- Storage Based Authorization in the Metastore Server
- Based on storage authorization, metadata in the Metastore can be protected, but more fine-grained access control (such as column level and row level) is not provided
- SQL Standards Based Authorization in HiveServer2
- Hive authorization based on SQL standard is fully compatible with SQL authorization model. This mode is recommended
- Default Hive Authorization(Legacy Mode)
- Hive is authorized by default. It is only designed to prevent users from misoperation, not to prevent malicious users from accessing unauthorized data
- Authorization in HiveServer2
- limit
- When enabled, dfs, add, delete, compile, and reset commands are disabled
- The method of setting hive configuration through the set command is restricted to some users
- By modifying the configuration file {hive site xml
- hive. security. authorization. sqlstd. Config whitelist
- By modifying the configuration file {hive site xml
- Adding and deleting functions and macros are only open to users with admin
- User defined functions (open support for permanent user-defined functions) can be created by users with admin role, and can be used by other users
- The Transform function is disabled
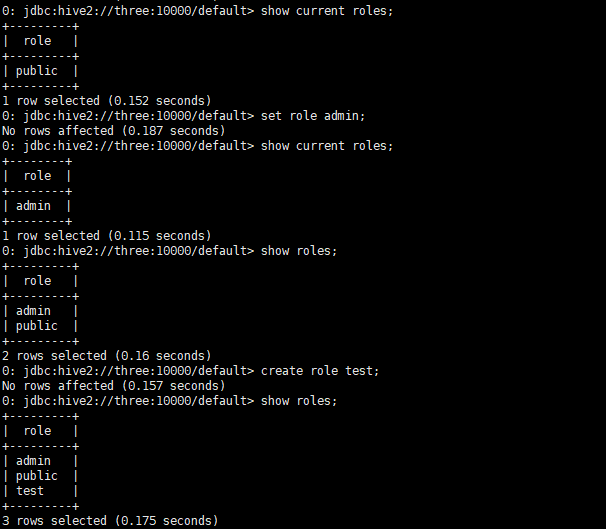
- concept
- Fully SQL compatible authorization model
- In addition to supporting the authorization and authentication of users, it also supports the authorization and authentication of role roles
- A role can be understood as a set of permissions. Users are authorized through a role
- A user can have one or more roles
- Another role is included by default: public and admin
- limit
hive-site.xml configuration
<!-- Mysql to configure -->
<property>
<name>hive.metastore.warehouse.dir</name>
<value>/var/hive/hive_remote/warehouse</value>
</property>
<property>
<name>javax.jdo.option.ConnectionURL</name>
<value>jdbc:mysql://one:3306/hive_remote?createDatabaseIfNotExist=true</value>
</property>
<property>
<name>javax.jdo.option.ConnectionDriverName</name>
<value>com.mysql.jdbc.Driver</value>
</property>
<property>
<name>javax.jdo.option.ConnectionUserName</name>
<value>root</value>
</property>
<property>
<name>javax.jdo.option.ConnectionPassword</name>
<value>123456</value>
</property>
<!-- Start authorization function -->
<property>
<name>hive.security.authorization.enabled</name>
<value>true</value>
</property>
<!-- Disable rule -->
<property>
<name>hive.server2.enable.doAs</name>
<value>false</value>
</property>
<!-- Who is admin Roles, multiple with commas -->
<property>
<name>hive.users.in.admin.role</name>
<value>root</value>
</property>
<property>
<name>hive.security.authorization.manager</name>
<value>org.apache.hadoop.hive.ql.security.authorization.plugin.sqlstd.SQLStdHiveAuthorizerFactory</value>
</property>
<property>
<name>hive.security.authenticator.manager</name>
<value>org.apache.hadoop.hive.ql.security.SessionStateUserAuthenticator</value>
</property>When you enter hive after configuration, you need to pay attention to the user name. Because it is anonymous, you cannot query it
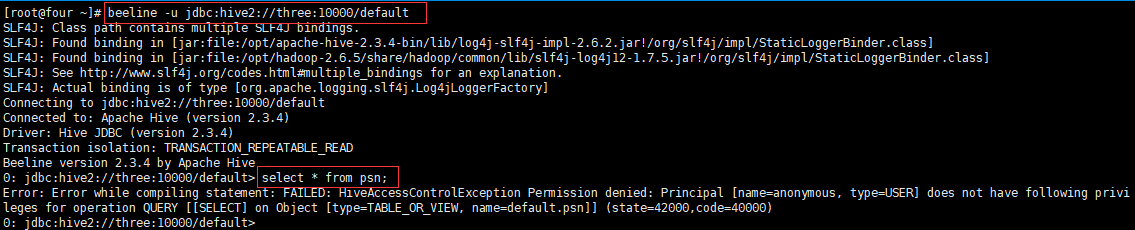
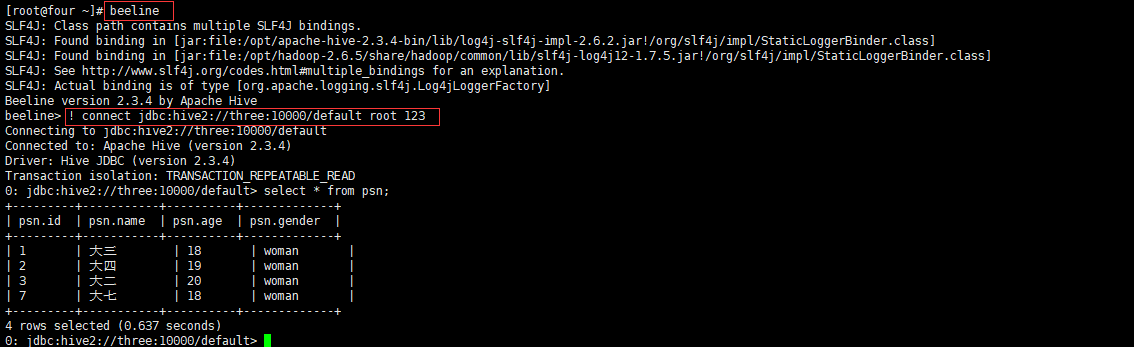
The user name should be added (the password doesn't matter, just enter it)
Add permission role
Assign permissions to new roles (empty by default)
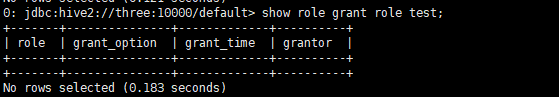
Role authorization assignment
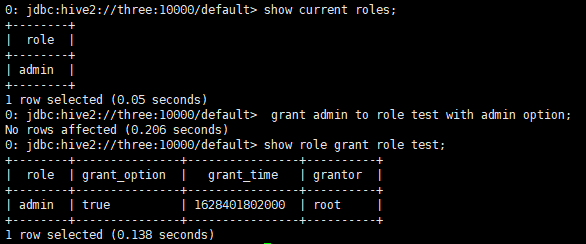
First, confirm that it is currently admin, and assign admin permissions to the test role
With the with admin option, it means that test has admin permissions and permissions assigned to other roles,
No, only have admin permission (for tables)
Whether the restriction of test is effective or not requires re-entry by the test user
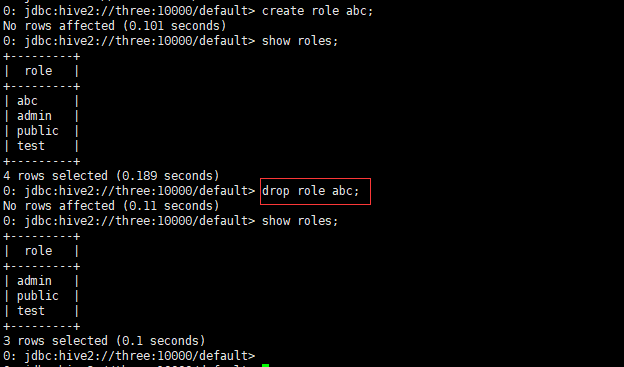
Delete role
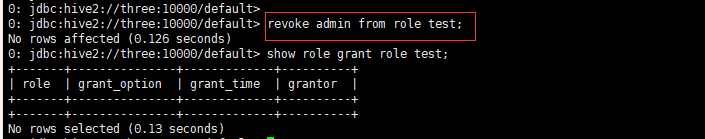
Delete role authorization
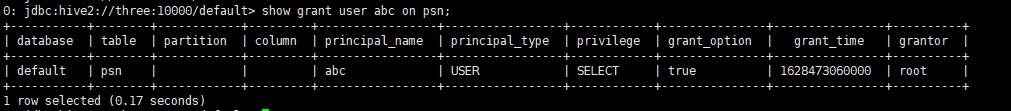
Assign the permissions of a table to the specified user (select, update, delete, insert, all)
- The query function of a specified table is assigned to the specified user (other operations do not have access)
- Users with grant option permission can also allocate table permissions for other users
- Other users cannot be assigned permissions that they do not have
- abc only has query function. It can also assign query function to other users. Other functions cannot be assigned
Assign using authorized users
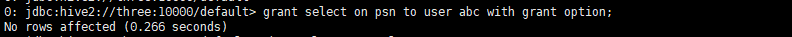
Operation by assigned user
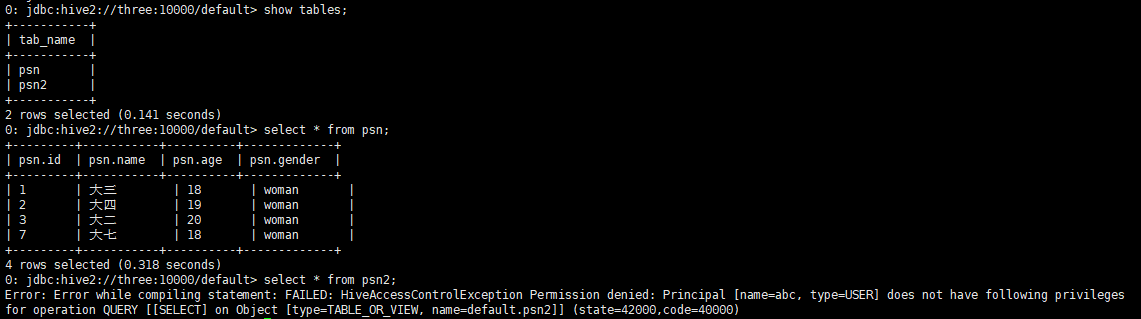
Query what restrictions the specified user has on the specified table