Password cracking
1. Introduction to password cracking
·Manual guessing
Trash can project, passive information collection
·Dictionary based brute force cracking (mainstream)
·Keyboard space character explosion
·Dictionary
Text file with user name and password (kali's own dictionary)
-/usr/share/wordlist
-/usr/share/wfuzz/wordlist
-/usr/share/seclists
2. Dictionary generation
(1)crunch
Facing the problem of guessing the password, we can use the dictionary to crack the password. In addition to kali's own password, we can also write our own password according to the rules.
The crunch command in kali allows us to write the required dictionary ourselves:
crunch <min-len> <max-len> [<charset string>] [options]
charset string is lowercase by default. The parameters are: minimum length, maximum length, character set used, and selected configuration parameters. For example:
crunch 6 6 0123456 -o START -d 2 -b 1mb / -c 100
-b split dictionary files by size (kb mb gb)
Because the dictionary file may be too large in some cases, we need to split it into smaller files. At this time, use the - b parameter
-c number of dictionary lines sets the number of lines in each dictionary file
(the above two parameters must be used in combination with - o START)
-d the number of consecutive occurrences of the same character, - d 2 is twice, such as a
-s specifies the starting string
crunch 4 4 01234567890 -s 9900
This sort starts from 9900 to 9999
character set
Every time you generate a dictionary, you don't need to manually enter some special character sets. For example, if I need A-Z character set, A-Z character set and 0-9 character set, I can use the character set provided by cruch:
crunch 4 4 -f /usr/share/crunch/charset.lst lalpha-sv -o 1.txt
Where, 4 represents the combination of only four characters (the minimum length is 4 and the maximum length is 4), - f is to find the character set in the file with the specified path, lalpha is a lowercase letter, - sv is a Swedish letter, - o is the output, and 1.txt is the file name
No duplication
The - p parameter can generate the full arrangement of our input strings:
crunch 1 1 -p 1234567890
The maximum and minimum password length exists but does not take effect, and the - p parameter must be placed last
Read file contents
The - q parameter can read the contents of each line in the file and generate a dictionary as basic characters
crunch 1 1 -filename
In this way, the dictionary file of each element arrangement and combination will be obtained
Write a dictionary of special rules
If the password conforms to a special structure, such as how many digits plus how many lowercase letters, we need to construct our own dictionary of corresponding rules, using the - t parameter:
crunch 6 6 -t @,%%^^ | more
| meaning | Symbol | English name |
|---|---|---|
| Lowercase letters | @ | lalpha |
| capital | , | ualpha |
| number | % | numeric |
| Symbol | ^ | symbols |
If you only want to get a few of them, you can further use the - t parameter:
crunch 5 5 abc DEF 123 \!@# -t ,@^%,
This meets the requirements of taking five characters, and the lowercase characters are selected from abc, the uppercase characters are selected from DEF, and the special characters are selected from@# Select (\ means escape symbol, so that special characters can be input, not special symbols with \) to generate a dictionary according to the given rules. If a person has no special needs, such as the number field, you can choose not to fill in, 0-9 by default; You can also choose not to fill in the lowercase letter column. It defaults to a-z, as long as you use + space occupation:
crunch 5 5 + DEF + \!@# -t ,@^%,
compress
If the output file is too large, we can choose to compress it:
crunch 4 4 -t @,%^ -o 1.txt -z 7z
Compressed to 7z format, gzip, bzip2 and lzma can also be used, but 7z has the highest compression ratio.
Combined application of crunch
You can set basic characters to generate a dictionary or use the - p parameter:
crunch 4 5 -p dog cat bird
Take the parameter after - p as the basic character, ignore the length, arrange and combine the basic characters to generate a dictionary. Similarly, the - p command can also be used with the - t command to combine basic characters with special rule characters:
crunch 5 5 -t aaa%% -p dog cat bird | more
The dictionary thus generated consists of three basic strings in front and two numbers in the back. Among them, aaa means that the first three parts of the password are composed of three basic strings, which only plays the role of placeholder. It can also be replaced by bbb or ccc.
To prevent repetition, you can also use the - d parameter mentioned earlier:
crunch 5 5 -d 2@ -t @@@%%
This prevents more than two repetitions in @ @.
(2)cewl
In addition to crunch, cewl is also a good dictionary generation software. More importantly, it can crawl website content to generate keyword dictionary, which is more accurate and efficient. The command is as follows:
cewl 1.1.1.1 -m 3 -d 3 -e -c -v -w a.txt (1.1.1.1 Can be the of the target site ip Address, or web address) -m:Minimum word length -d:Crawl depth -e:Collection contains emali Address information -c:Number of occurrences of each word a.txt Is the generated dictionary password file Support basic, digest, authentication Support agent;
Enter the following command to crawl the given url, specify the crawl depth, and output a word list, which can be used as a dictionary for cracking passwords:
cewl http://www.ignitetechnologies.in/
For record maintenance, better readability and future reference, we usually save the output word list to the txt file. We can use the - w parameter to save the output result to the txt file. The command is as follows:
cewl http://www.ignitetechnologies.in/ -w dict.txt
If you want to generate a dictionary with a specified word length, you can use the - m parameter, which means to specify the minimum word length:
cewl http://www.ignitetechnologies.in/ -m 9
You can use the - e parameter to enable the mail parameter, which is used in conjunction with the - n parameter. The - n parameter hides the generated word list when crawling a given website:
cewl http://www.ignitetechnologies.in/ -n -e
If you want to count the number of words repeated several times in the website, you can use the - c parameter to count:
cewl http://www.ignitetechnologies.in/ -c
If you want to increase the crawling level to traverse more words in the website to generate a larger dictionary, you can use the - d parameter and specify a crawling depth level for deeper crawling. The default level is 2:
cewl http://www.ignitetechnologies.in/ -d 3
3. Online password cracking
Online password cracking this cracking method generally requires that the object to be cracked can normally provide services to us. Generally speaking, it allows us to try to log in through a certain way or verify the correctness of the user's password
(1)hydra
Hydra, a powerful online password cracking tool, can crack Windows and Linux, vnc and other services. Using the - h parameter, you can see a large number of supported protocols, agents and applications. The basic syntax format is as follows:
Syntax: Hydra parameter IP service
The parameters are as follows:
Parameters: -l user Lowercase, specify the user name to crack, and use it when the user name is determined -L filename Uppercase, specifies the user name dictionary file for the user -p pass Lowercase, used to specify password cracking, rarely used, generally using password dictionary -P file Uppercase, used to specify the password dictionary -e ns Additional options, n: Empty password probe, s: Use specified account and password -M file Specify target ip List file, batch cracking -o file Specify the result output file -f Stop cracking when you find the first pair of login names or passwords -t tasks The number of threads running at the same time. The default is 16 -w time Set maximum timeout in -v / -V Show detailed process -R Resume blasting (if cracking is interrupted, execute next time) hydra -R /path/to/hydra.restore You can continue the task.) -x Custom password -s Non default service port
FTP protocol cracking
hydra -L User name dictionary -P Password dictionary -t 6 -e ns IP address -v
http protocol cracking
get Submit and crack web Sign in: hydra -L User name dictionary -P Password dictionary -t thread -v -e ns IP address http-get /admin/ hydra -L User name dictionary -P Password dictionary -t thread -v -e ns -f IP address http-get /admin/index.php post Submit and crack web Sign in: hydra -f -l user name -P Password dictionary -V -s 9900 IP address http-post-form "/admin/index.php?action=login:user=USER&pw=PASS:" #/index.php... This is the login url #The back door is POST data, in which the user name and password are replaced by USER PASS #Then there are the characters that will appear if there is a login error... Then start cracking
https protocol cracking
hydra -m /index.php -l user name -P Password dictionary.txt IP address https
Router cracking
hydra -l admin -x 6:10:1a.~!@#$%^&()-= -t 8 192.168.1.1 http-get / -l admin Is the user name trying to crack. # -x 6:10:1a. The password for enumeration is composed of numbers, lowercase letters, single character '.' and so on, with a length of 6 - 10 bits- t 8 indicates that the blasting attempt is divided into 8 parallel tasks. 192.168.1.1 is the Router address. HTTP get is the cracking method (Protocol)
smb cracking
hydra -l User name dictionary -P Password dictionary IP address smb
windows remote desktop
hydra ip address rdp -l administrator -P Password dictionary.txt -V
Mailbox pop3
hydra -l user name -P Password dictionary.txt my.pop3.mail pop3
In case of Linux password cracking, ssh protocol is generally used to log in. xhydra command opens the graphical interface, which is more friendly to beginners than the command line.
It should be noted that multi-threaded online password cracking may trigger the protection mechanism of some protocols: if the account is logged in more than the number of times per unit time, the request will be temporarily suspended, resulting in failure to try to log in again. Therefore, it is necessary to reasonably set the thread of hydra.
(2)pw-inspector
If the dictionary is complex and there are many unnecessary and unqualified passwords, you can use PW inspector to filter the dictionary:
pw -inspector -i input file -o output file -m Minimum length of a valid password -M Maximum length of a valid password -l Lowercase letters -u capital -p Printable characters -s Special characters -n number
For example, only lowercase letters are required:
pw-inspector -i pass.lst -o up.lst -l //Filter the lowercase characters of pass.lst dictionary and output them as lp.lst
If it is necessary to limit the length, add the parameter - m 3 -M 5. The minimum is 3 and the maximum is 5
(3)medusa
Compared with hydra, it has the following disadvantages: 1. Poor stability and frequent crashes. 2. Speed control is not easy to trigger service shielding or deadlock. 3. Create new processes per host and new instances per service, wasting resources. 4. Poor performance when cracking a large number of targets. medusa has good stability, proper speed control and thread based, and will not occupy too much resources, but the disadvantage is that it does not support too many service types.
-h Set target address -H Get destination address from file -u Set user name for cracking -U Get user name from file -p Set password for cracking -P Get password from dictionary -C Combined file information -O Log information file -e[n/s/ns] n Indicates an empty password, s Indicates that the password is the same as the user name -n Use non default tpc port -M Module execution -s Enable ssl -r Retry time, three seconds by default -t Set the number of threads -d View module information -F Scan the first correct password in any service and stop -f Scan to a correct password and stop -V Display mode (showing the process of cracking) -v num Show the complexity of the process (1)-6) -q View parameters (similar) show options)
basic operation
Specify a user name and password to crack
medusa -M ssh -u root -p qwaspbwa -h 192.168.72.153
Create a password file and specify it
medusea -M ssh -u root -P passlist.txt -h 192.168.72.142
At the same time, we need to change the number of threads
medusea -M ssh -U userlist.txt -P passlist.txt -h 192.168.72.142 -t 5
4. Offline password cracking
Plaintext is rarely used when the server transmits data. Considering security factors, encrypted transmission is gradually used. The main features are: hash algorithm is used for encryption (easy to encrypt and difficult to decrypt) for each authentication, and the data sent to the server is encrypted. Asymmetric encryption algorithm is generally used instead of symmetric encryption algorithm for identity authentication.
Symmetric encryption algorithm is simply a secret key, which is responsible for decryption and encryption without change. The advantage is that it is more convenient. The disadvantage is that once the secret key is obtained, all the information will be obtained. For example, if the letter a corresponds to 1 in a group of passwords, then a in each ciphertext corresponds to 1.
The asymmetric algorithm is one-way encryption. If you input a character with variable length, you will always get a string of random ciphertext with fixed length, which is difficult to deduce the ciphertext. However, the server retains a correct hash value. You only need to compare the hash value. If the hash value is correct, the encryption code must be correct.
Users can also use the method of adding salt to confuse the public: the password salt contains random values and encryption methods. The random values are randomly generated by the computer and mixed in the original password in a random way, and then a string is generated according to the encryption method and saved in the server. In other words, this is one-way, and the computer does not know the customer's original password, even if it knows the password In the encryption method, the string before encryption is inversely pushed out, which is also the result of the mixing of the real password and the random value, so the user's real password cannot be parsed. Adding salt is actually adding a random string to the password and then hashing, which reduces the possibility of inversely pushing out the password according to the hash.
It is called offline password cracking because we get the data packet encrypted by the hash algorithm. We need to calculate the plaintext hash value and compare it with the obtained hash value. If the hash value is correct, it means that the cracking is successful. In the final analysis, it still depends on the dictionary. However, compared with online cracking, it will not trigger the alarm mechanism.
(1) HASH identification tool
For offline password cracking, you first need to know which encryption method is used, and generally use tools (which may be incorrectly identified or unrecognized):
·hash-identifier
Enter hash identifier in kali's terminal to call this tool. Enter the hash value, and the possible encryption methods will be displayed.
·hashid
Enter the hash + hash value in the kali terminal interface to get the hash encryption type
(2) Offline password cracking tool -- hashcat
·Open source multithreaded password cracking tool
·Support more than 80 encryption algorithms
·CPU based computing power cracking
·Six modes:
| pattern | Code |
|---|---|
| 0 | dictionary attack |
| 1 | Arrange and combine the passwords in the dictionary |
| 2 | Try a combination of uppercase and lowercase letters for all passwords in the dictionary |
| 3 | Specifies all combinations of character sets |
| 4 | Replacement combination of all characters of password in dictionary |
| 5 | The program automatically generates masks for all passwords in the dictionary |
The set parameters are:
-m Specifies the hash type -a Specify cracking mode -V View version information -o Save the output results to the specified file --force Ignore warning --show Show cracked only hash Password and corresponding plaintext --remove Delete the successfully cracked from the source file hash --username ignore hash User name in table -b Test the computer cracking speed and related hardware information -O Limit password length -T Set the number of threads -r Use rule file -1 Custom character set -1 0123asd -2 Custom character set -2 0123asd -3 Custom character set -3 0123asd -i Enable incremental cracking mode --increment-min Set minimum password length --increment-max Set maximum password length
Integrated character set:
?l Represents lowercase letters ?u Represents capital letters ?d Representative number ?s Represents special characters ?a Represents upper and lower case letters, numbers, and special characters ?b 0x00-0xff
Add a character set after the cracked command to narrow the scope of cracking.
example:
Use md5 encryption first
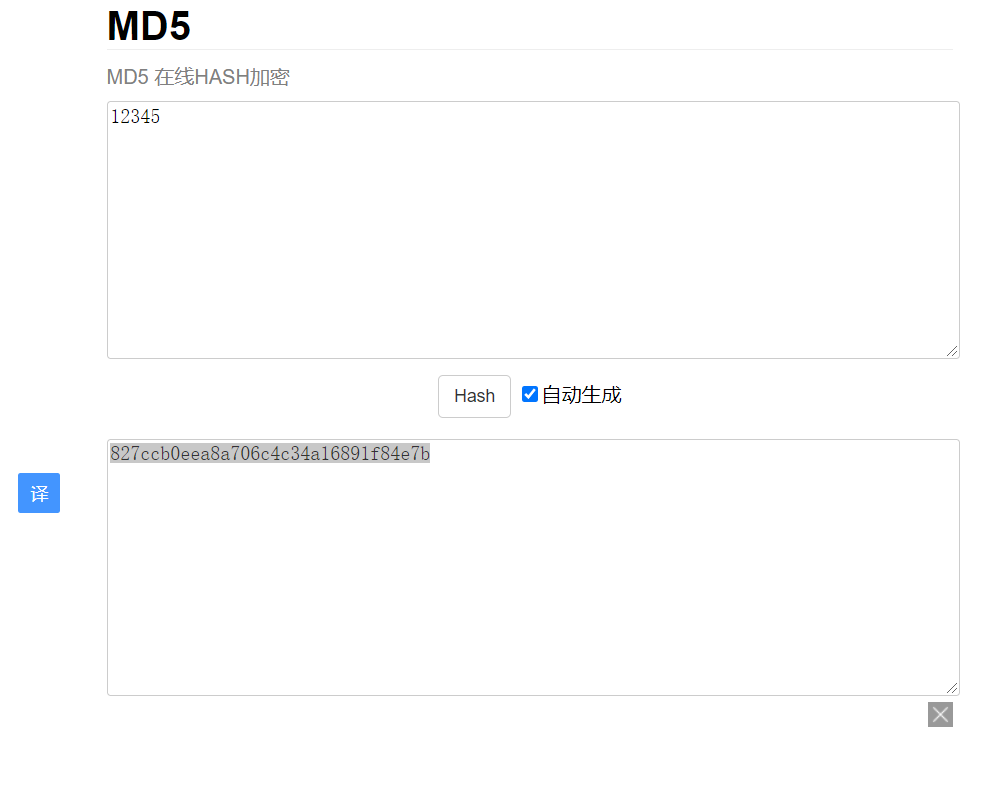
Get the ciphertext 827ccb0eea8a706c4c34a16891f84e7b, open hashcat to crack it, and enter the following command:
hashcat -m 0 -a 3 827ccb0eea8a706c4c34a16891f84e7b ?d?d?d?d?d
Crack the encrypted string
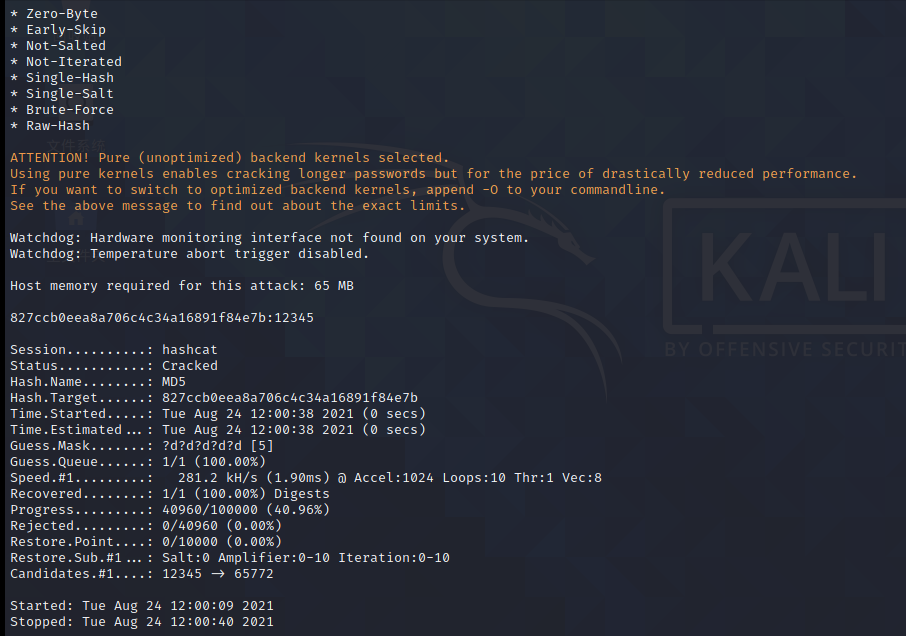
Cracked successfully, and the plaintext is 12345
(3) A more powerful hash cracking tool -- oclhashcat
Developed by the hashcat team, it is so powerful that the virtual machine cannot be installed. It can mobilize GPU and CPU to carry out a large number of operations. It is known as the world's fastest cracking software based on general graphics processor (GPGPU). The maximum support 55 bit password, anyway, we can't get it, touch it.
(4)RainbowCrack
When cracking the hash value, the software will first escape the password in the dictionary file into the hash value, and then compare it with the hash to be decrypted. If it needs to be cracked multiple times, the process will be repeated. Therefore, we can hash the password of the dictionary in advance and convert it into hash value, so as to compare it when cracking, saving the time of each conversion. The table generated by this pre calculation is called rainbow table
RainbowCrack tools included in kali:
-rtgen:Pre calculation, generating rainbow table, time-consuming stage -rtsort:yes rtgen The generated rainbow table is sorted -rcrack:Look up the rainbow table to crack the password -The above commands must be used sequentially
Format of rainbow table:
rtgen Hash type character range minimum number of bits maximum number of bits table index chain length chain number of index blocks
Hash types mainly include LM,NTLM,MD5,SHA1,SHA256
The main character types are:
[[number] numeric [[letter] alpha [letter+[number] alpha-numeric [[lowercase] loweralpha [Lowercase letters+[number] loweralpha-numeric [a lowercase letter+[capital letter] mixalpha [a lowercase letter+Capitalize+[number] mixalpha-numeric
For example, to generate a decrypted md5 and four digit pure digital rainbow table, use the command:
rtgen md5 numeric 4 4 0 3000 400000 0
A corresponding * *. rt * * format file will be generated. Use the rtsort command to start sorting
rtsort Generate file
Then use the sorted files to crack
rtcrack Table name -f hash.txt //hash.txt is the file name to be cracked rtcrack Table name -h hash //Directly follow the hash value rtcrack Table name -l File name (no suffix)