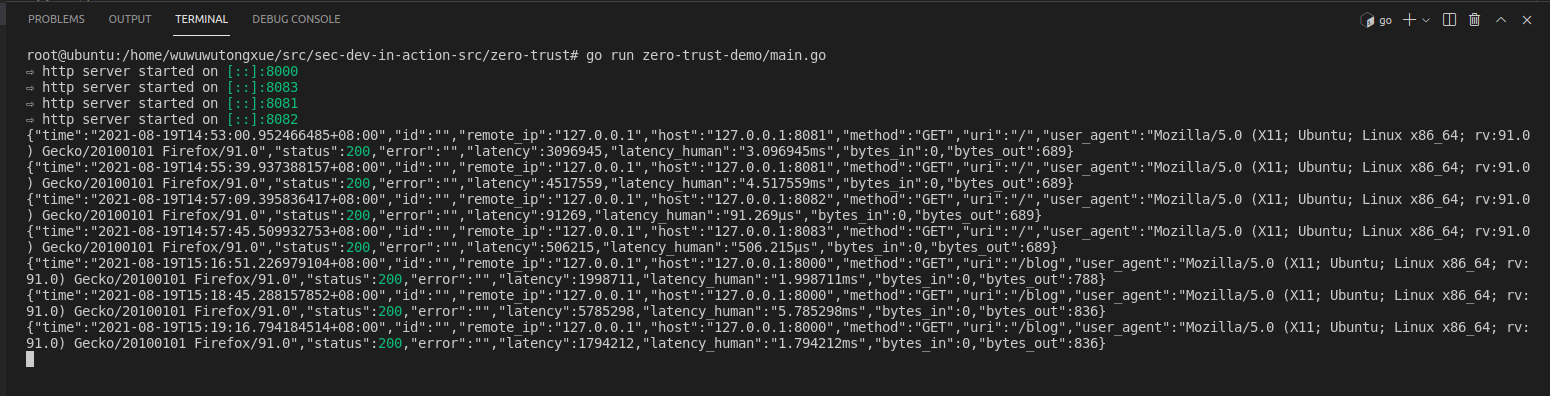
The information printed from the console is similar to that in the server blog directory above:
as follows
Code presentation and personal understanding
Main function:
This project structure directory
On the server Go and server Go two packages are mainly the implementation and call of some related functions and middleware
After a look, I can't understand and use many places and functions with my current ability, so I won't explain the source code for the time being.
The following is the main play, the implementation of zero trust proxy
Part by part
Implementation and configuration file of reverse proxy module
The configuration file of the reverse proxy consists of three parts: the front-end server (the reverse proxy itself), the back-end server (the upstream server of the reverse proxy), and the routing (that is, the url, according to different URLs)
, implementing different operations)
Profile:
Part I server configuration file:
server:
listen_ip: 0.0.0.0
//The ip monitored by the reverse proxy server. I haven't figured out what ip monitoring means
listen_port: 443
//The port on which the reverse proxy server listens
timeout: 30s
//Read / write time exceeded
idle_timeout: 30s
//Idle session exceeded time
tls_context:
//Certificate configuration
certificate_path: certs/server.crt
private_key_path: certs/server.key
The configuration file here is mainly filled with HTTP The corresponding field in the server structure. The public key and private key files are loaded through methods, which will not be discussed for the time being
Part II configuration of upstream server
upstreams:
- name: xsec1
//The name of the back-end server
connect_timeout: 5s
//Session exceeded time
url: http://127.0.0.1:8081
//Protocol and address of back-end server
- name: xsec2
connect_timeout: 5s
url: http://127.0.0.1:8082
Mainly for filling
Medium
// ReverseProxyConfig configuration settings for a proxy instance
type ReverseProxyConfig struct {
ConnectTimeout time.Duration
Timeout time.Duration
IdleTimeout time.Duration
}
This structure
Part III routing module
routes:
- host: p.xsec.io
rules:
- request.ip.network("10.211.55.0/24")
- request.email == "xsec888@gmail.com"
http:
paths:
- path: /
upstream: xsec1
authentication: true
- host: blog.xsec.io
rules:
- request.ip == "10.211.55.3"
- request.email == "xsec888@gmail.com"
http:
paths:
- path: /blog/
upstream: xsec1
authentication: true
The routing framework is used. The corresponding routing setting functions are encapsulated according to the host, upstream and path of the configuration file. The code is not understood